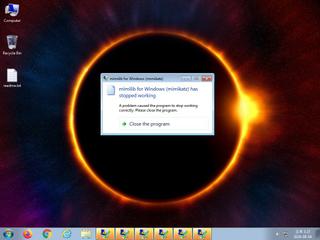
ScreenShot
| Created | 2024.08.04 13:26 | Machine | s1_win7_x6403 |
| Filename | mimilib.dll | ||
| Type | PE32+ executable (DLL) (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 54 detected (Mimikatz, HackTool, S13719267, HTool, Unsafe, uwccg, Malicious, score, eusljj, CLASSIC, Tool, HKTL, MIMIKATZ64, Apteryx, Detected, ai score=100, Malware@#3urk2nmtodhbg, Mikatz, TrojanPSW, Static AI, Malicious PE, susgen, confidence, 100%) | ||
| md5 | 80b4e71fcf1d3e41c95e608ae8258dcd | ||
| sha256 | 8c1e685c4d74b6d3deb7cb63a3797ddaa51c7fb8451b2531a036ef8ce55219f7 | ||
| ssdeep | 768:Klkr5X8k9jW/Y+lIIgxRWE/6yM8bRsnsFE+W8h9Wb7tQpla:gs8fkPW46y5basFOYItQpla | ||
| imphash | f91cbae9c276d5a9ad4babafc88ac0df | ||
| impfuzzy | 12:oedv9EnNpk0RzJXHvkscB7emcy77zPTZBzhPPXJ1XJU30O/9AGNDaZGGdFo3MH/4:9vsLRzJ8jB63on1Bz9L40q9NDac3MAqQ | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 54 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| info | Checks if process is being debugged by a debugger |
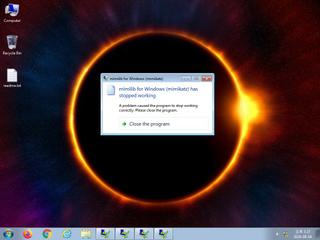
| info | One or more processes crashed |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x180006000 CreateRestrictedToken
0x180006008 CreateProcessAsUserW
0x180006010 ConvertSidToStringSidA
0x180006018 IsTextUnicode
0x180006020 OpenProcessToken
ntdll.dll
0x180006190 RtlFreeUnicodeString
0x180006198 RtlStringFromGUID
0x1800061a0 RtlEqualString
RPCRT4.dll
0x1800060f8 NdrMesTypeFree2
0x180006100 MesDecodeIncrementalHandleCreate
0x180006108 NdrMesTypeDecode2
0x180006110 MesIncrementalHandleReset
0x180006118 MesHandleFree
KERNEL32.dll
0x180006030 GetCurrentProcessId
0x180006038 GetCurrentThreadId
0x180006040 GetTickCount
0x180006048 QueryPerformanceCounter
0x180006050 SetUnhandledExceptionFilter
0x180006058 UnhandledExceptionFilter
0x180006060 TerminateProcess
0x180006068 RtlCaptureContext
0x180006070 RtlLookupFunctionEntry
0x180006078 Sleep
0x180006080 GetCurrentProcess
0x180006088 CloseHandle
0x180006090 FreeLibrary
0x180006098 LoadLibraryW
0x1800060a0 lstrlenW
0x1800060a8 GetProcAddress
0x1800060b0 LocalAlloc
0x1800060b8 LocalFree
0x1800060c0 GetTimeFormatA
0x1800060c8 GetDateFormatA
0x1800060d0 FileTimeToSystemTime
0x1800060d8 FileTimeToLocalFileTime
0x1800060e0 RtlVirtualUnwind
0x1800060e8 GetSystemTimeAsFileTime
msvcrt.dll
0x180006128 _wfopen
0x180006130 fclose
0x180006138 vfwprintf
0x180006140 fflush
0x180006148 memcpy
0x180006150 memset
0x180006158 __C_specific_handler
0x180006160 _XcptFilter
0x180006168 malloc
0x180006170 _initterm
0x180006178 free
0x180006180 _amsg_exit
EAT(Export Address Table) Library
0x1800011ec DhcpNewPktHook
0x18000113c DhcpServerCalloutEntry
0x1800013a0 DnsPluginCleanup
0x1800013a0 DnsPluginInitialize
0x1800012b0 DnsPluginQuery
0x180002994 ExtensionApiVersion
0x180001314 InitializeChangeNotify
0x180001318 PasswordChangeNotify
0x180001480 SpLsaModeInitialize
0x18000299c WinDbgExtensionDllInit
0x1800029d8 coffee
0x1800029e8 mimikatz
0x180001000 startW
ADVAPI32.dll
0x180006000 CreateRestrictedToken
0x180006008 CreateProcessAsUserW
0x180006010 ConvertSidToStringSidA
0x180006018 IsTextUnicode
0x180006020 OpenProcessToken
ntdll.dll
0x180006190 RtlFreeUnicodeString
0x180006198 RtlStringFromGUID
0x1800061a0 RtlEqualString
RPCRT4.dll
0x1800060f8 NdrMesTypeFree2
0x180006100 MesDecodeIncrementalHandleCreate
0x180006108 NdrMesTypeDecode2
0x180006110 MesIncrementalHandleReset
0x180006118 MesHandleFree
KERNEL32.dll
0x180006030 GetCurrentProcessId
0x180006038 GetCurrentThreadId
0x180006040 GetTickCount
0x180006048 QueryPerformanceCounter
0x180006050 SetUnhandledExceptionFilter
0x180006058 UnhandledExceptionFilter
0x180006060 TerminateProcess
0x180006068 RtlCaptureContext
0x180006070 RtlLookupFunctionEntry
0x180006078 Sleep
0x180006080 GetCurrentProcess
0x180006088 CloseHandle
0x180006090 FreeLibrary
0x180006098 LoadLibraryW
0x1800060a0 lstrlenW
0x1800060a8 GetProcAddress
0x1800060b0 LocalAlloc
0x1800060b8 LocalFree
0x1800060c0 GetTimeFormatA
0x1800060c8 GetDateFormatA
0x1800060d0 FileTimeToSystemTime
0x1800060d8 FileTimeToLocalFileTime
0x1800060e0 RtlVirtualUnwind
0x1800060e8 GetSystemTimeAsFileTime
msvcrt.dll
0x180006128 _wfopen
0x180006130 fclose
0x180006138 vfwprintf
0x180006140 fflush
0x180006148 memcpy
0x180006150 memset
0x180006158 __C_specific_handler
0x180006160 _XcptFilter
0x180006168 malloc
0x180006170 _initterm
0x180006178 free
0x180006180 _amsg_exit
EAT(Export Address Table) Library
0x1800011ec DhcpNewPktHook
0x18000113c DhcpServerCalloutEntry
0x1800013a0 DnsPluginCleanup
0x1800013a0 DnsPluginInitialize
0x1800012b0 DnsPluginQuery
0x180002994 ExtensionApiVersion
0x180001314 InitializeChangeNotify
0x180001318 PasswordChangeNotify
0x180001480 SpLsaModeInitialize
0x18000299c WinDbgExtensionDllInit
0x1800029d8 coffee
0x1800029e8 mimikatz
0x180001000 startW