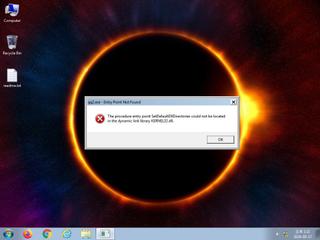
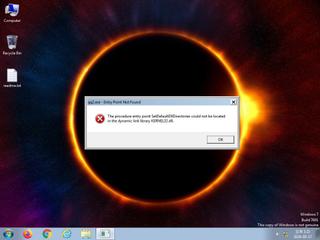
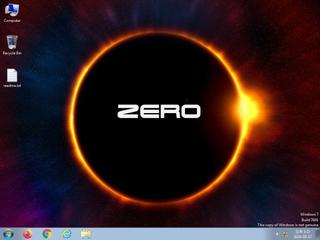
ScreenShot
| Created | 2024.09.17 14:03 | Machine | s1_win7_x6403 |
| Filename | qq2.exe | ||
| Type | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 54 detected (AIDetectMalware, Seheq, Malicious, score, Artemis, GenericKD, Unsafe, Kryptik, Vote, confidence, 100%, Genus, high confidence, HXUY, ccmw, Kryptik@AI, RDML, iVWrkb5uJXMofS8PGKk33w, csdvw, GenKryptik, Detected, ABTrojan, PMUU, BScope, TrojanProxy, Sybici, Krypt, GdSda, R002H09I124, Gencirc) | ||
| md5 | ffc6e86b94a45cd05eb5b249209970bd | ||
| sha256 | 3c7db61b397a28897ade5d4beaa84af510207cd5ff1b17feb6e82c5f3c2df71e | ||
| ssdeep | 49152:U1AQHSED94jNTvu4OjPlH8h6dd3memJ8UJQ9Od8PATX+8qbyyuF7DiyanYgaxxlW:SAQHSER4jNzcjtchGd3mem94EQH | ||
| imphash | 1e5a4769bafbf8d68687235e0a241fea | ||
| impfuzzy | 96:dbSNkeDW0U07TvMptgRx4wKoXOfK5qgcSKq72LV2IK9CK1:lSlW0U0vPvEqKq7sQIK9CK1 | ||
Network IP location
Signature (1cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 54 AntiVirus engines on VirusTotal as malicious |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
GDI32.dll
0x6d2454 ChoosePixelFormat
0x6d2458 CombineRgn
0x6d245c CreateCompatibleBitmap
0x6d2460 CreateICW
0x6d2464 CreatePen
0x6d2468 EndGdiRendering
0x6d246c EndPage
0x6d2470 EngDeleteClip
0x6d2474 EngQueryEMFInfo
0x6d2478 EngStretchBltROP
0x6d247c EngTransparentBlt
0x6d2480 EngUnicodeToMultiByteN
0x6d2484 FixBrushOrgEx
0x6d2488 GdiConvertBitmapV5
0x6d248c GdiDeleteSpoolFileHandle
0x6d2490 GdiFullscreenControl
0x6d2494 GdiIsMetaPrintDC
0x6d2498 GdiStartPageEMF
0x6d249c GetCharacterPlacementA
0x6d24a0 GetColorSpace
0x6d24a4 GetETM
0x6d24a8 GetEnhMetaFileW
0x6d24ac GetFontRealizationInfo
0x6d24b0 GetICMProfileA
0x6d24b4 GetICMProfileW
0x6d24b8 GetMapMode
0x6d24bc GetMiterLimit
0x6d24c0 GetOutlineTextMetricsW
0x6d24c4 GetROP2
0x6d24c8 GetTextExtentExPointW
0x6d24cc GetTextExtentPointI
0x6d24d0 GetTextFaceA
0x6d24d4 MoveToEx
0x6d24d8 NamedEscape
0x6d24dc OffsetClipRgn
0x6d24e0 OffsetRgn
0x6d24e4 PATHOBJ_bEnum
0x6d24e8 PATHOBJ_bEnumClipLines
0x6d24ec PaintRgn
0x6d24f0 PlgBlt
0x6d24f4 PolyTextOutA
0x6d24f8 Polygon
0x6d24fc QueryFontAssocStatus
0x6d2500 RealizePalette
0x6d2504 RemoveFontResourceA
0x6d2508 ResetDCW
0x6d250c STROBJ_bEnum
0x6d2510 STROBJ_dwGetCodePage
0x6d2514 SelectClipPath
0x6d2518 SelectFontLocal
0x6d251c SetDCPenColor
0x6d2520 SetGraphicsMode
0x6d2524 SetMetaFileBitsEx
0x6d2528 SetRectRgn
0x6d252c SetTextCharacterExtra
KERNEL32.dll
0x6d2534 CloseThreadpoolTimer
0x6d2538 CompareStringOrdinal
0x6d253c CreateDirectoryA
0x6d2540 CreateDirectoryW
0x6d2544 CreateHardLinkA
0x6d2548 CreateMutexExW
0x6d254c CreateProcessA
0x6d2550 CreateThreadpool
0x6d2554 CreateTimerQueueTimer
0x6d2558 CtrlRoutine
0x6d255c DeleteFileTransactedW
0x6d2560 DeleteProcThreadAttributeList
0x6d2564 DeleteTimerQueueTimer
0x6d2568 EnumDateFormatsA
0x6d256c EnumResourceTypesExW
0x6d2570 EnumTimeFormatsA
0x6d2574 EnumUILanguagesA
0x6d2578 ExitVDM
0x6d257c FileTimeToLocalFileTime
0x6d2580 FindFirstFileExA
0x6d2584 FindNextFileW
0x6d2588 FlsSetValue
0x6d258c FreeEnvironmentStringsA
0x6d2590 FreeLibrary
0x6d2594 GetACP
0x6d2598 GetCalendarDaysInMonth
0x6d259c GetCalendarInfoA
0x6d25a0 GetCalendarSupportedDateRange
0x6d25a4 GetConsoleAliasExesW
0x6d25a8 GetConsoleFontSize
0x6d25ac GetConsoleOriginalTitleA
0x6d25b0 GetCurrencyFormatA
0x6d25b4 GetCurrentDirectoryW
0x6d25b8 GetDiskFreeSpaceExA
0x6d25bc GetDllDirectoryW
0x6d25c0 GetEraNameCountedString
0x6d25c4 GetFileSizeEx
0x6d25c8 GetOverlappedResult
0x6d25cc GetProcAddress
0x6d25d0 GetQueuedCompletionStatusEx
0x6d25d4 GetShortPathNameW
0x6d25d8 GetStringTypeA
0x6d25dc GetSystemDefaultLocaleName
0x6d25e0 GetSystemPreferredUILanguages
0x6d25e4 GetTempPathW
0x6d25e8 GetTimeFormatW
0x6d25ec GetTimeZoneInformationForYear
0x6d25f0 GetUserGeoID
0x6d25f4 GetVersionExW
0x6d25f8 GetVolumeNameForVolumeMountPointA
0x6d25fc GetVolumeNameForVolumeMountPointW
0x6d2600 GetWriteWatch
0x6d2604 GlobalFindAtomW
0x6d2608 GlobalMemoryStatusEx
0x6d260c InterlockedPopEntrySList
0x6d2610 IsBadHugeWritePtr
0x6d2614 IsValidLocale
0x6d2618 LZStart
0x6d261c LoadLibraryA
0x6d2620 LockFile
0x6d2624 MoveFileTransactedW
0x6d2628 OpenMutexW
0x6d262c PostQueuedCompletionStatus
0x6d2630 PrivMoveFileIdentityW
0x6d2634 QueryDepthSList
0x6d2638 QueryProcessAffinityUpdateMode
0x6d263c QueueUserWorkItem
0x6d2640 ReadConsoleInputExA
0x6d2644 ResetWriteWatch
0x6d2648 ResolveLocaleName
0x6d264c SetCommState
0x6d2650 SetComputerNameExW
0x6d2654 SetConsoleTitleW
0x6d2658 SetDefaultCommConfigA
0x6d265c SetDefaultCommConfigW
0x6d2660 SetDefaultDllDirectories
0x6d2664 SetDynamicTimeZoneInformation
0x6d2668 SetEnvironmentStringsA
0x6d266c SetFileBandwidthReservation
0x6d2670 SetNamedPipeAttribute
0x6d2674 SetSearchPathMode
0x6d2678 SetThreadpoolThreadMinimum
0x6d267c SetTimerQueueTimer
0x6d2680 SetUnhandledExceptionFilter
0x6d2684 SignalObjectAndWait
0x6d2688 SleepConditionVariableCS
0x6d268c TryAcquireSRWLockShared
0x6d2690 TzSpecificLocalTimeToSystemTimeEx
0x6d2694 UnlockFile
0x6d2698 WaitForMultipleObjectsEx
0x6d269c WerGetFlags
0x6d26a0 lstrlenW
msvcrt.dll
0x6d26a8 _chgsign
0x6d26ac _stricoll
0x6d26b0 _wcsnset
0x6d26b4 clock
0x6d26b8 fclose
0x6d26bc feof
0x6d26c0 fgets
0x6d26c4 fputws
0x6d26c8 free
0x6d26cc getc
0x6d26d0 isspace
0x6d26d4 iswalpha
0x6d26d8 malloc
0x6d26dc mbtowc
0x6d26e0 memcpy
0x6d26e4 memset
0x6d26e8 rand
0x6d26ec strcat
0x6d26f0 strcpy_s
0x6d26f4 strcspn
0x6d26f8 strerror
0x6d26fc strlen
0x6d2700 strrchr
0x6d2704 swprintf_s
0x6d2708 swscanf_s
0x6d270c ungetwc
SHELL32.dll
0x6d2714 AssocGetDetailsOfPropKey
0x6d2718 DragQueryPoint
0x6d271c ExtractIconEx
0x6d2720 GetCurrentProcessExplicitAppUserModelID
0x6d2724 ILFree
0x6d2728 IsNetDrive
0x6d272c PifMgr_CloseProperties
0x6d2730 RestartDialog
0x6d2734 SHBindToFolderIDListParentEx
0x6d2738 SHBindToParent
0x6d273c SHCreateDirectoryExA
0x6d2740 SHCreateItemInKnownFolder
0x6d2744 SHCreateStdEnumFmtEtc
0x6d2748 SHGetFolderPathAndSubDirW
0x6d274c SHGetKnownFolderIDList
0x6d2750 SHGetKnownFolderItem
0x6d2754 SHGetNewLinkInfo
0x6d2758 SHGetNewLinkInfoA
0x6d275c SHGetSettings
0x6d2760 SHSetFolderPathW
USER32.dll
0x6d2768 AttachThreadInput
0x6d276c CallMsgFilterA
0x6d2770 CascadeChildWindows
0x6d2774 CharPrevW
0x6d2778 CheckWindowThreadDesktop
0x6d277c CloseWindow
0x6d2780 CreateSystemThreads
0x6d2784 DefMDIChildProcA
0x6d2788 DestroyCaret
0x6d278c DisplayConfigGetDeviceInfo
0x6d2790 EnterReaderModeHelper
0x6d2794 EnumDesktopWindows
0x6d2798 GetAltTabInfoA
0x6d279c GetClassNameA
0x6d27a0 GetClassNameW
0x6d27a4 GetCursor
0x6d27a8 GetDialogBaseUnits
0x6d27ac GetGuiResources
0x6d27b0 GetKBCodePage
0x6d27b4 GetLastInputInfo
0x6d27b8 GetMenuItemCount
0x6d27bc GetWindow
0x6d27c0 GetWindowCompositionInfo
0x6d27c4 GetWindowDC
0x6d27c8 GetWindowLongA
0x6d27cc GetWindowModuleFileName
0x6d27d0 IsCharUpperW
0x6d27d4 IsChild
0x6d27d8 LoadAcceleratorsA
0x6d27dc LoadStringA
0x6d27e0 LoadStringW
0x6d27e4 MessageBeep
0x6d27e8 MessageBoxExW
0x6d27ec PaintMenuBar
0x6d27f0 RegisterErrorReportingDialog
0x6d27f4 RegisterTasklist
0x6d27f8 RemoveClipboardFormatListener
0x6d27fc ScreenToClient
0x6d2800 SendMessageTimeoutA
0x6d2804 SetGestureConfig
0x6d2808 SetScrollPos
0x6d280c ShowSystemCursor
0x6d2810 ShutdownBlockReasonDestroy
0x6d2814 TrackPopupMenuEx
0x6d2818 TranslateAcceleratorW
0x6d281c TranslateMessage
0x6d2820 UnregisterDeviceNotification
0x6d2824 UnregisterPowerSettingNotification
0x6d2828 WinHelpW
EAT(Export Address Table) is none
GDI32.dll
0x6d2454 ChoosePixelFormat
0x6d2458 CombineRgn
0x6d245c CreateCompatibleBitmap
0x6d2460 CreateICW
0x6d2464 CreatePen
0x6d2468 EndGdiRendering
0x6d246c EndPage
0x6d2470 EngDeleteClip
0x6d2474 EngQueryEMFInfo
0x6d2478 EngStretchBltROP
0x6d247c EngTransparentBlt
0x6d2480 EngUnicodeToMultiByteN
0x6d2484 FixBrushOrgEx
0x6d2488 GdiConvertBitmapV5
0x6d248c GdiDeleteSpoolFileHandle
0x6d2490 GdiFullscreenControl
0x6d2494 GdiIsMetaPrintDC
0x6d2498 GdiStartPageEMF
0x6d249c GetCharacterPlacementA
0x6d24a0 GetColorSpace
0x6d24a4 GetETM
0x6d24a8 GetEnhMetaFileW
0x6d24ac GetFontRealizationInfo
0x6d24b0 GetICMProfileA
0x6d24b4 GetICMProfileW
0x6d24b8 GetMapMode
0x6d24bc GetMiterLimit
0x6d24c0 GetOutlineTextMetricsW
0x6d24c4 GetROP2
0x6d24c8 GetTextExtentExPointW
0x6d24cc GetTextExtentPointI
0x6d24d0 GetTextFaceA
0x6d24d4 MoveToEx
0x6d24d8 NamedEscape
0x6d24dc OffsetClipRgn
0x6d24e0 OffsetRgn
0x6d24e4 PATHOBJ_bEnum
0x6d24e8 PATHOBJ_bEnumClipLines
0x6d24ec PaintRgn
0x6d24f0 PlgBlt
0x6d24f4 PolyTextOutA
0x6d24f8 Polygon
0x6d24fc QueryFontAssocStatus
0x6d2500 RealizePalette
0x6d2504 RemoveFontResourceA
0x6d2508 ResetDCW
0x6d250c STROBJ_bEnum
0x6d2510 STROBJ_dwGetCodePage
0x6d2514 SelectClipPath
0x6d2518 SelectFontLocal
0x6d251c SetDCPenColor
0x6d2520 SetGraphicsMode
0x6d2524 SetMetaFileBitsEx
0x6d2528 SetRectRgn
0x6d252c SetTextCharacterExtra
KERNEL32.dll
0x6d2534 CloseThreadpoolTimer
0x6d2538 CompareStringOrdinal
0x6d253c CreateDirectoryA
0x6d2540 CreateDirectoryW
0x6d2544 CreateHardLinkA
0x6d2548 CreateMutexExW
0x6d254c CreateProcessA
0x6d2550 CreateThreadpool
0x6d2554 CreateTimerQueueTimer
0x6d2558 CtrlRoutine
0x6d255c DeleteFileTransactedW
0x6d2560 DeleteProcThreadAttributeList
0x6d2564 DeleteTimerQueueTimer
0x6d2568 EnumDateFormatsA
0x6d256c EnumResourceTypesExW
0x6d2570 EnumTimeFormatsA
0x6d2574 EnumUILanguagesA
0x6d2578 ExitVDM
0x6d257c FileTimeToLocalFileTime
0x6d2580 FindFirstFileExA
0x6d2584 FindNextFileW
0x6d2588 FlsSetValue
0x6d258c FreeEnvironmentStringsA
0x6d2590 FreeLibrary
0x6d2594 GetACP
0x6d2598 GetCalendarDaysInMonth
0x6d259c GetCalendarInfoA
0x6d25a0 GetCalendarSupportedDateRange
0x6d25a4 GetConsoleAliasExesW
0x6d25a8 GetConsoleFontSize
0x6d25ac GetConsoleOriginalTitleA
0x6d25b0 GetCurrencyFormatA
0x6d25b4 GetCurrentDirectoryW
0x6d25b8 GetDiskFreeSpaceExA
0x6d25bc GetDllDirectoryW
0x6d25c0 GetEraNameCountedString
0x6d25c4 GetFileSizeEx
0x6d25c8 GetOverlappedResult
0x6d25cc GetProcAddress
0x6d25d0 GetQueuedCompletionStatusEx
0x6d25d4 GetShortPathNameW
0x6d25d8 GetStringTypeA
0x6d25dc GetSystemDefaultLocaleName
0x6d25e0 GetSystemPreferredUILanguages
0x6d25e4 GetTempPathW
0x6d25e8 GetTimeFormatW
0x6d25ec GetTimeZoneInformationForYear
0x6d25f0 GetUserGeoID
0x6d25f4 GetVersionExW
0x6d25f8 GetVolumeNameForVolumeMountPointA
0x6d25fc GetVolumeNameForVolumeMountPointW
0x6d2600 GetWriteWatch
0x6d2604 GlobalFindAtomW
0x6d2608 GlobalMemoryStatusEx
0x6d260c InterlockedPopEntrySList
0x6d2610 IsBadHugeWritePtr
0x6d2614 IsValidLocale
0x6d2618 LZStart
0x6d261c LoadLibraryA
0x6d2620 LockFile
0x6d2624 MoveFileTransactedW
0x6d2628 OpenMutexW
0x6d262c PostQueuedCompletionStatus
0x6d2630 PrivMoveFileIdentityW
0x6d2634 QueryDepthSList
0x6d2638 QueryProcessAffinityUpdateMode
0x6d263c QueueUserWorkItem
0x6d2640 ReadConsoleInputExA
0x6d2644 ResetWriteWatch
0x6d2648 ResolveLocaleName
0x6d264c SetCommState
0x6d2650 SetComputerNameExW
0x6d2654 SetConsoleTitleW
0x6d2658 SetDefaultCommConfigA
0x6d265c SetDefaultCommConfigW
0x6d2660 SetDefaultDllDirectories
0x6d2664 SetDynamicTimeZoneInformation
0x6d2668 SetEnvironmentStringsA
0x6d266c SetFileBandwidthReservation
0x6d2670 SetNamedPipeAttribute
0x6d2674 SetSearchPathMode
0x6d2678 SetThreadpoolThreadMinimum
0x6d267c SetTimerQueueTimer
0x6d2680 SetUnhandledExceptionFilter
0x6d2684 SignalObjectAndWait
0x6d2688 SleepConditionVariableCS
0x6d268c TryAcquireSRWLockShared
0x6d2690 TzSpecificLocalTimeToSystemTimeEx
0x6d2694 UnlockFile
0x6d2698 WaitForMultipleObjectsEx
0x6d269c WerGetFlags
0x6d26a0 lstrlenW
msvcrt.dll
0x6d26a8 _chgsign
0x6d26ac _stricoll
0x6d26b0 _wcsnset
0x6d26b4 clock
0x6d26b8 fclose
0x6d26bc feof
0x6d26c0 fgets
0x6d26c4 fputws
0x6d26c8 free
0x6d26cc getc
0x6d26d0 isspace
0x6d26d4 iswalpha
0x6d26d8 malloc
0x6d26dc mbtowc
0x6d26e0 memcpy
0x6d26e4 memset
0x6d26e8 rand
0x6d26ec strcat
0x6d26f0 strcpy_s
0x6d26f4 strcspn
0x6d26f8 strerror
0x6d26fc strlen
0x6d2700 strrchr
0x6d2704 swprintf_s
0x6d2708 swscanf_s
0x6d270c ungetwc
SHELL32.dll
0x6d2714 AssocGetDetailsOfPropKey
0x6d2718 DragQueryPoint
0x6d271c ExtractIconEx
0x6d2720 GetCurrentProcessExplicitAppUserModelID
0x6d2724 ILFree
0x6d2728 IsNetDrive
0x6d272c PifMgr_CloseProperties
0x6d2730 RestartDialog
0x6d2734 SHBindToFolderIDListParentEx
0x6d2738 SHBindToParent
0x6d273c SHCreateDirectoryExA
0x6d2740 SHCreateItemInKnownFolder
0x6d2744 SHCreateStdEnumFmtEtc
0x6d2748 SHGetFolderPathAndSubDirW
0x6d274c SHGetKnownFolderIDList
0x6d2750 SHGetKnownFolderItem
0x6d2754 SHGetNewLinkInfo
0x6d2758 SHGetNewLinkInfoA
0x6d275c SHGetSettings
0x6d2760 SHSetFolderPathW
USER32.dll
0x6d2768 AttachThreadInput
0x6d276c CallMsgFilterA
0x6d2770 CascadeChildWindows
0x6d2774 CharPrevW
0x6d2778 CheckWindowThreadDesktop
0x6d277c CloseWindow
0x6d2780 CreateSystemThreads
0x6d2784 DefMDIChildProcA
0x6d2788 DestroyCaret
0x6d278c DisplayConfigGetDeviceInfo
0x6d2790 EnterReaderModeHelper
0x6d2794 EnumDesktopWindows
0x6d2798 GetAltTabInfoA
0x6d279c GetClassNameA
0x6d27a0 GetClassNameW
0x6d27a4 GetCursor
0x6d27a8 GetDialogBaseUnits
0x6d27ac GetGuiResources
0x6d27b0 GetKBCodePage
0x6d27b4 GetLastInputInfo
0x6d27b8 GetMenuItemCount
0x6d27bc GetWindow
0x6d27c0 GetWindowCompositionInfo
0x6d27c4 GetWindowDC
0x6d27c8 GetWindowLongA
0x6d27cc GetWindowModuleFileName
0x6d27d0 IsCharUpperW
0x6d27d4 IsChild
0x6d27d8 LoadAcceleratorsA
0x6d27dc LoadStringA
0x6d27e0 LoadStringW
0x6d27e4 MessageBeep
0x6d27e8 MessageBoxExW
0x6d27ec PaintMenuBar
0x6d27f0 RegisterErrorReportingDialog
0x6d27f4 RegisterTasklist
0x6d27f8 RemoveClipboardFormatListener
0x6d27fc ScreenToClient
0x6d2800 SendMessageTimeoutA
0x6d2804 SetGestureConfig
0x6d2808 SetScrollPos
0x6d280c ShowSystemCursor
0x6d2810 ShutdownBlockReasonDestroy
0x6d2814 TrackPopupMenuEx
0x6d2818 TranslateAcceleratorW
0x6d281c TranslateMessage
0x6d2820 UnregisterDeviceNotification
0x6d2824 UnregisterPowerSettingNotification
0x6d2828 WinHelpW
EAT(Export Address Table) is none