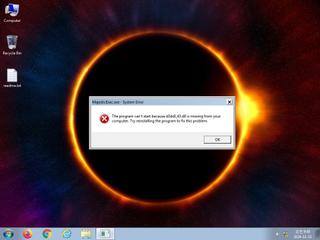
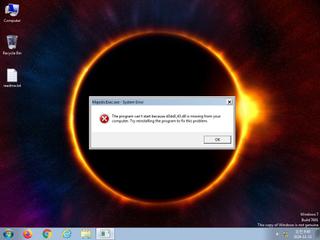
ScreenShot
| Created | 2024.11.11 09:52 | Machine | s1_win7_x6403 |
| Filename | MajesticExec.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | |||
| VT API (file) | 45 detected (AIDetectMalware, Donut, Marte, Unsafe, malicious, confidence, Attribute, HighConfidence, Windows, Donutloader, a variant of Generik, ELADIVY, Rozena, CLASSIC, Real Protect, Static AI, Suspicious PE, Detected, GrayWare, Wacapew, Casdet, ABTrojan, UNNO, Artemis, Chgt, R002H09K124, xSxloFwpPTo, susgen, PossibleThreat) | ||
| md5 | 1963ce8f3f680d344d195bc27449b9a7 | ||
| sha256 | 46d936bdc8ae3c40d119eec506b3a8aef4f6b97d10207fe4768692c3e887d082 | ||
| ssdeep | 196608:+0wy/5kJJl8s7n+Z+92NmbU5k+SKnt6wH32n2:1q1f7n+Z+DUK4zX22 | ||
| imphash | 8133a7fda15b324400e5417b3c03efd5 | ||
| impfuzzy | 12:ETAHqTkKjqRrcE2UIHxZOqMGJ2Q4W2TAah4ypB4PJuD1FF:yAhKORoJbfOqRJ5b44yPAJu5FF | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 45 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x1404c84f8 GetModuleHandleA
d3d9.dll
0x1404c8508 Direct3DCreate9
USER32.dll
0x1404c8518 GetClipboardData
GDI32.dll
0x1404c8528 GetDeviceCaps
ADVAPI32.dll
0x1404c8538 GetTokenInformation
ole32.dll
0x1404c8548 CoInitialize
WINHTTP.dll
0x1404c8558 WinHttpConnect
MSVCP140.dll
0x1404c8568 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
IMM32.dll
0x1404c8578 ImmReleaseContext
d3dx9_43.dll
0x1404c8588 D3DXCreateTextureFromFileInMemoryEx
ntdll.dll
0x1404c8598 RtlLookupFunctionEntry
VCRUNTIME140_1.dll
0x1404c85a8 __CxxFrameHandler4
VCRUNTIME140.dll
0x1404c85b8 memcmp
api-ms-win-crt-runtime-l1-1-0.dll
0x1404c85c8 _wassert
api-ms-win-crt-heap-l1-1-0.dll
0x1404c85d8 malloc
api-ms-win-crt-stdio-l1-1-0.dll
0x1404c85e8 __stdio_common_vsprintf_s
api-ms-win-crt-string-l1-1-0.dll
0x1404c85f8 strcmp
api-ms-win-crt-utility-l1-1-0.dll
0x1404c8608 qsort
api-ms-win-crt-multibyte-l1-1-0.dll
0x1404c8618 _mbsicmp
api-ms-win-crt-math-l1-1-0.dll
0x1404c8628 cosf
api-ms-win-crt-locale-l1-1-0.dll
0x1404c8638 _configthreadlocale
EAT(Export Address Table) is none
kernel32.dll
0x1404c84f8 GetModuleHandleA
d3d9.dll
0x1404c8508 Direct3DCreate9
USER32.dll
0x1404c8518 GetClipboardData
GDI32.dll
0x1404c8528 GetDeviceCaps
ADVAPI32.dll
0x1404c8538 GetTokenInformation
ole32.dll
0x1404c8548 CoInitialize
WINHTTP.dll
0x1404c8558 WinHttpConnect
MSVCP140.dll
0x1404c8568 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
IMM32.dll
0x1404c8578 ImmReleaseContext
d3dx9_43.dll
0x1404c8588 D3DXCreateTextureFromFileInMemoryEx
ntdll.dll
0x1404c8598 RtlLookupFunctionEntry
VCRUNTIME140_1.dll
0x1404c85a8 __CxxFrameHandler4
VCRUNTIME140.dll
0x1404c85b8 memcmp
api-ms-win-crt-runtime-l1-1-0.dll
0x1404c85c8 _wassert
api-ms-win-crt-heap-l1-1-0.dll
0x1404c85d8 malloc
api-ms-win-crt-stdio-l1-1-0.dll
0x1404c85e8 __stdio_common_vsprintf_s
api-ms-win-crt-string-l1-1-0.dll
0x1404c85f8 strcmp
api-ms-win-crt-utility-l1-1-0.dll
0x1404c8608 qsort
api-ms-win-crt-multibyte-l1-1-0.dll
0x1404c8618 _mbsicmp
api-ms-win-crt-math-l1-1-0.dll
0x1404c8628 cosf
api-ms-win-crt-locale-l1-1-0.dll
0x1404c8638 _configthreadlocale
EAT(Export Address Table) is none