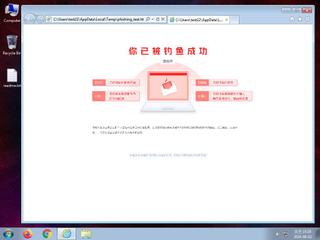
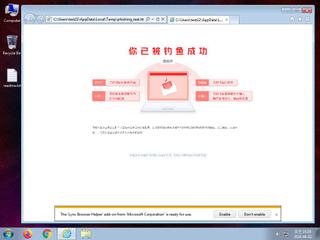
ScreenShot
| Created | 2024.09.02 10:20 | Machine | s1_win7_x6403 |
| Filename | %E6%94%BE%E5%81%87%E5%80%BC%E7%8F%AD%E5%AE%89%E6%8E%92.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 18 detected (AIDetectMalware, malicious, moderate confidence, GenericKD, Unsafe, Save, Donipye, ai score=87, R002H09HR24, susgen, confidence, 100%) | ||
| md5 | 07898838cbb961a9c4a61b180b6b48da | ||
| sha256 | bd9982c5696868d795ca294b7f273e0f3cd4b639c3e49d2aa021be7a21fb94c2 | ||
| ssdeep | 24576:9PWUMP9YLMgqjUfk9OpU1BFBBUB5y+zIVGiBc58:lps9+UHVUB5y+zIVG8c58 | ||
| imphash | bc559f8ca78b1db60e2a644532d66292 | ||
| impfuzzy | 48:wtZ0muWfncpVrjErggtVrBgrnBd3RYFwnWH:mQWfncpVrjeggtVrBgrnB5WH | ||
Network IP location
Signature (21cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | Drops a binary and executes it |
| watch | File has been identified by 18 AntiVirus engines on VirusTotal as malicious |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | An application raised an exception which may be indicative of an exploit crash |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a suspicious process |
| notice | Foreign language identified in PE resource |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Uses Windows utilities for basic Windows functionality |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
| info | Queries for the computername |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
Rules (17cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | CoinMiner_IN | CoinMiner | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsPE64 | (no description) | binaries (upload) |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | PNG_Format_Zero | PNG Format | binaries (download) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x140078000 SizeofResource
0x140078008 WriteFile
0x140078010 CreateFileW
0x140078018 MultiByteToWideChar
0x140078020 LockResource
0x140078028 CloseHandle
0x140078030 LoadResource
0x140078038 FindResourceW
0x140078040 WideCharToMultiByte
0x140078048 GetACP
0x140078050 WriteConsoleW
0x140078058 HeapSize
0x140078060 SetStdHandle
0x140078068 GetProcessHeap
0x140078070 SetEnvironmentVariableW
0x140078078 FreeEnvironmentStringsW
0x140078080 GetEnvironmentStringsW
0x140078088 GetOEMCP
0x140078090 IsValidCodePage
0x140078098 FindNextFileW
0x1400780a0 FindFirstFileExW
0x1400780a8 FindClose
0x1400780b0 GetTimeZoneInformation
0x1400780b8 HeapReAlloc
0x1400780c0 ReadConsoleW
0x1400780c8 ReadFile
0x1400780d0 EnumSystemLocalesW
0x1400780d8 GetUserDefaultLCID
0x1400780e0 IsValidLocale
0x1400780e8 GetLocaleInfoW
0x1400780f0 LCMapStringW
0x1400780f8 CompareStringW
0x140078100 GetTimeFormatW
0x140078108 GetDateFormatW
0x140078110 InitializeSRWLock
0x140078118 ReleaseSRWLockExclusive
0x140078120 AcquireSRWLockExclusive
0x140078128 TryAcquireSRWLockExclusive
0x140078130 GetCurrentThreadId
0x140078138 WaitForSingleObjectEx
0x140078140 EnterCriticalSection
0x140078148 LeaveCriticalSection
0x140078150 InitializeCriticalSectionEx
0x140078158 DeleteCriticalSection
0x140078160 EncodePointer
0x140078168 DecodePointer
0x140078170 GetStringTypeW
0x140078178 GetLocaleInfoEx
0x140078180 LCMapStringEx
0x140078188 QueryPerformanceCounter
0x140078190 CompareStringEx
0x140078198 GetCPInfo
0x1400781a0 GetSystemTimeAsFileTime
0x1400781a8 GetModuleHandleW
0x1400781b0 GetProcAddress
0x1400781b8 InitializeCriticalSectionAndSpinCount
0x1400781c0 SetEvent
0x1400781c8 ResetEvent
0x1400781d0 CreateEventW
0x1400781d8 RtlCaptureContext
0x1400781e0 RtlLookupFunctionEntry
0x1400781e8 RtlVirtualUnwind
0x1400781f0 UnhandledExceptionFilter
0x1400781f8 SetUnhandledExceptionFilter
0x140078200 GetCurrentProcess
0x140078208 TerminateProcess
0x140078210 IsProcessorFeaturePresent
0x140078218 IsDebuggerPresent
0x140078220 GetStartupInfoW
0x140078228 GetCurrentProcessId
0x140078230 InitializeSListHead
0x140078238 RtlUnwindEx
0x140078240 RtlPcToFileHeader
0x140078248 RaiseException
0x140078250 GetLastError
0x140078258 SetLastError
0x140078260 TlsAlloc
0x140078268 TlsGetValue
0x140078270 TlsSetValue
0x140078278 TlsFree
0x140078280 FreeLibrary
0x140078288 LoadLibraryExW
0x140078290 RtlUnwind
0x140078298 DuplicateHandle
0x1400782a0 CreateProcessW
0x1400782a8 GetModuleHandleExW
0x1400782b0 ExitProcess
0x1400782b8 GetModuleFileNameW
0x1400782c0 GetStdHandle
0x1400782c8 GetCommandLineA
0x1400782d0 GetCommandLineW
0x1400782d8 GetFileSizeEx
0x1400782e0 SetFilePointerEx
0x1400782e8 GetFileType
0x1400782f0 HeapAlloc
0x1400782f8 FlushFileBuffers
0x140078300 GetConsoleCP
0x140078308 GetConsoleMode
0x140078310 HeapFree
0x140078318 WaitForSingleObject
0x140078320 GetExitCodeProcess
0x140078328 GetFileAttributesExW
0x140078330 CreatePipe
WS2_32.dll
0x140078340 select
0x140078348 shutdown
0x140078350 WSASocketW
0x140078358 getaddrinfo
0x140078360 WSAStartup
0x140078368 getpeername
0x140078370 send
0x140078378 closesocket
0x140078380 ntohs
0x140078388 connect
0x140078390 recv
0x140078398 getsockopt
0x1400783a0 freeaddrinfo
0x1400783a8 ioctlsocket
0x1400783b0 getnameinfo
0x1400783b8 setsockopt
0x1400783c0 WSAGetLastError
0x1400783c8 __WSAFDIsSet
0x1400783d0 WSACleanup
0x1400783d8 socket
EAT(Export Address Table) is none
KERNEL32.dll
0x140078000 SizeofResource
0x140078008 WriteFile
0x140078010 CreateFileW
0x140078018 MultiByteToWideChar
0x140078020 LockResource
0x140078028 CloseHandle
0x140078030 LoadResource
0x140078038 FindResourceW
0x140078040 WideCharToMultiByte
0x140078048 GetACP
0x140078050 WriteConsoleW
0x140078058 HeapSize
0x140078060 SetStdHandle
0x140078068 GetProcessHeap
0x140078070 SetEnvironmentVariableW
0x140078078 FreeEnvironmentStringsW
0x140078080 GetEnvironmentStringsW
0x140078088 GetOEMCP
0x140078090 IsValidCodePage
0x140078098 FindNextFileW
0x1400780a0 FindFirstFileExW
0x1400780a8 FindClose
0x1400780b0 GetTimeZoneInformation
0x1400780b8 HeapReAlloc
0x1400780c0 ReadConsoleW
0x1400780c8 ReadFile
0x1400780d0 EnumSystemLocalesW
0x1400780d8 GetUserDefaultLCID
0x1400780e0 IsValidLocale
0x1400780e8 GetLocaleInfoW
0x1400780f0 LCMapStringW
0x1400780f8 CompareStringW
0x140078100 GetTimeFormatW
0x140078108 GetDateFormatW
0x140078110 InitializeSRWLock
0x140078118 ReleaseSRWLockExclusive
0x140078120 AcquireSRWLockExclusive
0x140078128 TryAcquireSRWLockExclusive
0x140078130 GetCurrentThreadId
0x140078138 WaitForSingleObjectEx
0x140078140 EnterCriticalSection
0x140078148 LeaveCriticalSection
0x140078150 InitializeCriticalSectionEx
0x140078158 DeleteCriticalSection
0x140078160 EncodePointer
0x140078168 DecodePointer
0x140078170 GetStringTypeW
0x140078178 GetLocaleInfoEx
0x140078180 LCMapStringEx
0x140078188 QueryPerformanceCounter
0x140078190 CompareStringEx
0x140078198 GetCPInfo
0x1400781a0 GetSystemTimeAsFileTime
0x1400781a8 GetModuleHandleW
0x1400781b0 GetProcAddress
0x1400781b8 InitializeCriticalSectionAndSpinCount
0x1400781c0 SetEvent
0x1400781c8 ResetEvent
0x1400781d0 CreateEventW
0x1400781d8 RtlCaptureContext
0x1400781e0 RtlLookupFunctionEntry
0x1400781e8 RtlVirtualUnwind
0x1400781f0 UnhandledExceptionFilter
0x1400781f8 SetUnhandledExceptionFilter
0x140078200 GetCurrentProcess
0x140078208 TerminateProcess
0x140078210 IsProcessorFeaturePresent
0x140078218 IsDebuggerPresent
0x140078220 GetStartupInfoW
0x140078228 GetCurrentProcessId
0x140078230 InitializeSListHead
0x140078238 RtlUnwindEx
0x140078240 RtlPcToFileHeader
0x140078248 RaiseException
0x140078250 GetLastError
0x140078258 SetLastError
0x140078260 TlsAlloc
0x140078268 TlsGetValue
0x140078270 TlsSetValue
0x140078278 TlsFree
0x140078280 FreeLibrary
0x140078288 LoadLibraryExW
0x140078290 RtlUnwind
0x140078298 DuplicateHandle
0x1400782a0 CreateProcessW
0x1400782a8 GetModuleHandleExW
0x1400782b0 ExitProcess
0x1400782b8 GetModuleFileNameW
0x1400782c0 GetStdHandle
0x1400782c8 GetCommandLineA
0x1400782d0 GetCommandLineW
0x1400782d8 GetFileSizeEx
0x1400782e0 SetFilePointerEx
0x1400782e8 GetFileType
0x1400782f0 HeapAlloc
0x1400782f8 FlushFileBuffers
0x140078300 GetConsoleCP
0x140078308 GetConsoleMode
0x140078310 HeapFree
0x140078318 WaitForSingleObject
0x140078320 GetExitCodeProcess
0x140078328 GetFileAttributesExW
0x140078330 CreatePipe
WS2_32.dll
0x140078340 select
0x140078348 shutdown
0x140078350 WSASocketW
0x140078358 getaddrinfo
0x140078360 WSAStartup
0x140078368 getpeername
0x140078370 send
0x140078378 closesocket
0x140078380 ntohs
0x140078388 connect
0x140078390 recv
0x140078398 getsockopt
0x1400783a0 freeaddrinfo
0x1400783a8 ioctlsocket
0x1400783b0 getnameinfo
0x1400783b8 setsockopt
0x1400783c0 WSAGetLastError
0x1400783c8 __WSAFDIsSet
0x1400783d0 WSACleanup
0x1400783d8 socket
EAT(Export Address Table) is none