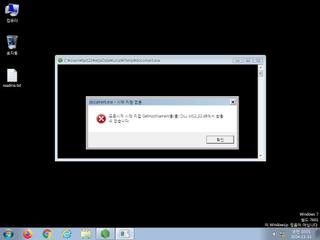
ScreenShot
| Created | 2024.11.11 10:07 | Machine | s1_win7_x6401 |
| Filename | document.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | |||
| VT API (file) | 39 detected (GenericKDQ, Malicious, score, Artemis, GenericQ, Attribute, HighConfidence, Doenerium, TrojanPSW, CLOUD, vcuqn, Detected, Malware@#39n7fdjwfpwz3, Leonem, ABTrojan, QECD, Hydra, Cryxos, Chgt, Gencirc, susgen) | ||
| md5 | a92c1499dbcfff3bc5b57853f6219eec | ||
| sha256 | b4c84c53e83488f95024a23205daaf21fcfb7b311f752f6497fbd8c6655611e2 | ||
| ssdeep | 393216:RQgHDlanaGBXvDKtz+bhPWES4tiNQPNrIKc4gaPbUAgrO4mg396l+ZArYsFRlrN2:R3on1HvSzxAMN3FZArYs+PvAX7OZ0i | ||
| imphash | f0486e7e054aa57188c99b0f71783b75 | ||
| impfuzzy | 192:U34BX/rbwL7T8gck/gKehFpi/k3CW5WlbF7V:U3Og8glOFpinu4x7V | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 39 AntiVirus engines on VirusTotal as malicious |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|