ScreenShot
| Created | 2024.07.31 10:24 | Machine | s1_win7_x6402 |
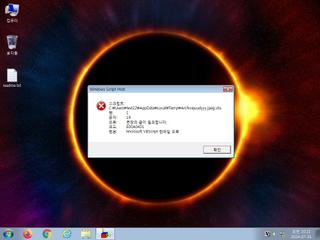
| Filename | Archivejuudyyy.jpeg.vbs | ||
| Type | C source, Little-endian UTF-16 Unicode text, with very long lines, with CRLF, CR line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 8 detected (gen81, SLoad, iacgm) | ||
| md5 | 7f2edeb8382cb0397d03bf2b3b32e528 | ||
| sha256 | e97292febc3a646570c920dabd05d4a733b509d09bf2574aea6bf9e39715ae10 | ||
| ssdeep | 768:pNDvG3Qbg2+y2m1BlElbJiPSpMU7wFVqESDF1vLm:+3QbgPlm1PUKUtB1v6 | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | File has been identified by 8 AntiVirus engines on VirusTotal as malicious |
| info | One or more processes crashed |
Rules (1cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | Javascript_ActiveXObject | Use ActiveXObject JavaScript | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|