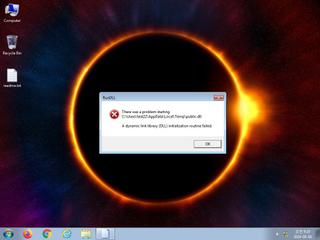
ScreenShot
| Created | 2024.08.06 09:36 | Machine | s1_win7_x6403 |
| Filename | public.dll | ||
| Type | PE32+ executable (DLL) (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 5 detected (malicious, high confidence, score, NanoDump, Detected, Gamarue) | ||
| md5 | 1e6e7fe9584055fc71294dc35a55241c | ||
| sha256 | c49d3eeeb6f2ecac701de73c4b6ed63e4aa8db0be2516af2bd84b36538557ddf | ||
| ssdeep | 384:NG5dslhJrXRdOGxqjXrABGgJYUBXc7arFiszL3YfLP8BIf/yHFC:N8dWkdjEwgJyQ3SoSy | ||
| imphash | 5ee28f7400f81bcba9b73317c7b0e6e9 | ||
| impfuzzy | 24:8MOYDZhKIyA4Tg9tihpBnylE9JPdLQzXh9DQb5d:kmelyendLyha | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| notice | File has been identified by 5 AntiVirus engines on VirusTotal as malicious |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
api-ms-win-crt-string-l1-1-0.dll
0x180006190 wcsncpy
0x180006198 wcsncat
0x1800061a0 _wcsicmp
0x1800061a8 wcsncmp
0x1800061b0 wcsnlen
api-ms-win-crt-convert-l1-1-0.dll
0x180006110 mbstowcs
api-ms-win-crt-utility-l1-1-0.dll
0x1800061d0 rand
0x1800061d8 srand
api-ms-win-crt-time-l1-1-0.dll
0x1800061c0 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x180006138 _cexit
0x180006140 _initialize_onexit_table
0x180006148 _initialize_narrow_environment
0x180006150 _seh_filter_dll
0x180006158 terminate
0x180006160 _initterm_e
0x180006168 _configure_narrow_argv
0x180006170 abort
0x180006178 _initterm
0x180006180 _execute_onexit_table
KERNEL32.dll
0x180006000 GetCurrentProcessId
0x180006008 LoadLibraryExW
0x180006010 FreeLibrary
0x180006018 TlsFree
0x180006020 TlsSetValue
0x180006028 TlsGetValue
0x180006030 TlsAlloc
0x180006038 InitializeCriticalSectionAndSpinCount
0x180006040 DeleteCriticalSection
0x180006048 SetLastError
0x180006050 InterlockedFlushSList
0x180006058 RtlUnwindEx
0x180006060 IsProcessorFeaturePresent
0x180006068 SetUnhandledExceptionFilter
0x180006070 UnhandledExceptionFilter
0x180006078 IsDebuggerPresent
0x180006080 RtlVirtualUnwind
0x180006088 RtlLookupFunctionEntry
0x180006090 RtlCaptureContext
0x180006098 InitializeSListHead
0x1800060a0 GetSystemTimeAsFileTime
0x1800060a8 GetCurrentThreadId
0x1800060b0 TerminateProcess
0x1800060b8 QueryPerformanceCounter
0x1800060c0 VirtualProtect
0x1800060c8 GetCurrentProcess
0x1800060d0 VirtualAlloc
0x1800060d8 GetModuleHandleA
0x1800060e0 GetProcAddress
0x1800060e8 HeapAlloc
0x1800060f0 GetProcessHeap
0x1800060f8 HeapFree
0x180006100 GetLastError
api-ms-win-crt-heap-l1-1-0.dll
0x180006120 free
0x180006128 calloc
EAT(Export Address Table) Library
0x1800012f0 DllMain
api-ms-win-crt-string-l1-1-0.dll
0x180006190 wcsncpy
0x180006198 wcsncat
0x1800061a0 _wcsicmp
0x1800061a8 wcsncmp
0x1800061b0 wcsnlen
api-ms-win-crt-convert-l1-1-0.dll
0x180006110 mbstowcs
api-ms-win-crt-utility-l1-1-0.dll
0x1800061d0 rand
0x1800061d8 srand
api-ms-win-crt-time-l1-1-0.dll
0x1800061c0 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x180006138 _cexit
0x180006140 _initialize_onexit_table
0x180006148 _initialize_narrow_environment
0x180006150 _seh_filter_dll
0x180006158 terminate
0x180006160 _initterm_e
0x180006168 _configure_narrow_argv
0x180006170 abort
0x180006178 _initterm
0x180006180 _execute_onexit_table
KERNEL32.dll
0x180006000 GetCurrentProcessId
0x180006008 LoadLibraryExW
0x180006010 FreeLibrary
0x180006018 TlsFree
0x180006020 TlsSetValue
0x180006028 TlsGetValue
0x180006030 TlsAlloc
0x180006038 InitializeCriticalSectionAndSpinCount
0x180006040 DeleteCriticalSection
0x180006048 SetLastError
0x180006050 InterlockedFlushSList
0x180006058 RtlUnwindEx
0x180006060 IsProcessorFeaturePresent
0x180006068 SetUnhandledExceptionFilter
0x180006070 UnhandledExceptionFilter
0x180006078 IsDebuggerPresent
0x180006080 RtlVirtualUnwind
0x180006088 RtlLookupFunctionEntry
0x180006090 RtlCaptureContext
0x180006098 InitializeSListHead
0x1800060a0 GetSystemTimeAsFileTime
0x1800060a8 GetCurrentThreadId
0x1800060b0 TerminateProcess
0x1800060b8 QueryPerformanceCounter
0x1800060c0 VirtualProtect
0x1800060c8 GetCurrentProcess
0x1800060d0 VirtualAlloc
0x1800060d8 GetModuleHandleA
0x1800060e0 GetProcAddress
0x1800060e8 HeapAlloc
0x1800060f0 GetProcessHeap
0x1800060f8 HeapFree
0x180006100 GetLastError
api-ms-win-crt-heap-l1-1-0.dll
0x180006120 free
0x180006128 calloc
EAT(Export Address Table) Library
0x1800012f0 DllMain