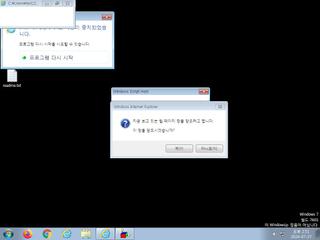
ScreenShot
| Created | 2024.07.27 14:52 | Machine | s1_win7_x6401 |
| Filename | ❉????????????????????????????????????_????????????????????????????❉_⑦⑨⑦④⑧⑦①②②⑥.hta | ||
| Type | HTML document, UTF-8 Unicode text, with very long lines, with CRLF line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 7 detected (Casbaneiro, TOPIS, svX9geGkdGF) | ||
| md5 | 30d99024fb26c365e71bcdd860205eb4 | ||
| sha256 | 92b01ff8e91052fe1537d9b35d8505b04ee896095c959f7ac1a68c94cfd228e6 | ||
| ssdeep | 1536:UqYHynreHKIXcArbapI/UtdLhly53ytrjvyDa+dzfZeG5SySLTuwEba/f1+zeWij:lBaKIZh/UtNnaer0YwjzE | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (18cnts)
| Level | Description |
|---|---|
| watch | A command shell or script process was created by an unexpected parent process |
| watch | Communicates with host for which no DNS query was performed |
| watch | Drops a binary and executes it |
| watch | Network communications indicative of a potential document or script payload download was initiated by the process wscript.exe |
| watch | One or more non-whitelisted processes were created |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| watch | Wscript.exe initiated network communications indicative of a script based payload download |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | An application raised an exception which may be indicative of an exploit crash |
| notice | Creates a suspicious process |
| notice | Creates executable files on the filesystem |
| notice | File has been identified by 7 AntiVirus engines on VirusTotal as malicious |
| notice | Performs some HTTP requests |
| notice | Resolves a suspicious Top Level Domain (TLD) |
| notice | Uses Windows utilities for basic Windows functionality |
| notice | Yara rule detected in process memory |
| info | Collects information to fingerprint the system (MachineGuid |
| info | One or more processes crashed |
Rules (9cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (download) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
Suricata ids
ET DNS Query to a *.top domain - Likely Hostile
ET INFO TLS Handshake Failure
ET DROP Spamhaus DROP Listed Traffic Inbound group 13
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
SURICATA Applayer Wrong direction first Data
ET INFO TLS Handshake Failure
ET DROP Spamhaus DROP Listed Traffic Inbound group 13
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
SURICATA Applayer Wrong direction first Data