ScreenShot
| Created | 2024.08.08 16:10 | Machine | s1_win7_x6401 |
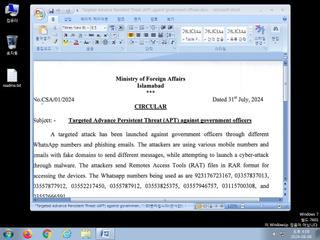
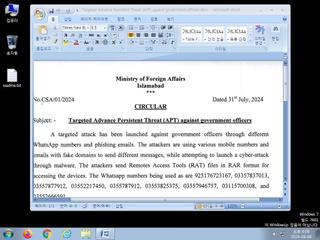
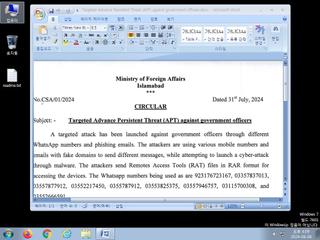
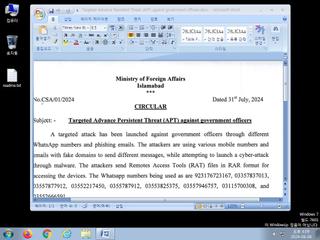
| Filename | Targeted Advance Persistent Threat (APT) against government officers.docx | ||
| Type | Microsoft OOXML | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 11 detected (Malicious, score, RemoteTemplateInj, Dotmer, CVE-2017-0199, equmby, W2000, cgazx, Probably Heur, W97OleLink, OMacro) | ||
| md5 | ccec3e4857cbb197ac79b0f3b01f5189 | ||
| sha256 | fec66a9aabf379d150ad51926b318f9c03edbe8f7e655193c036db6c0ba9a6b6 | ||
| ssdeep | 6144:eVwaZ1vuLuyLI1BydNHpHdQ5SFRFLogIH5pZyl6HJp/9/BIk8otiE8NgrhjWxn/Z:eVwa/vuLTLI1cpHd7WZpAwBIk82iEHrw | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (6cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 11 AntiVirus engines on VirusTotal as malicious |
| watch | Libraries known to be associated with a CVE were requested (may be False Positive) |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates (office) documents on the filesystem |
| notice | Creates hidden or system file |
| notice | Performs some HTTP requests |
Rules (2cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | docx | Word 2007 file format detection | binaries (upload) |
| info | zip_file_format | ZIP file format | binaries (upload) |
Network (5cnts) ?
Suricata ids
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)