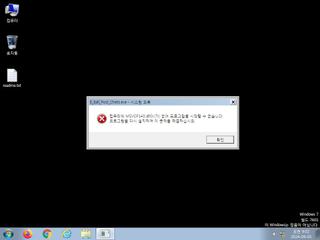
ScreenShot
| Created | 2024.09.03 09:14 | Machine | s1_win7_x6401 |
| Filename | 8_Ball_Pool_Cheto.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 48 detected (AIDetectMalware, Fragtor, malicious, moderate confidence, FYMP, Unsafe, Viff, Attribute, HighConfidence, MalwareX, CLOUD, R002C0DI224, Static AI, Suspicious PE, Detected, ai score=100, GrayWare, Wacapew, Wacatac, mclg, ABTrojan, YPMJ, R502664, BScope, Outbreak, Chgt, susgen, Barys, confidence, 100%) | ||
| md5 | b5ca92538a485317ce5c4dff6c5fd08f | ||
| sha256 | 0aff775071bc938ee44ac07e20e4cabddd5235edb34a437c4d7006a8dab91a5e | ||
| ssdeep | 24576:pEfEYaq13X2vhSMXlohmx+wQtaQUUlq/a:pEt3m30lqy | ||
| imphash | 89b0e9f4642fb133ab2ba12d6b206f68 | ||
| impfuzzy | 96:bJGqeNtV1wTUvb9dwRUu2rSuvsCNL1TS9Ln4i5d:AuAvb9d7umSUSLn4i5d | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 48 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | This executable has a PDB path |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x44d020 QueryPerformanceCounter
0x44d024 CreateMutexA
0x44d028 ReleaseMutex
0x44d02c Sleep
0x44d030 OpenMutexA
0x44d034 CloseHandle
0x44d038 Process32First
0x44d03c WriteProcessMemory
0x44d040 OpenProcess
0x44d044 CreateToolhelp32Snapshot
0x44d048 GetLastError
0x44d04c Process32Next
0x44d050 ReadProcessMemory
0x44d054 VirtualQueryEx
0x44d058 LocalFree
0x44d05c FormatMessageA
0x44d060 GlobalAlloc
0x44d064 InitializeCriticalSectionAndSpinCount
0x44d068 DeleteCriticalSection
0x44d06c CreateEventW
0x44d070 GetModuleHandleW
0x44d074 UnhandledExceptionFilter
0x44d078 SetUnhandledExceptionFilter
0x44d07c GetCurrentProcess
0x44d080 TerminateProcess
0x44d084 IsProcessorFeaturePresent
0x44d088 IsDebuggerPresent
0x44d08c GetStartupInfoW
0x44d090 GetCurrentProcessId
0x44d094 GetCurrentThreadId
0x44d098 GetSystemTimeAsFileTime
0x44d09c InitializeSListHead
0x44d0a0 GetCPInfoExW
0x44d0a4 CreateThread
0x44d0a8 MultiByteToWideChar
0x44d0ac FreeLibrary
0x44d0b0 GlobalFree
0x44d0b4 GlobalLock
0x44d0b8 WideCharToMultiByte
0x44d0bc GlobalUnlock
0x44d0c0 GetModuleHandleA
0x44d0c4 LoadLibraryA
0x44d0c8 QueryPerformanceFrequency
0x44d0cc GetProcAddress
USER32.dll
0x44d13c FindWindowA
0x44d140 EmptyClipboard
0x44d144 GetClipboardData
0x44d148 SetClipboardData
0x44d14c FindWindowExA
0x44d150 SetTimer
0x44d154 IsWindow
0x44d158 GetSystemMetrics
0x44d15c GetWindowRect
0x44d160 UpdateWindow
0x44d164 RegisterClassExA
0x44d168 PostQuitMessage
0x44d16c UnregisterClassA
0x44d170 MessageBoxA
0x44d174 SendMessageA
0x44d178 DispatchMessageA
0x44d17c PeekMessageA
0x44d180 DestroyWindow
0x44d184 ShowWindow
0x44d188 DefWindowProcA
0x44d18c CreateWindowExA
0x44d190 TranslateMessage
0x44d194 LoadIconA
0x44d198 SetWindowPos
0x44d19c GetWindowInfo
0x44d1a0 RegisterClassA
0x44d1a4 CloseClipboard
0x44d1a8 OpenClipboard
0x44d1ac GetCursorPos
0x44d1b0 SetCursorPos
0x44d1b4 ReleaseCapture
0x44d1b8 GetClientRect
0x44d1bc SetCursor
0x44d1c0 SetCapture
0x44d1c4 GetForegroundWindow
0x44d1c8 TrackMouseEvent
0x44d1cc ClientToScreen
0x44d1d0 EnumWindows
0x44d1d4 SetLayeredWindowAttributes
0x44d1d8 IsIconic
0x44d1dc GetKeyState
0x44d1e0 LoadCursorA
0x44d1e4 ScreenToClient
0x44d1e8 GetCapture
0x44d1ec GetWindowThreadProcessId
IMM32.dll
0x44d008 ImmAssociateContextEx
0x44d00c ImmReleaseContext
0x44d010 ImmGetContext
0x44d014 ImmSetCandidateWindow
0x44d018 ImmSetCompositionWindow
dwmapi.dll
0x44d34c DwmExtendFrameIntoClientArea
0x44d350 DwmSetWindowAttribute
MSVCP140.dll
0x44d0d4 ??0_Locinfo@std@@QAE@PBD@Z
0x44d0d8 ??1_Locinfo@std@@QAE@XZ
0x44d0dc ?_Getlconv@_Locinfo@std@@QBEPBUlconv@@XZ
0x44d0e0 ?_Getfalse@_Locinfo@std@@QBEPBDXZ
0x44d0e4 ?_Gettrue@_Locinfo@std@@QBEPBDXZ
0x44d0e8 ??Bid@locale@std@@QAEIXZ
0x44d0ec ?_Decref@facet@locale@std@@UAEPAV_Facet_base@3@XZ
0x44d0f0 ??0facet@locale@std@@IAE@I@Z
0x44d0f4 ??1facet@locale@std@@MAE@XZ
0x44d0f8 ?_Incref@facet@locale@std@@UAEXXZ
0x44d0fc ?_Random_device@std@@YAIXZ
0x44d100 ?id@?$numpunct@D@std@@2V0locale@2@A
0x44d104 ?_Init@locale@std@@CAPAV_Locimp@12@_N@Z
0x44d108 ?_Getgloballocale@locale@std@@CAPAV_Locimp@12@XZ
0x44d10c ??0_Lockit@std@@QAE@H@Z
0x44d110 ??1_Lockit@std@@QAE@XZ
0x44d114 ?_Xlength_error@std@@YAXPBD@Z
0x44d118 ?_Xout_of_range@std@@YAXPBD@Z
0x44d11c ?_Getcvt@_Locinfo@std@@QBE?AU_Cvtvec@@XZ
0x44d120 _Thrd_join
0x44d124 _Mbrtowc
0x44d128 ?_Throw_Cpp_error@std@@YAXH@Z
0x44d12c ?_Xbad_alloc@std@@YAXXZ
0x44d130 _Cnd_do_broadcast_at_thread_exit
0x44d134 _Thrd_id
d3d9.dll
0x44d344 Direct3DCreate9
VCRUNTIME140.dll
0x44d1f4 memset
0x44d1f8 _except_handler4_common
0x44d1fc __current_exception_context
0x44d200 __current_exception
0x44d204 __std_exception_copy
0x44d208 _CxxThrowException
0x44d20c strstr
0x44d210 __std_terminate
0x44d214 __CxxFrameHandler3
0x44d218 memchr
0x44d21c memcpy
0x44d220 memmove
0x44d224 __std_exception_destroy
api-ms-win-crt-stdio-l1-1-0.dll
0x44d2e0 __stdio_common_vsprintf
0x44d2e4 _wfopen
0x44d2e8 fwrite
0x44d2ec fread
0x44d2f0 __p__commode
0x44d2f4 fseek
0x44d2f8 fclose
0x44d2fc fflush
0x44d300 __acrt_iob_func
0x44d304 _set_fmode
0x44d308 ftell
0x44d30c __stdio_common_vsscanf
api-ms-win-crt-string-l1-1-0.dll
0x44d314 strncpy
0x44d318 strncmp
0x44d31c toupper
api-ms-win-crt-utility-l1-1-0.dll
0x44d330 srand
0x44d334 qsort
api-ms-win-crt-heap-l1-1-0.dll
0x44d234 malloc
0x44d238 free
0x44d23c calloc
0x44d240 _set_new_mode
0x44d244 _callnewh
api-ms-win-crt-convert-l1-1-0.dll
0x44d22c atof
api-ms-win-crt-runtime-l1-1-0.dll
0x44d290 _cexit
0x44d294 _configure_narrow_argv
0x44d298 _seh_filter_exe
0x44d29c _invalid_parameter_noinfo_noreturn
0x44d2a0 _controlfp_s
0x44d2a4 _initialize_narrow_environment
0x44d2a8 _initialize_onexit_table
0x44d2ac _crt_atexit
0x44d2b0 _register_thread_local_exe_atexit_callback
0x44d2b4 _c_exit
0x44d2b8 _get_narrow_winmain_command_line
0x44d2bc _register_onexit_function
0x44d2c0 terminate
0x44d2c4 _beginthreadex
0x44d2c8 _exit
0x44d2cc exit
0x44d2d0 _initterm
0x44d2d4 _initterm_e
0x44d2d8 _set_app_type
api-ms-win-crt-time-l1-1-0.dll
0x44d324 clock
0x44d328 _time64
api-ms-win-crt-math-l1-1-0.dll
0x44d254 _fdclass
0x44d258 _dclass
0x44d25c _libm_sse2_cos_precise
0x44d260 _CIfmod
0x44d264 __setusermatherr
0x44d268 _ldclass
0x44d26c _libm_sse2_sin_precise
0x44d270 _libm_sse2_sqrt_precise
0x44d274 ceil
0x44d278 _dsign
0x44d27c _fdsign
0x44d280 _libm_sse2_acos_precise
0x44d284 _CIatan2
0x44d288 _ldsign
api-ms-win-crt-locale-l1-1-0.dll
0x44d24c _configthreadlocale
d2d1.dll
0x44d33c None
DWrite.dll
0x44d000 DWriteCreateFactory
EAT(Export Address Table) is none
KERNEL32.dll
0x44d020 QueryPerformanceCounter
0x44d024 CreateMutexA
0x44d028 ReleaseMutex
0x44d02c Sleep
0x44d030 OpenMutexA
0x44d034 CloseHandle
0x44d038 Process32First
0x44d03c WriteProcessMemory
0x44d040 OpenProcess
0x44d044 CreateToolhelp32Snapshot
0x44d048 GetLastError
0x44d04c Process32Next
0x44d050 ReadProcessMemory
0x44d054 VirtualQueryEx
0x44d058 LocalFree
0x44d05c FormatMessageA
0x44d060 GlobalAlloc
0x44d064 InitializeCriticalSectionAndSpinCount
0x44d068 DeleteCriticalSection
0x44d06c CreateEventW
0x44d070 GetModuleHandleW
0x44d074 UnhandledExceptionFilter
0x44d078 SetUnhandledExceptionFilter
0x44d07c GetCurrentProcess
0x44d080 TerminateProcess
0x44d084 IsProcessorFeaturePresent
0x44d088 IsDebuggerPresent
0x44d08c GetStartupInfoW
0x44d090 GetCurrentProcessId
0x44d094 GetCurrentThreadId
0x44d098 GetSystemTimeAsFileTime
0x44d09c InitializeSListHead
0x44d0a0 GetCPInfoExW
0x44d0a4 CreateThread
0x44d0a8 MultiByteToWideChar
0x44d0ac FreeLibrary
0x44d0b0 GlobalFree
0x44d0b4 GlobalLock
0x44d0b8 WideCharToMultiByte
0x44d0bc GlobalUnlock
0x44d0c0 GetModuleHandleA
0x44d0c4 LoadLibraryA
0x44d0c8 QueryPerformanceFrequency
0x44d0cc GetProcAddress
USER32.dll
0x44d13c FindWindowA
0x44d140 EmptyClipboard
0x44d144 GetClipboardData
0x44d148 SetClipboardData
0x44d14c FindWindowExA
0x44d150 SetTimer
0x44d154 IsWindow
0x44d158 GetSystemMetrics
0x44d15c GetWindowRect
0x44d160 UpdateWindow
0x44d164 RegisterClassExA
0x44d168 PostQuitMessage
0x44d16c UnregisterClassA
0x44d170 MessageBoxA
0x44d174 SendMessageA
0x44d178 DispatchMessageA
0x44d17c PeekMessageA
0x44d180 DestroyWindow
0x44d184 ShowWindow
0x44d188 DefWindowProcA
0x44d18c CreateWindowExA
0x44d190 TranslateMessage
0x44d194 LoadIconA
0x44d198 SetWindowPos
0x44d19c GetWindowInfo
0x44d1a0 RegisterClassA
0x44d1a4 CloseClipboard
0x44d1a8 OpenClipboard
0x44d1ac GetCursorPos
0x44d1b0 SetCursorPos
0x44d1b4 ReleaseCapture
0x44d1b8 GetClientRect
0x44d1bc SetCursor
0x44d1c0 SetCapture
0x44d1c4 GetForegroundWindow
0x44d1c8 TrackMouseEvent
0x44d1cc ClientToScreen
0x44d1d0 EnumWindows
0x44d1d4 SetLayeredWindowAttributes
0x44d1d8 IsIconic
0x44d1dc GetKeyState
0x44d1e0 LoadCursorA
0x44d1e4 ScreenToClient
0x44d1e8 GetCapture
0x44d1ec GetWindowThreadProcessId
IMM32.dll
0x44d008 ImmAssociateContextEx
0x44d00c ImmReleaseContext
0x44d010 ImmGetContext
0x44d014 ImmSetCandidateWindow
0x44d018 ImmSetCompositionWindow
dwmapi.dll
0x44d34c DwmExtendFrameIntoClientArea
0x44d350 DwmSetWindowAttribute
MSVCP140.dll
0x44d0d4 ??0_Locinfo@std@@QAE@PBD@Z
0x44d0d8 ??1_Locinfo@std@@QAE@XZ
0x44d0dc ?_Getlconv@_Locinfo@std@@QBEPBUlconv@@XZ
0x44d0e0 ?_Getfalse@_Locinfo@std@@QBEPBDXZ
0x44d0e4 ?_Gettrue@_Locinfo@std@@QBEPBDXZ
0x44d0e8 ??Bid@locale@std@@QAEIXZ
0x44d0ec ?_Decref@facet@locale@std@@UAEPAV_Facet_base@3@XZ
0x44d0f0 ??0facet@locale@std@@IAE@I@Z
0x44d0f4 ??1facet@locale@std@@MAE@XZ
0x44d0f8 ?_Incref@facet@locale@std@@UAEXXZ
0x44d0fc ?_Random_device@std@@YAIXZ
0x44d100 ?id@?$numpunct@D@std@@2V0locale@2@A
0x44d104 ?_Init@locale@std@@CAPAV_Locimp@12@_N@Z
0x44d108 ?_Getgloballocale@locale@std@@CAPAV_Locimp@12@XZ
0x44d10c ??0_Lockit@std@@QAE@H@Z
0x44d110 ??1_Lockit@std@@QAE@XZ
0x44d114 ?_Xlength_error@std@@YAXPBD@Z
0x44d118 ?_Xout_of_range@std@@YAXPBD@Z
0x44d11c ?_Getcvt@_Locinfo@std@@QBE?AU_Cvtvec@@XZ
0x44d120 _Thrd_join
0x44d124 _Mbrtowc
0x44d128 ?_Throw_Cpp_error@std@@YAXH@Z
0x44d12c ?_Xbad_alloc@std@@YAXXZ
0x44d130 _Cnd_do_broadcast_at_thread_exit
0x44d134 _Thrd_id
d3d9.dll
0x44d344 Direct3DCreate9
VCRUNTIME140.dll
0x44d1f4 memset
0x44d1f8 _except_handler4_common
0x44d1fc __current_exception_context
0x44d200 __current_exception
0x44d204 __std_exception_copy
0x44d208 _CxxThrowException
0x44d20c strstr
0x44d210 __std_terminate
0x44d214 __CxxFrameHandler3
0x44d218 memchr
0x44d21c memcpy
0x44d220 memmove
0x44d224 __std_exception_destroy
api-ms-win-crt-stdio-l1-1-0.dll
0x44d2e0 __stdio_common_vsprintf
0x44d2e4 _wfopen
0x44d2e8 fwrite
0x44d2ec fread
0x44d2f0 __p__commode
0x44d2f4 fseek
0x44d2f8 fclose
0x44d2fc fflush
0x44d300 __acrt_iob_func
0x44d304 _set_fmode
0x44d308 ftell
0x44d30c __stdio_common_vsscanf
api-ms-win-crt-string-l1-1-0.dll
0x44d314 strncpy
0x44d318 strncmp
0x44d31c toupper
api-ms-win-crt-utility-l1-1-0.dll
0x44d330 srand
0x44d334 qsort
api-ms-win-crt-heap-l1-1-0.dll
0x44d234 malloc
0x44d238 free
0x44d23c calloc
0x44d240 _set_new_mode
0x44d244 _callnewh
api-ms-win-crt-convert-l1-1-0.dll
0x44d22c atof
api-ms-win-crt-runtime-l1-1-0.dll
0x44d290 _cexit
0x44d294 _configure_narrow_argv
0x44d298 _seh_filter_exe
0x44d29c _invalid_parameter_noinfo_noreturn
0x44d2a0 _controlfp_s
0x44d2a4 _initialize_narrow_environment
0x44d2a8 _initialize_onexit_table
0x44d2ac _crt_atexit
0x44d2b0 _register_thread_local_exe_atexit_callback
0x44d2b4 _c_exit
0x44d2b8 _get_narrow_winmain_command_line
0x44d2bc _register_onexit_function
0x44d2c0 terminate
0x44d2c4 _beginthreadex
0x44d2c8 _exit
0x44d2cc exit
0x44d2d0 _initterm
0x44d2d4 _initterm_e
0x44d2d8 _set_app_type
api-ms-win-crt-time-l1-1-0.dll
0x44d324 clock
0x44d328 _time64
api-ms-win-crt-math-l1-1-0.dll
0x44d254 _fdclass
0x44d258 _dclass
0x44d25c _libm_sse2_cos_precise
0x44d260 _CIfmod
0x44d264 __setusermatherr
0x44d268 _ldclass
0x44d26c _libm_sse2_sin_precise
0x44d270 _libm_sse2_sqrt_precise
0x44d274 ceil
0x44d278 _dsign
0x44d27c _fdsign
0x44d280 _libm_sse2_acos_precise
0x44d284 _CIatan2
0x44d288 _ldsign
api-ms-win-crt-locale-l1-1-0.dll
0x44d24c _configthreadlocale
d2d1.dll
0x44d33c None
DWrite.dll
0x44d000 DWriteCreateFactory
EAT(Export Address Table) is none