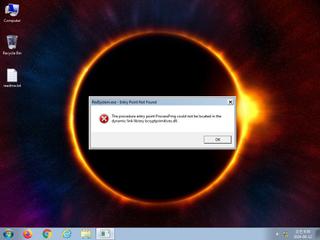
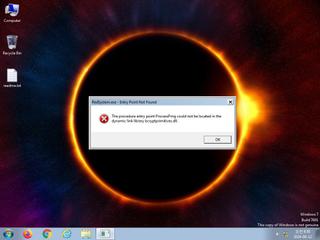
ScreenShot
| Created | 2024.08.12 09:12 | Machine | s1_win7_x6403 |
| Filename | RedSystem.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 48 detected (AIDetectMalware, Strab, malicious, high confidence, score, Jaik, Unsafe, Save, Attribute, HighConfidence, Artemis, MalwareX, CLOUD, mdwuw, Static AI, Suspicious PE, Detected, ai score=80, Wacatac, ZexaF, LqW@a4fwcje, MachineLearning, Anomalous, Chgt, R002H07H824, Nsmw, 3nxr4NvwG2I, susgen, confidence, B9nj) | ||
| md5 | 933f2db7b8ded6946f35720a366e7b14 | ||
| sha256 | ba8d4df86924743be143d569ac06b8a1b1d7e2c554720e7f31126a0db04c3daa | ||
| ssdeep | 12288:2LiIDxg9D7D8zxHk4la1v2mCVsNgSB+EKn6fGPR4Q5xx:2LiIlg9D7Doxk4ECaN3QEKbPR4Q5 | ||
| imphash | 1b27045adbbf28f4d991e6f3c9541cfa | ||
| impfuzzy | 48:kxosqtb/nRSE9Ae1rXI8OrRau9unRD/bbwZmOQEjSOlBoBMLSQMA:kxozb/UE+e1rXItrRau6RzfIjSOqQ | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 48 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | This executable has a PDB path |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
cryptprimitives.dll
0x4320c8 ProcessPrng
api-ms-win-core-synch-l1-2-0.dll
0x432024 WakeByAddressAll
0x432028 WaitOnAddress
0x43202c WakeByAddressSingle
ntdll.dll
0x432208 RtlNtStatusToDosError
0x43220c RtlUnwind
0x432210 RtlGetVersion
0x432214 RtlCaptureContext
0x432218 NtQueryInformationProcess
0x43221c NtQuerySystemInformation
0x432220 NtWriteFile
kernel32.dll
0x4320d0 GetComputerNameExW
0x4320d4 LoadLibraryExW
0x4320d8 TlsFree
0x4320dc TlsSetValue
0x4320e0 TlsGetValue
0x4320e4 TlsAlloc
0x4320e8 K32GetPerformanceInfo
0x4320ec DeleteCriticalSection
0x4320f0 GlobalMemoryStatusEx
0x4320f4 RaiseException
0x4320f8 InitializeCriticalSectionAndSpinCount
0x4320fc ReadProcessMemory
0x432100 HeapAlloc
0x432104 GetProcessIoCounters
0x432108 GetSystemTimes
0x43210c LocalFree
0x432110 LoadLibraryExA
0x432114 FreeLibrary
0x432118 GetLastError
0x43211c EncodePointer
0x432120 WaitForSingleObject
0x432124 IsProcessorFeaturePresent
0x432128 FormatMessageW
0x43212c OpenProcess
0x432130 SetUnhandledExceptionFilter
0x432134 AddVectoredExceptionHandler
0x432138 SetThreadStackGuarantee
0x43213c GetCurrentThread
0x432140 SwitchToThread
0x432144 CreateWaitableTimerExW
0x432148 SetWaitableTimer
0x43214c Sleep
0x432150 QueryPerformanceCounter
0x432154 ReleaseMutex
0x432158 SetLastError
0x43215c GetCurrentDirectoryW
0x432160 GetEnvironmentVariableW
0x432164 UnhandledExceptionFilter
0x432168 SetFileInformationByHandle
0x43216c IsDebuggerPresent
0x432170 InitializeSListHead
0x432174 GetSystemTimeAsFileTime
0x432178 GetCurrentThreadId
0x43217c LoadLibraryA
0x432180 GetProcAddress
0x432184 GetCurrentProcess
0x432188 VirtualProtectEx
0x43218c HeapFree
0x432190 WriteProcessMemory
0x432194 VirtualProtect
0x432198 VirtualAlloc
0x43219c GetProcessTimes
0x4321a0 GetStdHandle
0x4321a4 CreateFileW
0x4321a8 CloseHandle
0x4321ac TerminateProcess
0x4321b0 GetSystemTimePreciseAsFileTime
0x4321b4 HeapReAlloc
0x4321b8 WaitForSingleObjectEx
0x4321bc lstrlenW
0x4321c0 CreateMutexA
0x4321c4 FindClose
0x4321c8 GetFileInformationByHandle
0x4321cc GetFileInformationByHandleEx
0x4321d0 FindFirstFileW
0x4321d4 GetConsoleMode
0x4321d8 GetCurrentProcessId
0x4321dc GetModuleHandleW
0x4321e0 ExitProcess
0x4321e4 MultiByteToWideChar
0x4321e8 WriteConsoleW
0x4321ec CreateThread
0x4321f0 GetFullPathNameW
0x4321f4 GetModuleHandleA
0x4321f8 GetSystemInfo
0x4321fc VirtualQueryEx
0x432200 GetProcessHeap
advapi32.dll
0x432000 IsValidSid
0x432004 RegOpenKeyExW
0x432008 RegQueryValueExW
0x43200c GetLengthSid
0x432010 GetTokenInformation
0x432014 OpenProcessToken
0x432018 CopySid
0x43201c RegCloseKey
pdh.dll
0x432238 PdhGetFormattedCounterValue
0x43223c PdhOpenQueryA
0x432240 PdhRemoveCounter
0x432244 PdhAddEnglishCounterW
0x432248 PdhCloseQuery
0x43224c PdhCollectQueryData
powrprof.dll
0x432254 CallNtPowerInformation
psapi.dll
0x43225c GetProcessMemoryInfo
0x432260 GetModuleFileNameExW
shell32.dll
0x432268 CommandLineToArgvW
oleaut32.dll
0x432228 GetErrorInfo
0x43222c SysFreeString
0x432230 SysStringLen
api-ms-win-crt-heap-l1-1-0.dll
0x432034 calloc
0x432038 malloc
0x43203c free
0x432040 _set_new_mode
api-ms-win-crt-string-l1-1-0.dll
0x4320b8 wcslen
0x4320bc wcsncmp
0x4320c0 strcpy_s
api-ms-win-crt-runtime-l1-1-0.dll
0x432058 terminate
0x43205c _initialize_onexit_table
0x432060 _register_onexit_function
0x432064 _controlfp_s
0x432068 _register_thread_local_exe_atexit_callback
0x43206c _cexit
0x432070 __p___argv
0x432074 __p___argc
0x432078 abort
0x43207c _exit
0x432080 exit
0x432084 _initterm_e
0x432088 _c_exit
0x43208c _get_initial_narrow_environment
0x432090 _initialize_narrow_environment
0x432094 _configure_narrow_argv
0x432098 _crt_atexit
0x43209c _set_app_type
0x4320a0 _seh_filter_exe
0x4320a4 _initterm
api-ms-win-crt-math-l1-1-0.dll
0x432050 __setusermatherr
api-ms-win-crt-stdio-l1-1-0.dll
0x4320ac __p__commode
0x4320b0 _set_fmode
api-ms-win-crt-locale-l1-1-0.dll
0x432048 _configthreadlocale
EAT(Export Address Table) is none
cryptprimitives.dll
0x4320c8 ProcessPrng
api-ms-win-core-synch-l1-2-0.dll
0x432024 WakeByAddressAll
0x432028 WaitOnAddress
0x43202c WakeByAddressSingle
ntdll.dll
0x432208 RtlNtStatusToDosError
0x43220c RtlUnwind
0x432210 RtlGetVersion
0x432214 RtlCaptureContext
0x432218 NtQueryInformationProcess
0x43221c NtQuerySystemInformation
0x432220 NtWriteFile
kernel32.dll
0x4320d0 GetComputerNameExW
0x4320d4 LoadLibraryExW
0x4320d8 TlsFree
0x4320dc TlsSetValue
0x4320e0 TlsGetValue
0x4320e4 TlsAlloc
0x4320e8 K32GetPerformanceInfo
0x4320ec DeleteCriticalSection
0x4320f0 GlobalMemoryStatusEx
0x4320f4 RaiseException
0x4320f8 InitializeCriticalSectionAndSpinCount
0x4320fc ReadProcessMemory
0x432100 HeapAlloc
0x432104 GetProcessIoCounters
0x432108 GetSystemTimes
0x43210c LocalFree
0x432110 LoadLibraryExA
0x432114 FreeLibrary
0x432118 GetLastError
0x43211c EncodePointer
0x432120 WaitForSingleObject
0x432124 IsProcessorFeaturePresent
0x432128 FormatMessageW
0x43212c OpenProcess
0x432130 SetUnhandledExceptionFilter
0x432134 AddVectoredExceptionHandler
0x432138 SetThreadStackGuarantee
0x43213c GetCurrentThread
0x432140 SwitchToThread
0x432144 CreateWaitableTimerExW
0x432148 SetWaitableTimer
0x43214c Sleep
0x432150 QueryPerformanceCounter
0x432154 ReleaseMutex
0x432158 SetLastError
0x43215c GetCurrentDirectoryW
0x432160 GetEnvironmentVariableW
0x432164 UnhandledExceptionFilter
0x432168 SetFileInformationByHandle
0x43216c IsDebuggerPresent
0x432170 InitializeSListHead
0x432174 GetSystemTimeAsFileTime
0x432178 GetCurrentThreadId
0x43217c LoadLibraryA
0x432180 GetProcAddress
0x432184 GetCurrentProcess
0x432188 VirtualProtectEx
0x43218c HeapFree
0x432190 WriteProcessMemory
0x432194 VirtualProtect
0x432198 VirtualAlloc
0x43219c GetProcessTimes
0x4321a0 GetStdHandle
0x4321a4 CreateFileW
0x4321a8 CloseHandle
0x4321ac TerminateProcess
0x4321b0 GetSystemTimePreciseAsFileTime
0x4321b4 HeapReAlloc
0x4321b8 WaitForSingleObjectEx
0x4321bc lstrlenW
0x4321c0 CreateMutexA
0x4321c4 FindClose
0x4321c8 GetFileInformationByHandle
0x4321cc GetFileInformationByHandleEx
0x4321d0 FindFirstFileW
0x4321d4 GetConsoleMode
0x4321d8 GetCurrentProcessId
0x4321dc GetModuleHandleW
0x4321e0 ExitProcess
0x4321e4 MultiByteToWideChar
0x4321e8 WriteConsoleW
0x4321ec CreateThread
0x4321f0 GetFullPathNameW
0x4321f4 GetModuleHandleA
0x4321f8 GetSystemInfo
0x4321fc VirtualQueryEx
0x432200 GetProcessHeap
advapi32.dll
0x432000 IsValidSid
0x432004 RegOpenKeyExW
0x432008 RegQueryValueExW
0x43200c GetLengthSid
0x432010 GetTokenInformation
0x432014 OpenProcessToken
0x432018 CopySid
0x43201c RegCloseKey
pdh.dll
0x432238 PdhGetFormattedCounterValue
0x43223c PdhOpenQueryA
0x432240 PdhRemoveCounter
0x432244 PdhAddEnglishCounterW
0x432248 PdhCloseQuery
0x43224c PdhCollectQueryData
powrprof.dll
0x432254 CallNtPowerInformation
psapi.dll
0x43225c GetProcessMemoryInfo
0x432260 GetModuleFileNameExW
shell32.dll
0x432268 CommandLineToArgvW
oleaut32.dll
0x432228 GetErrorInfo
0x43222c SysFreeString
0x432230 SysStringLen
api-ms-win-crt-heap-l1-1-0.dll
0x432034 calloc
0x432038 malloc
0x43203c free
0x432040 _set_new_mode
api-ms-win-crt-string-l1-1-0.dll
0x4320b8 wcslen
0x4320bc wcsncmp
0x4320c0 strcpy_s
api-ms-win-crt-runtime-l1-1-0.dll
0x432058 terminate
0x43205c _initialize_onexit_table
0x432060 _register_onexit_function
0x432064 _controlfp_s
0x432068 _register_thread_local_exe_atexit_callback
0x43206c _cexit
0x432070 __p___argv
0x432074 __p___argc
0x432078 abort
0x43207c _exit
0x432080 exit
0x432084 _initterm_e
0x432088 _c_exit
0x43208c _get_initial_narrow_environment
0x432090 _initialize_narrow_environment
0x432094 _configure_narrow_argv
0x432098 _crt_atexit
0x43209c _set_app_type
0x4320a0 _seh_filter_exe
0x4320a4 _initterm
api-ms-win-crt-math-l1-1-0.dll
0x432050 __setusermatherr
api-ms-win-crt-stdio-l1-1-0.dll
0x4320ac __p__commode
0x4320b0 _set_fmode
api-ms-win-crt-locale-l1-1-0.dll
0x432048 _configthreadlocale
EAT(Export Address Table) is none