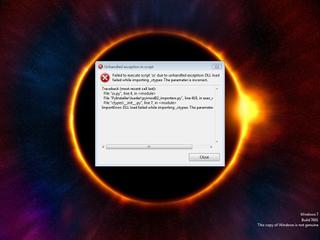
ScreenShot
| Created | 2025.02.07 11:36 | Machine | s1_win7_x6403 |
| Filename | svc.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 50 detected (Malicious, score, Zusy, Unsafe, confidence, 100%, GenusT, EIAH, Attribute, HighConfidence, high confidence, Nekark, OskiStealer, CLASSIC, ydehd, Static AI, Malicious PE, Detected, GrayWare, Wacapew, Wacatac, ABTrojan, XDPU, R690410, Artemis, R002H09B625, Gencirc, B9nj) | ||
| md5 | 4868a5a4c8e0ab56fa3be8469dd4bc75 | ||
| sha256 | b1e889002d9174c58dd9d8b20758516a3ff6e636ff14e00793da3ff9a09a7e9e | ||
| ssdeep | 24576:N8sLDE4McT5z35ba06PpeguG7XlYtidA+56Epa29C:VLDE4D5TVa0IV71YtF1 | ||
| imphash | 4b08efbed763524964334e9746c7ffd2 | ||
| impfuzzy | 96:lEju4nMr8csfStbgBlQHHZHhN7S9njLas6ussjQ7BLpU:Eu4nMJCBlgYtljEBLpU | ||
Network IP location
Signature (31cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 50 AntiVirus engines on VirusTotal as malicious |
| watch | Allocates execute permission to another process indicative of possible code injection |
| watch | Attempts to access Bitcoin/ALTCoin wallets |
| watch | Attempts to modify Explorer settings to prevent hidden files from being displayed |
| watch | Communicates with host for which no DNS query was performed |
| watch | Creates a thread using CreateRemoteThread in a non-child process indicative of process injection |
| watch | Drops a binary and executes it |
| watch | Executes one or more WMI queries |
| watch | Expresses interest in specific running processes |
| watch | Installs itself for autorun at Windows startup |
| watch | Manipulates memory of a non-child process indicative of process injection |
| watch | Network activity contains more than one unique useragent |
| watch | One or more of the buffers contains an embedded PE file |
| notice | A process attempted to delay the analysis task. |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | An executable file was downloaded by the processes svc.exe |
| notice | Creates executable files on the filesystem |
| notice | Creates hidden or system file |
| notice | Drops an executable to the user AppData folder |
| notice | Executes one or more WMI queries which can be used to identify virtual machines |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
| notice | Repeatedly searches for a not-found process |
| notice | Searches running processes potentially to identify processes for sandbox evasion |
| notice | Sends data using the HTTP POST Method |
| notice | Steals private information from local Internet browsers |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
| info | Queries for the computername |
Rules (21cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | infoStealer_browser_b_Zero | browser info stealer | binaries (upload) |
| danger | Win32_Trojan_Gen_1_0904B0_Zero | Win32 Trojan Emotet | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | ASPack_Zero | ASPack packed file | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Network_Downloader | File Downloader | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | JPEG_Format_Zero | JPEG Format | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | zip_file_format | ZIP file format | binaries (download) |
Network (9cnts) ?
Suricata ids
ET DROP Spamhaus DROP Listed Traffic Inbound group 31
ET INFO Executable Download from dotted-quad Host
ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET INFO Dotted Quad Host DLL Request
ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
ET INFO EXE CheckRemoteDebuggerPresent (Used in Malware Anti-Debugging)
ET HUNTING Suspicious Windows Executable WriteProcessMemory
ET INFO Executable Download from dotted-quad Host
ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET INFO Dotted Quad Host DLL Request
ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
ET INFO EXE CheckRemoteDebuggerPresent (Used in Malware Anti-Debugging)
ET HUNTING Suspicious Windows Executable WriteProcessMemory
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1400eb058 LoadLibraryA
0x1400eb060 SetCurrentDirectoryW
0x1400eb068 Process32First
0x1400eb070 GetComputerNameW
0x1400eb078 K32GetModuleFileNameExW
0x1400eb080 OpenProcess
0x1400eb088 GetVersionExW
0x1400eb090 GetModuleFileNameW
0x1400eb098 GetLocalTime
0x1400eb0a0 Process32Next
0x1400eb0a8 GlobalMemoryStatusEx
0x1400eb0b0 K32EnumProcesses
0x1400eb0b8 GetSystemInfo
0x1400eb0c0 CreateToolhelp32Snapshot
0x1400eb0c8 ExitProcess
0x1400eb0d0 TerminateThread
0x1400eb0d8 DeleteFileW
0x1400eb0e0 CreateThread
0x1400eb0e8 HeapAlloc
0x1400eb0f0 HeapFree
0x1400eb0f8 GetProcessHeap
0x1400eb100 FormatMessageA
0x1400eb108 SetLastError
0x1400eb110 OutputDebugStringA
0x1400eb118 LocalFree
0x1400eb120 HeapReAlloc
0x1400eb128 GetCurrentProcess
0x1400eb130 GetModuleHandleW
0x1400eb138 HeapDestroy
0x1400eb140 HeapCreate
0x1400eb148 GetCurrentThreadId
0x1400eb150 GetCurrentProcessId
0x1400eb158 GetFullPathNameW
0x1400eb160 GetFullPathNameA
0x1400eb168 CreateMutexW
0x1400eb170 HeapCompact
0x1400eb178 SetFilePointer
0x1400eb180 TryEnterCriticalSection
0x1400eb188 MapViewOfFile
0x1400eb190 UnmapViewOfFile
0x1400eb198 SetEndOfFile
0x1400eb1a0 SystemTimeToFileTime
0x1400eb1a8 QueryPerformanceCounter
0x1400eb1b0 WaitForSingleObject
0x1400eb1b8 UnlockFile
0x1400eb1c0 FlushViewOfFile
0x1400eb1c8 LockFile
0x1400eb1d0 WaitForSingleObjectEx
0x1400eb1d8 OutputDebugStringW
0x1400eb1e0 GetTickCount
0x1400eb1e8 UnlockFileEx
0x1400eb1f0 GetSystemTimeAsFileTime
0x1400eb1f8 InitializeCriticalSection
0x1400eb200 WideCharToMultiByte
0x1400eb208 LoadLibraryW
0x1400eb210 FormatMessageW
0x1400eb218 GetFileAttributesA
0x1400eb220 LeaveCriticalSection
0x1400eb228 HeapValidate
0x1400eb230 GetFileAttributesW
0x1400eb238 MultiByteToWideChar
0x1400eb240 GetProcAddress
0x1400eb248 GetTempPathW
0x1400eb250 HeapSize
0x1400eb258 LockFileEx
0x1400eb260 EnterCriticalSection
0x1400eb268 GetDiskFreeSpaceW
0x1400eb270 CreateFileMappingA
0x1400eb278 CreateFileMappingW
0x1400eb280 GetDiskFreeSpaceA
0x1400eb288 GetFileAttributesExW
0x1400eb290 DeleteCriticalSection
0x1400eb298 GetVersionExA
0x1400eb2a0 GetTempPathA
0x1400eb2a8 GetSystemTime
0x1400eb2b0 AreFileApisANSI
0x1400eb2b8 DeleteFileA
0x1400eb2c0 FindFirstFileW
0x1400eb2c8 CreateDirectoryW
0x1400eb2d0 CopyFileW
0x1400eb2d8 FindClose
0x1400eb2e0 FindNextFileW
0x1400eb2e8 GetWindowsDirectoryA
0x1400eb2f0 GetVolumeInformationA
0x1400eb2f8 TerminateProcess
0x1400eb300 CopyFileA
0x1400eb308 Process32FirstW
0x1400eb310 RemoveDirectoryW
0x1400eb318 Process32NextW
0x1400eb320 GetWindowsDirectoryW
0x1400eb328 GetVolumeInformationW
0x1400eb330 FindFirstFileA
0x1400eb338 FindNextFileA
0x1400eb340 WriteConsoleW
0x1400eb348 SetStdHandle
0x1400eb350 EnumSystemLocalesEx
0x1400eb358 IsValidLocaleName
0x1400eb360 LCMapStringEx
0x1400eb368 GetUserDefaultLocaleName
0x1400eb370 CompareStringEx
0x1400eb378 lstrcatA
0x1400eb380 FreeLibrary
0x1400eb388 lstrcpyA
0x1400eb390 GetCurrentDirectoryW
0x1400eb398 Sleep
0x1400eb3a0 lstrlenA
0x1400eb3a8 FreeEnvironmentStringsW
0x1400eb3b0 GetEnvironmentStringsW
0x1400eb3b8 GetTickCount64
0x1400eb3c0 ReadConsoleW
0x1400eb3c8 FlsFree
0x1400eb3d0 FlsSetValue
0x1400eb3d8 FlsGetValue
0x1400eb3e0 FlsAlloc
0x1400eb3e8 SetUnhandledExceptionFilter
0x1400eb3f0 UnhandledExceptionFilter
0x1400eb3f8 RtlVirtualUnwind
0x1400eb400 RtlCaptureContext
0x1400eb408 GetTimeZoneInformation
0x1400eb410 GetOEMCP
0x1400eb418 GetACP
0x1400eb420 IsValidCodePage
0x1400eb428 GetConsoleMode
0x1400eb430 GetConsoleCP
0x1400eb438 SetFilePointerEx
0x1400eb440 GetStartupInfoW
0x1400eb448 InitOnceExecuteOnce
0x1400eb450 GetFileType
0x1400eb458 GetStdHandle
0x1400eb460 GetModuleHandleExW
0x1400eb468 IsDebuggerPresent
0x1400eb470 IsProcessorFeaturePresent
0x1400eb478 InitializeCriticalSectionAndSpinCount
0x1400eb480 RtlUnwindEx
0x1400eb488 RtlLookupFunctionEntry
0x1400eb490 lstrcmpA
0x1400eb498 CloseHandle
0x1400eb4a0 GetLastError
0x1400eb4a8 CreateFileW
0x1400eb4b0 ReadFile
0x1400eb4b8 WriteFile
0x1400eb4c0 GetFileSize
0x1400eb4c8 FlushFileBuffers
0x1400eb4d0 CreateFileA
0x1400eb4d8 RaiseException
0x1400eb4e0 RtlPcToFileHeader
0x1400eb4e8 GetCommandLineW
0x1400eb4f0 LoadLibraryExW
0x1400eb4f8 ExitThread
0x1400eb500 GetCPInfo
0x1400eb508 GetLocaleInfoEx
0x1400eb510 InitializeCriticalSectionEx
0x1400eb518 DecodePointer
0x1400eb520 EncodePointer
0x1400eb528 GetStringTypeW
0x1400eb530 SetEnvironmentVariableA
USER32.dll
0x1400eb5a8 wsprintfW
0x1400eb5b0 GetDC
0x1400eb5b8 GetWindow
0x1400eb5c0 GetWindowTextW
0x1400eb5c8 GetSystemMetrics
0x1400eb5d0 GetWindowThreadProcessId
0x1400eb5d8 GetTopWindow
0x1400eb5e0 wsprintfA
ADVAPI32.dll
0x1400eb000 GetUserNameW
SHLWAPI.dll
0x1400eb588 PathStripPathA
0x1400eb590 PathFindExtensionW
0x1400eb598 StrCmpIW
SHELL32.dll
0x1400eb560 SHGetKnownFolderPath
0x1400eb568 ShellExecuteW
0x1400eb570 SHGetFolderPathW
0x1400eb578 SHGetFolderPathA
ole32.dll
0x1400eb690 CoUninitialize
0x1400eb698 CoInitializeSecurity
0x1400eb6a0 CoInitializeEx
0x1400eb6a8 CoSetProxyBlanket
0x1400eb6b0 CoCreateInstance
OLEAUT32.dll
0x1400eb540 SysAllocString
0x1400eb548 VariantClear
0x1400eb550 SysFreeString
crypt.dll
0x1400eb5f0 BCryptOpenAlgorithmProvider
0x1400eb5f8 BCryptSetProperty
0x1400eb600 BCryptDecrypt
0x1400eb608 BCryptCloseAlgorithmProvider
0x1400eb610 BCryptGenerateSymmetricKey
CRYPT32.dll
0x1400eb010 CryptUnprotectData
0x1400eb018 CryptStringToBinaryA
GDI32.dll
0x1400eb028 CreateCompatibleDC
0x1400eb030 SelectObject
0x1400eb038 DeleteObject
0x1400eb040 CreateCompatibleBitmap
0x1400eb048 BitBlt
gdiplus.dll
0x1400eb620 GdipSaveImageToFile
0x1400eb628 GdipGetImageEncoders
0x1400eb630 GdipCloneImage
0x1400eb638 GdipDisposeImage
0x1400eb640 GdipGetImageEncodersSize
0x1400eb648 GdiplusStartup
0x1400eb650 GdipFree
0x1400eb658 GdipAlloc
0x1400eb660 GdipCreateBitmapFromHBITMAP
0x1400eb668 GdiplusShutdown
msi.dll
0x1400eb678 None
0x1400eb680 None
EAT(Export Address Table) is none
KERNEL32.dll
0x1400eb058 LoadLibraryA
0x1400eb060 SetCurrentDirectoryW
0x1400eb068 Process32First
0x1400eb070 GetComputerNameW
0x1400eb078 K32GetModuleFileNameExW
0x1400eb080 OpenProcess
0x1400eb088 GetVersionExW
0x1400eb090 GetModuleFileNameW
0x1400eb098 GetLocalTime
0x1400eb0a0 Process32Next
0x1400eb0a8 GlobalMemoryStatusEx
0x1400eb0b0 K32EnumProcesses
0x1400eb0b8 GetSystemInfo
0x1400eb0c0 CreateToolhelp32Snapshot
0x1400eb0c8 ExitProcess
0x1400eb0d0 TerminateThread
0x1400eb0d8 DeleteFileW
0x1400eb0e0 CreateThread
0x1400eb0e8 HeapAlloc
0x1400eb0f0 HeapFree
0x1400eb0f8 GetProcessHeap
0x1400eb100 FormatMessageA
0x1400eb108 SetLastError
0x1400eb110 OutputDebugStringA
0x1400eb118 LocalFree
0x1400eb120 HeapReAlloc
0x1400eb128 GetCurrentProcess
0x1400eb130 GetModuleHandleW
0x1400eb138 HeapDestroy
0x1400eb140 HeapCreate
0x1400eb148 GetCurrentThreadId
0x1400eb150 GetCurrentProcessId
0x1400eb158 GetFullPathNameW
0x1400eb160 GetFullPathNameA
0x1400eb168 CreateMutexW
0x1400eb170 HeapCompact
0x1400eb178 SetFilePointer
0x1400eb180 TryEnterCriticalSection
0x1400eb188 MapViewOfFile
0x1400eb190 UnmapViewOfFile
0x1400eb198 SetEndOfFile
0x1400eb1a0 SystemTimeToFileTime
0x1400eb1a8 QueryPerformanceCounter
0x1400eb1b0 WaitForSingleObject
0x1400eb1b8 UnlockFile
0x1400eb1c0 FlushViewOfFile
0x1400eb1c8 LockFile
0x1400eb1d0 WaitForSingleObjectEx
0x1400eb1d8 OutputDebugStringW
0x1400eb1e0 GetTickCount
0x1400eb1e8 UnlockFileEx
0x1400eb1f0 GetSystemTimeAsFileTime
0x1400eb1f8 InitializeCriticalSection
0x1400eb200 WideCharToMultiByte
0x1400eb208 LoadLibraryW
0x1400eb210 FormatMessageW
0x1400eb218 GetFileAttributesA
0x1400eb220 LeaveCriticalSection
0x1400eb228 HeapValidate
0x1400eb230 GetFileAttributesW
0x1400eb238 MultiByteToWideChar
0x1400eb240 GetProcAddress
0x1400eb248 GetTempPathW
0x1400eb250 HeapSize
0x1400eb258 LockFileEx
0x1400eb260 EnterCriticalSection
0x1400eb268 GetDiskFreeSpaceW
0x1400eb270 CreateFileMappingA
0x1400eb278 CreateFileMappingW
0x1400eb280 GetDiskFreeSpaceA
0x1400eb288 GetFileAttributesExW
0x1400eb290 DeleteCriticalSection
0x1400eb298 GetVersionExA
0x1400eb2a0 GetTempPathA
0x1400eb2a8 GetSystemTime
0x1400eb2b0 AreFileApisANSI
0x1400eb2b8 DeleteFileA
0x1400eb2c0 FindFirstFileW
0x1400eb2c8 CreateDirectoryW
0x1400eb2d0 CopyFileW
0x1400eb2d8 FindClose
0x1400eb2e0 FindNextFileW
0x1400eb2e8 GetWindowsDirectoryA
0x1400eb2f0 GetVolumeInformationA
0x1400eb2f8 TerminateProcess
0x1400eb300 CopyFileA
0x1400eb308 Process32FirstW
0x1400eb310 RemoveDirectoryW
0x1400eb318 Process32NextW
0x1400eb320 GetWindowsDirectoryW
0x1400eb328 GetVolumeInformationW
0x1400eb330 FindFirstFileA
0x1400eb338 FindNextFileA
0x1400eb340 WriteConsoleW
0x1400eb348 SetStdHandle
0x1400eb350 EnumSystemLocalesEx
0x1400eb358 IsValidLocaleName
0x1400eb360 LCMapStringEx
0x1400eb368 GetUserDefaultLocaleName
0x1400eb370 CompareStringEx
0x1400eb378 lstrcatA
0x1400eb380 FreeLibrary
0x1400eb388 lstrcpyA
0x1400eb390 GetCurrentDirectoryW
0x1400eb398 Sleep
0x1400eb3a0 lstrlenA
0x1400eb3a8 FreeEnvironmentStringsW
0x1400eb3b0 GetEnvironmentStringsW
0x1400eb3b8 GetTickCount64
0x1400eb3c0 ReadConsoleW
0x1400eb3c8 FlsFree
0x1400eb3d0 FlsSetValue
0x1400eb3d8 FlsGetValue
0x1400eb3e0 FlsAlloc
0x1400eb3e8 SetUnhandledExceptionFilter
0x1400eb3f0 UnhandledExceptionFilter
0x1400eb3f8 RtlVirtualUnwind
0x1400eb400 RtlCaptureContext
0x1400eb408 GetTimeZoneInformation
0x1400eb410 GetOEMCP
0x1400eb418 GetACP
0x1400eb420 IsValidCodePage
0x1400eb428 GetConsoleMode
0x1400eb430 GetConsoleCP
0x1400eb438 SetFilePointerEx
0x1400eb440 GetStartupInfoW
0x1400eb448 InitOnceExecuteOnce
0x1400eb450 GetFileType
0x1400eb458 GetStdHandle
0x1400eb460 GetModuleHandleExW
0x1400eb468 IsDebuggerPresent
0x1400eb470 IsProcessorFeaturePresent
0x1400eb478 InitializeCriticalSectionAndSpinCount
0x1400eb480 RtlUnwindEx
0x1400eb488 RtlLookupFunctionEntry
0x1400eb490 lstrcmpA
0x1400eb498 CloseHandle
0x1400eb4a0 GetLastError
0x1400eb4a8 CreateFileW
0x1400eb4b0 ReadFile
0x1400eb4b8 WriteFile
0x1400eb4c0 GetFileSize
0x1400eb4c8 FlushFileBuffers
0x1400eb4d0 CreateFileA
0x1400eb4d8 RaiseException
0x1400eb4e0 RtlPcToFileHeader
0x1400eb4e8 GetCommandLineW
0x1400eb4f0 LoadLibraryExW
0x1400eb4f8 ExitThread
0x1400eb500 GetCPInfo
0x1400eb508 GetLocaleInfoEx
0x1400eb510 InitializeCriticalSectionEx
0x1400eb518 DecodePointer
0x1400eb520 EncodePointer
0x1400eb528 GetStringTypeW
0x1400eb530 SetEnvironmentVariableA
USER32.dll
0x1400eb5a8 wsprintfW
0x1400eb5b0 GetDC
0x1400eb5b8 GetWindow
0x1400eb5c0 GetWindowTextW
0x1400eb5c8 GetSystemMetrics
0x1400eb5d0 GetWindowThreadProcessId
0x1400eb5d8 GetTopWindow
0x1400eb5e0 wsprintfA
ADVAPI32.dll
0x1400eb000 GetUserNameW
SHLWAPI.dll
0x1400eb588 PathStripPathA
0x1400eb590 PathFindExtensionW
0x1400eb598 StrCmpIW
SHELL32.dll
0x1400eb560 SHGetKnownFolderPath
0x1400eb568 ShellExecuteW
0x1400eb570 SHGetFolderPathW
0x1400eb578 SHGetFolderPathA
ole32.dll
0x1400eb690 CoUninitialize
0x1400eb698 CoInitializeSecurity
0x1400eb6a0 CoInitializeEx
0x1400eb6a8 CoSetProxyBlanket
0x1400eb6b0 CoCreateInstance
OLEAUT32.dll
0x1400eb540 SysAllocString
0x1400eb548 VariantClear
0x1400eb550 SysFreeString
crypt.dll
0x1400eb5f0 BCryptOpenAlgorithmProvider
0x1400eb5f8 BCryptSetProperty
0x1400eb600 BCryptDecrypt
0x1400eb608 BCryptCloseAlgorithmProvider
0x1400eb610 BCryptGenerateSymmetricKey
CRYPT32.dll
0x1400eb010 CryptUnprotectData
0x1400eb018 CryptStringToBinaryA
GDI32.dll
0x1400eb028 CreateCompatibleDC
0x1400eb030 SelectObject
0x1400eb038 DeleteObject
0x1400eb040 CreateCompatibleBitmap
0x1400eb048 BitBlt
gdiplus.dll
0x1400eb620 GdipSaveImageToFile
0x1400eb628 GdipGetImageEncoders
0x1400eb630 GdipCloneImage
0x1400eb638 GdipDisposeImage
0x1400eb640 GdipGetImageEncodersSize
0x1400eb648 GdiplusStartup
0x1400eb650 GdipFree
0x1400eb658 GdipAlloc
0x1400eb660 GdipCreateBitmapFromHBITMAP
0x1400eb668 GdiplusShutdown
msi.dll
0x1400eb678 None
0x1400eb680 None
EAT(Export Address Table) is none