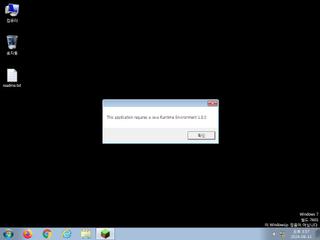
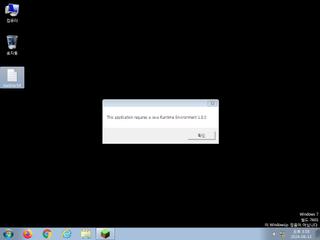
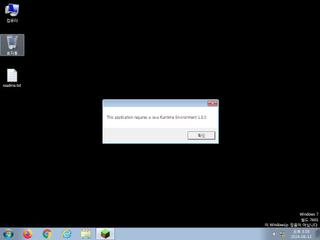
ScreenShot
| Created | 2024.08.13 16:00 | Machine | s1_win7_x6401 |
| Filename | NursultanClient.exe | ||
| Type | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 14 detected (AIDetectMalware, Unsafe, Crysan, Detected, ABRisk, BBZM, susgen, PossibleThreat) | ||
| md5 | b3d8b18d332153db164df8b55c3272a4 | ||
| sha256 | 00caadb35b55b93801f0a7a113b1c4da81acc4faecdb0daa28f811ac051da0cc | ||
| ssdeep | 49152:cXDCFN+WmdNxa2RTPokBMyHJWGs8FaRMqu3XCqRq8stcpVk4JobxJ17IxRYbwPm7:cXDXW8bTBrHJWGs2NyqeoNE/7SRYY2 | ||
| imphash | 6011984d7c1f1b97a34d7517a498bff8 | ||
| impfuzzy | 48:9jS93a6SX0nXQeJmRMlT/43F8tLECjIfunBXoylKGE:RSs602Xvy4C | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 14 AntiVirus engines on VirusTotal as malicious |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
| info | The executable uses a known packer |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.DLL
0x413204 RegCloseKey
0x413208 RegEnumKeyExA
0x41320c RegOpenKeyExA
0x413210 RegQueryValueExA
KERNEL32.dll
0x41321c CloseHandle
0x413220 CreateMutexA
0x413224 CreateProcessA
0x413228 ExitProcess
0x41322c FindResourceExA
0x413230 FormatMessageA
0x413234 GetCommandLineA
0x413238 GetCurrentDirectoryA
0x41323c GetCurrentProcess
0x413240 GetEnvironmentVariableA
0x413244 GetExitCodeProcess
0x413248 GetLastError
0x41324c GetModuleFileNameA
0x413250 GetModuleHandleA
0x413254 GetProcAddress
0x413258 GetStartupInfoA
0x41325c GlobalMemoryStatusEx
0x413260 LoadResource
0x413264 LocalFree
0x413268 LockResource
0x41326c SetEnvironmentVariableA
0x413270 SetLastError
0x413274 SetUnhandledExceptionFilter
0x413278 WaitForSingleObject
msvcrt.dll
0x413284 __getmainargs
0x413288 __p__environ
0x41328c __p__fmode
0x413290 __set_app_type
0x413294 _cexit
0x413298 _chdir
0x41329c _close
0x4132a0 _findclose
0x4132a4 _findfirst
0x4132a8 _findnext
0x4132ac _iob
0x4132b0 _itoa
0x4132b4 _onexit
0x4132b8 _open
0x4132bc _read
0x4132c0 _setmode
0x4132c4 _stat
0x4132c8 atexit
0x4132cc atoi
0x4132d0 fclose
0x4132d4 fopen
0x4132d8 fprintf
0x4132dc fwrite
0x4132e0 memset
0x4132e4 printf
0x4132e8 puts
0x4132ec signal
0x4132f0 strcat
0x4132f4 strchr
0x4132f8 strcmp
0x4132fc strcpy
0x413300 strlen
0x413304 strncat
0x413308 strncpy
0x41330c strpbrk
0x413310 strrchr
0x413314 strstr
0x413318 strtok
SHELL32.DLL
0x413324 ShellExecuteA
USER32.dll
0x413330 CreateWindowExA
0x413334 DispatchMessageA
0x413338 EnumWindows
0x41333c FindWindowExA
0x413340 GetMessageA
0x413344 GetSystemMetrics
0x413348 GetWindowLongA
0x41334c GetWindowRect
0x413350 GetWindowTextA
0x413354 GetWindowThreadProcessId
0x413358 KillTimer
0x41335c LoadImageA
0x413360 MessageBoxA
0x413364 PostQuitMessage
0x413368 SendMessageA
0x41336c SetForegroundWindow
0x413370 SetTimer
0x413374 SetWindowPos
0x413378 ShowWindow
0x41337c TranslateMessage
0x413380 UpdateWindow
EAT(Export Address Table) is none
ADVAPI32.DLL
0x413204 RegCloseKey
0x413208 RegEnumKeyExA
0x41320c RegOpenKeyExA
0x413210 RegQueryValueExA
KERNEL32.dll
0x41321c CloseHandle
0x413220 CreateMutexA
0x413224 CreateProcessA
0x413228 ExitProcess
0x41322c FindResourceExA
0x413230 FormatMessageA
0x413234 GetCommandLineA
0x413238 GetCurrentDirectoryA
0x41323c GetCurrentProcess
0x413240 GetEnvironmentVariableA
0x413244 GetExitCodeProcess
0x413248 GetLastError
0x41324c GetModuleFileNameA
0x413250 GetModuleHandleA
0x413254 GetProcAddress
0x413258 GetStartupInfoA
0x41325c GlobalMemoryStatusEx
0x413260 LoadResource
0x413264 LocalFree
0x413268 LockResource
0x41326c SetEnvironmentVariableA
0x413270 SetLastError
0x413274 SetUnhandledExceptionFilter
0x413278 WaitForSingleObject
msvcrt.dll
0x413284 __getmainargs
0x413288 __p__environ
0x41328c __p__fmode
0x413290 __set_app_type
0x413294 _cexit
0x413298 _chdir
0x41329c _close
0x4132a0 _findclose
0x4132a4 _findfirst
0x4132a8 _findnext
0x4132ac _iob
0x4132b0 _itoa
0x4132b4 _onexit
0x4132b8 _open
0x4132bc _read
0x4132c0 _setmode
0x4132c4 _stat
0x4132c8 atexit
0x4132cc atoi
0x4132d0 fclose
0x4132d4 fopen
0x4132d8 fprintf
0x4132dc fwrite
0x4132e0 memset
0x4132e4 printf
0x4132e8 puts
0x4132ec signal
0x4132f0 strcat
0x4132f4 strchr
0x4132f8 strcmp
0x4132fc strcpy
0x413300 strlen
0x413304 strncat
0x413308 strncpy
0x41330c strpbrk
0x413310 strrchr
0x413314 strstr
0x413318 strtok
SHELL32.DLL
0x413324 ShellExecuteA
USER32.dll
0x413330 CreateWindowExA
0x413334 DispatchMessageA
0x413338 EnumWindows
0x41333c FindWindowExA
0x413340 GetMessageA
0x413344 GetSystemMetrics
0x413348 GetWindowLongA
0x41334c GetWindowRect
0x413350 GetWindowTextA
0x413354 GetWindowThreadProcessId
0x413358 KillTimer
0x41335c LoadImageA
0x413360 MessageBoxA
0x413364 PostQuitMessage
0x413368 SendMessageA
0x41336c SetForegroundWindow
0x413370 SetTimer
0x413374 SetWindowPos
0x413378 ShowWindow
0x41337c TranslateMessage
0x413380 UpdateWindow
EAT(Export Address Table) is none