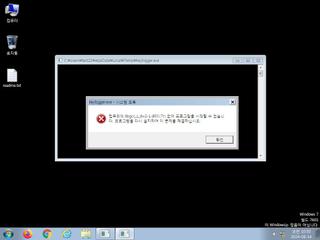
ScreenShot
| Created | 2024.08.14 10:56 | Machine | s1_win7_x6401 |
| Filename | keylogger.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 41 detected (malicious, high confidence, Artemis, Unsafe, GenericKD, Vz13, Attribute, HighConfidence, CLOUD, Generic Reputation PUA, Static AI, Suspicious PE, Detected, ai score=83, Wacatac, Chgt, R002H0CDL24, Agen, Mgil, susgen, confidence, 100%) | ||
| md5 | fbbc99e0b5c7a5f4b76886520f5a4f63 | ||
| sha256 | 6054e52edc7112fcecaaf39f37c6bdaa35f98bfaff45d4e01802b9a8bedd2eef | ||
| ssdeep | 768:7GXBPxEENGqtiAoga/G5PP3lLuzZPKqkQF/rxa0VeBFt:7GxHGqM5p/qPP3lLuBZkQFE0Vgt | ||
| imphash | aabc7d829ec4bcf3eb634829eff84ef7 | ||
| impfuzzy | 48:4fCCaVc5KXlhNOqdQGhv39Tqos1osn5cTz7Ei:4fCCOc5Ml3OqdQPF1Fn5cTzoi | ||
Network IP location
Signature (1cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 41 AntiVirus engines on VirusTotal as malicious |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x4091b0 AllocConsole
0x4091b4 DeleteCriticalSection
0x4091b8 EnterCriticalSection
0x4091bc ExitProcess
0x4091c0 FindClose
0x4091c4 FindFirstFileA
0x4091c8 FindNextFileA
0x4091cc FreeLibrary
0x4091d0 GetCommandLineA
0x4091d4 GetLastError
0x4091d8 GetModuleHandleA
0x4091dc GetProcAddress
0x4091e0 InitializeCriticalSection
0x4091e4 LeaveCriticalSection
0x4091e8 LoadLibraryA
0x4091ec SetUnhandledExceptionFilter
0x4091f0 TlsGetValue
0x4091f4 VirtualProtect
0x4091f8 VirtualQuery
msvcrt.dll
0x409200 _strdup
0x409204 _stricoll
msvcrt.dll
0x40920c __getmainargs
0x409210 __mb_cur_max
0x409214 __p__environ
0x409218 __p__fmode
0x40921c __set_app_type
0x409220 _cexit
0x409224 _errno
0x409228 _fpreset
0x40922c _fullpath
0x409230 _iob
0x409234 _isctype
0x409238 _onexit
0x40923c _pctype
0x409240 _setmode
0x409244 abort
0x409248 atexit
0x40924c calloc
0x409250 free
0x409254 fwrite
0x409258 malloc
0x40925c mbstowcs
0x409260 memcpy
0x409264 realloc
0x409268 setlocale
0x40926c signal
0x409270 strcoll
0x409274 strlen
0x409278 tolower
0x40927c vfprintf
0x409280 wcstombs
USER32.dll
0x409288 FindWindowA
0x40928c GetAsyncKeyState
0x409290 GetKeyState
0x409294 ShowWindow
libgcc_s_dw2-1.dll
0x40929c _Unwind_Resume
0x4092a0 __deregister_frame_info
0x4092a4 __register_frame_info
libstdc++-6.dll
0x4092ac _ZNSt14basic_ofstreamIcSt11char_traitsIcEE5closeEv
0x4092b0 _ZNSt14basic_ofstreamIcSt11char_traitsIcEE7is_openEv
0x4092b4 _ZNSt14basic_ofstreamIcSt11char_traitsIcEEC1EPKcSt13_Ios_Openmode
0x4092b8 _ZNSt14basic_ofstreamIcSt11char_traitsIcEED1Ev
0x4092bc _ZNSt8ios_base4InitC1Ev
0x4092c0 _ZNSt8ios_base4InitD1Ev
0x4092c4 _ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_PKc
0x4092c8 _ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_c
0x4092cc __gxx_personality_v0
EAT(Export Address Table) is none
KERNEL32.dll
0x4091b0 AllocConsole
0x4091b4 DeleteCriticalSection
0x4091b8 EnterCriticalSection
0x4091bc ExitProcess
0x4091c0 FindClose
0x4091c4 FindFirstFileA
0x4091c8 FindNextFileA
0x4091cc FreeLibrary
0x4091d0 GetCommandLineA
0x4091d4 GetLastError
0x4091d8 GetModuleHandleA
0x4091dc GetProcAddress
0x4091e0 InitializeCriticalSection
0x4091e4 LeaveCriticalSection
0x4091e8 LoadLibraryA
0x4091ec SetUnhandledExceptionFilter
0x4091f0 TlsGetValue
0x4091f4 VirtualProtect
0x4091f8 VirtualQuery
msvcrt.dll
0x409200 _strdup
0x409204 _stricoll
msvcrt.dll
0x40920c __getmainargs
0x409210 __mb_cur_max
0x409214 __p__environ
0x409218 __p__fmode
0x40921c __set_app_type
0x409220 _cexit
0x409224 _errno
0x409228 _fpreset
0x40922c _fullpath
0x409230 _iob
0x409234 _isctype
0x409238 _onexit
0x40923c _pctype
0x409240 _setmode
0x409244 abort
0x409248 atexit
0x40924c calloc
0x409250 free
0x409254 fwrite
0x409258 malloc
0x40925c mbstowcs
0x409260 memcpy
0x409264 realloc
0x409268 setlocale
0x40926c signal
0x409270 strcoll
0x409274 strlen
0x409278 tolower
0x40927c vfprintf
0x409280 wcstombs
USER32.dll
0x409288 FindWindowA
0x40928c GetAsyncKeyState
0x409290 GetKeyState
0x409294 ShowWindow
libgcc_s_dw2-1.dll
0x40929c _Unwind_Resume
0x4092a0 __deregister_frame_info
0x4092a4 __register_frame_info
libstdc++-6.dll
0x4092ac _ZNSt14basic_ofstreamIcSt11char_traitsIcEE5closeEv
0x4092b0 _ZNSt14basic_ofstreamIcSt11char_traitsIcEE7is_openEv
0x4092b4 _ZNSt14basic_ofstreamIcSt11char_traitsIcEEC1EPKcSt13_Ios_Openmode
0x4092b8 _ZNSt14basic_ofstreamIcSt11char_traitsIcEED1Ev
0x4092bc _ZNSt8ios_base4InitC1Ev
0x4092c0 _ZNSt8ios_base4InitD1Ev
0x4092c4 _ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_PKc
0x4092c8 _ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_c
0x4092cc __gxx_personality_v0
EAT(Export Address Table) is none