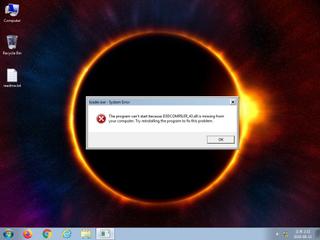
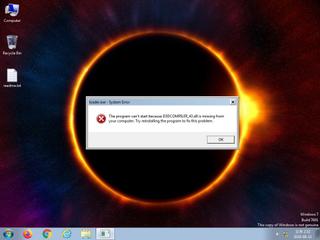
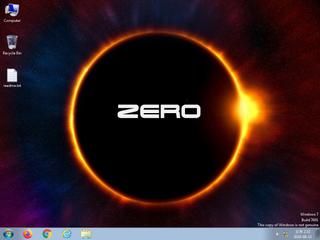
ScreenShot
| Created | 2024.08.11 15:47 | Machine | s1_win7_x6403 |
| Filename | loader.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 22 detected (AIDetectMalware, GameHack, malicious, moderate confidence, Unsafe, Vckm, Attribute, HighConfidence, JJ potentially unsafe, Artemis, Generic Reputation PUA, Detected, confidence) | ||
| md5 | fd5cebded11fb4fe38b5a1fe259414ae | ||
| sha256 | 04bf9303bcb11032a3e803ad4d11231b5ab6913edf38d58ea03f47180510550b | ||
| ssdeep | 49152:3bTcJn5/GD+lmAC8n68IONNXPXj3nje5m4RxkcU5d:9izeoYxk/5d | ||
| imphash | a7f9ed313fad44c20016bdaa2dceca77 | ||
| impfuzzy | 192:VmPeJ3+wh4Omk8aJrKsypIiR89PbG0jlXY:VmPe9TmyypIiR8I09Y | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 22 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Antivirus | Contains references to security software | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1400da0d0 InitializeCriticalSectionEx
0x1400da0d8 DeleteCriticalSection
0x1400da0e0 FormatMessageA
0x1400da0e8 LocalFree
0x1400da0f0 FreeLibrary
0x1400da0f8 VerifyVersionInfoW
0x1400da100 SetFileCompletionNotificationModes
0x1400da108 CloseThreadpoolIo
0x1400da110 CancelThreadpoolIo
0x1400da118 StartThreadpoolIo
0x1400da120 CreateThreadpoolIo
0x1400da128 GetOverlappedResult
0x1400da130 WriteFile
0x1400da138 ReadFile
0x1400da140 GetFileSizeEx
0x1400da148 CreateFileW
0x1400da150 OutputDebugStringW
0x1400da158 InitializeSListHead
0x1400da160 GetSystemTimeAsFileTime
0x1400da168 GetCurrentThreadId
0x1400da170 GetCurrentProcessId
0x1400da178 GetStartupInfoW
0x1400da180 SetUnhandledExceptionFilter
0x1400da188 UnhandledExceptionFilter
0x1400da190 IsDebuggerPresent
0x1400da198 RtlVirtualUnwind
0x1400da1a0 RtlLookupFunctionEntry
0x1400da1a8 RtlCaptureContext
0x1400da1b0 GetModuleHandleW
0x1400da1b8 CreateEventW
0x1400da1c0 WaitForSingleObjectEx
0x1400da1c8 ResetEvent
0x1400da1d0 SetEvent
0x1400da1d8 InitializeCriticalSectionAndSpinCount
0x1400da1e0 LeaveCriticalSection
0x1400da1e8 EnterCriticalSection
0x1400da1f0 InitOnceComplete
0x1400da1f8 InitOnceBeginInitialize
0x1400da200 GetLocaleInfoEx
0x1400da208 QueryPerformanceFrequency
0x1400da210 QueryPerformanceCounter
0x1400da218 VerSetConditionMask
0x1400da220 WideCharToMultiByte
0x1400da228 MultiByteToWideChar
0x1400da230 GlobalFree
0x1400da238 GlobalLock
0x1400da240 GlobalUnlock
0x1400da248 GlobalAlloc
0x1400da250 TerminateProcess
0x1400da258 ExitProcess
0x1400da260 GetCurrentProcess
0x1400da268 WaitForSingleObject
0x1400da270 GetLastError
0x1400da278 CloseHandle
0x1400da280 FindNextFileA
0x1400da288 FindFirstFileA
0x1400da290 GetTickCount64
0x1400da298 GetCurrentThread
0x1400da2a0 Sleep
0x1400da2a8 GetUserDefaultLocaleName
0x1400da2b0 LoadLibraryA
0x1400da2b8 GetProcAddress
0x1400da2c0 IsProcessorFeaturePresent
0x1400da2c8 GetModuleHandleA
0x1400da2d0 FormatMessageW
0x1400da2d8 FindClose
USER32.dll
0x1400da620 ShowWindow
0x1400da628 DestroyWindow
0x1400da630 CreateWindowExW
0x1400da638 RegisterClassExW
0x1400da640 UnregisterClassW
0x1400da648 UnregisterClassA
0x1400da650 PostQuitMessage
0x1400da658 DefWindowProcA
0x1400da660 PeekMessageA
0x1400da668 DispatchMessageA
0x1400da670 TranslateMessage
0x1400da678 LoadCursorA
0x1400da680 ScreenToClient
0x1400da688 ClientToScreen
0x1400da690 GetCursorPos
0x1400da698 SetCursor
0x1400da6a0 SetCursorPos
0x1400da6a8 GetSystemMetrics
0x1400da6b0 GetForegroundWindow
0x1400da6b8 IsWindowUnicode
0x1400da6c0 ReleaseCapture
0x1400da6c8 SetCapture
0x1400da6d0 GetCapture
0x1400da6d8 GetKeyState
0x1400da6e0 GetMessageExtraInfo
0x1400da6e8 TrackMouseEvent
0x1400da6f0 EmptyClipboard
0x1400da6f8 GetClipboardData
0x1400da700 UpdateWindow
0x1400da708 MoveWindow
0x1400da710 LoadIconA
0x1400da718 RegisterClassExA
0x1400da720 CreateWindowExA
0x1400da728 OpenClipboard
0x1400da730 GetWindowRect
0x1400da738 GetClientRect
0x1400da740 SetClipboardData
0x1400da748 CloseClipboard
ADVAPI32.dll
0x1400da000 RegQueryValueExA
0x1400da008 RegGetValueA
0x1400da010 RegCreateKeyExA
0x1400da018 RegSetValueExA
0x1400da020 RegOpenKeyExA
0x1400da028 RegCloseKey
0x1400da030 GetUserNameW
SHELL32.dll
0x1400da610 ShellExecuteExA
MSVCP140.dll
0x1400da2e8 ?sgetc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x1400da2f0 ?_Pninc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAPEADXZ
0x1400da2f8 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400da300 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x1400da308 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400da310 ??0?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x1400da318 ??1?$basic_istream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400da320 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x1400da328 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x1400da330 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x1400da338 _Mtx_init_in_situ
0x1400da340 _Mtx_destroy_in_situ
0x1400da348 ??0_Lockit@std@@QEAA@H@Z
0x1400da350 ??1_Lockit@std@@QEAA@XZ
0x1400da358 ??Bid@locale@std@@QEAA_KXZ
0x1400da360 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x1400da368 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x1400da370 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400da378 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400da380 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x1400da388 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x1400da390 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x1400da398 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x1400da3a0 ?_Fiopen@std@@YAPEAU_iobuf@@PEBDHH@Z
0x1400da3a8 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x1400da3b0 _Thrd_detach
0x1400da3b8 _Cnd_do_broadcast_at_thread_exit
0x1400da3c0 ?_Throw_C_error@std@@YAXH@Z
0x1400da3c8 ?_Throw_Cpp_error@std@@YAXH@Z
0x1400da3d0 ?_Xinvalid_argument@std@@YAXPEBD@Z
0x1400da3d8 ?__ExceptionPtrCreate@@YAXPEAX@Z
0x1400da3e0 ?__ExceptionPtrDestroy@@YAXPEAX@Z
0x1400da3e8 ?__ExceptionPtrCopy@@YAXPEAXPEBX@Z
0x1400da3f0 ?__ExceptionPtrAssign@@YAXPEAXPEBX@Z
0x1400da3f8 ?__ExceptionPtrToBool@@YA_NPEBX@Z
0x1400da400 ?__ExceptionPtrCurrentException@@YAXPEAX@Z
0x1400da408 ?__ExceptionPtrRethrow@@YAXPEBX@Z
0x1400da410 ?__ExceptionPtrCopyException@@YAXPEAXPEBX1@Z
0x1400da418 _Mtx_lock
0x1400da420 _Mtx_unlock
0x1400da428 _Cnd_init_in_situ
0x1400da430 _Cnd_destroy_in_situ
0x1400da438 _Cnd_wait
0x1400da440 _Cnd_broadcast
0x1400da448 ?_Schedule_chore@details@Concurrency@@YAHPEAU_Threadpool_chore@12@@Z
0x1400da450 ?_Release_chore@details@Concurrency@@YAXPEAU_Threadpool_chore@12@@Z
0x1400da458 ?_ReportUnobservedException@details@Concurrency@@YAXXZ
0x1400da460 ?GetCurrentThreadId@platform@details@Concurrency@@YAJXZ
0x1400da468 ?_Xbad_function_call@std@@YAXXZ
0x1400da470 ?_CallInContext@_ContextCallback@details@Concurrency@@QEBAXV?$function@$$A6AXXZ@std@@_N@Z
0x1400da478 ?_Reset@_ContextCallback@details@Concurrency@@AEAAXXZ
0x1400da480 ?_Assign@_ContextCallback@details@Concurrency@@AEAAXPEAX@Z
0x1400da488 ?_IsCurrentOriginSTA@_ContextCallback@details@Concurrency@@CA_NXZ
0x1400da490 ?_Capture@_ContextCallback@details@Concurrency@@AEAAXXZ
0x1400da498 ?ReportUnhandledError@_ExceptionHolder@details@Concurrency@@AEAAXXZ
0x1400da4a0 ??0task_continuation_context@Concurrency@@AEAA@XZ
0x1400da4a8 ?_LogScheduleTask@_TaskEventLogger@details@Concurrency@@QEAAX_N@Z
0x1400da4b0 ?_LogCancelTask@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4b8 ?_LogTaskCompleted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4c0 ?_LogTaskExecutionCompleted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4c8 ?_LogWorkItemStarted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4d0 ?_LogWorkItemCompleted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4d8 ?_Syserror_map@std@@YAPEBDH@Z
0x1400da4e0 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400da4e8 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400da4f0 ?_Xout_of_range@std@@YAXPEBD@Z
0x1400da4f8 ?_Xlength_error@std@@YAXPEBD@Z
0x1400da500 ?_Xbad_alloc@std@@YAXXZ
0x1400da508 ?_Winerror_map@std@@YAHH@Z
0x1400da510 ?sbumpc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x1400da518 ?classic@locale@std@@SAAEBV12@XZ
0x1400da520 ??0?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@IEAA@XZ
0x1400da528 ??1?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da530 ?_Pninc@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@IEAAPEA_WXZ
0x1400da538 ??1?$basic_ios@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da540 ?setstate@?$basic_ios@_WU?$char_traits@_W@std@@@std@@QEAAXH_N@Z
0x1400da548 ?imbue@?$basic_ios@_WU?$char_traits@_W@std@@@std@@QEAA?AVlocale@2@AEBV32@@Z
0x1400da550 ??5?$basic_istream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV01@AEA_K@Z
0x1400da558 ??6?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV01@_K@Z
0x1400da560 ??1?$basic_ostream@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da568 ??0?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAA@PEAV?$basic_streambuf@_WU?$char_traits@_W@std@@@1@_N@Z
0x1400da570 ?__ExceptionPtrCompare@@YA_NPEBX0@Z
0x1400da578 ?flush@?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV12@XZ
0x1400da580 ??0?$basic_ios@_WU?$char_traits@_W@std@@@std@@IEAA@XZ
0x1400da588 ??0?$basic_istream@_WU?$char_traits@_W@std@@@std@@QEAA@PEAV?$basic_streambuf@_WU?$char_traits@_W@std@@@1@_N@Z
0x1400da590 ??1?$basic_istream@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da598 ??5?$basic_istream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV01@AEAH@Z
0x1400da5a0 ?_Lock@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@UEAAXXZ
0x1400da5a8 ?_Unlock@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@UEAAXXZ
0x1400da5b0 ?imbue@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAXAEBVlocale@2@@Z
0x1400da5b8 ?setbuf@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAPEAV12@PEA_W_J@Z
0x1400da5c0 ?showmanyc@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAA_JXZ
0x1400da5c8 ?sync@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAHXZ
0x1400da5d0 ?uflow@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAGXZ
0x1400da5d8 ?xsgetn@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAA_JPEA_W_J@Z
0x1400da5e0 ?xsputn@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAA_JPEB_W_J@Z
0x1400da5e8 ?uncaught_exception@std@@YA_NXZ
0x1400da5f0 ?sputc@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@QEAAG_W@Z
0x1400da5f8 ?sputn@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@QEAA_JPEB_W_J@Z
0x1400da600 ?_Osfx@?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAAXXZ
CONCRT140.dll
0x1400da040 ?_Acquire@_ReentrantBlockingLock@details@Concurrency@@QEAAXXZ
0x1400da048 ?_Release@_ReentrantBlockingLock@details@Concurrency@@QEAAXXZ
0x1400da050 ??0_ReentrantBlockingLock@details@Concurrency@@QEAA@XZ
0x1400da058 ??1_ReentrantBlockingLock@details@Concurrency@@QEAA@XZ
IMM32.dll
0x1400da0a8 ImmReleaseContext
0x1400da0b0 ImmSetCompositionWindow
0x1400da0b8 ImmSetCandidateWindow
0x1400da0c0 ImmGetContext
D3DCOMPILER_43.dll
0x1400da098 D3DCompile
CRYPT32.dll
0x1400da068 CertFreeCertificateChain
0x1400da070 CertGetCertificateChain
0x1400da078 CertFreeCertificateContext
0x1400da080 CryptUnprotectMemory
0x1400da088 CertVerifyCertificateChainPolicy
crypt.dll
0x1400dab98 BCryptCloseAlgorithmProvider
0x1400daba0 BCryptGetProperty
0x1400daba8 BCryptOpenAlgorithmProvider
0x1400dabb0 BCryptFinishHash
0x1400dabb8 BCryptHashData
0x1400dabc0 BCryptCreateHash
0x1400dabc8 BCryptDestroyHash
WINHTTP.dll
0x1400da7e0 WinHttpAddRequestHeaders
0x1400da7e8 WinHttpOpenRequest
0x1400da7f0 WinHttpSetTimeouts
0x1400da7f8 WinHttpSendRequest
0x1400da800 WinHttpSetCredentials
0x1400da808 WinHttpQueryDataAvailable
0x1400da810 WinHttpWriteData
0x1400da818 WinHttpReadData
0x1400da820 WinHttpConnect
0x1400da828 WinHttpCloseHandle
0x1400da830 WinHttpSetOption
0x1400da838 WinHttpOpen
0x1400da840 WinHttpGetDefaultProxyConfiguration
0x1400da848 WinHttpSetStatusCallback
0x1400da850 WinHttpQueryOption
0x1400da858 WinHttpQueryAuthSchemes
0x1400da860 WinHttpReceiveResponse
0x1400da868 WinHttpQueryHeaders
0x1400da870 WinHttpGetIEProxyConfigForCurrentUser
0x1400da878 WinHttpGetProxyForUrl
d3d11.dll
0x1400dabd8 D3D11CreateDeviceAndSwapChain
VCRUNTIME140.dll
0x1400da758 __std_terminate
0x1400da760 __std_exception_copy
0x1400da768 __std_exception_destroy
0x1400da770 _CxxThrowException
0x1400da778 memchr
0x1400da780 memcmp
0x1400da788 memcpy
0x1400da790 memmove
0x1400da798 memset
0x1400da7a0 strstr
0x1400da7a8 _purecall
0x1400da7b0 __C_specific_handler
0x1400da7b8 __current_exception
0x1400da7c0 __current_exception_context
VCRUNTIME140_1.dll
0x1400da7d0 __CxxFrameHandler4
api-ms-win-crt-runtime-l1-1-0.dll
0x1400da9a8 abort
0x1400da9b0 _initialize_onexit_table
0x1400da9b8 _register_onexit_function
0x1400da9c0 _crt_atexit
0x1400da9c8 _configure_narrow_argv
0x1400da9d0 _cexit
0x1400da9d8 _seh_filter_exe
0x1400da9e0 _invalid_parameter_noinfo_noreturn
0x1400da9e8 _initterm_e
0x1400da9f0 _set_app_type
0x1400da9f8 _get_narrow_winmain_command_line
0x1400daa00 _errno
0x1400daa08 _beginthreadex
0x1400daa10 terminate
0x1400daa18 _initterm
0x1400daa20 _initialize_narrow_environment
0x1400daa28 exit
0x1400daa30 _register_thread_local_exe_atexit_callback
0x1400daa38 _c_exit
0x1400daa40 _exit
api-ms-win-crt-string-l1-1-0.dll
0x1400dab28 strncmp
0x1400dab30 isalpha
0x1400dab38 isdigit
0x1400dab40 wcsnlen
0x1400dab48 strnlen
0x1400dab50 strncpy
0x1400dab58 iswspace
0x1400dab60 strcmp
api-ms-win-crt-stdio-l1-1-0.dll
0x1400daa50 __p__commode
0x1400daa58 feof
0x1400daa60 ferror
0x1400daa68 fputc
0x1400daa70 fgetpos
0x1400daa78 fgetc
0x1400daa80 fflush
0x1400daa88 fread
0x1400daa90 fsetpos
0x1400daa98 _get_stream_buffer_pointers
0x1400daaa0 _set_fmode
0x1400daaa8 __acrt_iob_func
0x1400daab0 __stdio_common_vswprintf_s
0x1400daab8 __stdio_common_vsscanf
0x1400daac0 __stdio_common_vsprintf
0x1400daac8 __stdio_common_vfprintf
0x1400daad0 ftell
0x1400daad8 fseek
0x1400daae0 _wfopen
0x1400daae8 _fseeki64
0x1400daaf0 __stdio_common_vsnwprintf_s
0x1400daaf8 fclose
0x1400dab00 __stdio_common_vsprintf_s
0x1400dab08 fwrite
0x1400dab10 ungetc
0x1400dab18 setvbuf
api-ms-win-crt-heap-l1-1-0.dll
0x1400da900 _callnewh
0x1400da908 free
0x1400da910 malloc
0x1400da918 realloc
0x1400da920 _set_new_mode
api-ms-win-crt-convert-l1-1-0.dll
0x1400da888 _wcstod_l
0x1400da890 strtol
0x1400da898 wcstombs_s
0x1400da8a0 _i64tow_s
0x1400da8a8 wcstol
0x1400da8b0 _ui64tow_s
0x1400da8b8 _i64toa_s
0x1400da8c0 _ui64toa_s
api-ms-win-crt-filesystem-l1-1-0.dll
0x1400da8d0 _access_s
0x1400da8d8 remove
0x1400da8e0 _unlock_file
0x1400da8e8 _mkdir
0x1400da8f0 _lock_file
api-ms-win-crt-time-l1-1-0.dll
0x1400dab70 _time64
0x1400dab78 _localtime64
api-ms-win-crt-math-l1-1-0.dll
0x1400da958 powf
0x1400da960 cosf
0x1400da968 ldexp
0x1400da970 sqrtf
0x1400da978 fmodf
0x1400da980 ceilf
0x1400da988 sinf
0x1400da990 acosf
0x1400da998 __setusermatherr
api-ms-win-crt-utility-l1-1-0.dll
0x1400dab88 qsort
api-ms-win-crt-locale-l1-1-0.dll
0x1400da930 __pctype_func
0x1400da938 _create_locale
0x1400da940 _free_locale
0x1400da948 _configthreadlocale
EAT(Export Address Table) is none
KERNEL32.dll
0x1400da0d0 InitializeCriticalSectionEx
0x1400da0d8 DeleteCriticalSection
0x1400da0e0 FormatMessageA
0x1400da0e8 LocalFree
0x1400da0f0 FreeLibrary
0x1400da0f8 VerifyVersionInfoW
0x1400da100 SetFileCompletionNotificationModes
0x1400da108 CloseThreadpoolIo
0x1400da110 CancelThreadpoolIo
0x1400da118 StartThreadpoolIo
0x1400da120 CreateThreadpoolIo
0x1400da128 GetOverlappedResult
0x1400da130 WriteFile
0x1400da138 ReadFile
0x1400da140 GetFileSizeEx
0x1400da148 CreateFileW
0x1400da150 OutputDebugStringW
0x1400da158 InitializeSListHead
0x1400da160 GetSystemTimeAsFileTime
0x1400da168 GetCurrentThreadId
0x1400da170 GetCurrentProcessId
0x1400da178 GetStartupInfoW
0x1400da180 SetUnhandledExceptionFilter
0x1400da188 UnhandledExceptionFilter
0x1400da190 IsDebuggerPresent
0x1400da198 RtlVirtualUnwind
0x1400da1a0 RtlLookupFunctionEntry
0x1400da1a8 RtlCaptureContext
0x1400da1b0 GetModuleHandleW
0x1400da1b8 CreateEventW
0x1400da1c0 WaitForSingleObjectEx
0x1400da1c8 ResetEvent
0x1400da1d0 SetEvent
0x1400da1d8 InitializeCriticalSectionAndSpinCount
0x1400da1e0 LeaveCriticalSection
0x1400da1e8 EnterCriticalSection
0x1400da1f0 InitOnceComplete
0x1400da1f8 InitOnceBeginInitialize
0x1400da200 GetLocaleInfoEx
0x1400da208 QueryPerformanceFrequency
0x1400da210 QueryPerformanceCounter
0x1400da218 VerSetConditionMask
0x1400da220 WideCharToMultiByte
0x1400da228 MultiByteToWideChar
0x1400da230 GlobalFree
0x1400da238 GlobalLock
0x1400da240 GlobalUnlock
0x1400da248 GlobalAlloc
0x1400da250 TerminateProcess
0x1400da258 ExitProcess
0x1400da260 GetCurrentProcess
0x1400da268 WaitForSingleObject
0x1400da270 GetLastError
0x1400da278 CloseHandle
0x1400da280 FindNextFileA
0x1400da288 FindFirstFileA
0x1400da290 GetTickCount64
0x1400da298 GetCurrentThread
0x1400da2a0 Sleep
0x1400da2a8 GetUserDefaultLocaleName
0x1400da2b0 LoadLibraryA
0x1400da2b8 GetProcAddress
0x1400da2c0 IsProcessorFeaturePresent
0x1400da2c8 GetModuleHandleA
0x1400da2d0 FormatMessageW
0x1400da2d8 FindClose
USER32.dll
0x1400da620 ShowWindow
0x1400da628 DestroyWindow
0x1400da630 CreateWindowExW
0x1400da638 RegisterClassExW
0x1400da640 UnregisterClassW
0x1400da648 UnregisterClassA
0x1400da650 PostQuitMessage
0x1400da658 DefWindowProcA
0x1400da660 PeekMessageA
0x1400da668 DispatchMessageA
0x1400da670 TranslateMessage
0x1400da678 LoadCursorA
0x1400da680 ScreenToClient
0x1400da688 ClientToScreen
0x1400da690 GetCursorPos
0x1400da698 SetCursor
0x1400da6a0 SetCursorPos
0x1400da6a8 GetSystemMetrics
0x1400da6b0 GetForegroundWindow
0x1400da6b8 IsWindowUnicode
0x1400da6c0 ReleaseCapture
0x1400da6c8 SetCapture
0x1400da6d0 GetCapture
0x1400da6d8 GetKeyState
0x1400da6e0 GetMessageExtraInfo
0x1400da6e8 TrackMouseEvent
0x1400da6f0 EmptyClipboard
0x1400da6f8 GetClipboardData
0x1400da700 UpdateWindow
0x1400da708 MoveWindow
0x1400da710 LoadIconA
0x1400da718 RegisterClassExA
0x1400da720 CreateWindowExA
0x1400da728 OpenClipboard
0x1400da730 GetWindowRect
0x1400da738 GetClientRect
0x1400da740 SetClipboardData
0x1400da748 CloseClipboard
ADVAPI32.dll
0x1400da000 RegQueryValueExA
0x1400da008 RegGetValueA
0x1400da010 RegCreateKeyExA
0x1400da018 RegSetValueExA
0x1400da020 RegOpenKeyExA
0x1400da028 RegCloseKey
0x1400da030 GetUserNameW
SHELL32.dll
0x1400da610 ShellExecuteExA
MSVCP140.dll
0x1400da2e8 ?sgetc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x1400da2f0 ?_Pninc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAPEADXZ
0x1400da2f8 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400da300 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x1400da308 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400da310 ??0?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x1400da318 ??1?$basic_istream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400da320 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x1400da328 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x1400da330 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x1400da338 _Mtx_init_in_situ
0x1400da340 _Mtx_destroy_in_situ
0x1400da348 ??0_Lockit@std@@QEAA@H@Z
0x1400da350 ??1_Lockit@std@@QEAA@XZ
0x1400da358 ??Bid@locale@std@@QEAA_KXZ
0x1400da360 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x1400da368 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x1400da370 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400da378 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400da380 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x1400da388 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x1400da390 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x1400da398 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x1400da3a0 ?_Fiopen@std@@YAPEAU_iobuf@@PEBDHH@Z
0x1400da3a8 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x1400da3b0 _Thrd_detach
0x1400da3b8 _Cnd_do_broadcast_at_thread_exit
0x1400da3c0 ?_Throw_C_error@std@@YAXH@Z
0x1400da3c8 ?_Throw_Cpp_error@std@@YAXH@Z
0x1400da3d0 ?_Xinvalid_argument@std@@YAXPEBD@Z
0x1400da3d8 ?__ExceptionPtrCreate@@YAXPEAX@Z
0x1400da3e0 ?__ExceptionPtrDestroy@@YAXPEAX@Z
0x1400da3e8 ?__ExceptionPtrCopy@@YAXPEAXPEBX@Z
0x1400da3f0 ?__ExceptionPtrAssign@@YAXPEAXPEBX@Z
0x1400da3f8 ?__ExceptionPtrToBool@@YA_NPEBX@Z
0x1400da400 ?__ExceptionPtrCurrentException@@YAXPEAX@Z
0x1400da408 ?__ExceptionPtrRethrow@@YAXPEBX@Z
0x1400da410 ?__ExceptionPtrCopyException@@YAXPEAXPEBX1@Z
0x1400da418 _Mtx_lock
0x1400da420 _Mtx_unlock
0x1400da428 _Cnd_init_in_situ
0x1400da430 _Cnd_destroy_in_situ
0x1400da438 _Cnd_wait
0x1400da440 _Cnd_broadcast
0x1400da448 ?_Schedule_chore@details@Concurrency@@YAHPEAU_Threadpool_chore@12@@Z
0x1400da450 ?_Release_chore@details@Concurrency@@YAXPEAU_Threadpool_chore@12@@Z
0x1400da458 ?_ReportUnobservedException@details@Concurrency@@YAXXZ
0x1400da460 ?GetCurrentThreadId@platform@details@Concurrency@@YAJXZ
0x1400da468 ?_Xbad_function_call@std@@YAXXZ
0x1400da470 ?_CallInContext@_ContextCallback@details@Concurrency@@QEBAXV?$function@$$A6AXXZ@std@@_N@Z
0x1400da478 ?_Reset@_ContextCallback@details@Concurrency@@AEAAXXZ
0x1400da480 ?_Assign@_ContextCallback@details@Concurrency@@AEAAXPEAX@Z
0x1400da488 ?_IsCurrentOriginSTA@_ContextCallback@details@Concurrency@@CA_NXZ
0x1400da490 ?_Capture@_ContextCallback@details@Concurrency@@AEAAXXZ
0x1400da498 ?ReportUnhandledError@_ExceptionHolder@details@Concurrency@@AEAAXXZ
0x1400da4a0 ??0task_continuation_context@Concurrency@@AEAA@XZ
0x1400da4a8 ?_LogScheduleTask@_TaskEventLogger@details@Concurrency@@QEAAX_N@Z
0x1400da4b0 ?_LogCancelTask@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4b8 ?_LogTaskCompleted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4c0 ?_LogTaskExecutionCompleted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4c8 ?_LogWorkItemStarted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4d0 ?_LogWorkItemCompleted@_TaskEventLogger@details@Concurrency@@QEAAXXZ
0x1400da4d8 ?_Syserror_map@std@@YAPEBDH@Z
0x1400da4e0 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400da4e8 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400da4f0 ?_Xout_of_range@std@@YAXPEBD@Z
0x1400da4f8 ?_Xlength_error@std@@YAXPEBD@Z
0x1400da500 ?_Xbad_alloc@std@@YAXXZ
0x1400da508 ?_Winerror_map@std@@YAHH@Z
0x1400da510 ?sbumpc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x1400da518 ?classic@locale@std@@SAAEBV12@XZ
0x1400da520 ??0?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@IEAA@XZ
0x1400da528 ??1?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da530 ?_Pninc@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@IEAAPEA_WXZ
0x1400da538 ??1?$basic_ios@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da540 ?setstate@?$basic_ios@_WU?$char_traits@_W@std@@@std@@QEAAXH_N@Z
0x1400da548 ?imbue@?$basic_ios@_WU?$char_traits@_W@std@@@std@@QEAA?AVlocale@2@AEBV32@@Z
0x1400da550 ??5?$basic_istream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV01@AEA_K@Z
0x1400da558 ??6?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV01@_K@Z
0x1400da560 ??1?$basic_ostream@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da568 ??0?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAA@PEAV?$basic_streambuf@_WU?$char_traits@_W@std@@@1@_N@Z
0x1400da570 ?__ExceptionPtrCompare@@YA_NPEBX0@Z
0x1400da578 ?flush@?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV12@XZ
0x1400da580 ??0?$basic_ios@_WU?$char_traits@_W@std@@@std@@IEAA@XZ
0x1400da588 ??0?$basic_istream@_WU?$char_traits@_W@std@@@std@@QEAA@PEAV?$basic_streambuf@_WU?$char_traits@_W@std@@@1@_N@Z
0x1400da590 ??1?$basic_istream@_WU?$char_traits@_W@std@@@std@@UEAA@XZ
0x1400da598 ??5?$basic_istream@_WU?$char_traits@_W@std@@@std@@QEAAAEAV01@AEAH@Z
0x1400da5a0 ?_Lock@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@UEAAXXZ
0x1400da5a8 ?_Unlock@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@UEAAXXZ
0x1400da5b0 ?imbue@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAXAEBVlocale@2@@Z
0x1400da5b8 ?setbuf@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAPEAV12@PEA_W_J@Z
0x1400da5c0 ?showmanyc@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAA_JXZ
0x1400da5c8 ?sync@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAHXZ
0x1400da5d0 ?uflow@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAAGXZ
0x1400da5d8 ?xsgetn@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAA_JPEA_W_J@Z
0x1400da5e0 ?xsputn@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@MEAA_JPEB_W_J@Z
0x1400da5e8 ?uncaught_exception@std@@YA_NXZ
0x1400da5f0 ?sputc@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@QEAAG_W@Z
0x1400da5f8 ?sputn@?$basic_streambuf@_WU?$char_traits@_W@std@@@std@@QEAA_JPEB_W_J@Z
0x1400da600 ?_Osfx@?$basic_ostream@_WU?$char_traits@_W@std@@@std@@QEAAXXZ
CONCRT140.dll
0x1400da040 ?_Acquire@_ReentrantBlockingLock@details@Concurrency@@QEAAXXZ
0x1400da048 ?_Release@_ReentrantBlockingLock@details@Concurrency@@QEAAXXZ
0x1400da050 ??0_ReentrantBlockingLock@details@Concurrency@@QEAA@XZ
0x1400da058 ??1_ReentrantBlockingLock@details@Concurrency@@QEAA@XZ
IMM32.dll
0x1400da0a8 ImmReleaseContext
0x1400da0b0 ImmSetCompositionWindow
0x1400da0b8 ImmSetCandidateWindow
0x1400da0c0 ImmGetContext
D3DCOMPILER_43.dll
0x1400da098 D3DCompile
CRYPT32.dll
0x1400da068 CertFreeCertificateChain
0x1400da070 CertGetCertificateChain
0x1400da078 CertFreeCertificateContext
0x1400da080 CryptUnprotectMemory
0x1400da088 CertVerifyCertificateChainPolicy
crypt.dll
0x1400dab98 BCryptCloseAlgorithmProvider
0x1400daba0 BCryptGetProperty
0x1400daba8 BCryptOpenAlgorithmProvider
0x1400dabb0 BCryptFinishHash
0x1400dabb8 BCryptHashData
0x1400dabc0 BCryptCreateHash
0x1400dabc8 BCryptDestroyHash
WINHTTP.dll
0x1400da7e0 WinHttpAddRequestHeaders
0x1400da7e8 WinHttpOpenRequest
0x1400da7f0 WinHttpSetTimeouts
0x1400da7f8 WinHttpSendRequest
0x1400da800 WinHttpSetCredentials
0x1400da808 WinHttpQueryDataAvailable
0x1400da810 WinHttpWriteData
0x1400da818 WinHttpReadData
0x1400da820 WinHttpConnect
0x1400da828 WinHttpCloseHandle
0x1400da830 WinHttpSetOption
0x1400da838 WinHttpOpen
0x1400da840 WinHttpGetDefaultProxyConfiguration
0x1400da848 WinHttpSetStatusCallback
0x1400da850 WinHttpQueryOption
0x1400da858 WinHttpQueryAuthSchemes
0x1400da860 WinHttpReceiveResponse
0x1400da868 WinHttpQueryHeaders
0x1400da870 WinHttpGetIEProxyConfigForCurrentUser
0x1400da878 WinHttpGetProxyForUrl
d3d11.dll
0x1400dabd8 D3D11CreateDeviceAndSwapChain
VCRUNTIME140.dll
0x1400da758 __std_terminate
0x1400da760 __std_exception_copy
0x1400da768 __std_exception_destroy
0x1400da770 _CxxThrowException
0x1400da778 memchr
0x1400da780 memcmp
0x1400da788 memcpy
0x1400da790 memmove
0x1400da798 memset
0x1400da7a0 strstr
0x1400da7a8 _purecall
0x1400da7b0 __C_specific_handler
0x1400da7b8 __current_exception
0x1400da7c0 __current_exception_context
VCRUNTIME140_1.dll
0x1400da7d0 __CxxFrameHandler4
api-ms-win-crt-runtime-l1-1-0.dll
0x1400da9a8 abort
0x1400da9b0 _initialize_onexit_table
0x1400da9b8 _register_onexit_function
0x1400da9c0 _crt_atexit
0x1400da9c8 _configure_narrow_argv
0x1400da9d0 _cexit
0x1400da9d8 _seh_filter_exe
0x1400da9e0 _invalid_parameter_noinfo_noreturn
0x1400da9e8 _initterm_e
0x1400da9f0 _set_app_type
0x1400da9f8 _get_narrow_winmain_command_line
0x1400daa00 _errno
0x1400daa08 _beginthreadex
0x1400daa10 terminate
0x1400daa18 _initterm
0x1400daa20 _initialize_narrow_environment
0x1400daa28 exit
0x1400daa30 _register_thread_local_exe_atexit_callback
0x1400daa38 _c_exit
0x1400daa40 _exit
api-ms-win-crt-string-l1-1-0.dll
0x1400dab28 strncmp
0x1400dab30 isalpha
0x1400dab38 isdigit
0x1400dab40 wcsnlen
0x1400dab48 strnlen
0x1400dab50 strncpy
0x1400dab58 iswspace
0x1400dab60 strcmp
api-ms-win-crt-stdio-l1-1-0.dll
0x1400daa50 __p__commode
0x1400daa58 feof
0x1400daa60 ferror
0x1400daa68 fputc
0x1400daa70 fgetpos
0x1400daa78 fgetc
0x1400daa80 fflush
0x1400daa88 fread
0x1400daa90 fsetpos
0x1400daa98 _get_stream_buffer_pointers
0x1400daaa0 _set_fmode
0x1400daaa8 __acrt_iob_func
0x1400daab0 __stdio_common_vswprintf_s
0x1400daab8 __stdio_common_vsscanf
0x1400daac0 __stdio_common_vsprintf
0x1400daac8 __stdio_common_vfprintf
0x1400daad0 ftell
0x1400daad8 fseek
0x1400daae0 _wfopen
0x1400daae8 _fseeki64
0x1400daaf0 __stdio_common_vsnwprintf_s
0x1400daaf8 fclose
0x1400dab00 __stdio_common_vsprintf_s
0x1400dab08 fwrite
0x1400dab10 ungetc
0x1400dab18 setvbuf
api-ms-win-crt-heap-l1-1-0.dll
0x1400da900 _callnewh
0x1400da908 free
0x1400da910 malloc
0x1400da918 realloc
0x1400da920 _set_new_mode
api-ms-win-crt-convert-l1-1-0.dll
0x1400da888 _wcstod_l
0x1400da890 strtol
0x1400da898 wcstombs_s
0x1400da8a0 _i64tow_s
0x1400da8a8 wcstol
0x1400da8b0 _ui64tow_s
0x1400da8b8 _i64toa_s
0x1400da8c0 _ui64toa_s
api-ms-win-crt-filesystem-l1-1-0.dll
0x1400da8d0 _access_s
0x1400da8d8 remove
0x1400da8e0 _unlock_file
0x1400da8e8 _mkdir
0x1400da8f0 _lock_file
api-ms-win-crt-time-l1-1-0.dll
0x1400dab70 _time64
0x1400dab78 _localtime64
api-ms-win-crt-math-l1-1-0.dll
0x1400da958 powf
0x1400da960 cosf
0x1400da968 ldexp
0x1400da970 sqrtf
0x1400da978 fmodf
0x1400da980 ceilf
0x1400da988 sinf
0x1400da990 acosf
0x1400da998 __setusermatherr
api-ms-win-crt-utility-l1-1-0.dll
0x1400dab88 qsort
api-ms-win-crt-locale-l1-1-0.dll
0x1400da930 __pctype_func
0x1400da938 _create_locale
0x1400da940 _free_locale
0x1400da948 _configthreadlocale
EAT(Export Address Table) is none