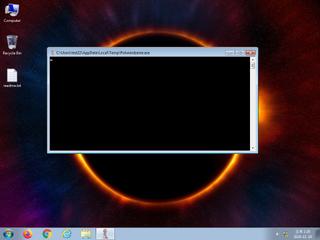
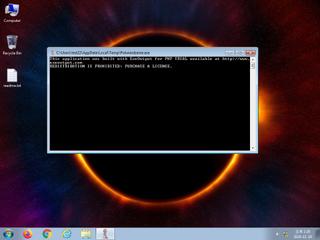
ScreenShot
| Created | 2024.11.19 14:49 | Machine | s1_win7_x6403 |
| Filename | Potwierdzenie.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 8 detected (AIDetectMalware, Unsafe, grayware, confidence, Malicious, akai) | ||
| md5 | bb1c7286c327eafc7cf6a21492cdfa0f | ||
| sha256 | 8ac63cd639f78b172efc3c4cfecbe7dae3cd7f3dc245d31476187b0517c1babd | ||
| ssdeep | 786432:npmGxqs8IFPB/4vQiZYgVcNioTjAHaUUfC+TDNED:n8bGJQvCgVxcj4zaC+TZe | ||
| imphash | 25fdfeb72f9d8c6c3fcea46af42b3f09 | ||
| impfuzzy | 96:DG6k9KcN7Jj4INTX1V90pOeyX5b3xWNNiyfHMqKLKmM:DQjFTFjt5pb3ENNv/0LK | ||
Network IP location
Signature (20cnts)
| Level | Description |
|---|---|
| danger | Executed a process and injected code into it |
| watch | Allocates execute permission to another process indicative of possible code injection |
| watch | Creates a thread using CreateRemoteThread in a non-child process indicative of process injection |
| watch | Detects the presence of Wine emulator |
| watch | Manipulates memory of a non-child process indicative of process injection |
| watch | One or more of the buffers contains an embedded PE file |
| watch | Potential code injection by writing to the memory of another process |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates hidden or system file |
| notice | File has been identified by 8 AntiVirus engines on VirusTotal as malicious |
| notice | One or more potentially interesting buffers were extracted |
| notice | Potentially malicious URLs were found in the process memory dump |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
| info | Queries for the computername |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (31cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | Code_injection | Code injection with CreateRemoteThread in a remote process | memory |
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | Hijack_Network | Hijack network configuration | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | local_credential_Steal | Steal credential | memory |
| notice | Network_DNS | Communications use DNS | memory |
| notice | network_smtp_raw | Communications smtp | memory |
| notice | Network_TCP_Socket | Communications over RAW Socket | memory |
| notice | Persistence | Install itself for autorun at Windows startup | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerException__ConsoleCtrl | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | ftp_command | ftp command | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x807368 SetFileAttributesW
0x80736c GetFileType
0x807370 GetACP
0x807374 GetExitCodeProcess
0x807378 CloseHandle
0x80737c LocalFree
0x807380 GetCurrentProcessId
0x807384 SizeofResource
0x807388 VirtualProtect
0x80738c TerminateThread
0x807390 QueryPerformanceFrequency
0x807394 IsDebuggerPresent
0x807398 FlushInstructionCache
0x80739c GetFullPathNameW
0x8073a0 VirtualFree
0x8073a4 GetProcessHeap
0x8073a8 ExitProcess
0x8073ac HeapAlloc
0x8073b0 GetCPInfoExW
0x8073b4 RtlUnwind
0x8073b8 GetCPInfo
0x8073bc EnumSystemLocalesW
0x8073c0 GetStdHandle
0x8073c4 GetTimeZoneInformation
0x8073c8 DisconnectNamedPipe
0x8073cc GetModuleHandleW
0x8073d0 FreeLibrary
0x8073d4 TryEnterCriticalSection
0x8073d8 SetDllDirectoryW
0x8073dc HeapDestroy
0x8073e0 ReadFile
0x8073e4 CreateProcessW
0x8073e8 GetLastError
0x8073ec GetModuleFileNameW
0x8073f0 SetLastError
0x8073f4 FindResourceW
0x8073f8 CreateThread
0x8073fc CompareStringW
0x807400 lstrcmpA
0x807404 LoadLibraryA
0x807408 ResetEvent
0x80740c FreeResource
0x807410 GetVersion
0x807414 RaiseException
0x807418 FormatMessageW
0x80741c SwitchToThread
0x807420 GetExitCodeThread
0x807424 OutputDebugStringW
0x807428 GetCurrentThread
0x80742c LoadLibraryExW
0x807430 LockResource
0x807434 GetCurrentThreadId
0x807438 UnhandledExceptionFilter
0x80743c VirtualQuery
0x807440 VirtualQueryEx
0x807444 Sleep
0x807448 EnterCriticalSection
0x80744c SetFilePointer
0x807450 FlushFileBuffers
0x807454 LoadResource
0x807458 SuspendThread
0x80745c GetTickCount
0x807460 WaitForMultipleObjects
0x807464 GetFileSize
0x807468 GetStartupInfoW
0x80746c GetFileAttributesW
0x807470 SetCurrentDirectoryW
0x807474 InitializeCriticalSection
0x807478 GetThreadPriority
0x80747c GetCurrentProcess
0x807480 SetThreadPriority
0x807484 VirtualAlloc
0x807488 GetCommandLineW
0x80748c GetSystemInfo
0x807490 LeaveCriticalSection
0x807494 GetProcAddress
0x807498 ResumeThread
0x80749c GetVersionExW
0x8074a0 VerifyVersionInfoW
0x8074a4 GetModuleHandleA
0x8074a8 HeapCreate
0x8074ac LCMapStringW
0x8074b0 GetDiskFreeSpaceW
0x8074b4 VerSetConditionMask
0x8074b8 FindFirstFileW
0x8074bc GetUserDefaultUILanguage
0x8074c0 GetConsoleOutputCP
0x8074c4 GetConsoleCP
0x8074c8 lstrlenW
0x8074cc QueryPerformanceCounter
0x8074d0 SetEndOfFile
0x8074d4 InitializeCriticalSectionAndSpinCount
0x8074d8 HeapFree
0x8074dc WideCharToMultiByte
0x8074e0 FindClose
0x8074e4 MultiByteToWideChar
0x8074e8 LoadLibraryW
0x8074ec SetEvent
0x8074f0 GetLocaleInfoW
0x8074f4 CreateFileW
0x8074f8 DeleteFileW
0x8074fc IsDBCSLeadByteEx
0x807500 ConnectNamedPipe
0x807504 GetEnvironmentVariableW
0x807508 GetLocalTime
0x80750c WaitForSingleObject
0x807510 WriteFile
0x807514 CreateNamedPipeW
0x807518 ExitThread
0x80751c DeleteCriticalSection
0x807520 GetDateFormatW
0x807524 TlsGetValue
0x807528 IsValidLocale
0x80752c TlsSetValue
0x807530 GetSystemDefaultUILanguage
0x807534 EnumCalendarInfoW
0x807538 LocalAlloc
0x80753c RemoveDirectoryW
0x807540 SetConsoleCtrlHandler
0x807544 CreateEventW
0x807548 SetThreadLocale
0x80754c GetThreadLocale
user32.dll
0x807554 UnregisterClassW
0x807558 CreateWindowExW
0x80755c GetClassInfoW
0x807560 WaitForInputIdle
0x807564 TranslateMessage
0x807568 CharLowerBuffW
0x80756c CharUpperW
0x807570 PeekMessageW
0x807574 GetSystemMetrics
0x807578 DefWindowProcW
0x80757c SetWindowLongW
0x807580 GetWindowLongW
0x807584 PostMessageW
0x807588 MessageBoxW
0x80758c DestroyWindow
0x807590 CharUpperBuffW
0x807594 SendMessageTimeoutW
0x807598 RegisterClassW
0x80759c CharNextW
0x8075a0 MsgWaitForMultipleObjects
0x8075a4 LoadStringW
0x8075a8 DispatchMessageW
oleaut32.dll
0x8075b0 SafeArrayPutElement
0x8075b4 VariantInit
0x8075b8 VariantClear
0x8075bc SysFreeString
0x8075c0 SafeArrayAccessData
0x8075c4 SysReAllocStringLen
0x8075c8 SafeArrayCreate
0x8075cc SafeArrayGetElement
0x8075d0 SysAllocStringLen
0x8075d4 SafeArrayUnaccessData
0x8075d8 SafeArrayPtrOfIndex
0x8075dc VariantCopy
0x8075e0 SafeArrayGetUBound
0x8075e4 SafeArrayGetLBound
0x8075e8 VariantChangeType
kernel32
0x8075f0 InterlockedPopEntrySList
0x8075f4 QueryDepthSList
0x8075f8 InterlockedFlushSList
0x8075fc InitializeSListHead
0x807600 InterlockedPushEntrySList
advapi32.dll
0x807608 RegSetValueExW
0x80760c RegConnectRegistryW
0x807610 RegEnumKeyExW
0x807614 RegLoadKeyW
0x807618 RegDeleteKeyW
0x80761c RegOpenKeyExW
0x807620 RegQueryInfoKeyW
0x807624 RegUnLoadKeyW
0x807628 RegSaveKeyW
0x80762c RegDeleteValueW
0x807630 RegReplaceKeyW
0x807634 RegFlushKey
0x807638 RegEnumValueW
0x80763c RegQueryValueExW
0x807640 InitializeSecurityDescriptor
0x807644 RegCloseKey
0x807648 RegCreateKeyExW
0x80764c SetSecurityDescriptorDacl
0x807650 RegRestoreKeyW
EAT(Export Address Table) Library
0x412504 __dbk_fcall_wrapper
0x7fa63c dbkFCallWrapperAddr
kernel32.dll
0x807368 SetFileAttributesW
0x80736c GetFileType
0x807370 GetACP
0x807374 GetExitCodeProcess
0x807378 CloseHandle
0x80737c LocalFree
0x807380 GetCurrentProcessId
0x807384 SizeofResource
0x807388 VirtualProtect
0x80738c TerminateThread
0x807390 QueryPerformanceFrequency
0x807394 IsDebuggerPresent
0x807398 FlushInstructionCache
0x80739c GetFullPathNameW
0x8073a0 VirtualFree
0x8073a4 GetProcessHeap
0x8073a8 ExitProcess
0x8073ac HeapAlloc
0x8073b0 GetCPInfoExW
0x8073b4 RtlUnwind
0x8073b8 GetCPInfo
0x8073bc EnumSystemLocalesW
0x8073c0 GetStdHandle
0x8073c4 GetTimeZoneInformation
0x8073c8 DisconnectNamedPipe
0x8073cc GetModuleHandleW
0x8073d0 FreeLibrary
0x8073d4 TryEnterCriticalSection
0x8073d8 SetDllDirectoryW
0x8073dc HeapDestroy
0x8073e0 ReadFile
0x8073e4 CreateProcessW
0x8073e8 GetLastError
0x8073ec GetModuleFileNameW
0x8073f0 SetLastError
0x8073f4 FindResourceW
0x8073f8 CreateThread
0x8073fc CompareStringW
0x807400 lstrcmpA
0x807404 LoadLibraryA
0x807408 ResetEvent
0x80740c FreeResource
0x807410 GetVersion
0x807414 RaiseException
0x807418 FormatMessageW
0x80741c SwitchToThread
0x807420 GetExitCodeThread
0x807424 OutputDebugStringW
0x807428 GetCurrentThread
0x80742c LoadLibraryExW
0x807430 LockResource
0x807434 GetCurrentThreadId
0x807438 UnhandledExceptionFilter
0x80743c VirtualQuery
0x807440 VirtualQueryEx
0x807444 Sleep
0x807448 EnterCriticalSection
0x80744c SetFilePointer
0x807450 FlushFileBuffers
0x807454 LoadResource
0x807458 SuspendThread
0x80745c GetTickCount
0x807460 WaitForMultipleObjects
0x807464 GetFileSize
0x807468 GetStartupInfoW
0x80746c GetFileAttributesW
0x807470 SetCurrentDirectoryW
0x807474 InitializeCriticalSection
0x807478 GetThreadPriority
0x80747c GetCurrentProcess
0x807480 SetThreadPriority
0x807484 VirtualAlloc
0x807488 GetCommandLineW
0x80748c GetSystemInfo
0x807490 LeaveCriticalSection
0x807494 GetProcAddress
0x807498 ResumeThread
0x80749c GetVersionExW
0x8074a0 VerifyVersionInfoW
0x8074a4 GetModuleHandleA
0x8074a8 HeapCreate
0x8074ac LCMapStringW
0x8074b0 GetDiskFreeSpaceW
0x8074b4 VerSetConditionMask
0x8074b8 FindFirstFileW
0x8074bc GetUserDefaultUILanguage
0x8074c0 GetConsoleOutputCP
0x8074c4 GetConsoleCP
0x8074c8 lstrlenW
0x8074cc QueryPerformanceCounter
0x8074d0 SetEndOfFile
0x8074d4 InitializeCriticalSectionAndSpinCount
0x8074d8 HeapFree
0x8074dc WideCharToMultiByte
0x8074e0 FindClose
0x8074e4 MultiByteToWideChar
0x8074e8 LoadLibraryW
0x8074ec SetEvent
0x8074f0 GetLocaleInfoW
0x8074f4 CreateFileW
0x8074f8 DeleteFileW
0x8074fc IsDBCSLeadByteEx
0x807500 ConnectNamedPipe
0x807504 GetEnvironmentVariableW
0x807508 GetLocalTime
0x80750c WaitForSingleObject
0x807510 WriteFile
0x807514 CreateNamedPipeW
0x807518 ExitThread
0x80751c DeleteCriticalSection
0x807520 GetDateFormatW
0x807524 TlsGetValue
0x807528 IsValidLocale
0x80752c TlsSetValue
0x807530 GetSystemDefaultUILanguage
0x807534 EnumCalendarInfoW
0x807538 LocalAlloc
0x80753c RemoveDirectoryW
0x807540 SetConsoleCtrlHandler
0x807544 CreateEventW
0x807548 SetThreadLocale
0x80754c GetThreadLocale
user32.dll
0x807554 UnregisterClassW
0x807558 CreateWindowExW
0x80755c GetClassInfoW
0x807560 WaitForInputIdle
0x807564 TranslateMessage
0x807568 CharLowerBuffW
0x80756c CharUpperW
0x807570 PeekMessageW
0x807574 GetSystemMetrics
0x807578 DefWindowProcW
0x80757c SetWindowLongW
0x807580 GetWindowLongW
0x807584 PostMessageW
0x807588 MessageBoxW
0x80758c DestroyWindow
0x807590 CharUpperBuffW
0x807594 SendMessageTimeoutW
0x807598 RegisterClassW
0x80759c CharNextW
0x8075a0 MsgWaitForMultipleObjects
0x8075a4 LoadStringW
0x8075a8 DispatchMessageW
oleaut32.dll
0x8075b0 SafeArrayPutElement
0x8075b4 VariantInit
0x8075b8 VariantClear
0x8075bc SysFreeString
0x8075c0 SafeArrayAccessData
0x8075c4 SysReAllocStringLen
0x8075c8 SafeArrayCreate
0x8075cc SafeArrayGetElement
0x8075d0 SysAllocStringLen
0x8075d4 SafeArrayUnaccessData
0x8075d8 SafeArrayPtrOfIndex
0x8075dc VariantCopy
0x8075e0 SafeArrayGetUBound
0x8075e4 SafeArrayGetLBound
0x8075e8 VariantChangeType
kernel32
0x8075f0 InterlockedPopEntrySList
0x8075f4 QueryDepthSList
0x8075f8 InterlockedFlushSList
0x8075fc InitializeSListHead
0x807600 InterlockedPushEntrySList
advapi32.dll
0x807608 RegSetValueExW
0x80760c RegConnectRegistryW
0x807610 RegEnumKeyExW
0x807614 RegLoadKeyW
0x807618 RegDeleteKeyW
0x80761c RegOpenKeyExW
0x807620 RegQueryInfoKeyW
0x807624 RegUnLoadKeyW
0x807628 RegSaveKeyW
0x80762c RegDeleteValueW
0x807630 RegReplaceKeyW
0x807634 RegFlushKey
0x807638 RegEnumValueW
0x80763c RegQueryValueExW
0x807640 InitializeSecurityDescriptor
0x807644 RegCloseKey
0x807648 RegCreateKeyExW
0x80764c SetSecurityDescriptorDacl
0x807650 RegRestoreKeyW
EAT(Export Address Table) Library
0x412504 __dbk_fcall_wrapper
0x7fa63c dbkFCallWrapperAddr