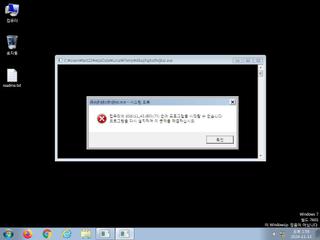
ScreenShot
| Created | 2024.11.13 14:13 | Machine | s1_win7_x6401 |
| Filename | dkasjhajksdhdjkas.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 46 detected (AIDetectMalware, GameHack, Malicious, score, Lazy, Unsafe, confidence, Attribute, HighConfidence, high confidence, FileRepMalware, Misc, HackTool, SSHNpY3d4AU, AGEN, Static AI, Malicious PE, Detected, Sabsik, Wacatac, Eldorado, R674221, Artemis, Chgt, Gencirc, Hl6ZuIWXMG0, susgen, GenKryptik, GHEK) | ||
| md5 | 09e252478ab23c7c677a2765234335bd | ||
| sha256 | abc35b74a68a91f2a6640467e6eedcac02f7ffb02bac14b196deda5cb63070b6 | ||
| ssdeep | 98304:miV01Ssm1ttYbODo4CyZwg562/K5a6e6c8hDkDe9ncT40Dfv:miiyZYkoryEJg6cXs0Dfv | ||
| imphash | e99d73805a6ee3c07dc37bfd5cd694cd | ||
| impfuzzy | 192:T+raWKkTQTxvFRloOXOoXYaeUpDB+hdyOM1H:iaVrdgoTp9sIOMF | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 46 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | ftp_command | ftp command | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
d3dx11_43.dll
0x14012ae88 D3DX11CreateShaderResourceViewFromMemory
d3d11.dll
0x14012ae78 D3D11CreateDeviceAndSwapChain
D3DCOMPILER_43.dll
0x14012a170 D3DCompile
KERNEL32.dll
0x14012a1a8 ReadFile
0x14012a1b0 PeekNamedPipe
0x14012a1b8 WaitForMultipleObjects
0x14012a1c0 GetFileSizeEx
0x14012a1c8 CreateFileMappingA
0x14012a1d0 GetEnvironmentVariableA
0x14012a1d8 WaitForSingleObjectEx
0x14012a1e0 MoveFileExA
0x14012a1e8 GetTickCount
0x14012a1f0 CreateFileMappingW
0x14012a1f8 MapViewOfFile
0x14012a200 UnmapViewOfFile
0x14012a208 GetModuleFileNameA
0x14012a210 GetModuleHandleW
0x14012a218 QueryFullProcessImageNameW
0x14012a220 QueryPerformanceCounter
0x14012a228 FreeLibrary
0x14012a230 VerSetConditionMask
0x14012a238 VerifyVersionInfoA
0x14012a240 DeleteCriticalSection
0x14012a248 OutputDebugStringW
0x14012a250 ReleaseSRWLockExclusive
0x14012a258 AcquireSRWLockExclusive
0x14012a260 WakeAllConditionVariable
0x14012a268 SleepConditionVariableSRW
0x14012a270 RtlCaptureContext
0x14012a278 RtlLookupFunctionEntry
0x14012a280 RtlVirtualUnwind
0x14012a288 UnhandledExceptionFilter
0x14012a290 SetUnhandledExceptionFilter
0x14012a298 IsProcessorFeaturePresent
0x14012a2a0 GetCurrentProcessId
0x14012a2a8 GetCurrentThreadId
0x14012a2b0 GetSystemTimeAsFileTime
0x14012a2b8 InitializeSListHead
0x14012a2c0 GetProcAddress
0x14012a2c8 QueryPerformanceFrequency
0x14012a2d0 LoadLibraryA
0x14012a2d8 GetModuleHandleA
0x14012a2e0 GlobalUnlock
0x14012a2e8 GlobalLock
0x14012a2f0 GlobalFree
0x14012a2f8 GlobalAlloc
0x14012a300 GetFileAttributesW
0x14012a308 lstrcmpiW
0x14012a310 GetConsoleWindow
0x14012a318 WideCharToMultiByte
0x14012a320 CreateThread
0x14012a328 CloseHandle
0x14012a330 Process32FirstW
0x14012a338 CreateFileA
0x14012a340 Process32NextW
0x14012a348 GetLastError
0x14012a350 Sleep
0x14012a358 GetSystemDirectoryA
0x14012a360 SleepEx
0x14012a368 LeaveCriticalSection
0x14012a370 CreateFileW
0x14012a378 HeapDestroy
0x14012a380 HeapAlloc
0x14012a388 HeapReAlloc
0x14012a390 GetFileType
0x14012a398 HeapFree
0x14012a3a0 HeapSize
0x14012a3a8 GetProcessHeap
0x14012a3b0 GetCurrentProcess
0x14012a3b8 MultiByteToWideChar
0x14012a3c0 CreateToolhelp32Snapshot
0x14012a3c8 SetConsoleWindowInfo
0x14012a3d0 TerminateProcess
0x14012a3d8 DeviceIoControl
0x14012a3e0 GetStdHandle
0x14012a3e8 SetConsoleScreenBufferSize
0x14012a3f0 SetConsoleTitleA
0x14012a3f8 SetConsoleTextAttribute
0x14012a400 InitializeCriticalSectionEx
0x14012a408 IsDebuggerPresent
0x14012a410 SetLastError
0x14012a418 FormatMessageA
0x14012a420 EnterCriticalSection
0x14012a428 LocalFree
0x14012a430 VirtualProtect
USER32.dll
0x14012a740 LoadCursorW
0x14012a748 ScreenToClient
0x14012a750 SetCursor
0x14012a758 SetCursorPos
0x14012a760 OpenClipboard
0x14012a768 CloseClipboard
0x14012a770 EmptyClipboard
0x14012a778 GetCursorPos
0x14012a780 UpdateWindow
0x14012a788 GetClipboardData
0x14012a790 SetClipboardData
0x14012a798 FindWindowA
0x14012a7a0 GetKeyState
0x14012a7a8 GetWindow
0x14012a7b0 MessageBoxA
0x14012a7b8 DestroyWindow
0x14012a7c0 SetWindowPos
0x14012a7c8 SetWindowLongPtrW
0x14012a7d0 GetSystemMetrics
0x14012a7d8 GetWindowLongPtrW
0x14012a7e0 ShowWindow
0x14012a7e8 GetAsyncKeyState
0x14012a7f0 DispatchMessageW
0x14012a7f8 ClientToScreen
0x14012a800 PeekMessageW
0x14012a808 GetForegroundWindow
0x14012a810 SetLayeredWindowAttributes
0x14012a818 TranslateMessage
0x14012a820 FindWindowW
0x14012a828 GetClientRect
ADVAPI32.dll
0x14012a000 StartServiceW
0x14012a008 ControlService
0x14012a010 DeleteService
0x14012a018 OpenSCManagerW
0x14012a020 CloseServiceHandle
0x14012a028 QueryServiceStatus
0x14012a030 CreateServiceW
0x14012a038 OpenProcessToken
0x14012a040 AddAccessAllowedAce
0x14012a048 GetLengthSid
0x14012a050 GetTokenInformation
0x14012a058 InitializeAcl
0x14012a060 IsValidSid
0x14012a068 SetSecurityInfo
0x14012a070 CopySid
0x14012a078 CryptEncrypt
0x14012a080 CryptImportKey
0x14012a088 CryptDestroyKey
0x14012a090 CryptDestroyHash
0x14012a098 CryptHashData
0x14012a0a0 CryptCreateHash
0x14012a0a8 CryptGenRandom
0x14012a0b0 CryptGetHashParam
0x14012a0b8 CryptReleaseContext
0x14012a0c0 CryptAcquireContextA
0x14012a0c8 ConvertSidToStringSidA
0x14012a0d0 OpenServiceW
SHELL32.dll
0x14012a730 ShellExecuteA
MSVCP140.dll
0x14012a440 ?uflow@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x14012a448 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x14012a450 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x14012a458 ?setbuf@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAPEAV12@PEAD_J@Z
0x14012a460 ?sync@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x14012a468 ?imbue@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAXAEBVlocale@2@@Z
0x14012a470 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a478 ??1?$basic_ostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a480 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAV01@AEAV01@@Z@Z
0x14012a488 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAVios_base@1@AEAV21@@Z@Z
0x14012a490 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@_N@Z
0x14012a498 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@H@Z
0x14012a4a0 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@M@Z
0x14012a4a8 ??1?$basic_istream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a4b0 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEA_N@Z
0x14012a4b8 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEAH@Z
0x14012a4c0 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEAM@Z
0x14012a4c8 ?getloc@ios_base@std@@QEBA?AVlocale@2@XZ
0x14012a4d0 ?_Getcat@?$ctype@D@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x14012a4d8 ??1?$codecvt@_WDU_Mbstatet@@@std@@MEAA@XZ
0x14012a4e0 ??0?$codecvt@_WDU_Mbstatet@@@std@@QEAA@_K@Z
0x14012a4e8 ?in@?$codecvt@_WDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEA_W3AEAPEA_W@Z
0x14012a4f0 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x14012a4f8 ?_Addfac@_Locimp@locale@std@@AEAAXPEAVfacet@23@_K@Z
0x14012a500 ?_Decref@facet@locale@std@@UEAAPEAV_Facet_base@3@XZ
0x14012a508 ?_Incref@facet@locale@std@@UEAAXXZ
0x14012a510 ??Bid@locale@std@@QEAA_KXZ
0x14012a518 ??0?$basic_iostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@@Z
0x14012a520 ??1?$basic_iostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a528 ?cout@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x14012a530 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x14012a538 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x14012a540 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x14012a548 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x14012a550 ?write@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@PEBD_J@Z
0x14012a558 ?put@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@D@Z
0x14012a560 ?widen@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADD@Z
0x14012a568 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x14012a570 ?sgetc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x14012a578 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x14012a580 ?snextc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x14012a588 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x14012a590 ?_Ipfx@?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA_N_N@Z
0x14012a598 _Mtx_unlock
0x14012a5a0 _Thrd_join
0x14012a5a8 _Xtime_get_ticks
0x14012a5b0 ?_Unlock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x14012a5b8 ?_Lock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x14012a5c0 ?sbumpc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x14012a5c8 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a5d0 ??4?$_Yarn@D@std@@QEAAAEAV01@PEBD@Z
0x14012a5d8 ??0?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x14012a5e0 ??0?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x14012a5e8 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x14012a5f0 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x14012a5f8 ?uncaught_exceptions@std@@YAHXZ
0x14012a600 ?_Throw_Cpp_error@std@@YAXH@Z
0x14012a608 ??0_Lockit@std@@QEAA@H@Z
0x14012a610 _Query_perf_counter
0x14012a618 _Thrd_id
0x14012a620 _Thrd_sleep
0x14012a628 _Cnd_do_broadcast_at_thread_exit
0x14012a630 _Mtx_init_in_situ
0x14012a638 _Mtx_lock
0x14012a640 _Mtx_destroy_in_situ
0x14012a648 ?id@?$codecvt@_WDU_Mbstatet@@@std@@2V0locale@2@A
0x14012a650 ?id@?$ctype@D@std@@2V0locale@2@A
0x14012a658 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x14012a660 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x14012a668 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x14012a670 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x14012a678 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x14012a680 ?setw@std@@YA?AU?$_Smanip@_J@1@_J@Z
0x14012a688 ?_Fiopen@std@@YAPEAU_iobuf@@PEBDHH@Z
0x14012a690 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x14012a698 ?cerr@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x14012a6a0 ?_Xout_of_range@std@@YAXPEBD@Z
0x14012a6a8 ?cin@std@@3V?$basic_istream@DU?$char_traits@D@std@@@1@A
0x14012a6b0 ?_Init@locale@std@@CAPEAV_Locimp@12@_N@Z
0x14012a6b8 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x14012a6c0 ?_Xbad_function_call@std@@YAXXZ
0x14012a6c8 ?_Xlength_error@std@@YAXPEBD@Z
0x14012a6d0 _Query_perf_frequency
0x14012a6d8 ??1_Lockit@std@@QEAA@XZ
0x14012a6e0 ?_New_Locimp@_Locimp@locale@std@@CAPEAV123@AEBV123@@Z
dwmapi.dll
0x14012ae98 DwmExtendFrameIntoClientArea
WINHTTP.dll
0x14012a8e8 WinHttpQueryOption
0x14012a8f0 WinHttpOpen
0x14012a8f8 WinHttpSendRequest
0x14012a900 WinHttpCloseHandle
0x14012a908 WinHttpOpenRequest
0x14012a910 WinHttpReceiveResponse
0x14012a918 WinHttpConnect
CRYPT32.dll
0x14012a0e0 CertFreeCertificateChainEngine
0x14012a0e8 CertCreateCertificateChainEngine
0x14012a0f0 CryptQueryObject
0x14012a0f8 CertGetNameStringA
0x14012a100 CertFindExtension
0x14012a108 CertAddCertificateContextToStore
0x14012a110 CryptDecodeObjectEx
0x14012a118 CertGetCertificateChain
0x14012a120 PFXImportCertStore
0x14012a128 CryptStringToBinaryA
0x14012a130 CertFindCertificateInStore
0x14012a138 CertEnumCertificatesInStore
0x14012a140 CertCloseStore
0x14012a148 CertGetCertificateContextProperty
0x14012a150 CertOpenStore
0x14012a158 CertFreeCertificateChain
0x14012a160 CertFreeCertificateContext
IMM32.dll
0x14012a180 ImmReleaseContext
0x14012a188 ImmSetCompositionWindow
0x14012a190 ImmGetContext
0x14012a198 ImmSetCandidateWindow
Normaliz.dll
0x14012a6f0 IdnToAscii
WLDAP32.dll
0x14012a928 None
0x14012a930 None
0x14012a938 None
0x14012a940 None
0x14012a948 None
0x14012a950 None
0x14012a958 None
0x14012a960 None
0x14012a968 None
0x14012a970 None
0x14012a978 None
0x14012a980 None
0x14012a988 None
0x14012a990 None
0x14012a998 None
0x14012a9a0 None
0x14012a9a8 None
0x14012a9b0 None
WS2_32.dll
0x14012a9c0 freeaddrinfo
0x14012a9c8 recvfrom
0x14012a9d0 __WSAFDIsSet
0x14012a9d8 ioctlsocket
0x14012a9e0 listen
0x14012a9e8 htonl
0x14012a9f0 sendto
0x14012a9f8 accept
0x14012aa00 WSACleanup
0x14012aa08 WSAStartup
0x14012aa10 WSAIoctl
0x14012aa18 gethostname
0x14012aa20 getaddrinfo
0x14012aa28 closesocket
0x14012aa30 WSASetLastError
0x14012aa38 socket
0x14012aa40 setsockopt
0x14012aa48 ntohs
0x14012aa50 htons
0x14012aa58 getsockopt
0x14012aa60 getsockname
0x14012aa68 getpeername
0x14012aa70 ntohl
0x14012aa78 ind
0x14012aa80 WSAGetLastError
0x14012aa88 select
0x14012aa90 send
0x14012aa98 recv
0x14012aaa0 connect
RPCRT4.dll
0x14012a710 UuidToStringA
0x14012a718 UuidCreate
0x14012a720 RpcStringFreeA
PSAPI.DLL
0x14012a700 GetModuleInformation
USERENV.dll
0x14012a838 UnloadUserProfile
VCRUNTIME140_1.dll
0x14012a8d8 __CxxFrameHandler4
VCRUNTIME140.dll
0x14012a848 __std_exception_copy
0x14012a850 memset
0x14012a858 strchr
0x14012a860 strrchr
0x14012a868 __std_exception_destroy
0x14012a870 longjmp
0x14012a878 __C_specific_handler
0x14012a880 __std_terminate
0x14012a888 __current_exception
0x14012a890 __current_exception_context
0x14012a898 memcpy
0x14012a8a0 strstr
0x14012a8a8 _CxxThrowException
0x14012a8b0 memchr
0x14012a8b8 memcmp
0x14012a8c0 __intrinsic_setjmp
0x14012a8c8 memmove
api-ms-win-crt-runtime-l1-1-0.dll
0x14012abf8 exit
0x14012ac00 _invalid_parameter_noinfo_noreturn
0x14012ac08 terminate
0x14012ac10 strerror
0x14012ac18 __sys_nerr
0x14012ac20 _invalid_parameter_noinfo
0x14012ac28 _resetstkoflw
0x14012ac30 system
0x14012ac38 _getpid
0x14012ac40 _beginthreadex
0x14012ac48 _register_thread_local_exe_atexit_callback
0x14012ac50 _c_exit
0x14012ac58 __p___argv
0x14012ac60 __p___argc
0x14012ac68 _exit
0x14012ac70 _initterm_e
0x14012ac78 _initterm
0x14012ac80 _get_initial_narrow_environment
0x14012ac88 _set_app_type
0x14012ac90 _seh_filter_exe
0x14012ac98 _cexit
0x14012aca0 _crt_atexit
0x14012aca8 _register_onexit_function
0x14012acb0 _initialize_onexit_table
0x14012acb8 _initialize_narrow_environment
0x14012acc0 _configure_narrow_argv
0x14012acc8 _errno
api-ms-win-crt-stdio-l1-1-0.dll
0x14012acd8 fclose
0x14012ace0 __p__commode
0x14012ace8 __acrt_iob_func
0x14012acf0 _lseeki64
0x14012acf8 __stdio_common_vsprintf_s
0x14012ad00 fgetc
0x14012ad08 fflush
0x14012ad10 _read
0x14012ad18 feof
0x14012ad20 fputs
0x14012ad28 fopen
0x14012ad30 _write
0x14012ad38 _close
0x14012ad40 _open
0x14012ad48 __stdio_common_vfprintf
0x14012ad50 fputc
0x14012ad58 _pclose
0x14012ad60 fgets
0x14012ad68 fwrite
0x14012ad70 _set_fmode
0x14012ad78 __stdio_common_vsscanf
0x14012ad80 _wfopen
0x14012ad88 __stdio_common_vsprintf
0x14012ad90 fseek
0x14012ad98 ftell
0x14012ada0 _get_stream_buffer_pointers
0x14012ada8 _fseeki64
0x14012adb0 fread
0x14012adb8 fsetpos
0x14012adc0 ungetc
0x14012adc8 fgetpos
0x14012add0 setvbuf
0x14012add8 _popen
api-ms-win-crt-heap-l1-1-0.dll
0x14012ab28 malloc
0x14012ab30 _set_new_mode
0x14012ab38 realloc
0x14012ab40 free
0x14012ab48 calloc
0x14012ab50 _callnewh
api-ms-win-crt-math-l1-1-0.dll
0x14012ab78 __setusermatherr
0x14012ab80 tanf
0x14012ab88 _dclass
0x14012ab90 fmodf
0x14012ab98 cosf
0x14012aba0 cos
0x14012aba8 ceilf
0x14012abb0 atanf
0x14012abb8 asinf
0x14012abc0 powf
0x14012abc8 roundf
0x14012abd0 sin
0x14012abd8 sinf
0x14012abe0 sqrtf
0x14012abe8 acosf
api-ms-win-crt-string-l1-1-0.dll
0x14012ade8 strncmp
0x14012adf0 strncpy
0x14012adf8 isupper
0x14012ae00 tolower
0x14012ae08 strpbrk
0x14012ae10 strcmp
0x14012ae18 _strdup
0x14012ae20 strspn
0x14012ae28 strcspn
api-ms-win-crt-time-l1-1-0.dll
0x14012ae38 _localtime64_s
0x14012ae40 _gmtime64
0x14012ae48 strftime
0x14012ae50 _time64
api-ms-win-crt-convert-l1-1-0.dll
0x14012aab0 strtoull
0x14012aab8 strtoul
0x14012aac0 strtod
0x14012aac8 atof
0x14012aad0 atoi
0x14012aad8 strtol
0x14012aae0 strtoll
api-ms-win-crt-utility-l1-1-0.dll
0x14012ae60 qsort
0x14012ae68 rand
api-ms-win-crt-filesystem-l1-1-0.dll
0x14012aaf0 _unlock_file
0x14012aaf8 _lock_file
0x14012ab00 _unlink
0x14012ab08 _stat64
0x14012ab10 _fstat64
0x14012ab18 _access
api-ms-win-crt-locale-l1-1-0.dll
0x14012ab60 _configthreadlocale
0x14012ab68 localeconv
EAT(Export Address Table) is none
d3dx11_43.dll
0x14012ae88 D3DX11CreateShaderResourceViewFromMemory
d3d11.dll
0x14012ae78 D3D11CreateDeviceAndSwapChain
D3DCOMPILER_43.dll
0x14012a170 D3DCompile
KERNEL32.dll
0x14012a1a8 ReadFile
0x14012a1b0 PeekNamedPipe
0x14012a1b8 WaitForMultipleObjects
0x14012a1c0 GetFileSizeEx
0x14012a1c8 CreateFileMappingA
0x14012a1d0 GetEnvironmentVariableA
0x14012a1d8 WaitForSingleObjectEx
0x14012a1e0 MoveFileExA
0x14012a1e8 GetTickCount
0x14012a1f0 CreateFileMappingW
0x14012a1f8 MapViewOfFile
0x14012a200 UnmapViewOfFile
0x14012a208 GetModuleFileNameA
0x14012a210 GetModuleHandleW
0x14012a218 QueryFullProcessImageNameW
0x14012a220 QueryPerformanceCounter
0x14012a228 FreeLibrary
0x14012a230 VerSetConditionMask
0x14012a238 VerifyVersionInfoA
0x14012a240 DeleteCriticalSection
0x14012a248 OutputDebugStringW
0x14012a250 ReleaseSRWLockExclusive
0x14012a258 AcquireSRWLockExclusive
0x14012a260 WakeAllConditionVariable
0x14012a268 SleepConditionVariableSRW
0x14012a270 RtlCaptureContext
0x14012a278 RtlLookupFunctionEntry
0x14012a280 RtlVirtualUnwind
0x14012a288 UnhandledExceptionFilter
0x14012a290 SetUnhandledExceptionFilter
0x14012a298 IsProcessorFeaturePresent
0x14012a2a0 GetCurrentProcessId
0x14012a2a8 GetCurrentThreadId
0x14012a2b0 GetSystemTimeAsFileTime
0x14012a2b8 InitializeSListHead
0x14012a2c0 GetProcAddress
0x14012a2c8 QueryPerformanceFrequency
0x14012a2d0 LoadLibraryA
0x14012a2d8 GetModuleHandleA
0x14012a2e0 GlobalUnlock
0x14012a2e8 GlobalLock
0x14012a2f0 GlobalFree
0x14012a2f8 GlobalAlloc
0x14012a300 GetFileAttributesW
0x14012a308 lstrcmpiW
0x14012a310 GetConsoleWindow
0x14012a318 WideCharToMultiByte
0x14012a320 CreateThread
0x14012a328 CloseHandle
0x14012a330 Process32FirstW
0x14012a338 CreateFileA
0x14012a340 Process32NextW
0x14012a348 GetLastError
0x14012a350 Sleep
0x14012a358 GetSystemDirectoryA
0x14012a360 SleepEx
0x14012a368 LeaveCriticalSection
0x14012a370 CreateFileW
0x14012a378 HeapDestroy
0x14012a380 HeapAlloc
0x14012a388 HeapReAlloc
0x14012a390 GetFileType
0x14012a398 HeapFree
0x14012a3a0 HeapSize
0x14012a3a8 GetProcessHeap
0x14012a3b0 GetCurrentProcess
0x14012a3b8 MultiByteToWideChar
0x14012a3c0 CreateToolhelp32Snapshot
0x14012a3c8 SetConsoleWindowInfo
0x14012a3d0 TerminateProcess
0x14012a3d8 DeviceIoControl
0x14012a3e0 GetStdHandle
0x14012a3e8 SetConsoleScreenBufferSize
0x14012a3f0 SetConsoleTitleA
0x14012a3f8 SetConsoleTextAttribute
0x14012a400 InitializeCriticalSectionEx
0x14012a408 IsDebuggerPresent
0x14012a410 SetLastError
0x14012a418 FormatMessageA
0x14012a420 EnterCriticalSection
0x14012a428 LocalFree
0x14012a430 VirtualProtect
USER32.dll
0x14012a740 LoadCursorW
0x14012a748 ScreenToClient
0x14012a750 SetCursor
0x14012a758 SetCursorPos
0x14012a760 OpenClipboard
0x14012a768 CloseClipboard
0x14012a770 EmptyClipboard
0x14012a778 GetCursorPos
0x14012a780 UpdateWindow
0x14012a788 GetClipboardData
0x14012a790 SetClipboardData
0x14012a798 FindWindowA
0x14012a7a0 GetKeyState
0x14012a7a8 GetWindow
0x14012a7b0 MessageBoxA
0x14012a7b8 DestroyWindow
0x14012a7c0 SetWindowPos
0x14012a7c8 SetWindowLongPtrW
0x14012a7d0 GetSystemMetrics
0x14012a7d8 GetWindowLongPtrW
0x14012a7e0 ShowWindow
0x14012a7e8 GetAsyncKeyState
0x14012a7f0 DispatchMessageW
0x14012a7f8 ClientToScreen
0x14012a800 PeekMessageW
0x14012a808 GetForegroundWindow
0x14012a810 SetLayeredWindowAttributes
0x14012a818 TranslateMessage
0x14012a820 FindWindowW
0x14012a828 GetClientRect
ADVAPI32.dll
0x14012a000 StartServiceW
0x14012a008 ControlService
0x14012a010 DeleteService
0x14012a018 OpenSCManagerW
0x14012a020 CloseServiceHandle
0x14012a028 QueryServiceStatus
0x14012a030 CreateServiceW
0x14012a038 OpenProcessToken
0x14012a040 AddAccessAllowedAce
0x14012a048 GetLengthSid
0x14012a050 GetTokenInformation
0x14012a058 InitializeAcl
0x14012a060 IsValidSid
0x14012a068 SetSecurityInfo
0x14012a070 CopySid
0x14012a078 CryptEncrypt
0x14012a080 CryptImportKey
0x14012a088 CryptDestroyKey
0x14012a090 CryptDestroyHash
0x14012a098 CryptHashData
0x14012a0a0 CryptCreateHash
0x14012a0a8 CryptGenRandom
0x14012a0b0 CryptGetHashParam
0x14012a0b8 CryptReleaseContext
0x14012a0c0 CryptAcquireContextA
0x14012a0c8 ConvertSidToStringSidA
0x14012a0d0 OpenServiceW
SHELL32.dll
0x14012a730 ShellExecuteA
MSVCP140.dll
0x14012a440 ?uflow@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x14012a448 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x14012a450 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x14012a458 ?setbuf@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAPEAV12@PEAD_J@Z
0x14012a460 ?sync@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x14012a468 ?imbue@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAXAEBVlocale@2@@Z
0x14012a470 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a478 ??1?$basic_ostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a480 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAV01@AEAV01@@Z@Z
0x14012a488 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAVios_base@1@AEAV21@@Z@Z
0x14012a490 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@_N@Z
0x14012a498 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@H@Z
0x14012a4a0 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@M@Z
0x14012a4a8 ??1?$basic_istream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a4b0 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEA_N@Z
0x14012a4b8 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEAH@Z
0x14012a4c0 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEAM@Z
0x14012a4c8 ?getloc@ios_base@std@@QEBA?AVlocale@2@XZ
0x14012a4d0 ?_Getcat@?$ctype@D@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x14012a4d8 ??1?$codecvt@_WDU_Mbstatet@@@std@@MEAA@XZ
0x14012a4e0 ??0?$codecvt@_WDU_Mbstatet@@@std@@QEAA@_K@Z
0x14012a4e8 ?in@?$codecvt@_WDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEA_W3AEAPEA_W@Z
0x14012a4f0 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x14012a4f8 ?_Addfac@_Locimp@locale@std@@AEAAXPEAVfacet@23@_K@Z
0x14012a500 ?_Decref@facet@locale@std@@UEAAPEAV_Facet_base@3@XZ
0x14012a508 ?_Incref@facet@locale@std@@UEAAXXZ
0x14012a510 ??Bid@locale@std@@QEAA_KXZ
0x14012a518 ??0?$basic_iostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@@Z
0x14012a520 ??1?$basic_iostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a528 ?cout@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x14012a530 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x14012a538 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x14012a540 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x14012a548 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x14012a550 ?write@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@PEBD_J@Z
0x14012a558 ?put@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@D@Z
0x14012a560 ?widen@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADD@Z
0x14012a568 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x14012a570 ?sgetc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x14012a578 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x14012a580 ?snextc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x14012a588 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x14012a590 ?_Ipfx@?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA_N_N@Z
0x14012a598 _Mtx_unlock
0x14012a5a0 _Thrd_join
0x14012a5a8 _Xtime_get_ticks
0x14012a5b0 ?_Unlock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x14012a5b8 ?_Lock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x14012a5c0 ?sbumpc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x14012a5c8 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x14012a5d0 ??4?$_Yarn@D@std@@QEAAAEAV01@PEBD@Z
0x14012a5d8 ??0?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x14012a5e0 ??0?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x14012a5e8 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x14012a5f0 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x14012a5f8 ?uncaught_exceptions@std@@YAHXZ
0x14012a600 ?_Throw_Cpp_error@std@@YAXH@Z
0x14012a608 ??0_Lockit@std@@QEAA@H@Z
0x14012a610 _Query_perf_counter
0x14012a618 _Thrd_id
0x14012a620 _Thrd_sleep
0x14012a628 _Cnd_do_broadcast_at_thread_exit
0x14012a630 _Mtx_init_in_situ
0x14012a638 _Mtx_lock
0x14012a640 _Mtx_destroy_in_situ
0x14012a648 ?id@?$codecvt@_WDU_Mbstatet@@@std@@2V0locale@2@A
0x14012a650 ?id@?$ctype@D@std@@2V0locale@2@A
0x14012a658 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x14012a660 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x14012a668 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x14012a670 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x14012a678 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x14012a680 ?setw@std@@YA?AU?$_Smanip@_J@1@_J@Z
0x14012a688 ?_Fiopen@std@@YAPEAU_iobuf@@PEBDHH@Z
0x14012a690 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x14012a698 ?cerr@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x14012a6a0 ?_Xout_of_range@std@@YAXPEBD@Z
0x14012a6a8 ?cin@std@@3V?$basic_istream@DU?$char_traits@D@std@@@1@A
0x14012a6b0 ?_Init@locale@std@@CAPEAV_Locimp@12@_N@Z
0x14012a6b8 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x14012a6c0 ?_Xbad_function_call@std@@YAXXZ
0x14012a6c8 ?_Xlength_error@std@@YAXPEBD@Z
0x14012a6d0 _Query_perf_frequency
0x14012a6d8 ??1_Lockit@std@@QEAA@XZ
0x14012a6e0 ?_New_Locimp@_Locimp@locale@std@@CAPEAV123@AEBV123@@Z
dwmapi.dll
0x14012ae98 DwmExtendFrameIntoClientArea
WINHTTP.dll
0x14012a8e8 WinHttpQueryOption
0x14012a8f0 WinHttpOpen
0x14012a8f8 WinHttpSendRequest
0x14012a900 WinHttpCloseHandle
0x14012a908 WinHttpOpenRequest
0x14012a910 WinHttpReceiveResponse
0x14012a918 WinHttpConnect
CRYPT32.dll
0x14012a0e0 CertFreeCertificateChainEngine
0x14012a0e8 CertCreateCertificateChainEngine
0x14012a0f0 CryptQueryObject
0x14012a0f8 CertGetNameStringA
0x14012a100 CertFindExtension
0x14012a108 CertAddCertificateContextToStore
0x14012a110 CryptDecodeObjectEx
0x14012a118 CertGetCertificateChain
0x14012a120 PFXImportCertStore
0x14012a128 CryptStringToBinaryA
0x14012a130 CertFindCertificateInStore
0x14012a138 CertEnumCertificatesInStore
0x14012a140 CertCloseStore
0x14012a148 CertGetCertificateContextProperty
0x14012a150 CertOpenStore
0x14012a158 CertFreeCertificateChain
0x14012a160 CertFreeCertificateContext
IMM32.dll
0x14012a180 ImmReleaseContext
0x14012a188 ImmSetCompositionWindow
0x14012a190 ImmGetContext
0x14012a198 ImmSetCandidateWindow
Normaliz.dll
0x14012a6f0 IdnToAscii
WLDAP32.dll
0x14012a928 None
0x14012a930 None
0x14012a938 None
0x14012a940 None
0x14012a948 None
0x14012a950 None
0x14012a958 None
0x14012a960 None
0x14012a968 None
0x14012a970 None
0x14012a978 None
0x14012a980 None
0x14012a988 None
0x14012a990 None
0x14012a998 None
0x14012a9a0 None
0x14012a9a8 None
0x14012a9b0 None
WS2_32.dll
0x14012a9c0 freeaddrinfo
0x14012a9c8 recvfrom
0x14012a9d0 __WSAFDIsSet
0x14012a9d8 ioctlsocket
0x14012a9e0 listen
0x14012a9e8 htonl
0x14012a9f0 sendto
0x14012a9f8 accept
0x14012aa00 WSACleanup
0x14012aa08 WSAStartup
0x14012aa10 WSAIoctl
0x14012aa18 gethostname
0x14012aa20 getaddrinfo
0x14012aa28 closesocket
0x14012aa30 WSASetLastError
0x14012aa38 socket
0x14012aa40 setsockopt
0x14012aa48 ntohs
0x14012aa50 htons
0x14012aa58 getsockopt
0x14012aa60 getsockname
0x14012aa68 getpeername
0x14012aa70 ntohl
0x14012aa78 ind
0x14012aa80 WSAGetLastError
0x14012aa88 select
0x14012aa90 send
0x14012aa98 recv
0x14012aaa0 connect
RPCRT4.dll
0x14012a710 UuidToStringA
0x14012a718 UuidCreate
0x14012a720 RpcStringFreeA
PSAPI.DLL
0x14012a700 GetModuleInformation
USERENV.dll
0x14012a838 UnloadUserProfile
VCRUNTIME140_1.dll
0x14012a8d8 __CxxFrameHandler4
VCRUNTIME140.dll
0x14012a848 __std_exception_copy
0x14012a850 memset
0x14012a858 strchr
0x14012a860 strrchr
0x14012a868 __std_exception_destroy
0x14012a870 longjmp
0x14012a878 __C_specific_handler
0x14012a880 __std_terminate
0x14012a888 __current_exception
0x14012a890 __current_exception_context
0x14012a898 memcpy
0x14012a8a0 strstr
0x14012a8a8 _CxxThrowException
0x14012a8b0 memchr
0x14012a8b8 memcmp
0x14012a8c0 __intrinsic_setjmp
0x14012a8c8 memmove
api-ms-win-crt-runtime-l1-1-0.dll
0x14012abf8 exit
0x14012ac00 _invalid_parameter_noinfo_noreturn
0x14012ac08 terminate
0x14012ac10 strerror
0x14012ac18 __sys_nerr
0x14012ac20 _invalid_parameter_noinfo
0x14012ac28 _resetstkoflw
0x14012ac30 system
0x14012ac38 _getpid
0x14012ac40 _beginthreadex
0x14012ac48 _register_thread_local_exe_atexit_callback
0x14012ac50 _c_exit
0x14012ac58 __p___argv
0x14012ac60 __p___argc
0x14012ac68 _exit
0x14012ac70 _initterm_e
0x14012ac78 _initterm
0x14012ac80 _get_initial_narrow_environment
0x14012ac88 _set_app_type
0x14012ac90 _seh_filter_exe
0x14012ac98 _cexit
0x14012aca0 _crt_atexit
0x14012aca8 _register_onexit_function
0x14012acb0 _initialize_onexit_table
0x14012acb8 _initialize_narrow_environment
0x14012acc0 _configure_narrow_argv
0x14012acc8 _errno
api-ms-win-crt-stdio-l1-1-0.dll
0x14012acd8 fclose
0x14012ace0 __p__commode
0x14012ace8 __acrt_iob_func
0x14012acf0 _lseeki64
0x14012acf8 __stdio_common_vsprintf_s
0x14012ad00 fgetc
0x14012ad08 fflush
0x14012ad10 _read
0x14012ad18 feof
0x14012ad20 fputs
0x14012ad28 fopen
0x14012ad30 _write
0x14012ad38 _close
0x14012ad40 _open
0x14012ad48 __stdio_common_vfprintf
0x14012ad50 fputc
0x14012ad58 _pclose
0x14012ad60 fgets
0x14012ad68 fwrite
0x14012ad70 _set_fmode
0x14012ad78 __stdio_common_vsscanf
0x14012ad80 _wfopen
0x14012ad88 __stdio_common_vsprintf
0x14012ad90 fseek
0x14012ad98 ftell
0x14012ada0 _get_stream_buffer_pointers
0x14012ada8 _fseeki64
0x14012adb0 fread
0x14012adb8 fsetpos
0x14012adc0 ungetc
0x14012adc8 fgetpos
0x14012add0 setvbuf
0x14012add8 _popen
api-ms-win-crt-heap-l1-1-0.dll
0x14012ab28 malloc
0x14012ab30 _set_new_mode
0x14012ab38 realloc
0x14012ab40 free
0x14012ab48 calloc
0x14012ab50 _callnewh
api-ms-win-crt-math-l1-1-0.dll
0x14012ab78 __setusermatherr
0x14012ab80 tanf
0x14012ab88 _dclass
0x14012ab90 fmodf
0x14012ab98 cosf
0x14012aba0 cos
0x14012aba8 ceilf
0x14012abb0 atanf
0x14012abb8 asinf
0x14012abc0 powf
0x14012abc8 roundf
0x14012abd0 sin
0x14012abd8 sinf
0x14012abe0 sqrtf
0x14012abe8 acosf
api-ms-win-crt-string-l1-1-0.dll
0x14012ade8 strncmp
0x14012adf0 strncpy
0x14012adf8 isupper
0x14012ae00 tolower
0x14012ae08 strpbrk
0x14012ae10 strcmp
0x14012ae18 _strdup
0x14012ae20 strspn
0x14012ae28 strcspn
api-ms-win-crt-time-l1-1-0.dll
0x14012ae38 _localtime64_s
0x14012ae40 _gmtime64
0x14012ae48 strftime
0x14012ae50 _time64
api-ms-win-crt-convert-l1-1-0.dll
0x14012aab0 strtoull
0x14012aab8 strtoul
0x14012aac0 strtod
0x14012aac8 atof
0x14012aad0 atoi
0x14012aad8 strtol
0x14012aae0 strtoll
api-ms-win-crt-utility-l1-1-0.dll
0x14012ae60 qsort
0x14012ae68 rand
api-ms-win-crt-filesystem-l1-1-0.dll
0x14012aaf0 _unlock_file
0x14012aaf8 _lock_file
0x14012ab00 _unlink
0x14012ab08 _stat64
0x14012ab10 _fstat64
0x14012ab18 _access
api-ms-win-crt-locale-l1-1-0.dll
0x14012ab60 _configthreadlocale
0x14012ab68 localeconv
EAT(Export Address Table) is none