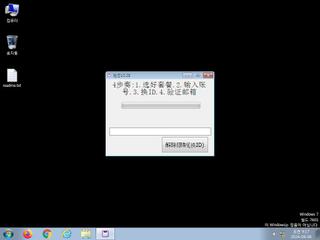
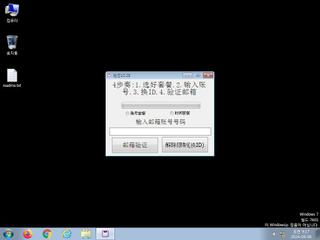
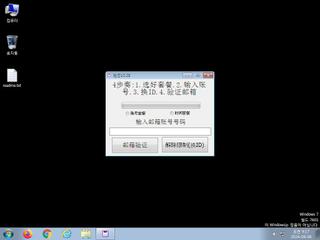
ScreenShot
| Created | 2024.08.06 09:37 | Machine | s1_win7_x6401 |
| Filename | 1.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 28 detected (AIDetectMalware, malicious, high confidence, score, Sality, Unsafe, Save, Attribute, HighConfidence, FileRepMalware, Misc, Real Protect, moderate, VMProtBad, Static AI, Suspicious PE, Detected, VMProtect, Malgent, ZexaF, @BW@aSK4SKdj, susgen, confidence) | ||
| md5 | c94b912d6522020372342c328fab4bc9 | ||
| sha256 | 486398f4ad2893c6fa6f17c00c35c7240ead7812c6ca2d282de6f5738f686055 | ||
| ssdeep | 196608:u2GfcMp7LWAWBnQ4SgbnHtYc0GdjuB7DMWcMq:alWAWBfSOHz0G4uWL | ||
| imphash | ff774b7f77cb7f48854b8436dceff24b | ||
| impfuzzy | 24:viAo2Xr7xEZVxcAfr+xlyGQ58QtXJHc9NDI5Q8:viWCZV6AjtGQ5ZXpcM5Q8 | ||
Network IP location
Signature (13cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 28 AntiVirus engines on VirusTotal as malicious |
| watch | Attempts to modify browser security settings |
| watch | Installs an hook procedure to monitor for mouse events |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | Drops an executable to the user AppData folder |
| notice | Foreign language identified in PE resource |
| notice | One or more potentially interesting buffers were extracted |
| notice | Resolves a suspicious Top Level Domain (TLD) |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is likely packed with VMProtect |
| info | Checks amount of memory in system |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (14cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| watch | VMProtect_Zero | VMProtect packed file | binaries (upload) |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x10ab000 GetVersionExW
USER32.dll
0x10ab008 LockWindowUpdate
GDI32.dll
0x10ab010 ExtSelectClipRgn
MSIMG32.dll
0x10ab018 TransparentBlt
COMDLG32.dll
0x10ab020 GetFileTitleW
WINSPOOL.DRV
0x10ab028 ClosePrinter
ADVAPI32.dll
0x10ab030 RegEnumValueW
SHELL32.dll
0x10ab038 SHFileOperationW
COMCTL32.dll
0x10ab040 _TrackMouseEvent
SHLWAPI.dll
0x10ab048 PathFindExtensionW
ole32.dll
0x10ab050 CoFreeUnusedLibraries
OLEAUT32.dll
0x10ab058 VariantCopy
oledlg.dll
0x10ab060 OleUIBusyW
urlmon.dll
0x10ab068 UrlMkSetSessionOption
gdiplus.dll
0x10ab070 GdipSetInterpolationMode
WININET.dll
0x10ab078 InternetGetCookieExW
UxTheme.dll
0x10ab080 CloseThemeData
WS2_32.dll
0x10ab088 WSAGetLastError
OLEACC.dll
0x10ab090 LresultFromObject
IMM32.dll
0x10ab098 ImmReleaseContext
WINMM.dll
0x10ab0a0 mciSendStringW
WTSAPI32.dll
0x10ab0a8 WTSSendMessageW
KERNEL32.dll
0x10ab0b0 VirtualQuery
USER32.dll
0x10ab0b8 GetProcessWindowStation
KERNEL32.dll
0x10ab0c0 LocalAlloc
0x10ab0c4 LocalFree
0x10ab0c8 GetModuleFileNameW
0x10ab0cc GetProcessAffinityMask
0x10ab0d0 SetProcessAffinityMask
0x10ab0d4 SetThreadAffinityMask
0x10ab0d8 Sleep
0x10ab0dc ExitProcess
0x10ab0e0 FreeLibrary
0x10ab0e4 LoadLibraryA
0x10ab0e8 GetModuleHandleA
0x10ab0ec GetProcAddress
USER32.dll
0x10ab0f4 GetProcessWindowStation
0x10ab0f8 GetUserObjectInformationW
EAT(Export Address Table) is none
KERNEL32.dll
0x10ab000 GetVersionExW
USER32.dll
0x10ab008 LockWindowUpdate
GDI32.dll
0x10ab010 ExtSelectClipRgn
MSIMG32.dll
0x10ab018 TransparentBlt
COMDLG32.dll
0x10ab020 GetFileTitleW
WINSPOOL.DRV
0x10ab028 ClosePrinter
ADVAPI32.dll
0x10ab030 RegEnumValueW
SHELL32.dll
0x10ab038 SHFileOperationW
COMCTL32.dll
0x10ab040 _TrackMouseEvent
SHLWAPI.dll
0x10ab048 PathFindExtensionW
ole32.dll
0x10ab050 CoFreeUnusedLibraries
OLEAUT32.dll
0x10ab058 VariantCopy
oledlg.dll
0x10ab060 OleUIBusyW
urlmon.dll
0x10ab068 UrlMkSetSessionOption
gdiplus.dll
0x10ab070 GdipSetInterpolationMode
WININET.dll
0x10ab078 InternetGetCookieExW
UxTheme.dll
0x10ab080 CloseThemeData
WS2_32.dll
0x10ab088 WSAGetLastError
OLEACC.dll
0x10ab090 LresultFromObject
IMM32.dll
0x10ab098 ImmReleaseContext
WINMM.dll
0x10ab0a0 mciSendStringW
WTSAPI32.dll
0x10ab0a8 WTSSendMessageW
KERNEL32.dll
0x10ab0b0 VirtualQuery
USER32.dll
0x10ab0b8 GetProcessWindowStation
KERNEL32.dll
0x10ab0c0 LocalAlloc
0x10ab0c4 LocalFree
0x10ab0c8 GetModuleFileNameW
0x10ab0cc GetProcessAffinityMask
0x10ab0d0 SetProcessAffinityMask
0x10ab0d4 SetThreadAffinityMask
0x10ab0d8 Sleep
0x10ab0dc ExitProcess
0x10ab0e0 FreeLibrary
0x10ab0e4 LoadLibraryA
0x10ab0e8 GetModuleHandleA
0x10ab0ec GetProcAddress
USER32.dll
0x10ab0f4 GetProcessWindowStation
0x10ab0f8 GetUserObjectInformationW
EAT(Export Address Table) is none