ScreenShot
| Created | 2025.03.24 21:37 | Machine | s1_win7_x6401 |
| Filename | W-1553916722.xlsb | ||
| Type | Microsoft Excel 2007+ | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 12 detected (Save, ma35, Eldorado, MalMacro, gen3, multiple detections, CLASSIC, Qakbot, IQAY) | ||
| md5 | 82c18cbd86f03a752314840a80deeb80 | ||
| sha256 | 508e823895c2dbc8fc72b35fc1a888b81a0509ee4856566fa236a7ad70396bc3 | ||
| ssdeep | 24576:K9vBKAnpis3QXPH5sjl+opcMrAm9vBKAnpis3Q+9vBKAnpis3QSVLFUN:m5KA65VSrX5KAV5KAVNFK | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 12 AntiVirus engines on VirusTotal as malicious |
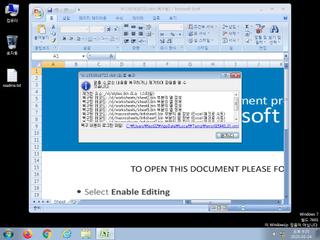
| watch | Network communications indicative of a potential document or script payload download was initiated by the process excel.exe |
| watch | One or more non-whitelisted processes were created |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates a suspicious process |
| notice | Creates executable files on the filesystem |
| notice | Creates hidden or system file |
| info | Checks amount of memory in system |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| info | xlsb | Excel Binary Workbook file format detection | binaries (upload) |
| info | zip_file_format | ZIP file format | binaries (upload) |
Network (5cnts) ?
Suricata ids
ET INFO TLS Handshake Failure
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)