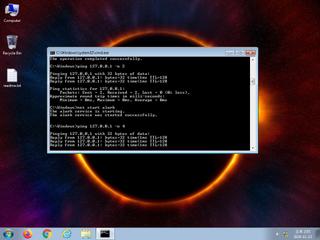
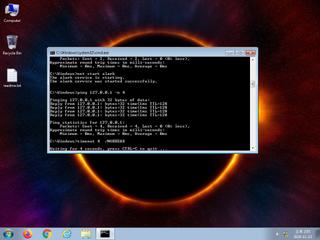
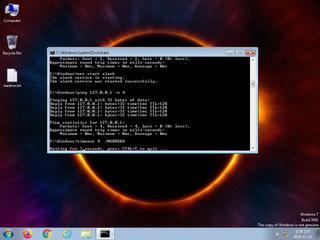
ScreenShot
| Created | 2024.11.13 14:11 | Machine | s1_win7_x6403 |
| Filename | clr.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, RAR self-extracting archive | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 55 detected (lCIq, Malicious, score, Clearlogs, Clearlog, Unsafe, grayware, confidence, many, HackTool, AYQF, moderate confidence, multiple detections, Genome, Scar, cqqapi, CLASSIC, VirusConstructor, TSPY, FAREIT, YYSRV, Detected, Malware@#2f8qa3jru3l1h, Multiverze, Razy, RFBI, R348454, Artemis, BScope, Ditertag, Probably Heur, ExeHeaderL, Qimw, susgen) | ||
| md5 | a736e23ae291f6d3a848fdb1aaa7348f | ||
| sha256 | d00d806f1df7195c4d6b5757d90c3e81fdbf8d4f2efcbc895ee752af0b09b28c | ||
| ssdeep | 1536:o8V6g/5b+Dae3E/j9pGtbFIViUDq51plh6HcUa3WloAuyQjn:o8V6E5e3YxGF6zDUj/Rj3Pjn | ||
| imphash | af7b8813a2e213ad2ed4a1d42c1b2975 | ||
| impfuzzy | 6:dBJAEHGDzyRlbRmVOZ/EwRgsyIBMeGaTKOdLMKJAm3EQbS4QG:VA/DzqYOZ9RghIBXGq+m3EP4QG | ||
Network IP location
Signature (15cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 55 AntiVirus engines on VirusTotal as malicious |
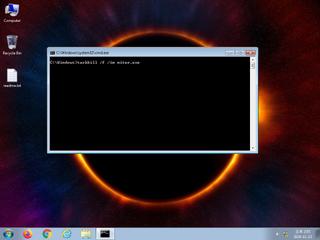
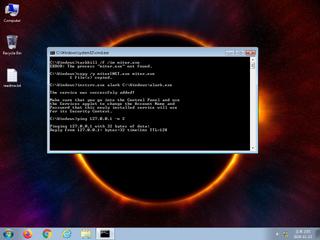
| warning | Stops Windows services |
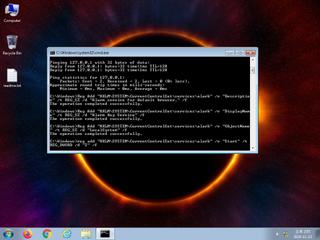
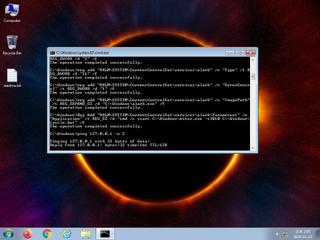
| watch | Installs itself for autorun at Windows startup |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a service |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Executes one or more WMI queries |
| notice | Terminates another process |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is compressed using UPX |
| notice | Uses Windows utilities for basic Windows functionality |
| info | Checks amount of memory in system |
| info | Command line console output was observed |
| info | Queries for the computername |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.DLL
0x426ef0 LoadLibraryA
0x426ef4 GetProcAddress
0x426ef8 VirtualProtect
0x426efc VirtualAlloc
0x426f00 VirtualFree
0x426f04 ExitProcess
ADVAPI32.dll
0x426f0c RegCloseKey
COMCTL32.dll
0x426f14 None
COMDLG32.dll
0x426f1c GetSaveFileNameA
GDI32.dll
0x426f24 DeleteDC
ole32.dll
0x426f2c OleInitialize
OLEAUT32.dll
0x426f34 VariantInit
SHELL32.dll
0x426f3c SHGetMalloc
USER32.dll
0x426f44 GetDC
EAT(Export Address Table) is none
KERNEL32.DLL
0x426ef0 LoadLibraryA
0x426ef4 GetProcAddress
0x426ef8 VirtualProtect
0x426efc VirtualAlloc
0x426f00 VirtualFree
0x426f04 ExitProcess
ADVAPI32.dll
0x426f0c RegCloseKey
COMCTL32.dll
0x426f14 None
COMDLG32.dll
0x426f1c GetSaveFileNameA
GDI32.dll
0x426f24 DeleteDC
ole32.dll
0x426f2c OleInitialize
OLEAUT32.dll
0x426f34 VariantInit
SHELL32.dll
0x426f3c SHGetMalloc
USER32.dll
0x426f44 GetDC
EAT(Export Address Table) is none