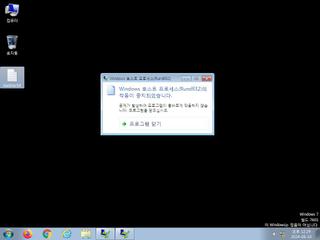
ScreenShot
| Created | 2024.08.10 12:32 | Machine | s1_win7_x6401 |
| Filename | rutua.dll | ||
| Type | PE32 executable (DLL) (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 24 detected (AIDetectMalware, malicious, high confidence, score, Unsafe, Vy7j, Attribute, HighConfidence, VMProtect, BC suspicious, Artemis, MalwareX, Kryptik, GYKdcmG8yzF, Static AI, Malicious PE, Wacapew, FakeAV, Floxif, FileInfector, Outbreak, confidence, Wacatac, H9nj) | ||
| md5 | ff432e4003e9d7135a97bd4dc0445dc3 | ||
| sha256 | 03495c3e0d041d6c6c1949cf6cfabea9b3d4308fee9cbf85754bb00b434d3778 | ||
| ssdeep | 393216:fRdW64cosTowwMzcG5FU90WGqNyW8O9hHZUSStMbZlna4:T6gozccuLoNyW8evUSs2 | ||
| imphash | 6c871eb5afcc648e749d578ab8277277 | ||
| impfuzzy | 3:s3rAVMQWmJIWgI/:4rAmC | ||
Network IP location
Signature (6cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 24 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x6d1fd000 AddVectoredExceptionHandler
msvcrt.dll
0x6d1fd008 __mb_cur_max
EAT(Export Address Table) Library
0x6c7a6460 MainFunc
0x6cabf64c _cgo_dummy_export
KERNEL32.dll
0x6d1fd000 AddVectoredExceptionHandler
msvcrt.dll
0x6d1fd008 __mb_cur_max
EAT(Export Address Table) Library
0x6c7a6460 MainFunc
0x6cabf64c _cgo_dummy_export