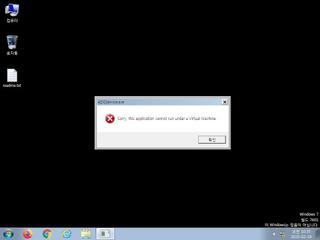
ScreenShot
| Created | 2025.02.19 10:52 | Machine | s1_win7_x6401 |
| Filename | ADGService.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | |||
| VT API (file) | |||
| md5 | d760d6d65e21de73fedc69a38c5dc0d4 | ||
| sha256 | 015af7c563b2df9ae027b7cd2572222a7af5e8ad305d6c4cebf1e39c7bf579a0 | ||
| ssdeep | 196608:5d2cpswULFj2+DEF6o7pAe8xBmukHmalxo7hNSgaHW7EDr2bi/NRa:WcIfu6kOBinWhNSga | ||
| imphash | 7f830c1be2775636f0aaf6ee74829bf2 | ||
| impfuzzy | 96:FzJG2RqybQfNcVC1AXJ4Zcp+AjxtvuGzvVq:S2cOZ4pgc | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
msvcrt.dll
0x14075f000 __C_specific_handler
0x14075f008 __getmainargs
0x14075f010 __initenv
0x14075f018 __iob_func
0x14075f020 __set_app_type
0x14075f028 __setusermatherr
0x14075f030 _amsg_exit
0x14075f038 _cexit
0x14075f040 _commode
0x14075f048 _fmode
0x14075f050 _initterm
0x14075f058 _onexit
0x14075f060 _time64
0x14075f068 _wcsicmp
0x14075f070 _wcsnicmp
0x14075f078 abort
0x14075f080 calloc
0x14075f088 exit
0x14075f090 fprintf
0x14075f098 free
0x14075f0a0 fwrite
0x14075f0a8 malloc
0x14075f0b0 memcpy
0x14075f0b8 memset
0x14075f0c0 rand
0x14075f0c8 signal
0x14075f0d0 srand
0x14075f0d8 strcat
0x14075f0e0 strcpy
0x14075f0e8 strlen
0x14075f0f0 strncmp
0x14075f0f8 strstr
0x14075f100 vfprintf
0x14075f108 wcscat
0x14075f110 wcscpy
0x14075f118 wcslen
0x14075f120 wcsncmp
0x14075f128 wcsstr
KERNEL32.dll
0x14075f138 DeleteCriticalSection
0x14075f140 EnterCriticalSection
0x14075f148 GetLastError
0x14075f150 InitializeCriticalSection
0x14075f158 LeaveCriticalSection
0x14075f160 SetUnhandledExceptionFilter
0x14075f168 Sleep
0x14075f170 TlsGetValue
0x14075f178 VirtualProtect
0x14075f180 VirtualQuery
KERNEL32.dll
0x14075f190 GetSystemTimeAsFileTime
0x14075f198 CreateEventA
0x14075f1a0 GetModuleHandleA
0x14075f1a8 TerminateProcess
0x14075f1b0 GetCurrentProcess
0x14075f1b8 CreateToolhelp32Snapshot
0x14075f1c0 Thread32First
0x14075f1c8 GetCurrentProcessId
0x14075f1d0 GetCurrentThreadId
0x14075f1d8 OpenThread
0x14075f1e0 Thread32Next
0x14075f1e8 CloseHandle
0x14075f1f0 SuspendThread
0x14075f1f8 ResumeThread
0x14075f200 WriteProcessMemory
0x14075f208 GetSystemInfo
0x14075f210 VirtualAlloc
0x14075f218 VirtualProtect
0x14075f220 VirtualFree
0x14075f228 GetProcessAffinityMask
0x14075f230 SetProcessAffinityMask
0x14075f238 GetCurrentThread
0x14075f240 SetThreadAffinityMask
0x14075f248 Sleep
0x14075f250 LoadLibraryA
0x14075f258 FreeLibrary
0x14075f260 GetTickCount
0x14075f268 SystemTimeToFileTime
0x14075f270 FileTimeToSystemTime
0x14075f278 GlobalFree
0x14075f280 HeapAlloc
0x14075f288 HeapFree
0x14075f290 GetProcAddress
0x14075f298 ExitProcess
0x14075f2a0 EnterCriticalSection
0x14075f2a8 LeaveCriticalSection
0x14075f2b0 InitializeCriticalSection
0x14075f2b8 DeleteCriticalSection
0x14075f2c0 MultiByteToWideChar
0x14075f2c8 GetModuleHandleW
0x14075f2d0 LoadResource
0x14075f2d8 FindResourceExW
0x14075f2e0 FindResourceExA
0x14075f2e8 WideCharToMultiByte
0x14075f2f0 GetThreadLocale
0x14075f2f8 GetUserDefaultLCID
0x14075f300 GetSystemDefaultLCID
0x14075f308 EnumResourceNamesA
0x14075f310 EnumResourceNamesW
0x14075f318 EnumResourceLanguagesA
0x14075f320 EnumResourceLanguagesW
0x14075f328 EnumResourceTypesA
0x14075f330 EnumResourceTypesW
0x14075f338 CreateFileW
0x14075f340 LoadLibraryW
0x14075f348 GetLastError
0x14075f350 FlushFileBuffers
0x14075f358 FlsSetValue
0x14075f360 GetCommandLineA
0x14075f368 GetCPInfo
0x14075f370 GetACP
0x14075f378 GetOEMCP
0x14075f380 IsValidCodePage
0x14075f388 EncodePointer
0x14075f390 DecodePointer
0x14075f398 FlsGetValue
0x14075f3a0 FlsFree
0x14075f3a8 SetLastError
0x14075f3b0 FlsAlloc
0x14075f3b8 UnhandledExceptionFilter
0x14075f3c0 SetUnhandledExceptionFilter
0x14075f3c8 IsDebuggerPresent
0x14075f3d0 RtlVirtualUnwind
0x14075f3d8 RtlLookupFunctionEntry
0x14075f3e0 RtlCaptureContext
0x14075f3e8 RaiseException
0x14075f3f0 RtlPcToFileHeader
0x14075f3f8 RtlUnwindEx
0x14075f400 LCMapStringA
0x14075f408 LCMapStringW
0x14075f410 SetHandleCount
0x14075f418 GetStdHandle
0x14075f420 GetFileType
0x14075f428 GetStartupInfoA
0x14075f430 GetModuleFileNameA
0x14075f438 FreeEnvironmentStringsA
0x14075f440 GetEnvironmentStrings
0x14075f448 FreeEnvironmentStringsW
0x14075f450 GetEnvironmentStringsW
0x14075f458 HeapSetInformation
0x14075f460 HeapCreate
0x14075f468 HeapDestroy
0x14075f470 QueryPerformanceCounter
0x14075f478 GetStringTypeA
0x14075f480 GetStringTypeW
0x14075f488 GetLocaleInfoA
0x14075f490 HeapSize
0x14075f498 WriteFile
0x14075f4a0 SetFilePointer
0x14075f4a8 GetConsoleCP
0x14075f4b0 GetConsoleMode
0x14075f4b8 HeapReAlloc
0x14075f4c0 InitializeCriticalSectionAndSpinCount
0x14075f4c8 SetStdHandle
0x14075f4d0 WriteConsoleA
0x14075f4d8 GetConsoleOutputCP
0x14075f4e0 WriteConsoleW
0x14075f4e8 CreateFileA
EAT(Export Address Table) is none
msvcrt.dll
0x14075f000 __C_specific_handler
0x14075f008 __getmainargs
0x14075f010 __initenv
0x14075f018 __iob_func
0x14075f020 __set_app_type
0x14075f028 __setusermatherr
0x14075f030 _amsg_exit
0x14075f038 _cexit
0x14075f040 _commode
0x14075f048 _fmode
0x14075f050 _initterm
0x14075f058 _onexit
0x14075f060 _time64
0x14075f068 _wcsicmp
0x14075f070 _wcsnicmp
0x14075f078 abort
0x14075f080 calloc
0x14075f088 exit
0x14075f090 fprintf
0x14075f098 free
0x14075f0a0 fwrite
0x14075f0a8 malloc
0x14075f0b0 memcpy
0x14075f0b8 memset
0x14075f0c0 rand
0x14075f0c8 signal
0x14075f0d0 srand
0x14075f0d8 strcat
0x14075f0e0 strcpy
0x14075f0e8 strlen
0x14075f0f0 strncmp
0x14075f0f8 strstr
0x14075f100 vfprintf
0x14075f108 wcscat
0x14075f110 wcscpy
0x14075f118 wcslen
0x14075f120 wcsncmp
0x14075f128 wcsstr
KERNEL32.dll
0x14075f138 DeleteCriticalSection
0x14075f140 EnterCriticalSection
0x14075f148 GetLastError
0x14075f150 InitializeCriticalSection
0x14075f158 LeaveCriticalSection
0x14075f160 SetUnhandledExceptionFilter
0x14075f168 Sleep
0x14075f170 TlsGetValue
0x14075f178 VirtualProtect
0x14075f180 VirtualQuery
KERNEL32.dll
0x14075f190 GetSystemTimeAsFileTime
0x14075f198 CreateEventA
0x14075f1a0 GetModuleHandleA
0x14075f1a8 TerminateProcess
0x14075f1b0 GetCurrentProcess
0x14075f1b8 CreateToolhelp32Snapshot
0x14075f1c0 Thread32First
0x14075f1c8 GetCurrentProcessId
0x14075f1d0 GetCurrentThreadId
0x14075f1d8 OpenThread
0x14075f1e0 Thread32Next
0x14075f1e8 CloseHandle
0x14075f1f0 SuspendThread
0x14075f1f8 ResumeThread
0x14075f200 WriteProcessMemory
0x14075f208 GetSystemInfo
0x14075f210 VirtualAlloc
0x14075f218 VirtualProtect
0x14075f220 VirtualFree
0x14075f228 GetProcessAffinityMask
0x14075f230 SetProcessAffinityMask
0x14075f238 GetCurrentThread
0x14075f240 SetThreadAffinityMask
0x14075f248 Sleep
0x14075f250 LoadLibraryA
0x14075f258 FreeLibrary
0x14075f260 GetTickCount
0x14075f268 SystemTimeToFileTime
0x14075f270 FileTimeToSystemTime
0x14075f278 GlobalFree
0x14075f280 HeapAlloc
0x14075f288 HeapFree
0x14075f290 GetProcAddress
0x14075f298 ExitProcess
0x14075f2a0 EnterCriticalSection
0x14075f2a8 LeaveCriticalSection
0x14075f2b0 InitializeCriticalSection
0x14075f2b8 DeleteCriticalSection
0x14075f2c0 MultiByteToWideChar
0x14075f2c8 GetModuleHandleW
0x14075f2d0 LoadResource
0x14075f2d8 FindResourceExW
0x14075f2e0 FindResourceExA
0x14075f2e8 WideCharToMultiByte
0x14075f2f0 GetThreadLocale
0x14075f2f8 GetUserDefaultLCID
0x14075f300 GetSystemDefaultLCID
0x14075f308 EnumResourceNamesA
0x14075f310 EnumResourceNamesW
0x14075f318 EnumResourceLanguagesA
0x14075f320 EnumResourceLanguagesW
0x14075f328 EnumResourceTypesA
0x14075f330 EnumResourceTypesW
0x14075f338 CreateFileW
0x14075f340 LoadLibraryW
0x14075f348 GetLastError
0x14075f350 FlushFileBuffers
0x14075f358 FlsSetValue
0x14075f360 GetCommandLineA
0x14075f368 GetCPInfo
0x14075f370 GetACP
0x14075f378 GetOEMCP
0x14075f380 IsValidCodePage
0x14075f388 EncodePointer
0x14075f390 DecodePointer
0x14075f398 FlsGetValue
0x14075f3a0 FlsFree
0x14075f3a8 SetLastError
0x14075f3b0 FlsAlloc
0x14075f3b8 UnhandledExceptionFilter
0x14075f3c0 SetUnhandledExceptionFilter
0x14075f3c8 IsDebuggerPresent
0x14075f3d0 RtlVirtualUnwind
0x14075f3d8 RtlLookupFunctionEntry
0x14075f3e0 RtlCaptureContext
0x14075f3e8 RaiseException
0x14075f3f0 RtlPcToFileHeader
0x14075f3f8 RtlUnwindEx
0x14075f400 LCMapStringA
0x14075f408 LCMapStringW
0x14075f410 SetHandleCount
0x14075f418 GetStdHandle
0x14075f420 GetFileType
0x14075f428 GetStartupInfoA
0x14075f430 GetModuleFileNameA
0x14075f438 FreeEnvironmentStringsA
0x14075f440 GetEnvironmentStrings
0x14075f448 FreeEnvironmentStringsW
0x14075f450 GetEnvironmentStringsW
0x14075f458 HeapSetInformation
0x14075f460 HeapCreate
0x14075f468 HeapDestroy
0x14075f470 QueryPerformanceCounter
0x14075f478 GetStringTypeA
0x14075f480 GetStringTypeW
0x14075f488 GetLocaleInfoA
0x14075f490 HeapSize
0x14075f498 WriteFile
0x14075f4a0 SetFilePointer
0x14075f4a8 GetConsoleCP
0x14075f4b0 GetConsoleMode
0x14075f4b8 HeapReAlloc
0x14075f4c0 InitializeCriticalSectionAndSpinCount
0x14075f4c8 SetStdHandle
0x14075f4d0 WriteConsoleA
0x14075f4d8 GetConsoleOutputCP
0x14075f4e0 WriteConsoleW
0x14075f4e8 CreateFileA
EAT(Export Address Table) is none