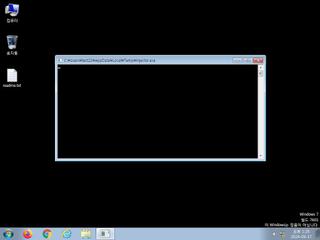
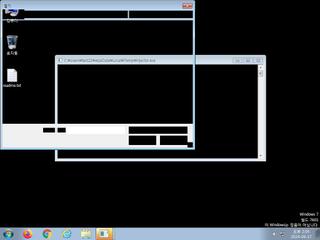
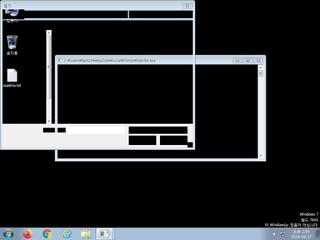
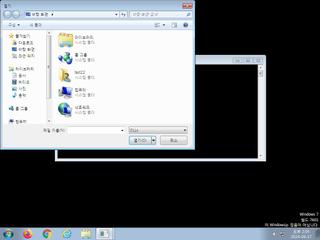
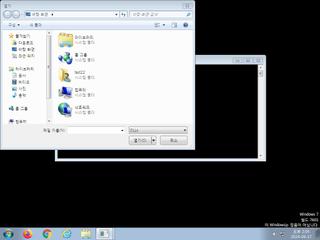
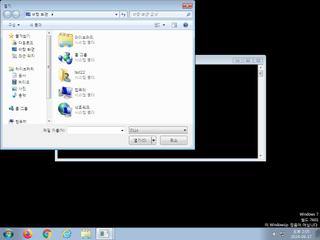
ScreenShot
| Created | 2024.09.17 14:06 | Machine | s1_win7_x6401 |
| Filename | injector.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 16 detected (GenericKD, FileRepMalware, Misc, Detected, ABRisk, HRBL, Artemis, MALICIOUS) | ||
| md5 | c44b5e54b7b3d5494612bf666d4ea9d3 | ||
| sha256 | b1bb075756076ada2b6afbb7da70b8aab44b7bdcdd91fbab77872286e708d8d5 | ||
| ssdeep | 96:5hCHKHfsrFbQEw5Yl3+TCqv+ktYhwYLNDKD0FnuGNDq1c/WkEPM7DhZD+MCt:5hFfsrF4O3UoB6oW0Fnvwc/HEPMXT+H | ||
| imphash | 9f4525c3c1b8fb4c3706f52d18677db1 | ||
| impfuzzy | 12:yJcDpzhZJzAtVzhr0KPXJ1XJwdTRzwDfL/D1F6XvG+G8UwJYKtdVBQ1HzVgEI:wcDpzb18Vzd0yLKxwLL/5F6O58vldwpO | ||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 16 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates a shortcut to an executable file |
| info | Checks amount of memory in system |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Queries for the computername |
| info | This executable has a PDB path |
Rules (2cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x140002010 Sleep
0x140002018 GetLastError
0x140002020 GetProcAddress
0x140002028 VirtualAllocEx
0x140002030 OpenProcess
0x140002038 CloseHandle
0x140002040 WriteProcessMemory
0x140002048 GetSystemTimeAsFileTime
0x140002050 GetCurrentProcessId
0x140002058 GetModuleHandleA
0x140002060 CreateRemoteThread
0x140002068 GetTickCount
0x140002070 QueryPerformanceCounter
0x140002078 DecodePointer
0x140002080 RtlCaptureContext
0x140002088 RtlLookupFunctionEntry
0x140002090 RtlVirtualUnwind
0x140002098 IsDebuggerPresent
0x1400020a0 SetUnhandledExceptionFilter
0x1400020a8 UnhandledExceptionFilter
0x1400020b0 GetCurrentProcess
0x1400020b8 TerminateProcess
0x1400020c0 EncodePointer
0x1400020c8 GetCurrentThreadId
USER32.dll
0x1400021a8 MessageBoxA
COMDLG32.dll
0x140002000 GetOpenFileNameA
MSVCR100.dll
0x1400020d8 _configthreadlocale
0x1400020e0 __setusermatherr
0x1400020e8 _commode
0x1400020f0 _fmode
0x1400020f8 __set_app_type
0x140002100 __crt_debugger_hook
0x140002108 ?terminate@@YAXXZ
0x140002110 _unlock
0x140002118 __dllonexit
0x140002120 _lock
0x140002128 _onexit
0x140002130 _initterm
0x140002138 __initenv
0x140002140 _cexit
0x140002148 _exit
0x140002150 _XcptFilter
0x140002158 __C_specific_handler
0x140002160 __getmainargs
0x140002168 _amsg_exit
0x140002170 exit
0x140002178 printf
0x140002180 scanf
0x140002188 vsprintf
0x140002190 _initterm_e
0x140002198 memset
EAT(Export Address Table) is none
KERNEL32.dll
0x140002010 Sleep
0x140002018 GetLastError
0x140002020 GetProcAddress
0x140002028 VirtualAllocEx
0x140002030 OpenProcess
0x140002038 CloseHandle
0x140002040 WriteProcessMemory
0x140002048 GetSystemTimeAsFileTime
0x140002050 GetCurrentProcessId
0x140002058 GetModuleHandleA
0x140002060 CreateRemoteThread
0x140002068 GetTickCount
0x140002070 QueryPerformanceCounter
0x140002078 DecodePointer
0x140002080 RtlCaptureContext
0x140002088 RtlLookupFunctionEntry
0x140002090 RtlVirtualUnwind
0x140002098 IsDebuggerPresent
0x1400020a0 SetUnhandledExceptionFilter
0x1400020a8 UnhandledExceptionFilter
0x1400020b0 GetCurrentProcess
0x1400020b8 TerminateProcess
0x1400020c0 EncodePointer
0x1400020c8 GetCurrentThreadId
USER32.dll
0x1400021a8 MessageBoxA
COMDLG32.dll
0x140002000 GetOpenFileNameA
MSVCR100.dll
0x1400020d8 _configthreadlocale
0x1400020e0 __setusermatherr
0x1400020e8 _commode
0x1400020f0 _fmode
0x1400020f8 __set_app_type
0x140002100 __crt_debugger_hook
0x140002108 ?terminate@@YAXXZ
0x140002110 _unlock
0x140002118 __dllonexit
0x140002120 _lock
0x140002128 _onexit
0x140002130 _initterm
0x140002138 __initenv
0x140002140 _cexit
0x140002148 _exit
0x140002150 _XcptFilter
0x140002158 __C_specific_handler
0x140002160 __getmainargs
0x140002168 _amsg_exit
0x140002170 exit
0x140002178 printf
0x140002180 scanf
0x140002188 vsprintf
0x140002190 _initterm_e
0x140002198 memset
EAT(Export Address Table) is none