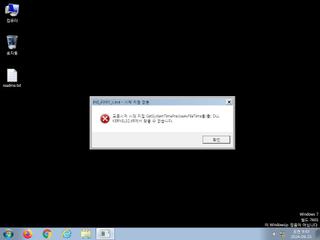
ScreenShot
| Created | 2024.09.23 09:52 | Machine | s1_win7_x6401 |
| Filename | inst_4WKY_x.exe | ||
| Type | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 6 detected (AIDetectMalware, malicious, confidence, Attribute, HighConfidence, XWorm) | ||
| md5 | ce0639cb84857bd4ad992206e7369cb9 | ||
| sha256 | e6e07cde3550631edba2fdf14825cb64f97a06715fca13cea78e6f85a0481f14 | ||
| ssdeep | 24576:1Hm7GnfHOGiTGzXzJ0Zduvfv5/iM6eBvOeMxRXm98tyMq0:pm7GfuGia0Zduvfv6wGeyla8ty | ||
| imphash | 8d489fb407dee81072c055a97f32e2d1 | ||
| impfuzzy | 96:8fpcmGWJGaRqtWbxxttN0yAqnHVblxDKXHg7:tactWnttN0yATw7 | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| notice | File has been identified by 6 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1400fd688 DeleteCriticalSection
0x1400fd690 EnterCriticalSection
0x1400fd698 InitializeCriticalSection
0x1400fd6a0 LeaveCriticalSection
0x1400fd6a8 RaiseException
0x1400fd6b0 RtlUnwindEx
0x1400fd6b8 VirtualProtect
0x1400fd6c0 VirtualQuery
0x1400fd6c8 __C_specific_handler
msvcrt.dll
0x1400fd6d8 __getmainargs
0x1400fd6e0 __initenv
0x1400fd6e8 __iob_func
0x1400fd6f0 __set_app_type
0x1400fd6f8 __setusermatherr
0x1400fd700 _amsg_exit
0x1400fd708 _cexit
0x1400fd710 _commode
0x1400fd718 _fmode
0x1400fd720 _fpreset
0x1400fd728 _initterm
0x1400fd730 _onexit
0x1400fd738 abort
0x1400fd740 calloc
0x1400fd748 exit
0x1400fd750 fprintf
0x1400fd758 free
0x1400fd760 fwrite
0x1400fd768 malloc
0x1400fd770 memcmp
0x1400fd778 memcpy
0x1400fd780 memmove
0x1400fd788 memset
0x1400fd790 signal
0x1400fd798 strlen
0x1400fd7a0 strncmp
0x1400fd7a8 vfprintf
ntdll.dll
0x1400fd7b8 NtCreateFile
0x1400fd7c0 NtReadFile
0x1400fd7c8 NtWriteFile
0x1400fd7d0 RtlNtStatusToDosError
USERENV.dll
0x1400fd7e0 GetUserProfileDirectoryW
WS2_32.dll
0x1400fd7f0 WSACleanup
0x1400fd7f8 WSADuplicateSocketW
0x1400fd800 WSAGetLastError
0x1400fd808 WSARecv
0x1400fd810 WSASend
0x1400fd818 WSASocketW
0x1400fd820 WSAStartup
0x1400fd828 accept
0x1400fd830 ind
0x1400fd838 closesocket
0x1400fd840 connect
0x1400fd848 freeaddrinfo
0x1400fd850 getaddrinfo
0x1400fd858 getpeername
0x1400fd860 getsockname
0x1400fd868 getsockopt
0x1400fd870 ioctlsocket
0x1400fd878 listen
0x1400fd880 recv
0x1400fd888 recvfrom
0x1400fd890 select
0x1400fd898 send
0x1400fd8a0 sendto
0x1400fd8a8 setsockopt
0x1400fd8b0 shutdown
KERNEL32.dll
0x1400fd8c0 AddVectoredExceptionHandler
0x1400fd8c8 CancelIo
0x1400fd8d0 CloseHandle
0x1400fd8d8 CompareStringOrdinal
0x1400fd8e0 CopyFileExW
0x1400fd8e8 CreateDirectoryW
0x1400fd8f0 CreateEventW
0x1400fd8f8 CreateFileMappingA
0x1400fd900 CreateFileW
0x1400fd908 CreateHardLinkW
0x1400fd910 CreateMutexA
0x1400fd918 CreateNamedPipeW
0x1400fd920 CreateProcessW
0x1400fd928 CreateSymbolicLinkW
0x1400fd930 CreateThread
0x1400fd938 CreateTimerQueue
0x1400fd940 CreateTimerQueueTimer
0x1400fd948 CreateToolhelp32Snapshot
0x1400fd950 CreateWaitableTimerExW
0x1400fd958 DeleteFileW
0x1400fd960 DeleteProcThreadAttributeList
0x1400fd968 DeleteTimerQueue
0x1400fd970 DeviceIoControl
0x1400fd978 DuplicateHandle
0x1400fd980 ExitProcess
0x1400fd988 FindClose
0x1400fd990 FindFirstFileW
0x1400fd998 FindNextFileW
0x1400fd9a0 FlushFileBuffers
0x1400fd9a8 FormatMessageW
0x1400fd9b0 FreeEnvironmentStringsW
0x1400fd9b8 GetCommandLineW
0x1400fd9c0 GetConsoleMode
0x1400fd9c8 GetCurrentDirectoryW
0x1400fd9d0 GetCurrentProcess
0x1400fd9d8 GetCurrentProcessId
0x1400fd9e0 GetCurrentThread
0x1400fd9e8 GetEnvironmentStringsW
0x1400fd9f0 GetEnvironmentVariableW
0x1400fd9f8 GetExitCodeProcess
0x1400fda00 GetFileAttributesW
0x1400fda08 GetFileInformationByHandle
0x1400fda10 GetFileInformationByHandleEx
0x1400fda18 GetFileType
0x1400fda20 GetFinalPathNameByHandleW
0x1400fda28 GetFullPathNameW
0x1400fda30 GetLastError
0x1400fda38 GetModuleFileNameW
0x1400fda40 GetModuleHandleA
0x1400fda48 GetModuleHandleW
0x1400fda50 GetOverlappedResult
0x1400fda58 GetProcAddress
0x1400fda60 GetProcessHeap
0x1400fda68 GetProcessId
0x1400fda70 GetStdHandle
0x1400fda78 GetSystemDirectoryW
0x1400fda80 GetSystemInfo
0x1400fda88 GetSystemTimePreciseAsFileTime
0x1400fda90 GetTempPathW
0x1400fda98 GetWindowsDirectoryW
0x1400fdaa0 HeapAlloc
0x1400fdaa8 HeapCreate
0x1400fdab0 HeapFree
0x1400fdab8 HeapReAlloc
0x1400fdac0 InitOnceBeginInitialize
0x1400fdac8 InitOnceComplete
0x1400fdad0 InitializeProcThreadAttributeList
0x1400fdad8 LoadLibraryA
0x1400fdae0 MapViewOfFile
0x1400fdae8 Module32FirstW
0x1400fdaf0 Module32NextW
0x1400fdaf8 MoveFileExW
0x1400fdb00 MultiByteToWideChar
0x1400fdb08 QueryPerformanceCounter
0x1400fdb10 QueryPerformanceFrequency
0x1400fdb18 ReadConsoleW
0x1400fdb20 ReadFile
0x1400fdb28 ReadFileEx
0x1400fdb30 RemoveDirectoryW
0x1400fdb38 RtlCaptureContext
0x1400fdb40 RtlLookupFunctionEntry
0x1400fdb48 RtlVirtualUnwind
0x1400fdb50 SetCurrentDirectoryW
0x1400fdb58 SetEnvironmentVariableW
0x1400fdb60 SetFileAttributesW
0x1400fdb68 SetFileInformationByHandle
0x1400fdb70 SetFilePointerEx
0x1400fdb78 SetFileTime
0x1400fdb80 SetHandleInformation
0x1400fdb88 SetLastError
0x1400fdb90 SetThreadStackGuarantee
0x1400fdb98 SetUnhandledExceptionFilter
0x1400fdba0 SetWaitableTimer
0x1400fdba8 Sleep
0x1400fdbb0 SleepEx
0x1400fdbb8 SwitchToThread
0x1400fdbc0 TerminateProcess
0x1400fdbc8 TlsAlloc
0x1400fdbd0 TlsFree
0x1400fdbd8 TlsGetValue
0x1400fdbe0 TlsSetValue
0x1400fdbe8 UnmapViewOfFile
0x1400fdbf0 UpdateProcThreadAttribute
0x1400fdbf8 WaitForMultipleObjects
0x1400fdc00 WaitForSingleObject
0x1400fdc08 WideCharToMultiByte
0x1400fdc10 WriteConsoleW
0x1400fdc18 WriteFileEx
api-ms-win-core-synch-l1-2-0.dll
0x1400fdc28 WaitOnAddress
0x1400fdc30 WakeByAddressAll
0x1400fdc38 WakeByAddressSingle
cryptprimitives.dll
0x1400fdc48 ProcessPrng
EAT(Export Address Table) is none
KERNEL32.dll
0x1400fd688 DeleteCriticalSection
0x1400fd690 EnterCriticalSection
0x1400fd698 InitializeCriticalSection
0x1400fd6a0 LeaveCriticalSection
0x1400fd6a8 RaiseException
0x1400fd6b0 RtlUnwindEx
0x1400fd6b8 VirtualProtect
0x1400fd6c0 VirtualQuery
0x1400fd6c8 __C_specific_handler
msvcrt.dll
0x1400fd6d8 __getmainargs
0x1400fd6e0 __initenv
0x1400fd6e8 __iob_func
0x1400fd6f0 __set_app_type
0x1400fd6f8 __setusermatherr
0x1400fd700 _amsg_exit
0x1400fd708 _cexit
0x1400fd710 _commode
0x1400fd718 _fmode
0x1400fd720 _fpreset
0x1400fd728 _initterm
0x1400fd730 _onexit
0x1400fd738 abort
0x1400fd740 calloc
0x1400fd748 exit
0x1400fd750 fprintf
0x1400fd758 free
0x1400fd760 fwrite
0x1400fd768 malloc
0x1400fd770 memcmp
0x1400fd778 memcpy
0x1400fd780 memmove
0x1400fd788 memset
0x1400fd790 signal
0x1400fd798 strlen
0x1400fd7a0 strncmp
0x1400fd7a8 vfprintf
ntdll.dll
0x1400fd7b8 NtCreateFile
0x1400fd7c0 NtReadFile
0x1400fd7c8 NtWriteFile
0x1400fd7d0 RtlNtStatusToDosError
USERENV.dll
0x1400fd7e0 GetUserProfileDirectoryW
WS2_32.dll
0x1400fd7f0 WSACleanup
0x1400fd7f8 WSADuplicateSocketW
0x1400fd800 WSAGetLastError
0x1400fd808 WSARecv
0x1400fd810 WSASend
0x1400fd818 WSASocketW
0x1400fd820 WSAStartup
0x1400fd828 accept
0x1400fd830 ind
0x1400fd838 closesocket
0x1400fd840 connect
0x1400fd848 freeaddrinfo
0x1400fd850 getaddrinfo
0x1400fd858 getpeername
0x1400fd860 getsockname
0x1400fd868 getsockopt
0x1400fd870 ioctlsocket
0x1400fd878 listen
0x1400fd880 recv
0x1400fd888 recvfrom
0x1400fd890 select
0x1400fd898 send
0x1400fd8a0 sendto
0x1400fd8a8 setsockopt
0x1400fd8b0 shutdown
KERNEL32.dll
0x1400fd8c0 AddVectoredExceptionHandler
0x1400fd8c8 CancelIo
0x1400fd8d0 CloseHandle
0x1400fd8d8 CompareStringOrdinal
0x1400fd8e0 CopyFileExW
0x1400fd8e8 CreateDirectoryW
0x1400fd8f0 CreateEventW
0x1400fd8f8 CreateFileMappingA
0x1400fd900 CreateFileW
0x1400fd908 CreateHardLinkW
0x1400fd910 CreateMutexA
0x1400fd918 CreateNamedPipeW
0x1400fd920 CreateProcessW
0x1400fd928 CreateSymbolicLinkW
0x1400fd930 CreateThread
0x1400fd938 CreateTimerQueue
0x1400fd940 CreateTimerQueueTimer
0x1400fd948 CreateToolhelp32Snapshot
0x1400fd950 CreateWaitableTimerExW
0x1400fd958 DeleteFileW
0x1400fd960 DeleteProcThreadAttributeList
0x1400fd968 DeleteTimerQueue
0x1400fd970 DeviceIoControl
0x1400fd978 DuplicateHandle
0x1400fd980 ExitProcess
0x1400fd988 FindClose
0x1400fd990 FindFirstFileW
0x1400fd998 FindNextFileW
0x1400fd9a0 FlushFileBuffers
0x1400fd9a8 FormatMessageW
0x1400fd9b0 FreeEnvironmentStringsW
0x1400fd9b8 GetCommandLineW
0x1400fd9c0 GetConsoleMode
0x1400fd9c8 GetCurrentDirectoryW
0x1400fd9d0 GetCurrentProcess
0x1400fd9d8 GetCurrentProcessId
0x1400fd9e0 GetCurrentThread
0x1400fd9e8 GetEnvironmentStringsW
0x1400fd9f0 GetEnvironmentVariableW
0x1400fd9f8 GetExitCodeProcess
0x1400fda00 GetFileAttributesW
0x1400fda08 GetFileInformationByHandle
0x1400fda10 GetFileInformationByHandleEx
0x1400fda18 GetFileType
0x1400fda20 GetFinalPathNameByHandleW
0x1400fda28 GetFullPathNameW
0x1400fda30 GetLastError
0x1400fda38 GetModuleFileNameW
0x1400fda40 GetModuleHandleA
0x1400fda48 GetModuleHandleW
0x1400fda50 GetOverlappedResult
0x1400fda58 GetProcAddress
0x1400fda60 GetProcessHeap
0x1400fda68 GetProcessId
0x1400fda70 GetStdHandle
0x1400fda78 GetSystemDirectoryW
0x1400fda80 GetSystemInfo
0x1400fda88 GetSystemTimePreciseAsFileTime
0x1400fda90 GetTempPathW
0x1400fda98 GetWindowsDirectoryW
0x1400fdaa0 HeapAlloc
0x1400fdaa8 HeapCreate
0x1400fdab0 HeapFree
0x1400fdab8 HeapReAlloc
0x1400fdac0 InitOnceBeginInitialize
0x1400fdac8 InitOnceComplete
0x1400fdad0 InitializeProcThreadAttributeList
0x1400fdad8 LoadLibraryA
0x1400fdae0 MapViewOfFile
0x1400fdae8 Module32FirstW
0x1400fdaf0 Module32NextW
0x1400fdaf8 MoveFileExW
0x1400fdb00 MultiByteToWideChar
0x1400fdb08 QueryPerformanceCounter
0x1400fdb10 QueryPerformanceFrequency
0x1400fdb18 ReadConsoleW
0x1400fdb20 ReadFile
0x1400fdb28 ReadFileEx
0x1400fdb30 RemoveDirectoryW
0x1400fdb38 RtlCaptureContext
0x1400fdb40 RtlLookupFunctionEntry
0x1400fdb48 RtlVirtualUnwind
0x1400fdb50 SetCurrentDirectoryW
0x1400fdb58 SetEnvironmentVariableW
0x1400fdb60 SetFileAttributesW
0x1400fdb68 SetFileInformationByHandle
0x1400fdb70 SetFilePointerEx
0x1400fdb78 SetFileTime
0x1400fdb80 SetHandleInformation
0x1400fdb88 SetLastError
0x1400fdb90 SetThreadStackGuarantee
0x1400fdb98 SetUnhandledExceptionFilter
0x1400fdba0 SetWaitableTimer
0x1400fdba8 Sleep
0x1400fdbb0 SleepEx
0x1400fdbb8 SwitchToThread
0x1400fdbc0 TerminateProcess
0x1400fdbc8 TlsAlloc
0x1400fdbd0 TlsFree
0x1400fdbd8 TlsGetValue
0x1400fdbe0 TlsSetValue
0x1400fdbe8 UnmapViewOfFile
0x1400fdbf0 UpdateProcThreadAttribute
0x1400fdbf8 WaitForMultipleObjects
0x1400fdc00 WaitForSingleObject
0x1400fdc08 WideCharToMultiByte
0x1400fdc10 WriteConsoleW
0x1400fdc18 WriteFileEx
api-ms-win-core-synch-l1-2-0.dll
0x1400fdc28 WaitOnAddress
0x1400fdc30 WakeByAddressAll
0x1400fdc38 WakeByAddressSingle
cryptprimitives.dll
0x1400fdc48 ProcessPrng
EAT(Export Address Table) is none