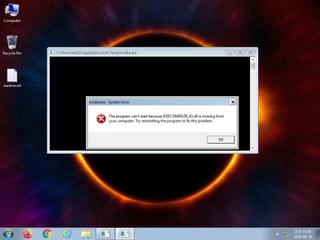
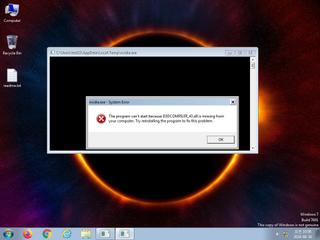
ScreenShot
| Created | 2024.08.30 11:23 | Machine | s1_win7_x6403 |
| Filename | nvidia.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 21 detected (AIDetectMalware, malicious, high confidence, score, Unsafe, Save, Attribute, HighConfidence, VMProtect, L suspicious, AGEN, Real Protect, VMProtBad, Static AI, Suspicious PE, Detected, Wacapew, confidence) | ||
| md5 | 4b3659cdd58a9f5cda08278568d65da1 | ||
| sha256 | 11bf2a65b41443e8feb207f59ef95068fecfbe14a566971b0e725c091d39bf8e | ||
| ssdeep | 196608:+p/o0pcsYyuI/lQrTe6HNCHxYiMr+h5ij6zLwk:R0piQu7tSxsr+h5LzLwk | ||
| imphash | 95035853cdeedbdbff3f31900417830d | ||
| impfuzzy | 24:2WclYy4BzMGTZx/R6oOO5yWdboT5OZpwaQtXJHc9NDI5Q8:jS14/T5Rdo10pwnXpcM5Q8 | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 21 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is likely packed with VMProtect |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | VMProtect_Zero | VMProtect packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
d3d11.dll
0x140bc7000 D3D11CreateDeviceAndSwapChain
D3DCOMPILER_43.dll
0x140bc7010 D3DCompile
KERNEL32.dll
0x140bc7020 ReadFile
USER32.dll
0x140bc7030 SetCursor
ADVAPI32.dll
0x140bc7040 DeleteService
MSVCP140.dll
0x140bc7050 ?sync@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
dwmapi.dll
0x140bc7060 DwmExtendFrameIntoClientArea
WINHTTP.dll
0x140bc7070 WinHttpSendRequest
CRYPT32.dll
0x140bc7080 CertCreateCertificateChainEngine
IMM32.dll
0x140bc7090 ImmReleaseContext
Normaliz.dll
0x140bc70a0 IdnToAscii
WLDAP32.dll
0x140bc70b0 None
WS2_32.dll
0x140bc70c0 ntohl
RPCRT4.dll
0x140bc70d0 UuidToStringA
PSAPI.DLL
0x140bc70e0 GetModuleInformation
USERENV.dll
0x140bc70f0 UnloadUserProfile
VCRUNTIME140_1.dll
0x140bc7100 __CxxFrameHandler4
VCRUNTIME140.dll
0x140bc7110 __current_exception_context
api-ms-win-crt-runtime-l1-1-0.dll
0x140bc7120 exit
api-ms-win-crt-stdio-l1-1-0.dll
0x140bc7130 fgetc
api-ms-win-crt-heap-l1-1-0.dll
0x140bc7140 free
api-ms-win-crt-math-l1-1-0.dll
0x140bc7150 acosf
api-ms-win-crt-string-l1-1-0.dll
0x140bc7160 strncmp
api-ms-win-crt-convert-l1-1-0.dll
0x140bc7170 atoi
api-ms-win-crt-utility-l1-1-0.dll
0x140bc7180 qsort
api-ms-win-crt-filesystem-l1-1-0.dll
0x140bc7190 _access
api-ms-win-crt-locale-l1-1-0.dll
0x140bc71a0 localeconv
api-ms-win-crt-time-l1-1-0.dll
0x140bc71b0 _time64
SHELL32.dll
0x140bc71c0 ShellExecuteA
WTSAPI32.dll
0x140bc71d0 WTSSendMessageW
KERNEL32.dll
0x140bc71e0 GetSystemTimeAsFileTime
USER32.dll
0x140bc71f0 GetUserObjectInformationW
KERNEL32.dll
0x140bc7200 LocalAlloc
0x140bc7208 LocalFree
0x140bc7210 GetModuleFileNameW
0x140bc7218 GetProcessAffinityMask
0x140bc7220 SetProcessAffinityMask
0x140bc7228 SetThreadAffinityMask
0x140bc7230 Sleep
0x140bc7238 ExitProcess
0x140bc7240 FreeLibrary
0x140bc7248 LoadLibraryA
0x140bc7250 GetModuleHandleA
0x140bc7258 GetProcAddress
USER32.dll
0x140bc7268 GetProcessWindowStation
0x140bc7270 GetUserObjectInformationW
EAT(Export Address Table) Library
d3d11.dll
0x140bc7000 D3D11CreateDeviceAndSwapChain
D3DCOMPILER_43.dll
0x140bc7010 D3DCompile
KERNEL32.dll
0x140bc7020 ReadFile
USER32.dll
0x140bc7030 SetCursor
ADVAPI32.dll
0x140bc7040 DeleteService
MSVCP140.dll
0x140bc7050 ?sync@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
dwmapi.dll
0x140bc7060 DwmExtendFrameIntoClientArea
WINHTTP.dll
0x140bc7070 WinHttpSendRequest
CRYPT32.dll
0x140bc7080 CertCreateCertificateChainEngine
IMM32.dll
0x140bc7090 ImmReleaseContext
Normaliz.dll
0x140bc70a0 IdnToAscii
WLDAP32.dll
0x140bc70b0 None
WS2_32.dll
0x140bc70c0 ntohl
RPCRT4.dll
0x140bc70d0 UuidToStringA
PSAPI.DLL
0x140bc70e0 GetModuleInformation
USERENV.dll
0x140bc70f0 UnloadUserProfile
VCRUNTIME140_1.dll
0x140bc7100 __CxxFrameHandler4
VCRUNTIME140.dll
0x140bc7110 __current_exception_context
api-ms-win-crt-runtime-l1-1-0.dll
0x140bc7120 exit
api-ms-win-crt-stdio-l1-1-0.dll
0x140bc7130 fgetc
api-ms-win-crt-heap-l1-1-0.dll
0x140bc7140 free
api-ms-win-crt-math-l1-1-0.dll
0x140bc7150 acosf
api-ms-win-crt-string-l1-1-0.dll
0x140bc7160 strncmp
api-ms-win-crt-convert-l1-1-0.dll
0x140bc7170 atoi
api-ms-win-crt-utility-l1-1-0.dll
0x140bc7180 qsort
api-ms-win-crt-filesystem-l1-1-0.dll
0x140bc7190 _access
api-ms-win-crt-locale-l1-1-0.dll
0x140bc71a0 localeconv
api-ms-win-crt-time-l1-1-0.dll
0x140bc71b0 _time64
SHELL32.dll
0x140bc71c0 ShellExecuteA
WTSAPI32.dll
0x140bc71d0 WTSSendMessageW
KERNEL32.dll
0x140bc71e0 GetSystemTimeAsFileTime
USER32.dll
0x140bc71f0 GetUserObjectInformationW
KERNEL32.dll
0x140bc7200 LocalAlloc
0x140bc7208 LocalFree
0x140bc7210 GetModuleFileNameW
0x140bc7218 GetProcessAffinityMask
0x140bc7220 SetProcessAffinityMask
0x140bc7228 SetThreadAffinityMask
0x140bc7230 Sleep
0x140bc7238 ExitProcess
0x140bc7240 FreeLibrary
0x140bc7248 LoadLibraryA
0x140bc7250 GetModuleHandleA
0x140bc7258 GetProcAddress
USER32.dll
0x140bc7268 GetProcessWindowStation
0x140bc7270 GetUserObjectInformationW
EAT(Export Address Table) Library