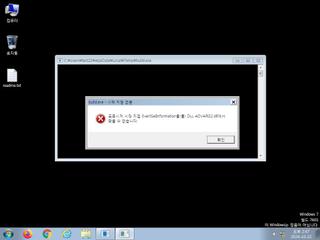
ScreenShot
| Created | 2024.10.22 14:51 | Machine | s1_win7_x6401 |
| Filename | build.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 32 detected (Malicious, score, Artemis, V28f, confidence, Giant, Mikey, Genus, Attribute, HighConfidence, cjis, LESS, bWQ1Ovfdsa3m25N+, naeal, Dapato, aekq, Wacatac, Outbreak, Chgt, Javascript, ciRt) | ||
| md5 | 0f0d9c2f1a7d16b87a8b6be05c9d12c3 | ||
| sha256 | 6bd8253c684ad2e56599f8898606a39240e3ebeab66ac35bf5e7f8191b8719b4 | ||
| ssdeep | 393216:qEr+7CAtJyEsYLrH95y/1uzVyQcNnxu+ds+o0ECKHOQKtuK+Vf6qrdWY6wdla9Fo:qdv86wQ0xYKV8HFrsPFlXHo | ||
| imphash | b1c5e35cfdb33b753d65d387789d99f4 | ||
| impfuzzy | 192:t++E2FX/rbcBT8Urfk/g4W5WQeSh+3QvaF7eo:t+c08EqTufh+3f7eo | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 32 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
Rules (9cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | ftp_command | ftp command | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|