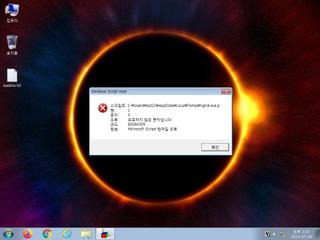
ScreenShot
| Created | 2024.07.29 13:49 | Machine | s1_win7_x6402 |
| Filename | ngrok.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 28 detected (Common, Artemis, Unsafe, a variant of WinGo, Ngrok, B potentially unsafe, DangerousSig, NetTool, MalCert, CLASSIC, PrivacyRisk, Redcap, Packed2, BadCert, Detected, CoinMiner, ABApplication, MGDP, FakeSig, susgen) | ||
| md5 | f02b8dabd9612d56140b7b435f70424b | ||
| sha256 | a90600d7ad852842934c03c5a8c752143c9ee11e6720f4114747f546ad53a3d1 | ||
| ssdeep | 393216:IN0uwoFGVN8x5ytoOO5mM2/1F/HXZjTN2VziJ+0Wg5tPW:W0uwoFsN8aS | ||
| imphash | 07361a3a7f515bf56ca93120b2aca73b | ||
| impfuzzy | 24:ibVjh9wOcX13uTkkboVaXOr6kwmDgUPMztxdD1tr6tl:AwOcX13UjXOmokxp1Zol | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 28 AntiVirus engines on VirusTotal as malicious |
| watch | Network communications indicative of a potential document or script payload download was initiated by the process wscript.exe |
| watch | Wscript.exe initiated network communications indicative of a script based payload download |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Performs some HTTP requests |
| info | One or more processes crashed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | ftp_command | ftp command | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | wget_command | wget command | binaries (upload) |
PE API
IAT(Import Address Table) Library
kernel32.dll
0x1ed1340 WriteFile
0x1ed1348 WriteConsoleW
0x1ed1350 WerSetFlags
0x1ed1358 WerGetFlags
0x1ed1360 WaitForMultipleObjects
0x1ed1368 WaitForSingleObject
0x1ed1370 VirtualQuery
0x1ed1378 VirtualFree
0x1ed1380 VirtualAlloc
0x1ed1388 TlsAlloc
0x1ed1390 SwitchToThread
0x1ed1398 SuspendThread
0x1ed13a0 SetWaitableTimer
0x1ed13a8 SetThreadPriority
0x1ed13b0 SetProcessPriorityBoost
0x1ed13b8 SetEvent
0x1ed13c0 SetErrorMode
0x1ed13c8 SetConsoleCtrlHandler
0x1ed13d0 RtlVirtualUnwind
0x1ed13d8 RtlLookupFunctionEntry
0x1ed13e0 ResumeThread
0x1ed13e8 RaiseFailFastException
0x1ed13f0 PostQueuedCompletionStatus
0x1ed13f8 LoadLibraryW
0x1ed1400 LoadLibraryExW
0x1ed1408 SetThreadContext
0x1ed1410 GetThreadContext
0x1ed1418 GetSystemInfo
0x1ed1420 GetSystemDirectoryA
0x1ed1428 GetStdHandle
0x1ed1430 GetQueuedCompletionStatusEx
0x1ed1438 GetProcessAffinityMask
0x1ed1440 GetProcAddress
0x1ed1448 GetErrorMode
0x1ed1450 GetEnvironmentStringsW
0x1ed1458 GetCurrentThreadId
0x1ed1460 GetConsoleMode
0x1ed1468 FreeEnvironmentStringsW
0x1ed1470 ExitProcess
0x1ed1478 DuplicateHandle
0x1ed1480 CreateWaitableTimerExW
0x1ed1488 CreateWaitableTimerA
0x1ed1490 CreateThread
0x1ed1498 CreateIoCompletionPort
0x1ed14a0 CreateFileA
0x1ed14a8 CreateEventA
0x1ed14b0 CloseHandle
0x1ed14b8 AddVectoredExceptionHandler
0x1ed14c0 AddVectoredContinueHandler
EAT(Export Address Table) is none
kernel32.dll
0x1ed1340 WriteFile
0x1ed1348 WriteConsoleW
0x1ed1350 WerSetFlags
0x1ed1358 WerGetFlags
0x1ed1360 WaitForMultipleObjects
0x1ed1368 WaitForSingleObject
0x1ed1370 VirtualQuery
0x1ed1378 VirtualFree
0x1ed1380 VirtualAlloc
0x1ed1388 TlsAlloc
0x1ed1390 SwitchToThread
0x1ed1398 SuspendThread
0x1ed13a0 SetWaitableTimer
0x1ed13a8 SetThreadPriority
0x1ed13b0 SetProcessPriorityBoost
0x1ed13b8 SetEvent
0x1ed13c0 SetErrorMode
0x1ed13c8 SetConsoleCtrlHandler
0x1ed13d0 RtlVirtualUnwind
0x1ed13d8 RtlLookupFunctionEntry
0x1ed13e0 ResumeThread
0x1ed13e8 RaiseFailFastException
0x1ed13f0 PostQueuedCompletionStatus
0x1ed13f8 LoadLibraryW
0x1ed1400 LoadLibraryExW
0x1ed1408 SetThreadContext
0x1ed1410 GetThreadContext
0x1ed1418 GetSystemInfo
0x1ed1420 GetSystemDirectoryA
0x1ed1428 GetStdHandle
0x1ed1430 GetQueuedCompletionStatusEx
0x1ed1438 GetProcessAffinityMask
0x1ed1440 GetProcAddress
0x1ed1448 GetErrorMode
0x1ed1450 GetEnvironmentStringsW
0x1ed1458 GetCurrentThreadId
0x1ed1460 GetConsoleMode
0x1ed1468 FreeEnvironmentStringsW
0x1ed1470 ExitProcess
0x1ed1478 DuplicateHandle
0x1ed1480 CreateWaitableTimerExW
0x1ed1488 CreateWaitableTimerA
0x1ed1490 CreateThread
0x1ed1498 CreateIoCompletionPort
0x1ed14a0 CreateFileA
0x1ed14a8 CreateEventA
0x1ed14b0 CloseHandle
0x1ed14b8 AddVectoredExceptionHandler
0x1ed14c0 AddVectoredContinueHandler
EAT(Export Address Table) is none