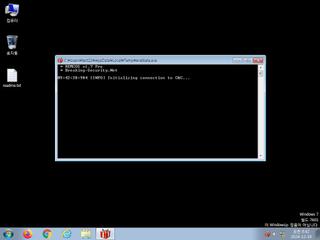
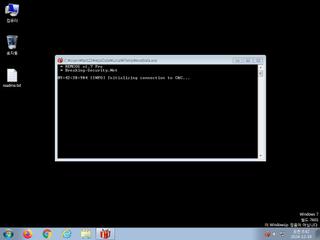
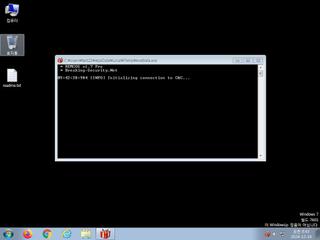
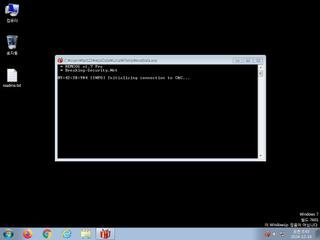
ScreenShot
| Created | 2024.12.19 08:45 | Machine | s1_win7_x6401 |
| Filename | evetbeta.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 69 detected (AIDetectMalware, Remcos, Malicious, score, Mauvaise, Unsafe, Rescoms, V3or, confidence, 100%, Rescom, Windows, Threat, RemcosRAT, Azden, erfeyu, CLASSIC, AGEN, DownLoader23, SOCMER, Real Protect, high, Static AI, Malicious PE, bgmwv, Detected, A@70v67g, AKNB, R198292, FOFQ, Genetic, GenAsa, 7DchS5duLaA, susgen) | ||
| md5 | 6f6137e6f85dc8dac7ff87ca4c86af4c | ||
| sha256 | a370eacabf4af9caa5502c39b40c95eda6be23666231e24da1b56277a222f3e9 | ||
| ssdeep | 1536:ohhW0YTGZWdVseJxaM9kraLdV2QkQ1TbPX8IHOCkIsI4ESHNTh9E+JP19qkP60rq:uhzYTGWVvJ8f2v1TbPzuMsIFSHNThy+O | ||
| imphash | d3a62971944197f0701c7049a9c739d1 | ||
| impfuzzy | 192:J+3ViWtwVWh4IrjUbRfF8XfjzjLqYs/F1SC:Js0W+NfF8Xfjzje3J | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | Connects to IP addresses that are no longer responding to requests (legitimate services will remain up-and-running usually) |
| danger | File has been identified by 69 AntiVirus engines on VirusTotal as malicious |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
| info | The executable uses a known packer |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | infoStealer_browser_b_Zero | browser info stealer | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | Network_Downloader | File Downloader | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x41006c GetModuleFileNameA
0x410070 GetLongPathNameA
0x410074 CreateMutexA
0x410078 OpenMutexA
0x41007c Process32Next
0x410080 Process32First
0x410084 CreateToolhelp32Snapshot
0x410088 SizeofResource
0x41008c LockResource
0x410090 LoadResource
0x410094 FindResourceA
0x410098 GetLocaleInfoA
0x41009c Process32NextW
0x4100a0 Process32FirstW
0x4100a4 lstrlenA
0x4100a8 GetDriveTypeA
0x4100ac CreateProcessA
0x4100b0 GetTickCount
0x4100b4 GlobalUnlock
0x4100b8 GlobalLock
0x4100bc GlobalAlloc
0x4100c0 WinExec
0x4100c4 GetCurrentProcessId
0x4100c8 CreateDirectoryW
0x4100cc CopyFileA
0x4100d0 GetFileAttributesW
0x4100d4 GetLogicalDriveStringsA
0x4100d8 GetCurrentProcess
0x4100dc ResumeThread
0x4100e0 SetThreadContext
0x4100e4 WriteProcessMemory
0x4100e8 VirtualAllocEx
0x4100ec ReadProcessMemory
0x4100f0 GetThreadContext
0x4100f4 VirtualAlloc
0x4100f8 GlobalFree
0x4100fc LocalAlloc
0x410100 TerminateProcess
0x410104 ReadFile
0x410108 PeekNamedPipe
0x41010c GetStdHandle
0x410110 CreatePipe
0x410114 OpenProcess
0x410118 DuplicateHandle
0x41011c GetCurrentThread
0x410120 lstrcpynA
0x410124 ExitProcess
0x410128 AllocConsole
0x41012c GetStartupInfoA
0x410130 ExpandEnvironmentStringsA
0x410134 FindFirstFileA
0x410138 FindNextFileA
0x41013c GetLastError
0x410140 LoadLibraryA
0x410144 GetProcAddress
0x410148 CreateFileMappingA
0x41014c MapViewOfFileEx
0x410150 DeleteFileA
0x410154 RemoveDirectoryA
0x410158 CloseHandle
0x41015c GetFileAttributesA
0x410160 SetFileAttributesA
0x410164 SetEvent
0x410168 TerminateThread
0x41016c FindFirstFileW
0x410170 FindNextFileW
0x410174 FindClose
0x410178 GetLocalTime
0x41017c CreateEventA
0x410180 WaitForSingleObject
0x410184 CreateDirectoryA
0x410188 ExitThread
0x41018c Sleep
0x410190 GetModuleHandleA
0x410194 DeleteFileW
0x410198 CreateThread
USER32.dll
0x4103dc GetWindowTextLengthA
0x4103e0 GetForegroundWindow
0x4103e4 UnhookWindowsHookEx
0x4103e8 CloseClipboard
0x4103ec GetClipboardData
0x4103f0 OpenClipboard
0x4103f4 SetClipboardData
0x4103f8 EmptyClipboard
0x4103fc ExitWindowsEx
0x410400 MessageBoxA
0x410404 GetKeyboardLayoutNameA
0x410408 GetWindowThreadProcessId
0x41040c ShowWindow
0x410410 CloseWindow
0x410414 GetWindowTextA
0x410418 GetWindowTextW
0x41041c EnumWindows
0x410420 SendInput
0x410424 CreateWindowExA
0x410428 RegisterClassExA
0x41042c AppendMenuA
0x410430 CreatePopupMenu
0x410434 TrackPopupMenu
0x410438 SetForegroundWindow
0x41043c GetCursorPos
0x410440 DefWindowProcA
0x410444 GetKeyState
0x410448 CallNextHookEx
0x41044c SetWindowsHookExA
0x410450 GetMessageA
0x410454 TranslateMessage
0x410458 GetKeyboardLayout
0x41045c FindWindowA
0x410460 DispatchMessageA
0x410464 IsWindowVisible
GDI32.dll
0x410040 CreateDCA
0x410044 CreateCompatibleDC
0x410048 GetDeviceCaps
0x41004c CreateCompatibleBitmap
0x410050 SelectObject
0x410054 StretchBlt
0x410058 GetObjectA
0x41005c GetDIBits
0x410060 DeleteObject
0x410064 DeleteDC
ADVAPI32.dll
0x410000 OpenProcessToken
0x410004 LookupPrivilegeValueA
0x410008 AdjustTokenPrivileges
0x41000c RegCreateKeyExA
0x410010 RegQueryInfoKeyA
0x410014 RegEnumKeyExA
0x410018 RegEnumValueA
0x41001c RegDeleteValueA
0x410020 RegCreateKeyA
0x410024 RegSetValueExA
0x410028 RegOpenKeyExA
0x41002c RegDeleteKeyA
0x410030 RegCloseKey
0x410034 RegQueryValueExA
0x410038 GetUserNameW
SHELL32.dll
0x4103bc ShellExecuteA
0x4103c0 ExtractIconA
0x4103c4 Shell_NotifyIconA
0x4103c8 ShellExecuteExA
0x4103cc ShellExecuteW
MSVCP60.dll
0x4101a0 ?begin@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEPADXZ
0x4101a4 ?end@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEPADXZ
0x4101a8 ?assign@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV12@ABV12@@Z
0x4101ac ?replace@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV12@IIPBD@Z
0x4101b0 ??8std@@YA_NPBDABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@@Z
0x4101b4 ??Y?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@PBD@Z
0x4101b8 ??4?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEAAV01@ABV01@@Z
0x4101bc ??0?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@ABV?$allocator@G@1@@Z
0x4101c0 ?find_last_of@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIDI@Z
0x4101c4 ??9std@@YA_NABV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@PBG@Z
0x4101c8 ??Y?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEAAV01@G@Z
0x4101cc ?substr@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBE?AV12@II@Z
0x4101d0 ?rfind@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEIGI@Z
0x4101d4 ?npos@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@2IB
0x4101d8 ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIPBDII@Z
0x4101dc ??0Init@ios_base@std@@QAE@XZ
0x4101e0 ??1Init@ios_base@std@@QAE@XZ
0x4101e4 ??0_Winit@std@@QAE@XZ
0x4101e8 ??1_Winit@std@@QAE@XZ
0x4101ec ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIABV12@I@Z
0x4101f0 ?find_last_of@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIPBDI@Z
0x4101f4 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@PBGABV10@@Z
0x4101f8 ??Y?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@D@Z
0x4101fc ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@DABV10@@Z
0x410200 ?rfind@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIDI@Z
0x410204 ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIDI@Z
0x410208 ?begin@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEPBGXZ
0x41020c ?end@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEPBGXZ
0x410210 ?length@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEIXZ
0x410214 ??Bios_base@std@@QBEPAXXZ
0x410218 ?assign@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV12@PBDI@Z
0x41021c ??6std@@YAAAV?$basic_ostream@DU?$char_traits@D@std@@@0@AAV10@PBD@Z
0x410220 ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIPBDI@Z
0x410224 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@IDABV?$allocator@D@1@@Z
0x410228 ??8std@@YA_NABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@0@Z
0x41022c ??0?$basic_ofstream@DU?$char_traits@D@std@@@std@@QAE@PBDH@Z
0x410230 ?is_open@?$basic_ofstream@DU?$char_traits@D@std@@@std@@QBE_NXZ
0x410234 ?data@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEPBDXZ
0x410238 ??8std@@YA_NABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@PBD@Z
0x41023c ??0logic_error@std@@QAE@ABV01@@Z
0x410240 ??0out_of_range@std@@QAE@ABV01@@Z
0x410244 ??1out_of_range@std@@UAE@XZ
0x410248 ??0out_of_range@std@@QAE@ABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@1@@Z
0x41024c ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@PBDABV?$allocator@D@1@@Z
0x410250 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@ABV?$allocator@D@1@@Z
0x410254 ??1?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@XZ
0x410258 ?c_str@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEPBDXZ
0x41025c ?resize@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEXI@Z
0x410260 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@ABV01@@Z
0x410264 ??4?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@ABV01@@Z
0x410268 ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@ABV10@0@Z
0x41026c ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@PBDABV10@@Z
0x410270 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@PBDIABV?$allocator@D@1@@Z
0x410274 ??_D?$basic_fstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x410278 ?close@?$basic_fstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x41027c ?write@?$basic_ostream@DU?$char_traits@D@std@@@std@@QAEAAV12@PBDH@Z
0x410280 ?seekp@?$basic_ostream@DU?$char_traits@D@std@@@std@@QAEAAV12@JW4seekdir@ios_base@2@@Z
0x410284 ??0?$basic_fstream@DU?$char_traits@D@std@@@std@@QAE@PBDH@Z
0x410288 ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@ABV10@PBD@Z
0x41028c ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@ABV10@D@Z
0x410290 ?size@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIXZ
0x410294 ??Y?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@ABV01@@Z
0x410298 ?substr@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBE?AV12@II@Z
0x41029c ?npos@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@2IB
0x4102a0 ?length@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIXZ
0x4102a4 ??9std@@YA_NABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@PBD@Z
0x4102a8 ?empty@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBE_NXZ
0x4102ac ??A?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAADI@Z
0x4102b0 ?find@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEIABV12@I@Z
0x4102b4 ??0?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@ABV01@@Z
0x4102b8 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@ABV10@0@Z
0x4102bc ??0?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@PBGABV?$allocator@G@1@@Z
0x4102c0 ??1?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@XZ
0x4102c4 ?c_str@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEPBGXZ
0x4102c8 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@ABV10@PBG@Z
0x4102cc ?end@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEPAGXZ
0x4102d0 ?begin@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEPAGXZ
0x4102d4 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@ABV10@G@Z
0x4102d8 ??4?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@PBD@Z
0x4102dc ??_D?$basic_ifstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x4102e0 ?close@?$basic_ifstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x4102e4 ?read@?$basic_istream@DU?$char_traits@D@std@@@std@@QAEAAV12@PADH@Z
0x4102e8 ?seekg@?$basic_istream@DU?$char_traits@D@std@@@std@@QAEAAV12@JW4seekdir@ios_base@2@@Z
0x4102ec ?tellg@?$basic_istream@DU?$char_traits@D@std@@@std@@QAE?AV?$fpos@H@2@XZ
0x4102f0 ?is_open@?$basic_ifstream@DU?$char_traits@D@std@@@std@@QBE_NXZ
0x4102f4 ??0?$basic_ifstream@DU?$char_traits@D@std@@@std@@QAE@PBDH@Z
0x4102f8 ??_D?$basic_ofstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x4102fc ?close@?$basic_ofstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x410300 ??6std@@YAAAV?$basic_ostream@DU?$char_traits@D@std@@@0@AAV10@ABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@@Z
MSVCRT.dll
0x410308 _wrename
0x41030c _controlfp
0x410310 __set_app_type
0x410314 __p__fmode
0x410318 __p__commode
0x41031c _adjust_fdiv
0x410320 __setusermatherr
0x410324 _initterm
0x410328 __getmainargs
0x41032c _acmdln
0x410330 _XcptFilter
0x410334 _exit
0x410338 _onexit
0x41033c __dllonexit
0x410340 ??1type_info@@UAE@XZ
0x410344 _iob
0x410348 freopen
0x41034c srand
0x410350 rand
0x410354 mbstowcs
0x410358 realloc
0x41035c _itoa
0x410360 sprintf
0x410364 getenv
0x410368 toupper
0x41036c tolower
0x410370 wcscmp
0x410374 printf
0x410378 strncmp
0x41037c malloc
0x410380 free
0x410384 _EH_prolog
0x410388 __CxxFrameHandler
0x41038c time
0x410390 localtime
0x410394 strftime
0x410398 puts
0x41039c atoi
0x4103a0 _ftol
0x4103a4 ??2@YAPAXI@Z
0x4103a8 _except_handler3
0x4103ac exit
0x4103b0 ??0exception@@QAE@ABV0@@Z
0x4103b4 _CxxThrowException
WINMM.dll
0x410480 waveInOpen
0x410484 waveInStop
0x410488 waveInClose
0x41048c waveInAddBuffer
0x410490 waveInPrepareHeader
0x410494 waveInUnprepareHeader
0x410498 waveInStart
SHLWAPI.dll
0x4103d4 PathFileExistsA
WS2_32.dll
0x4104a0 htons
0x4104a4 gethostbyname
0x4104a8 closesocket
0x4104ac socket
0x4104b0 send
0x4104b4 WSAGetLastError
0x4104b8 connect
0x4104bc recv
0x4104c0 WSAStartup
urlmon.dll
0x4104f8 URLDownloadToFileA
gdiplus.dll
0x4104c8 GdipLoadImageFromStreamICM
0x4104cc GdipDisposeImage
0x4104d0 GdipCloneImage
0x4104d4 GdipAlloc
0x4104d8 GdipSaveImageToStream
0x4104dc GdipSaveImageToFile
0x4104e0 GdipLoadImageFromStream
0x4104e4 GdiplusStartup
0x4104e8 GdipGetImageEncoders
0x4104ec GdipFree
0x4104f0 GdipGetImageEncodersSize
WININET.dll
0x41046c InternetCloseHandle
0x410470 InternetOpenUrlA
0x410474 InternetOpenA
0x410478 InternetReadFile
EAT(Export Address Table) is none
KERNEL32.dll
0x41006c GetModuleFileNameA
0x410070 GetLongPathNameA
0x410074 CreateMutexA
0x410078 OpenMutexA
0x41007c Process32Next
0x410080 Process32First
0x410084 CreateToolhelp32Snapshot
0x410088 SizeofResource
0x41008c LockResource
0x410090 LoadResource
0x410094 FindResourceA
0x410098 GetLocaleInfoA
0x41009c Process32NextW
0x4100a0 Process32FirstW
0x4100a4 lstrlenA
0x4100a8 GetDriveTypeA
0x4100ac CreateProcessA
0x4100b0 GetTickCount
0x4100b4 GlobalUnlock
0x4100b8 GlobalLock
0x4100bc GlobalAlloc
0x4100c0 WinExec
0x4100c4 GetCurrentProcessId
0x4100c8 CreateDirectoryW
0x4100cc CopyFileA
0x4100d0 GetFileAttributesW
0x4100d4 GetLogicalDriveStringsA
0x4100d8 GetCurrentProcess
0x4100dc ResumeThread
0x4100e0 SetThreadContext
0x4100e4 WriteProcessMemory
0x4100e8 VirtualAllocEx
0x4100ec ReadProcessMemory
0x4100f0 GetThreadContext
0x4100f4 VirtualAlloc
0x4100f8 GlobalFree
0x4100fc LocalAlloc
0x410100 TerminateProcess
0x410104 ReadFile
0x410108 PeekNamedPipe
0x41010c GetStdHandle
0x410110 CreatePipe
0x410114 OpenProcess
0x410118 DuplicateHandle
0x41011c GetCurrentThread
0x410120 lstrcpynA
0x410124 ExitProcess
0x410128 AllocConsole
0x41012c GetStartupInfoA
0x410130 ExpandEnvironmentStringsA
0x410134 FindFirstFileA
0x410138 FindNextFileA
0x41013c GetLastError
0x410140 LoadLibraryA
0x410144 GetProcAddress
0x410148 CreateFileMappingA
0x41014c MapViewOfFileEx
0x410150 DeleteFileA
0x410154 RemoveDirectoryA
0x410158 CloseHandle
0x41015c GetFileAttributesA
0x410160 SetFileAttributesA
0x410164 SetEvent
0x410168 TerminateThread
0x41016c FindFirstFileW
0x410170 FindNextFileW
0x410174 FindClose
0x410178 GetLocalTime
0x41017c CreateEventA
0x410180 WaitForSingleObject
0x410184 CreateDirectoryA
0x410188 ExitThread
0x41018c Sleep
0x410190 GetModuleHandleA
0x410194 DeleteFileW
0x410198 CreateThread
USER32.dll
0x4103dc GetWindowTextLengthA
0x4103e0 GetForegroundWindow
0x4103e4 UnhookWindowsHookEx
0x4103e8 CloseClipboard
0x4103ec GetClipboardData
0x4103f0 OpenClipboard
0x4103f4 SetClipboardData
0x4103f8 EmptyClipboard
0x4103fc ExitWindowsEx
0x410400 MessageBoxA
0x410404 GetKeyboardLayoutNameA
0x410408 GetWindowThreadProcessId
0x41040c ShowWindow
0x410410 CloseWindow
0x410414 GetWindowTextA
0x410418 GetWindowTextW
0x41041c EnumWindows
0x410420 SendInput
0x410424 CreateWindowExA
0x410428 RegisterClassExA
0x41042c AppendMenuA
0x410430 CreatePopupMenu
0x410434 TrackPopupMenu
0x410438 SetForegroundWindow
0x41043c GetCursorPos
0x410440 DefWindowProcA
0x410444 GetKeyState
0x410448 CallNextHookEx
0x41044c SetWindowsHookExA
0x410450 GetMessageA
0x410454 TranslateMessage
0x410458 GetKeyboardLayout
0x41045c FindWindowA
0x410460 DispatchMessageA
0x410464 IsWindowVisible
GDI32.dll
0x410040 CreateDCA
0x410044 CreateCompatibleDC
0x410048 GetDeviceCaps
0x41004c CreateCompatibleBitmap
0x410050 SelectObject
0x410054 StretchBlt
0x410058 GetObjectA
0x41005c GetDIBits
0x410060 DeleteObject
0x410064 DeleteDC
ADVAPI32.dll
0x410000 OpenProcessToken
0x410004 LookupPrivilegeValueA
0x410008 AdjustTokenPrivileges
0x41000c RegCreateKeyExA
0x410010 RegQueryInfoKeyA
0x410014 RegEnumKeyExA
0x410018 RegEnumValueA
0x41001c RegDeleteValueA
0x410020 RegCreateKeyA
0x410024 RegSetValueExA
0x410028 RegOpenKeyExA
0x41002c RegDeleteKeyA
0x410030 RegCloseKey
0x410034 RegQueryValueExA
0x410038 GetUserNameW
SHELL32.dll
0x4103bc ShellExecuteA
0x4103c0 ExtractIconA
0x4103c4 Shell_NotifyIconA
0x4103c8 ShellExecuteExA
0x4103cc ShellExecuteW
MSVCP60.dll
0x4101a0 ?begin@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEPADXZ
0x4101a4 ?end@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEPADXZ
0x4101a8 ?assign@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV12@ABV12@@Z
0x4101ac ?replace@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV12@IIPBD@Z
0x4101b0 ??8std@@YA_NPBDABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@@Z
0x4101b4 ??Y?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@PBD@Z
0x4101b8 ??4?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEAAV01@ABV01@@Z
0x4101bc ??0?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@ABV?$allocator@G@1@@Z
0x4101c0 ?find_last_of@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIDI@Z
0x4101c4 ??9std@@YA_NABV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@PBG@Z
0x4101c8 ??Y?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEAAV01@G@Z
0x4101cc ?substr@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBE?AV12@II@Z
0x4101d0 ?rfind@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEIGI@Z
0x4101d4 ?npos@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@2IB
0x4101d8 ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIPBDII@Z
0x4101dc ??0Init@ios_base@std@@QAE@XZ
0x4101e0 ??1Init@ios_base@std@@QAE@XZ
0x4101e4 ??0_Winit@std@@QAE@XZ
0x4101e8 ??1_Winit@std@@QAE@XZ
0x4101ec ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIABV12@I@Z
0x4101f0 ?find_last_of@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIPBDI@Z
0x4101f4 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@PBGABV10@@Z
0x4101f8 ??Y?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@D@Z
0x4101fc ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@DABV10@@Z
0x410200 ?rfind@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIDI@Z
0x410204 ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIDI@Z
0x410208 ?begin@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEPBGXZ
0x41020c ?end@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEPBGXZ
0x410210 ?length@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEIXZ
0x410214 ??Bios_base@std@@QBEPAXXZ
0x410218 ?assign@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV12@PBDI@Z
0x41021c ??6std@@YAAAV?$basic_ostream@DU?$char_traits@D@std@@@0@AAV10@PBD@Z
0x410220 ?find@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIPBDI@Z
0x410224 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@IDABV?$allocator@D@1@@Z
0x410228 ??8std@@YA_NABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@0@Z
0x41022c ??0?$basic_ofstream@DU?$char_traits@D@std@@@std@@QAE@PBDH@Z
0x410230 ?is_open@?$basic_ofstream@DU?$char_traits@D@std@@@std@@QBE_NXZ
0x410234 ?data@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEPBDXZ
0x410238 ??8std@@YA_NABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@PBD@Z
0x41023c ??0logic_error@std@@QAE@ABV01@@Z
0x410240 ??0out_of_range@std@@QAE@ABV01@@Z
0x410244 ??1out_of_range@std@@UAE@XZ
0x410248 ??0out_of_range@std@@QAE@ABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@1@@Z
0x41024c ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@PBDABV?$allocator@D@1@@Z
0x410250 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@ABV?$allocator@D@1@@Z
0x410254 ??1?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@XZ
0x410258 ?c_str@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEPBDXZ
0x41025c ?resize@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEXI@Z
0x410260 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@ABV01@@Z
0x410264 ??4?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@ABV01@@Z
0x410268 ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@ABV10@0@Z
0x41026c ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@PBDABV10@@Z
0x410270 ??0?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAE@PBDIABV?$allocator@D@1@@Z
0x410274 ??_D?$basic_fstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x410278 ?close@?$basic_fstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x41027c ?write@?$basic_ostream@DU?$char_traits@D@std@@@std@@QAEAAV12@PBDH@Z
0x410280 ?seekp@?$basic_ostream@DU?$char_traits@D@std@@@std@@QAEAAV12@JW4seekdir@ios_base@2@@Z
0x410284 ??0?$basic_fstream@DU?$char_traits@D@std@@@std@@QAE@PBDH@Z
0x410288 ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@ABV10@PBD@Z
0x41028c ??Hstd@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@ABV10@D@Z
0x410290 ?size@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIXZ
0x410294 ??Y?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@ABV01@@Z
0x410298 ?substr@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBE?AV12@II@Z
0x41029c ?npos@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@2IB
0x4102a0 ?length@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBEIXZ
0x4102a4 ??9std@@YA_NABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@PBD@Z
0x4102a8 ?empty@?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QBE_NXZ
0x4102ac ??A?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAADI@Z
0x4102b0 ?find@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEIABV12@I@Z
0x4102b4 ??0?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@ABV01@@Z
0x4102b8 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@ABV10@0@Z
0x4102bc ??0?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@PBGABV?$allocator@G@1@@Z
0x4102c0 ??1?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAE@XZ
0x4102c4 ?c_str@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QBEPBGXZ
0x4102c8 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@ABV10@PBG@Z
0x4102cc ?end@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEPAGXZ
0x4102d0 ?begin@?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@std@@QAEPAGXZ
0x4102d4 ??Hstd@@YA?AV?$basic_string@GU?$char_traits@G@std@@V?$allocator@G@2@@0@ABV10@G@Z
0x4102d8 ??4?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@QAEAAV01@PBD@Z
0x4102dc ??_D?$basic_ifstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x4102e0 ?close@?$basic_ifstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x4102e4 ?read@?$basic_istream@DU?$char_traits@D@std@@@std@@QAEAAV12@PADH@Z
0x4102e8 ?seekg@?$basic_istream@DU?$char_traits@D@std@@@std@@QAEAAV12@JW4seekdir@ios_base@2@@Z
0x4102ec ?tellg@?$basic_istream@DU?$char_traits@D@std@@@std@@QAE?AV?$fpos@H@2@XZ
0x4102f0 ?is_open@?$basic_ifstream@DU?$char_traits@D@std@@@std@@QBE_NXZ
0x4102f4 ??0?$basic_ifstream@DU?$char_traits@D@std@@@std@@QAE@PBDH@Z
0x4102f8 ??_D?$basic_ofstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x4102fc ?close@?$basic_ofstream@DU?$char_traits@D@std@@@std@@QAEXXZ
0x410300 ??6std@@YAAAV?$basic_ostream@DU?$char_traits@D@std@@@0@AAV10@ABV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@0@@Z
MSVCRT.dll
0x410308 _wrename
0x41030c _controlfp
0x410310 __set_app_type
0x410314 __p__fmode
0x410318 __p__commode
0x41031c _adjust_fdiv
0x410320 __setusermatherr
0x410324 _initterm
0x410328 __getmainargs
0x41032c _acmdln
0x410330 _XcptFilter
0x410334 _exit
0x410338 _onexit
0x41033c __dllonexit
0x410340 ??1type_info@@UAE@XZ
0x410344 _iob
0x410348 freopen
0x41034c srand
0x410350 rand
0x410354 mbstowcs
0x410358 realloc
0x41035c _itoa
0x410360 sprintf
0x410364 getenv
0x410368 toupper
0x41036c tolower
0x410370 wcscmp
0x410374 printf
0x410378 strncmp
0x41037c malloc
0x410380 free
0x410384 _EH_prolog
0x410388 __CxxFrameHandler
0x41038c time
0x410390 localtime
0x410394 strftime
0x410398 puts
0x41039c atoi
0x4103a0 _ftol
0x4103a4 ??2@YAPAXI@Z
0x4103a8 _except_handler3
0x4103ac exit
0x4103b0 ??0exception@@QAE@ABV0@@Z
0x4103b4 _CxxThrowException
WINMM.dll
0x410480 waveInOpen
0x410484 waveInStop
0x410488 waveInClose
0x41048c waveInAddBuffer
0x410490 waveInPrepareHeader
0x410494 waveInUnprepareHeader
0x410498 waveInStart
SHLWAPI.dll
0x4103d4 PathFileExistsA
WS2_32.dll
0x4104a0 htons
0x4104a4 gethostbyname
0x4104a8 closesocket
0x4104ac socket
0x4104b0 send
0x4104b4 WSAGetLastError
0x4104b8 connect
0x4104bc recv
0x4104c0 WSAStartup
urlmon.dll
0x4104f8 URLDownloadToFileA
gdiplus.dll
0x4104c8 GdipLoadImageFromStreamICM
0x4104cc GdipDisposeImage
0x4104d0 GdipCloneImage
0x4104d4 GdipAlloc
0x4104d8 GdipSaveImageToStream
0x4104dc GdipSaveImageToFile
0x4104e0 GdipLoadImageFromStream
0x4104e4 GdiplusStartup
0x4104e8 GdipGetImageEncoders
0x4104ec GdipFree
0x4104f0 GdipGetImageEncodersSize
WININET.dll
0x41046c InternetCloseHandle
0x410470 InternetOpenUrlA
0x410474 InternetOpenA
0x410478 InternetReadFile
EAT(Export Address Table) is none