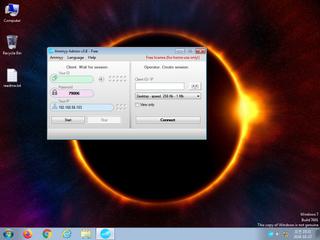
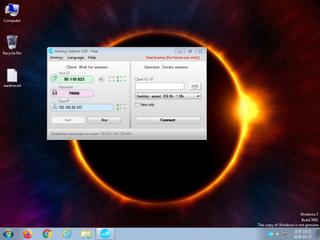
ScreenShot
| Created | 2024.10.17 11:04 | Machine | s1_win7_x6403 |
| Filename | AA_v3.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 55 detected (AIDetectMalware, Ammyy, Malicious, score, RemAdmAmmyy, RemoteAdmin, Unsafe, Uv94, grayware, confidence, 100%, Hacktool, high confidence, B potentially unsafe, MiscX, fmhliy, CLASSIC, Tool, remote, access, Generic Reputation PUA, Static AI, Malicious PE, Detected, BB@7z3yvj, PUADlManager, InstallCore, ABApplication, HDAV, RemAdm, MulDrop, Gencirc, YRMXaoj5DM0, AmmyyAdmin, Atncz) | ||
| md5 | 4d4c220362f24e0ba72797572e447795 | ||
| sha256 | bc483e6acdf276b57bb87317962c0091bb1421e61fa3306490b5858eabc61320 | ||
| ssdeep | 24576:B3YRddOnSok4fx2j2z5kMNbsRtrxc130jvs:+RenlHx2j2zxlkpj0 | ||
| imphash | 53059d798e2a15316406229bd2ddc5b6 | ||
| impfuzzy | 192:FgjX+yTwIaHcFWuKhUD7J0+HAlQXDLPEWFbwAE8Tq8otnqFp:oD4p+/J0+glQX/PEapTq8o5kp | ||
Network IP location
Signature (9cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 55 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| watch | Installs itself for autorun at Windows startup |
| notice | Creates a service |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Sends data using the HTTP POST Method |
| info | The executable uses a known packer |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Ammy_Admin_r0d | Ammy Admin | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (10cnts) ?
Suricata ids
ET POLICY IP Check (rl. ammyy. com)
PE API
IAT(Import Address Table) Library
WS2_32.dll
0x486830 WSAGetLastError
0x486834 send
0x486838 recv
0x48683c select
0x486840 WSAStartup
0x486844 getpeername
0x486848 getservbyport
0x48684c ntohs
0x486850 gethostbyaddr
0x486854 gethostbyname
0x486858 inet_addr
0x48685c getservbyname
0x486860 htonl
0x486864 inet_ntoa
0x486868 WSAIoctl
0x48686c connect
0x486870 accept
0x486874 htons
0x486878 ind
0x48687c listen
0x486880 socket
0x486884 __WSAFDIsSet
0x486888 shutdown
0x48688c setsockopt
0x486890 ioctlsocket
0x486894 WSACleanup
0x486898 closesocket
GDI32.dll
0x4860e8 GetDIBits
0x4860ec CreateCompatibleBitmap
0x4860f0 RealizePalette
0x4860f4 SelectPalette
0x4860f8 CreatePalette
0x4860fc GetSystemPaletteEntries
0x486100 GdiFlush
0x486104 CombineRgn
0x486108 GetRegionData
0x48610c SetStretchBltMode
0x486110 DeleteDC
0x486114 SelectObject
0x486118 CreateCompatibleDC
0x48611c BitBlt
0x486120 SetBkMode
0x486124 CreateFontIndirectA
0x486128 DPtoLP
0x48612c GetDeviceCaps
0x486130 CreateFontA
0x486134 CreateSolidBrush
0x486138 StretchBlt
0x48613c CreateRectRgn
0x486140 ExtTextOutA
0x486144 GetBitmapBits
0x486148 GetObjectA
0x48614c CreateDIBSection
0x486150 SetBitmapBits
0x486154 CreateRectRgnIndirect
0x486158 SelectClipRgn
0x48615c TextOutW
0x486160 CreatePatternBrush
0x486164 SetTextAlign
0x486168 SetBrushOrgEx
0x48616c ExtTextOutW
0x486170 SetTextColor
0x486174 SetBkColor
0x486178 CreateDIBitmap
0x48617c GetTextExtentPoint32W
0x486180 DeleteObject
0x486184 GetStockObject
USER32.dll
0x486578 FindWindowA
0x48657c OpenDesktopA
0x486580 LoadIconA
0x486584 SystemParametersInfoW
0x486588 IntersectRect
0x48658c IsWindowVisible
0x486590 GetIconInfo
0x486594 GetCursorInfo
0x486598 EqualRect
0x48659c OpenInputDesktop
0x4865a0 CloseDesktop
0x4865a4 GetUserObjectInformationA
0x4865a8 GetThreadDesktop
0x4865ac EmptyClipboard
0x4865b0 SetClipboardData
0x4865b4 RegisterClassExA
0x4865b8 GetDesktopWindow
0x4865bc PeekMessageA
0x4865c0 MsgWaitForMultipleObjects
0x4865c4 mouse_event
0x4865c8 SendInput
0x4865cc LockWorkStation
0x4865d0 SetThreadDesktop
0x4865d4 SetDlgItemTextA
0x4865d8 SetDlgItemInt
0x4865dc CallNextHookEx
0x4865e0 SetWindowsHookExA
0x4865e4 UnhookWindowsHookEx
0x4865e8 DestroyAcceleratorTable
0x4865ec TranslateAcceleratorA
0x4865f0 CreateAcceleratorTableA
0x4865f4 SetWindowTextA
0x4865f8 ReleaseCapture
0x4865fc SendMessageTimeoutA
0x486600 SwitchToThisWindow
0x486604 SendMessageA
0x486608 FindWindowW
0x48660c MessageBoxA
0x486610 ShowWindow
0x486614 wsprintfA
0x486618 SetCapture
0x48661c GetAsyncKeyState
0x486620 RegisterClassExW
0x486624 DestroyCursor
0x486628 MessageBeep
0x48662c wsprintfW
0x486630 SetCursorPos
0x486634 GetClipboardOwner
0x486638 OpenClipboard
0x48663c GetClipboardData
0x486640 CloseClipboard
0x486644 ShowWindowAsync
0x486648 SetScrollInfo
0x48664c ReleaseDC
0x486650 GetDC
0x486654 DestroyIcon
0x486658 DrawIconEx
0x48665c LoadImageA
0x486660 EnableWindow
0x486664 SetDlgItemTextW
0x486668 DestroyWindow
0x48666c SetWindowPos
0x486670 GetWindow
0x486674 WindowFromPoint
0x486678 SetClassLongW
0x48667c InsertMenuItemW
0x486680 ChangeClipboardChain
0x486684 MapWindowPoints
0x486688 InsertMenuItemA
0x48668c EnumWindows
0x486690 GetClassNameA
0x486694 GetWindowTextA
0x486698 KillTimer
0x48669c GetWindowLongW
0x4866a0 PostMessageA
0x4866a4 DrawTextW
0x4866a8 SetRect
0x4866ac ShowScrollBar
0x4866b0 IsIconic
0x4866b4 ScrollWindowEx
0x4866b8 AdjustWindowRectEx
0x4866bc GetMenuState
0x4866c0 GetWindowPlacement
0x4866c4 SetWindowPlacement
0x4866c8 GetSysColorBrush
0x4866cc AppendMenuW
0x4866d0 SetClipboardViewer
0x4866d4 DrawTextA
0x4866d8 EndDialog
0x4866dc CreateDialogParamW
0x4866e0 DialogBoxParamA
0x4866e4 CallWindowProcW
0x4866e8 CallWindowProcA
0x4866ec DefWindowProcA
0x4866f0 IsWindowUnicode
0x4866f4 GetSystemMenu
0x4866f8 RedrawWindow
0x4866fc InvalidateRect
0x486700 ScreenToClient
0x486704 DrawStateA
0x486708 DrawEdge
0x48670c GetClientRect
0x486710 CreateWindowExA
0x486714 IsWindow
0x486718 GetParent
0x48671c GetWindowLongA
0x486720 GetForegroundWindow
0x486724 GetWindowThreadProcessId
0x486728 AttachThreadInput
0x48672c SetActiveWindow
0x486730 SetCursor
0x486734 SetTimer
0x486738 PostThreadMessageA
0x48673c MoveWindow
0x486740 BeginPaint
0x486744 EndPaint
0x486748 GetDlgItemInt
0x48674c SendDlgItemMessageA
0x486750 MapDialogRect
0x486754 SetWindowLongA
0x486758 ClientToScreen
0x48675c LoadCursorA
0x486760 RegisterClassW
0x486764 CreateWindowExW
0x486768 SetWindowLongW
0x48676c UpdateWindow
0x486770 GetMessageA
0x486774 IsDialogMessageA
0x486778 TranslateMessage
0x48677c DispatchMessageA
0x486780 SetWindowTextW
0x486784 SetMenu
0x486788 LoadMenuA
0x48678c GetMenuItemInfoA
0x486790 SetMenuItemInfoA
0x486794 GetSubMenu
0x486798 SetMenuItemInfoW
0x48679c GetMenuItemID
0x4867a0 EnableMenuItem
0x4867a4 GetMenuItemCount
0x4867a8 CheckMenuItem
0x4867ac GetKeyState
0x4867b0 SetForegroundWindow
0x4867b4 SetFocus
0x4867b8 GetFocus
0x4867bc PostQuitMessage
0x4867c0 DefWindowProcW
0x4867c4 CreatePopupMenu
0x4867c8 GetCursorPos
0x4867cc TrackPopupMenu
0x4867d0 GetSysColor
0x4867d4 GetSystemMetrics
0x4867d8 GetMenuItemInfoW
0x4867dc DrawMenuBar
0x4867e0 AppendMenuA
0x4867e4 DestroyMenu
0x4867e8 GetDlgItem
0x4867ec MessageBoxW
0x4867f0 SendMessageW
0x4867f4 GetWindowRect
0x4867f8 SystemParametersInfoA
SHELL32.dll
0x486524 SHBrowseForFolderW
0x486528 ShellExecuteExW
0x48652c SHGetFileInfoW
0x486530 SHGetFolderPathA
0x486534 SHGetFolderPathW
0x486538 Shell_NotifyIconA
0x48653c ShellExecuteA
0x486540 SHGetPathFromIDListW
0x486544 ShellExecuteW
0x486548 SHGetSpecialFolderPathW
0x48654c SHGetMalloc
MSVCRT.dll
0x48637c _strnicmp
0x486380 _strupr
0x486384 _strlwr
0x486388 _wcsicmp
0x48638c strcat
0x486390 _controlfp
0x486394 _iob
0x486398 __set_app_type
0x48639c __p__fmode
0x4863a0 __p__commode
0x4863a4 _adjust_fdiv
0x4863a8 __CxxFrameHandler
0x4863ac strlen
0x4863b0 isspace
0x4863b4 memchr
0x4863b8 _errno
0x4863bc strtol
0x4863c0 isdigit
0x4863c4 strstr
0x4863c8 memcpy
0x4863cc ??2@YAPAXI@Z
0x4863d0 _purecall
0x4863d4 free
0x4863d8 memset
0x4863dc malloc
0x4863e0 sprintf
0x4863e4 printf
0x4863e8 fwrite
0x4863ec srand
0x4863f0 time
0x4863f4 _CxxThrowException
0x4863f8 rand
0x4863fc atol
0x486400 _stricmp
0x486404 isprint
0x486408 tolower
0x48640c strncpy
0x486410 wcslen
0x486414 atoi
0x486418 abs
0x48641c wcscpy
0x486420 strcmp
0x486424 strcpy
0x486428 memcmp
0x48642c iswspace
0x486430 wcsncmp
0x486434 _wtoi
0x486438 _ultow
0x48643c wcschr
0x486440 strchr
0x486444 swprintf
0x486448 _ftol
0x48644c _stat
0x486450 strtoul
0x486454 calloc
0x486458 _rotl
0x48645c _rotr
0x486460 fopen
0x486464 fread
0x486468 fclose
0x48646c fseek
0x486470 ftell
0x486474 fflush
0x486478 wcsncpy
0x48647c wcsrchr
0x486480 vsprintf
0x486484 vswprintf
0x486488 memmove
0x48648c strrchr
0x486490 strncmp
0x486494 mbstowcs
0x486498 wcscmp
0x48649c wcsstr
0x4864a0 iswdigit
0x4864a4 _beginthreadex
0x4864a8 _endthreadex
0x4864ac atof
0x4864b0 _i64tow
0x4864b4 wcscat
0x4864b8 realloc
0x4864bc exit
0x4864c0 fprintf
0x4864c4 sscanf
0x4864c8 getenv
0x4864cc floor
0x4864d0 fputc
0x4864d4 _CIpow
0x4864d8 _CIacos
0x4864dc ??1type_info@@UAE@XZ
0x4864e0 __dllonexit
0x4864e4 _onexit
0x4864e8 _except_handler3
0x4864ec ?terminate@@YAXXZ
0x4864f0 _exit
0x4864f4 _XcptFilter
0x4864f8 _acmdln
0x4864fc __getmainargs
0x486500 _initterm
0x486504 __setusermatherr
Secur32.dll
0x48655c FreeContextBuffer
0x486560 QuerySecurityPackageInfoA
0x486564 FreeCredentialsHandle
0x486568 InitializeSecurityContextA
0x48656c CompleteAuthToken
0x486570 AcquireCredentialsHandleA
SETUPAPI.dll
0x48650c SetupDiGetDeviceRegistryPropertyA
0x486510 SetupDiDestroyDeviceInfoList
0x486514 SetupDiGetClassDevsA
0x486518 SetupDiClassGuidsFromNameA
0x48651c SetupDiEnumDeviceInfo
iphlpapi.dll
0x4868ac GetAdaptersInfo
ADVAPI32.dll
0x486000 ConvertSidToStringSidA
0x486004 GetTokenInformation
0x486008 OpenProcessToken
0x48600c RegCloseKey
0x486010 RegQueryValueExA
0x486014 RegOpenKeyExA
0x486018 FreeSid
0x48601c SetFileSecurityW
0x486020 SetSecurityDescriptorDacl
0x486024 InitializeSecurityDescriptor
0x486028 AllocateAndInitializeSid
0x48602c ImpersonateLoggedOnUser
0x486030 RevertToSelf
0x486034 GetUserNameA
0x486038 StartServiceCtrlDispatcherW
0x48603c RegisterServiceCtrlHandlerExA
0x486040 SetServiceStatus
0x486044 SetTokenInformation
0x486048 DuplicateTokenEx
0x48604c CreateProcessAsUserW
0x486050 QueryServiceStatus
0x486054 CloseServiceHandle
0x486058 OpenServiceA
0x48605c OpenSCManagerA
0x486060 CreateServiceW
0x486064 DeleteService
0x486068 ControlService
0x48606c StartServiceA
0x486070 StartServiceW
0x486074 RegCreateKeyExA
0x486078 RegQueryValueExW
0x48607c RegSetValueExW
0x486080 RegSetValueExA
0x486084 RegDeleteKeyA
0x486088 RegDeleteValueW
0x48608c RegCreateKeyExW
0x486090 RegEnumKeyExW
0x486094 RegOpenKeyExW
0x486098 SetEntriesInAclA
SHLWAPI.dll
0x486554 PathGetDriveNumberA
comdlg32.dll
0x4868a0 GetOpenFileNameW
0x4868a4 GetSaveFileNameW
USERENV.dll
0x486800 LoadUserProfileA
0x486804 UnloadUserProfile
COMCTL32.dll
0x4860a0 CreateToolbarEx
0x4860a4 ImageList_Create
0x4860a8 ImageList_Draw
0x4860ac ImageList_Destroy
0x4860b0 None
0x4860b4 ImageList_GetIconSize
0x4860b8 ImageList_ReplaceIcon
0x4860bc ImageList_Add
0x4860c0 ImageList_Duplicate
0x4860c4 _TrackMouseEvent
0x4860c8 CreatePropertySheetPageW
0x4860cc PropertySheetW
WININET.dll
0x48680c HttpSendRequestA
0x486810 HttpQueryInfoA
0x486814 InternetConnectA
0x486818 InternetSetOptionA
0x48681c InternetCloseHandle
0x486820 InternetReadFile
0x486824 InternetOpenA
0x486828 HttpOpenRequestA
DSOUND.dll
0x4860d4 None
0x4860d8 None
0x4860dc None
0x4860e0 None
KERNEL32.dll
0x48618c SizeofResource
0x486190 LoadResource
0x486194 LockResource
0x486198 GetLocalTime
0x48619c TryEnterCriticalSection
0x4861a0 LeaveCriticalSection
0x4861a4 EnterCriticalSection
0x4861a8 DeleteCriticalSection
0x4861ac InitializeCriticalSection
0x4861b0 SetFileTime
0x4861b4 GetFileTime
0x4861b8 OpenMutexA
0x4861bc CreateMutexA
0x4861c0 ResetEvent
0x4861c4 SetEvent
0x4861c8 FindResourceExA
0x4861cc CreateEventA
0x4861d0 ExitProcess
0x4861d4 SetUnhandledExceptionFilter
0x4861d8 GetSystemDirectoryA
0x4861dc CompareFileTime
0x4861e0 GetSystemTimeAsFileTime
0x4861e4 GetSystemDirectoryW
0x4861e8 lstrcatW
0x4861ec LoadLibraryW
0x4861f0 WaitNamedPipeW
0x4861f4 FileTimeToSystemTime
0x4861f8 SetLastError
0x4861fc GetExitCodeProcess
0x486200 WaitForSingleObject
0x486204 BeginUpdateResourceW
0x486208 EndUpdateResourceW
0x48620c UpdateResourceA
0x486210 CreateThread
0x486214 OpenProcess
0x486218 CreateToolhelp32Snapshot
0x48621c Process32First
0x486220 Process32Next
0x486224 LoadLibraryA
0x486228 FreeLibrary
0x48622c GetFileSize
0x486230 SetFilePointer
0x486234 WriteFile
0x486238 GetFileAttributesW
0x48623c lstrcmpiW
0x486240 lstrcmpW
0x486244 MulDiv
0x486248 FormatMessageW
0x48624c MultiByteToWideChar
0x486250 WideCharToMultiByte
0x486254 GetModuleFileNameW
0x486258 GetComputerNameA
0x48625c LocalAlloc
0x486260 GetExitCodeThread
0x486264 SystemTimeToFileTime
0x486268 MoveFileW
0x48626c DeleteFileW
0x486270 GetTempPathW
0x486274 CreateFileW
0x486278 FindFirstFileW
0x48627c FindClose
0x486280 CreateFileA
0x486284 DeviceIoControl
0x486288 GetUserDefaultUILanguage
0x48628c GetLocaleInfoA
0x486290 CreateDirectoryW
0x486294 SetCurrentDirectoryW
0x486298 GetStartupInfoW
0x48629c CreateProcessW
0x4862a0 GetModuleHandleA
0x4862a4 GetProcAddress
0x4862a8 SetProcessShutdownParameters
0x4862ac GetVersionExA
0x4862b0 GetCurrentProcess
0x4862b4 GetLastError
0x4862b8 CloseHandle
0x4862bc LocalFree
0x4862c0 GetCurrentThreadId
0x4862c4 GetCurrentProcessId
0x4862c8 Sleep
0x4862cc GetTickCount
0x4862d0 QueryPerformanceFrequency
0x4862d4 QueryPerformanceCounter
0x4862d8 InterlockedIncrement
0x4862dc InterlockedDecrement
0x4862e0 lstrlenA
0x4862e4 lstrlenW
0x4862e8 TerminateProcess
0x4862ec GlobalUnlock
0x4862f0 GlobalLock
0x4862f4 SystemTimeToTzSpecificLocalTime
0x4862f8 GetFileSizeEx
0x4862fc SetEndOfFile
0x486300 SetFilePointerEx
0x486304 GlobalAlloc
0x486308 GetDriveTypeW
0x48630c RemoveDirectoryW
0x486310 FindNextFileW
0x486314 SetFileAttributesW
0x486318 GetLogicalDrives
0x48631c ProcessIdToSessionId
0x486320 SleepEx
0x486324 CreateDirectoryA
0x486328 DeleteFileA
0x48632c GlobalFree
0x486330 IsBadReadPtr
0x486334 lstrcmpA
0x486338 LocalFileTimeToFileTime
0x48633c ReadFile
0x486340 lstrcpyA
0x486344 GetCurrentDirectoryA
0x486348 FindResourceA
0x48634c DuplicateHandle
0x486350 CreateSemaphoreA
0x486354 SetThreadPriority
0x486358 TlsSetValue
0x48635c GetCurrentThread
0x486360 TlsAlloc
0x486364 ResumeThread
0x486368 TlsGetValue
0x48636c InterlockedExchange
0x486370 GetStartupInfoA
0x486374 OpenEventA
EAT(Export Address Table) is none
WS2_32.dll
0x486830 WSAGetLastError
0x486834 send
0x486838 recv
0x48683c select
0x486840 WSAStartup
0x486844 getpeername
0x486848 getservbyport
0x48684c ntohs
0x486850 gethostbyaddr
0x486854 gethostbyname
0x486858 inet_addr
0x48685c getservbyname
0x486860 htonl
0x486864 inet_ntoa
0x486868 WSAIoctl
0x48686c connect
0x486870 accept
0x486874 htons
0x486878 ind
0x48687c listen
0x486880 socket
0x486884 __WSAFDIsSet
0x486888 shutdown
0x48688c setsockopt
0x486890 ioctlsocket
0x486894 WSACleanup
0x486898 closesocket
GDI32.dll
0x4860e8 GetDIBits
0x4860ec CreateCompatibleBitmap
0x4860f0 RealizePalette
0x4860f4 SelectPalette
0x4860f8 CreatePalette
0x4860fc GetSystemPaletteEntries
0x486100 GdiFlush
0x486104 CombineRgn
0x486108 GetRegionData
0x48610c SetStretchBltMode
0x486110 DeleteDC
0x486114 SelectObject
0x486118 CreateCompatibleDC
0x48611c BitBlt
0x486120 SetBkMode
0x486124 CreateFontIndirectA
0x486128 DPtoLP
0x48612c GetDeviceCaps
0x486130 CreateFontA
0x486134 CreateSolidBrush
0x486138 StretchBlt
0x48613c CreateRectRgn
0x486140 ExtTextOutA
0x486144 GetBitmapBits
0x486148 GetObjectA
0x48614c CreateDIBSection
0x486150 SetBitmapBits
0x486154 CreateRectRgnIndirect
0x486158 SelectClipRgn
0x48615c TextOutW
0x486160 CreatePatternBrush
0x486164 SetTextAlign
0x486168 SetBrushOrgEx
0x48616c ExtTextOutW
0x486170 SetTextColor
0x486174 SetBkColor
0x486178 CreateDIBitmap
0x48617c GetTextExtentPoint32W
0x486180 DeleteObject
0x486184 GetStockObject
USER32.dll
0x486578 FindWindowA
0x48657c OpenDesktopA
0x486580 LoadIconA
0x486584 SystemParametersInfoW
0x486588 IntersectRect
0x48658c IsWindowVisible
0x486590 GetIconInfo
0x486594 GetCursorInfo
0x486598 EqualRect
0x48659c OpenInputDesktop
0x4865a0 CloseDesktop
0x4865a4 GetUserObjectInformationA
0x4865a8 GetThreadDesktop
0x4865ac EmptyClipboard
0x4865b0 SetClipboardData
0x4865b4 RegisterClassExA
0x4865b8 GetDesktopWindow
0x4865bc PeekMessageA
0x4865c0 MsgWaitForMultipleObjects
0x4865c4 mouse_event
0x4865c8 SendInput
0x4865cc LockWorkStation
0x4865d0 SetThreadDesktop
0x4865d4 SetDlgItemTextA
0x4865d8 SetDlgItemInt
0x4865dc CallNextHookEx
0x4865e0 SetWindowsHookExA
0x4865e4 UnhookWindowsHookEx
0x4865e8 DestroyAcceleratorTable
0x4865ec TranslateAcceleratorA
0x4865f0 CreateAcceleratorTableA
0x4865f4 SetWindowTextA
0x4865f8 ReleaseCapture
0x4865fc SendMessageTimeoutA
0x486600 SwitchToThisWindow
0x486604 SendMessageA
0x486608 FindWindowW
0x48660c MessageBoxA
0x486610 ShowWindow
0x486614 wsprintfA
0x486618 SetCapture
0x48661c GetAsyncKeyState
0x486620 RegisterClassExW
0x486624 DestroyCursor
0x486628 MessageBeep
0x48662c wsprintfW
0x486630 SetCursorPos
0x486634 GetClipboardOwner
0x486638 OpenClipboard
0x48663c GetClipboardData
0x486640 CloseClipboard
0x486644 ShowWindowAsync
0x486648 SetScrollInfo
0x48664c ReleaseDC
0x486650 GetDC
0x486654 DestroyIcon
0x486658 DrawIconEx
0x48665c LoadImageA
0x486660 EnableWindow
0x486664 SetDlgItemTextW
0x486668 DestroyWindow
0x48666c SetWindowPos
0x486670 GetWindow
0x486674 WindowFromPoint
0x486678 SetClassLongW
0x48667c InsertMenuItemW
0x486680 ChangeClipboardChain
0x486684 MapWindowPoints
0x486688 InsertMenuItemA
0x48668c EnumWindows
0x486690 GetClassNameA
0x486694 GetWindowTextA
0x486698 KillTimer
0x48669c GetWindowLongW
0x4866a0 PostMessageA
0x4866a4 DrawTextW
0x4866a8 SetRect
0x4866ac ShowScrollBar
0x4866b0 IsIconic
0x4866b4 ScrollWindowEx
0x4866b8 AdjustWindowRectEx
0x4866bc GetMenuState
0x4866c0 GetWindowPlacement
0x4866c4 SetWindowPlacement
0x4866c8 GetSysColorBrush
0x4866cc AppendMenuW
0x4866d0 SetClipboardViewer
0x4866d4 DrawTextA
0x4866d8 EndDialog
0x4866dc CreateDialogParamW
0x4866e0 DialogBoxParamA
0x4866e4 CallWindowProcW
0x4866e8 CallWindowProcA
0x4866ec DefWindowProcA
0x4866f0 IsWindowUnicode
0x4866f4 GetSystemMenu
0x4866f8 RedrawWindow
0x4866fc InvalidateRect
0x486700 ScreenToClient
0x486704 DrawStateA
0x486708 DrawEdge
0x48670c GetClientRect
0x486710 CreateWindowExA
0x486714 IsWindow
0x486718 GetParent
0x48671c GetWindowLongA
0x486720 GetForegroundWindow
0x486724 GetWindowThreadProcessId
0x486728 AttachThreadInput
0x48672c SetActiveWindow
0x486730 SetCursor
0x486734 SetTimer
0x486738 PostThreadMessageA
0x48673c MoveWindow
0x486740 BeginPaint
0x486744 EndPaint
0x486748 GetDlgItemInt
0x48674c SendDlgItemMessageA
0x486750 MapDialogRect
0x486754 SetWindowLongA
0x486758 ClientToScreen
0x48675c LoadCursorA
0x486760 RegisterClassW
0x486764 CreateWindowExW
0x486768 SetWindowLongW
0x48676c UpdateWindow
0x486770 GetMessageA
0x486774 IsDialogMessageA
0x486778 TranslateMessage
0x48677c DispatchMessageA
0x486780 SetWindowTextW
0x486784 SetMenu
0x486788 LoadMenuA
0x48678c GetMenuItemInfoA
0x486790 SetMenuItemInfoA
0x486794 GetSubMenu
0x486798 SetMenuItemInfoW
0x48679c GetMenuItemID
0x4867a0 EnableMenuItem
0x4867a4 GetMenuItemCount
0x4867a8 CheckMenuItem
0x4867ac GetKeyState
0x4867b0 SetForegroundWindow
0x4867b4 SetFocus
0x4867b8 GetFocus
0x4867bc PostQuitMessage
0x4867c0 DefWindowProcW
0x4867c4 CreatePopupMenu
0x4867c8 GetCursorPos
0x4867cc TrackPopupMenu
0x4867d0 GetSysColor
0x4867d4 GetSystemMetrics
0x4867d8 GetMenuItemInfoW
0x4867dc DrawMenuBar
0x4867e0 AppendMenuA
0x4867e4 DestroyMenu
0x4867e8 GetDlgItem
0x4867ec MessageBoxW
0x4867f0 SendMessageW
0x4867f4 GetWindowRect
0x4867f8 SystemParametersInfoA
SHELL32.dll
0x486524 SHBrowseForFolderW
0x486528 ShellExecuteExW
0x48652c SHGetFileInfoW
0x486530 SHGetFolderPathA
0x486534 SHGetFolderPathW
0x486538 Shell_NotifyIconA
0x48653c ShellExecuteA
0x486540 SHGetPathFromIDListW
0x486544 ShellExecuteW
0x486548 SHGetSpecialFolderPathW
0x48654c SHGetMalloc
MSVCRT.dll
0x48637c _strnicmp
0x486380 _strupr
0x486384 _strlwr
0x486388 _wcsicmp
0x48638c strcat
0x486390 _controlfp
0x486394 _iob
0x486398 __set_app_type
0x48639c __p__fmode
0x4863a0 __p__commode
0x4863a4 _adjust_fdiv
0x4863a8 __CxxFrameHandler
0x4863ac strlen
0x4863b0 isspace
0x4863b4 memchr
0x4863b8 _errno
0x4863bc strtol
0x4863c0 isdigit
0x4863c4 strstr
0x4863c8 memcpy
0x4863cc ??2@YAPAXI@Z
0x4863d0 _purecall
0x4863d4 free
0x4863d8 memset
0x4863dc malloc
0x4863e0 sprintf
0x4863e4 printf
0x4863e8 fwrite
0x4863ec srand
0x4863f0 time
0x4863f4 _CxxThrowException
0x4863f8 rand
0x4863fc atol
0x486400 _stricmp
0x486404 isprint
0x486408 tolower
0x48640c strncpy
0x486410 wcslen
0x486414 atoi
0x486418 abs
0x48641c wcscpy
0x486420 strcmp
0x486424 strcpy
0x486428 memcmp
0x48642c iswspace
0x486430 wcsncmp
0x486434 _wtoi
0x486438 _ultow
0x48643c wcschr
0x486440 strchr
0x486444 swprintf
0x486448 _ftol
0x48644c _stat
0x486450 strtoul
0x486454 calloc
0x486458 _rotl
0x48645c _rotr
0x486460 fopen
0x486464 fread
0x486468 fclose
0x48646c fseek
0x486470 ftell
0x486474 fflush
0x486478 wcsncpy
0x48647c wcsrchr
0x486480 vsprintf
0x486484 vswprintf
0x486488 memmove
0x48648c strrchr
0x486490 strncmp
0x486494 mbstowcs
0x486498 wcscmp
0x48649c wcsstr
0x4864a0 iswdigit
0x4864a4 _beginthreadex
0x4864a8 _endthreadex
0x4864ac atof
0x4864b0 _i64tow
0x4864b4 wcscat
0x4864b8 realloc
0x4864bc exit
0x4864c0 fprintf
0x4864c4 sscanf
0x4864c8 getenv
0x4864cc floor
0x4864d0 fputc
0x4864d4 _CIpow
0x4864d8 _CIacos
0x4864dc ??1type_info@@UAE@XZ
0x4864e0 __dllonexit
0x4864e4 _onexit
0x4864e8 _except_handler3
0x4864ec ?terminate@@YAXXZ
0x4864f0 _exit
0x4864f4 _XcptFilter
0x4864f8 _acmdln
0x4864fc __getmainargs
0x486500 _initterm
0x486504 __setusermatherr
Secur32.dll
0x48655c FreeContextBuffer
0x486560 QuerySecurityPackageInfoA
0x486564 FreeCredentialsHandle
0x486568 InitializeSecurityContextA
0x48656c CompleteAuthToken
0x486570 AcquireCredentialsHandleA
SETUPAPI.dll
0x48650c SetupDiGetDeviceRegistryPropertyA
0x486510 SetupDiDestroyDeviceInfoList
0x486514 SetupDiGetClassDevsA
0x486518 SetupDiClassGuidsFromNameA
0x48651c SetupDiEnumDeviceInfo
iphlpapi.dll
0x4868ac GetAdaptersInfo
ADVAPI32.dll
0x486000 ConvertSidToStringSidA
0x486004 GetTokenInformation
0x486008 OpenProcessToken
0x48600c RegCloseKey
0x486010 RegQueryValueExA
0x486014 RegOpenKeyExA
0x486018 FreeSid
0x48601c SetFileSecurityW
0x486020 SetSecurityDescriptorDacl
0x486024 InitializeSecurityDescriptor
0x486028 AllocateAndInitializeSid
0x48602c ImpersonateLoggedOnUser
0x486030 RevertToSelf
0x486034 GetUserNameA
0x486038 StartServiceCtrlDispatcherW
0x48603c RegisterServiceCtrlHandlerExA
0x486040 SetServiceStatus
0x486044 SetTokenInformation
0x486048 DuplicateTokenEx
0x48604c CreateProcessAsUserW
0x486050 QueryServiceStatus
0x486054 CloseServiceHandle
0x486058 OpenServiceA
0x48605c OpenSCManagerA
0x486060 CreateServiceW
0x486064 DeleteService
0x486068 ControlService
0x48606c StartServiceA
0x486070 StartServiceW
0x486074 RegCreateKeyExA
0x486078 RegQueryValueExW
0x48607c RegSetValueExW
0x486080 RegSetValueExA
0x486084 RegDeleteKeyA
0x486088 RegDeleteValueW
0x48608c RegCreateKeyExW
0x486090 RegEnumKeyExW
0x486094 RegOpenKeyExW
0x486098 SetEntriesInAclA
SHLWAPI.dll
0x486554 PathGetDriveNumberA
comdlg32.dll
0x4868a0 GetOpenFileNameW
0x4868a4 GetSaveFileNameW
USERENV.dll
0x486800 LoadUserProfileA
0x486804 UnloadUserProfile
COMCTL32.dll
0x4860a0 CreateToolbarEx
0x4860a4 ImageList_Create
0x4860a8 ImageList_Draw
0x4860ac ImageList_Destroy
0x4860b0 None
0x4860b4 ImageList_GetIconSize
0x4860b8 ImageList_ReplaceIcon
0x4860bc ImageList_Add
0x4860c0 ImageList_Duplicate
0x4860c4 _TrackMouseEvent
0x4860c8 CreatePropertySheetPageW
0x4860cc PropertySheetW
WININET.dll
0x48680c HttpSendRequestA
0x486810 HttpQueryInfoA
0x486814 InternetConnectA
0x486818 InternetSetOptionA
0x48681c InternetCloseHandle
0x486820 InternetReadFile
0x486824 InternetOpenA
0x486828 HttpOpenRequestA
DSOUND.dll
0x4860d4 None
0x4860d8 None
0x4860dc None
0x4860e0 None
KERNEL32.dll
0x48618c SizeofResource
0x486190 LoadResource
0x486194 LockResource
0x486198 GetLocalTime
0x48619c TryEnterCriticalSection
0x4861a0 LeaveCriticalSection
0x4861a4 EnterCriticalSection
0x4861a8 DeleteCriticalSection
0x4861ac InitializeCriticalSection
0x4861b0 SetFileTime
0x4861b4 GetFileTime
0x4861b8 OpenMutexA
0x4861bc CreateMutexA
0x4861c0 ResetEvent
0x4861c4 SetEvent
0x4861c8 FindResourceExA
0x4861cc CreateEventA
0x4861d0 ExitProcess
0x4861d4 SetUnhandledExceptionFilter
0x4861d8 GetSystemDirectoryA
0x4861dc CompareFileTime
0x4861e0 GetSystemTimeAsFileTime
0x4861e4 GetSystemDirectoryW
0x4861e8 lstrcatW
0x4861ec LoadLibraryW
0x4861f0 WaitNamedPipeW
0x4861f4 FileTimeToSystemTime
0x4861f8 SetLastError
0x4861fc GetExitCodeProcess
0x486200 WaitForSingleObject
0x486204 BeginUpdateResourceW
0x486208 EndUpdateResourceW
0x48620c UpdateResourceA
0x486210 CreateThread
0x486214 OpenProcess
0x486218 CreateToolhelp32Snapshot
0x48621c Process32First
0x486220 Process32Next
0x486224 LoadLibraryA
0x486228 FreeLibrary
0x48622c GetFileSize
0x486230 SetFilePointer
0x486234 WriteFile
0x486238 GetFileAttributesW
0x48623c lstrcmpiW
0x486240 lstrcmpW
0x486244 MulDiv
0x486248 FormatMessageW
0x48624c MultiByteToWideChar
0x486250 WideCharToMultiByte
0x486254 GetModuleFileNameW
0x486258 GetComputerNameA
0x48625c LocalAlloc
0x486260 GetExitCodeThread
0x486264 SystemTimeToFileTime
0x486268 MoveFileW
0x48626c DeleteFileW
0x486270 GetTempPathW
0x486274 CreateFileW
0x486278 FindFirstFileW
0x48627c FindClose
0x486280 CreateFileA
0x486284 DeviceIoControl
0x486288 GetUserDefaultUILanguage
0x48628c GetLocaleInfoA
0x486290 CreateDirectoryW
0x486294 SetCurrentDirectoryW
0x486298 GetStartupInfoW
0x48629c CreateProcessW
0x4862a0 GetModuleHandleA
0x4862a4 GetProcAddress
0x4862a8 SetProcessShutdownParameters
0x4862ac GetVersionExA
0x4862b0 GetCurrentProcess
0x4862b4 GetLastError
0x4862b8 CloseHandle
0x4862bc LocalFree
0x4862c0 GetCurrentThreadId
0x4862c4 GetCurrentProcessId
0x4862c8 Sleep
0x4862cc GetTickCount
0x4862d0 QueryPerformanceFrequency
0x4862d4 QueryPerformanceCounter
0x4862d8 InterlockedIncrement
0x4862dc InterlockedDecrement
0x4862e0 lstrlenA
0x4862e4 lstrlenW
0x4862e8 TerminateProcess
0x4862ec GlobalUnlock
0x4862f0 GlobalLock
0x4862f4 SystemTimeToTzSpecificLocalTime
0x4862f8 GetFileSizeEx
0x4862fc SetEndOfFile
0x486300 SetFilePointerEx
0x486304 GlobalAlloc
0x486308 GetDriveTypeW
0x48630c RemoveDirectoryW
0x486310 FindNextFileW
0x486314 SetFileAttributesW
0x486318 GetLogicalDrives
0x48631c ProcessIdToSessionId
0x486320 SleepEx
0x486324 CreateDirectoryA
0x486328 DeleteFileA
0x48632c GlobalFree
0x486330 IsBadReadPtr
0x486334 lstrcmpA
0x486338 LocalFileTimeToFileTime
0x48633c ReadFile
0x486340 lstrcpyA
0x486344 GetCurrentDirectoryA
0x486348 FindResourceA
0x48634c DuplicateHandle
0x486350 CreateSemaphoreA
0x486354 SetThreadPriority
0x486358 TlsSetValue
0x48635c GetCurrentThread
0x486360 TlsAlloc
0x486364 ResumeThread
0x486368 TlsGetValue
0x48636c InterlockedExchange
0x486370 GetStartupInfoA
0x486374 OpenEventA
EAT(Export Address Table) is none