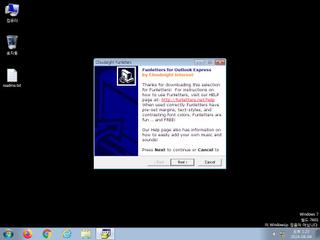
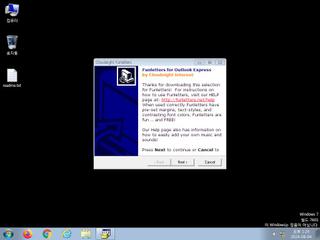
ScreenShot
| Created | 2024.08.04 13:46 | Machine | s1_win7_x6401 |
| Filename | china.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 13 detected (AIDetectMalware, Unsafe, Malicious, Zapchast, CLASSIC, mIRC, high, score, Detected, Fareit, Static AI, Suspicious PE, susgen) | ||
| md5 | a95e09168ff4b517c1ffa385206543b5 | ||
| sha256 | d417c5248d33ba5e02b468a08551c5eab4601ec318855ce0d9a0c7fb4103fa4f | ||
| ssdeep | 1536:a2qyK6nJjTpvWzt7p8AeAPJ2+Z814UZ0gaFE3zCE4GWAlPPBwsW:LrTvWzt7p8AeUwAhqsE3zCE4GDBW | ||
| imphash | d609a88c9c1c0b83071e61f9c45f78d2 | ||
| impfuzzy | 24:8cfpwPpOov+f0ivXrgw4yvbaDlPzOOgdA+w31hH:8cfpFrcEX0xrODG+uDH | ||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 13 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Drops an executable to the user AppData folder |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (11cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | ASPack_Zero | ASPack packed file | binaries (download) |
| watch | ASPack_Zero | ASPack packed file | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| info | CAB_file_format | CAB archive file | binaries (upload) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (download) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x406064 DeleteCriticalSection
0x406068 LeaveCriticalSection
0x40606c EnterCriticalSection
0x406070 InitializeCriticalSection
0x406074 VirtualFree
0x406078 VirtualAlloc
0x40607c LocalFree
0x406080 LocalAlloc
0x406084 TlsSetValue
0x406088 TlsGetValue
0x40608c GetModuleHandleA
0x406090 GetModuleFileNameA
0x406094 GetLastError
0x406098 GetCommandLineA
0x40609c WriteFile
0x4060a0 SetFilePointer
0x4060a4 SetEndOfFile
0x4060a8 RtlUnwind
0x4060ac ReadFile
0x4060b0 RaiseException
0x4060b4 GetStdHandle
0x4060b8 GetFileSize
0x4060bc GetFileType
0x4060c0 ExitProcess
0x4060c4 CreateFileA
0x4060c8 CloseHandle
user32.dll
0x4060d0 MessageBoxA
kernel32.dll
0x4060d8 WriteFile
0x4060dc SizeofResource
0x4060e0 LockResource
0x4060e4 LoadResource
0x4060e8 LoadLibraryA
0x4060ec GetTempPathA
0x4060f0 GetTempFileNameA
0x4060f4 GetProcAddress
0x4060f8 FreeResource
0x4060fc FreeLibrary
0x406100 FindResourceA
0x406104 FindFirstFileA
0x406108 FindClose
0x40610c FileTimeToLocalFileTime
0x406110 FileTimeToDosDateTime
0x406114 DeleteFileA
0x406118 CreateFileA
0x40611c CloseHandle
user32.dll
0x406124 TranslateMessage
0x406128 PeekMessageA
0x40612c MessageBoxA
0x406130 GetActiveWindow
0x406134 DispatchMessageA
EAT(Export Address Table) is none
kernel32.dll
0x406064 DeleteCriticalSection
0x406068 LeaveCriticalSection
0x40606c EnterCriticalSection
0x406070 InitializeCriticalSection
0x406074 VirtualFree
0x406078 VirtualAlloc
0x40607c LocalFree
0x406080 LocalAlloc
0x406084 TlsSetValue
0x406088 TlsGetValue
0x40608c GetModuleHandleA
0x406090 GetModuleFileNameA
0x406094 GetLastError
0x406098 GetCommandLineA
0x40609c WriteFile
0x4060a0 SetFilePointer
0x4060a4 SetEndOfFile
0x4060a8 RtlUnwind
0x4060ac ReadFile
0x4060b0 RaiseException
0x4060b4 GetStdHandle
0x4060b8 GetFileSize
0x4060bc GetFileType
0x4060c0 ExitProcess
0x4060c4 CreateFileA
0x4060c8 CloseHandle
user32.dll
0x4060d0 MessageBoxA
kernel32.dll
0x4060d8 WriteFile
0x4060dc SizeofResource
0x4060e0 LockResource
0x4060e4 LoadResource
0x4060e8 LoadLibraryA
0x4060ec GetTempPathA
0x4060f0 GetTempFileNameA
0x4060f4 GetProcAddress
0x4060f8 FreeResource
0x4060fc FreeLibrary
0x406100 FindResourceA
0x406104 FindFirstFileA
0x406108 FindClose
0x40610c FileTimeToLocalFileTime
0x406110 FileTimeToDosDateTime
0x406114 DeleteFileA
0x406118 CreateFileA
0x40611c CloseHandle
user32.dll
0x406124 TranslateMessage
0x406128 PeekMessageA
0x40612c MessageBoxA
0x406130 GetActiveWindow
0x406134 DispatchMessageA
EAT(Export Address Table) is none