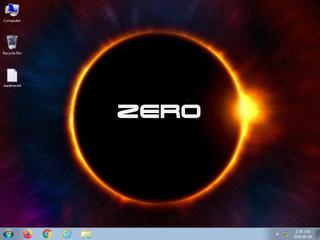
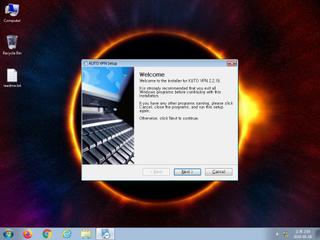
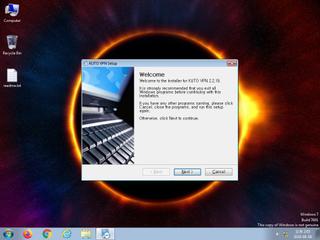
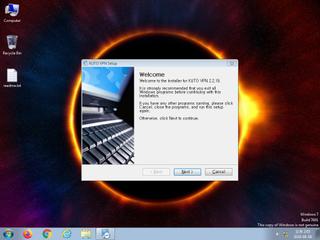
ScreenShot
| Created | 2024.08.08 14:09 | Machine | s1_win7_x6403 |
| Filename | latest.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 26 detected (Common, GenericKD, Unsafe, malicious, multiple detections, Artemis, MalwareX, Kryptik, CLOUD, zobmy, ai score=87, WinGo, Coinminer, R002H0CH524) | ||
| md5 | 664cebe18c30cc4c32a4dbf0715bf864 | ||
| sha256 | 4d38d3ec76c40174797b8deef25d85fd641baf489a86e1dc42989b82df0ed31d | ||
| ssdeep | 196608:Xz9+P1yXqSd6uGQeHQZGZ4PX5m3GloXDA5LTXHL3h0Z3+Xu+50ah:XYPLSUOVZGZwXQ3kae3LL350ah | ||
| imphash | d3f487c6c23e9d9845b2eca3fbdd93dd | ||
| impfuzzy | 48:tl0qOqGOJpPaAecfYtTE0c1GT+KQ4zuFbv:tl0qZGOjPlecfYtT9c4gv | ||
Network IP location
Signature (9cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 26 AntiVirus engines on VirusTotal as malicious |
| watch | Deletes executed files from disk |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
Rules (27cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Network_Downloader | File Downloader | binaries (download) |
| watch | Network_Downloader | File Downloader | binaries (upload) |
| watch | Network_Downloader | File Downloader | memory |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | ScreenShot | Take ScreenShot | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | JPEG_Format_Zero | JPEG Format | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x40700c _lclose
0x407010 GetModuleFileNameA
0x407014 _lread
0x407018 _llseek
0x40701c _lopen
0x407020 _lwrite
0x407024 _lcreat
0x407028 CreateDirectoryA
0x40702c SetCurrentDirectoryA
0x407030 lstrcatA
0x407034 FreeLibrary
0x407038 GetProcAddress
0x40703c LoadLibraryA
0x407040 GetDiskFreeSpaceA
0x407044 GetFileAttributesA
0x407048 RemoveDirectoryA
0x40704c DeleteFileA
0x407050 lstrlenA
0x407054 GetCurrentDirectoryA
0x407058 CloseHandle
0x40705c GetExitCodeProcess
0x407060 LocalFree
0x407064 GetCurrentProcess
0x407068 MoveFileExA
0x40706c Sleep
0x407070 GetStringTypeW
0x407074 MultiByteToWideChar
0x407078 LCMapStringW
0x40707c HeapReAlloc
0x407080 RtlUnwind
0x407084 HeapSize
0x407088 lstrcpyA
0x40708c GetTempPathA
0x407090 CompareStringA
0x407094 IsValidCodePage
0x407098 GetOEMCP
0x40709c GetModuleHandleW
0x4070a0 ExitProcess
0x4070a4 DecodePointer
0x4070a8 GetLastError
0x4070ac HeapFree
0x4070b0 HeapAlloc
0x4070b4 GetCommandLineA
0x4070b8 HeapSetInformation
0x4070bc GetStartupInfoW
0x4070c0 InitializeCriticalSectionAndSpinCount
0x4070c4 DeleteCriticalSection
0x4070c8 LeaveCriticalSection
0x4070cc EnterCriticalSection
0x4070d0 EncodePointer
0x4070d4 LoadLibraryW
0x4070d8 UnhandledExceptionFilter
0x4070dc SetUnhandledExceptionFilter
0x4070e0 IsDebuggerPresent
0x4070e4 TerminateProcess
0x4070e8 TlsAlloc
0x4070ec TlsGetValue
0x4070f0 TlsSetValue
0x4070f4 TlsFree
0x4070f8 InterlockedIncrement
0x4070fc SetLastError
0x407100 GetCurrentThreadId
0x407104 InterlockedDecrement
0x407108 WriteFile
0x40710c GetStdHandle
0x407110 GetModuleFileNameW
0x407114 IsProcessorFeaturePresent
0x407118 HeapCreate
0x40711c FreeEnvironmentStringsW
0x407120 WideCharToMultiByte
0x407124 GetEnvironmentStringsW
0x407128 SetHandleCount
0x40712c GetFileType
0x407130 QueryPerformanceCounter
0x407134 GetTickCount
0x407138 GetCurrentProcessId
0x40713c GetSystemTimeAsFileTime
0x407140 GetCPInfo
0x407144 GetACP
USER32.dll
0x407154 TranslateMessage
0x407158 DispatchMessageA
0x40715c PeekMessageA
0x407160 wsprintfA
0x407164 LoadCursorA
0x407168 SetCursor
0x40716c MessageBoxA
0x407170 MsgWaitForMultipleObjects
ADVAPI32.dll
0x407000 GetTokenInformation
0x407004 OpenProcessToken
SHELL32.dll
0x40714c ShellExecuteExA
EAT(Export Address Table) is none
KERNEL32.dll
0x40700c _lclose
0x407010 GetModuleFileNameA
0x407014 _lread
0x407018 _llseek
0x40701c _lopen
0x407020 _lwrite
0x407024 _lcreat
0x407028 CreateDirectoryA
0x40702c SetCurrentDirectoryA
0x407030 lstrcatA
0x407034 FreeLibrary
0x407038 GetProcAddress
0x40703c LoadLibraryA
0x407040 GetDiskFreeSpaceA
0x407044 GetFileAttributesA
0x407048 RemoveDirectoryA
0x40704c DeleteFileA
0x407050 lstrlenA
0x407054 GetCurrentDirectoryA
0x407058 CloseHandle
0x40705c GetExitCodeProcess
0x407060 LocalFree
0x407064 GetCurrentProcess
0x407068 MoveFileExA
0x40706c Sleep
0x407070 GetStringTypeW
0x407074 MultiByteToWideChar
0x407078 LCMapStringW
0x40707c HeapReAlloc
0x407080 RtlUnwind
0x407084 HeapSize
0x407088 lstrcpyA
0x40708c GetTempPathA
0x407090 CompareStringA
0x407094 IsValidCodePage
0x407098 GetOEMCP
0x40709c GetModuleHandleW
0x4070a0 ExitProcess
0x4070a4 DecodePointer
0x4070a8 GetLastError
0x4070ac HeapFree
0x4070b0 HeapAlloc
0x4070b4 GetCommandLineA
0x4070b8 HeapSetInformation
0x4070bc GetStartupInfoW
0x4070c0 InitializeCriticalSectionAndSpinCount
0x4070c4 DeleteCriticalSection
0x4070c8 LeaveCriticalSection
0x4070cc EnterCriticalSection
0x4070d0 EncodePointer
0x4070d4 LoadLibraryW
0x4070d8 UnhandledExceptionFilter
0x4070dc SetUnhandledExceptionFilter
0x4070e0 IsDebuggerPresent
0x4070e4 TerminateProcess
0x4070e8 TlsAlloc
0x4070ec TlsGetValue
0x4070f0 TlsSetValue
0x4070f4 TlsFree
0x4070f8 InterlockedIncrement
0x4070fc SetLastError
0x407100 GetCurrentThreadId
0x407104 InterlockedDecrement
0x407108 WriteFile
0x40710c GetStdHandle
0x407110 GetModuleFileNameW
0x407114 IsProcessorFeaturePresent
0x407118 HeapCreate
0x40711c FreeEnvironmentStringsW
0x407120 WideCharToMultiByte
0x407124 GetEnvironmentStringsW
0x407128 SetHandleCount
0x40712c GetFileType
0x407130 QueryPerformanceCounter
0x407134 GetTickCount
0x407138 GetCurrentProcessId
0x40713c GetSystemTimeAsFileTime
0x407140 GetCPInfo
0x407144 GetACP
USER32.dll
0x407154 TranslateMessage
0x407158 DispatchMessageA
0x40715c PeekMessageA
0x407160 wsprintfA
0x407164 LoadCursorA
0x407168 SetCursor
0x40716c MessageBoxA
0x407170 MsgWaitForMultipleObjects
ADVAPI32.dll
0x407000 GetTokenInformation
0x407004 OpenProcessToken
SHELL32.dll
0x40714c ShellExecuteExA
EAT(Export Address Table) is none