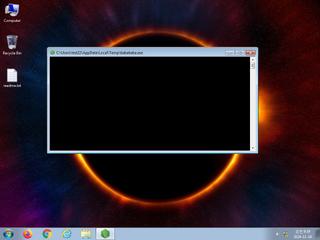
ScreenShot
| Created | 2024.11.18 09:42 | Machine | s1_win7_x6403 |
| Filename | babababa.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 11 detected (Artemis, a variant of Generik, FECVJLI, FileRepMalware, Misc, Wacatac) | ||
| md5 | 8fb77810c61e160a657298815346996e | ||
| sha256 | a0840c581f8f1d606fdc43bc98bd386755433bf1fb36647ecf2165eea433ff66 | ||
| ssdeep | 393216:d76L6otUitqtH7wHtXq2pt2jbOCacCFIK0fpP9HF4VW8yfGnVQx4urYsANulL7Nv:d0LoCOn+2Gs4urYDNulLBiub | ||
| imphash | 66b10d8b5718b0fd6fb4865843d44280 | ||
| impfuzzy | 192:JeW92FX/rbFrTisrck/gkehFpiV37W5W/bF7E:JejViMlQFpi5uIx7E | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 11 AntiVirus engines on VirusTotal as malicious |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|