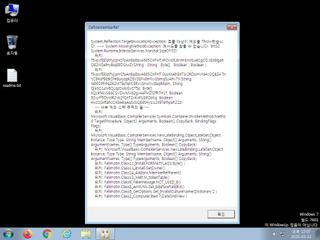
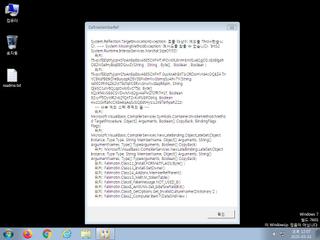
ScreenShot
| Created | 2025.03.31 12:25 | Machine | s1_win7_x6401 |
| Filename | nixsudo.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 47 detected (AIDetectMalware, Penguish, Ghanarava, Artemis, GenericKD, Unsafe, Vpjo, Attribute, HighConfidence, a variant of Generik, GXLYXZH, CLOUD, mvtdq, Inject5, GHOSTSOCKS, YXFC1Z, Detected, Wacatac, Leonem, ABTrojan, WXPX, MALICIOUS, TScope, Delf, Gencirc, susgen, Behavior) | ||
| md5 | 09f7e5af8af839111c760e5fead1363f | ||
| sha256 | 81e8ba37f175c8798101d49019f24188d0877185e68cbe8b2ad3ca1f0cb89eef | ||
| ssdeep | 196608:mzThHKR3CVPLc4F8d+qSicW9mHTPUULixyoWh2FMmq6nQJEx:mlKJADF8dCnToWhROQJEx | ||
| imphash | d73e412edccba7ffc3c299db8491f3eb | ||
| impfuzzy | 96:nkHBEKDL1N+IBNJeOcImTX1pDnji+XXogAoaENiLfHbaDOK4AzPvrn:2KGzUTFln+E4toaENY/baD54Ajvj | ||
Network IP location
Signature (18cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 47 AntiVirus engines on VirusTotal as malicious |
| watch | A process attempted to delay the analysis task. |
| watch | Attempts to remove evidence of file being downloaded from the Internet |
| watch | Communicates with host for which no DNS query was performed |
| watch | Detects the presence of Wine emulator |
| watch | Looks for the Windows Idle Time to determine the uptime |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Expresses interest in specific running processes |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
| info | Queries for the computername |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (11cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Gen_1_0904B0_Zero | Win32 Trojan Emotet | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | PNG_Format_Zero | PNG Format | binaries (download) |
PE API
IAT(Import Address Table) Library
kernel32.dll
0x8bb568 GetFileTime
0x8bb56c GetFileType
0x8bb570 SetFileTime
0x8bb574 QueryDosDeviceW
0x8bb578 GetACP
0x8bb57c GetExitCodeProcess
0x8bb580 GetStringTypeExW
0x8bb584 CloseHandle
0x8bb588 LocalFree
0x8bb58c GetCurrentProcessId
0x8bb590 SizeofResource
0x8bb594 VirtualProtect
0x8bb598 UnlockFile
0x8bb59c SetEnvironmentVariableW
0x8bb5a0 TerminateThread
0x8bb5a4 QueryPerformanceFrequency
0x8bb5a8 IsDebuggerPresent
0x8bb5ac FindNextFileW
0x8bb5b0 FlushInstructionCache
0x8bb5b4 GetFullPathNameW
0x8bb5b8 VirtualFree
0x8bb5bc GetProcessHeap
0x8bb5c0 ExitProcess
0x8bb5c4 HeapAlloc
0x8bb5c8 GetCPInfoExW
0x8bb5cc GetSystemTime
0x8bb5d0 GetLongPathNameW
0x8bb5d4 RtlUnwind
0x8bb5d8 GetCPInfo
0x8bb5dc EnumSystemLocalesW
0x8bb5e0 GetStdHandle
0x8bb5e4 GetTimeZoneInformation
0x8bb5e8 FileTimeToLocalFileTime
0x8bb5ec GetModuleHandleW
0x8bb5f0 FreeLibrary
0x8bb5f4 TryEnterCriticalSection
0x8bb5f8 HeapDestroy
0x8bb5fc FileTimeToDosDateTime
0x8bb600 ReadFile
0x8bb604 DosDateTimeToFileTime
0x8bb608 CreateProcessW
0x8bb60c GetLastError
0x8bb610 GetModuleFileNameW
0x8bb614 SetLastError
0x8bb618 FindResourceW
0x8bb61c lstrlenA
0x8bb620 OpenMutexW
0x8bb624 CreateThread
0x8bb628 CompareStringW
0x8bb62c CopyFileW
0x8bb630 MapViewOfFile
0x8bb634 CreateMutexW
0x8bb638 LoadLibraryA
0x8bb63c GetVolumeInformationW
0x8bb640 ResetEvent
0x8bb644 FreeResource
0x8bb648 GetComputerNameExW
0x8bb64c GetDriveTypeW
0x8bb650 GetVersion
0x8bb654 MoveFileW
0x8bb658 RaiseException
0x8bb65c FormatMessageW
0x8bb660 OpenProcess
0x8bb664 SwitchToThread
0x8bb668 GetExitCodeThread
0x8bb66c ReadDirectoryChangesW
0x8bb670 GetCurrentThread
0x8bb674 LocalFileTimeToFileTime
0x8bb678 GetFileAttributesExW
0x8bb67c IsBadReadPtr
0x8bb680 ExpandEnvironmentStringsW
0x8bb684 LockResource
0x8bb688 LoadLibraryExW
0x8bb68c FileTimeToSystemTime
0x8bb690 GetCurrentThreadId
0x8bb694 UnhandledExceptionFilter
0x8bb698 VirtualQuery
0x8bb69c GlobalFree
0x8bb6a0 VirtualQueryEx
0x8bb6a4 Sleep
0x8bb6a8 EnterCriticalSection
0x8bb6ac SetFilePointer
0x8bb6b0 ReleaseMutex
0x8bb6b4 FlushFileBuffers
0x8bb6b8 GetStringTypeExA
0x8bb6bc LoadResource
0x8bb6c0 SuspendThread
0x8bb6c4 GetTickCount
0x8bb6c8 WritePrivateProfileStringW
0x8bb6cc WaitForMultipleObjects
0x8bb6d0 GetTempFileNameW
0x8bb6d4 GetFileSize
0x8bb6d8 GetStartupInfoW
0x8bb6dc GetFileAttributesW
0x8bb6e0 SetCurrentDirectoryW
0x8bb6e4 GetCurrentDirectoryW
0x8bb6e8 InitializeCriticalSection
0x8bb6ec VerLanguageNameW
0x8bb6f0 GetThreadPriority
0x8bb6f4 GetCurrentProcess
0x8bb6f8 SetThreadPriority
0x8bb6fc VirtualAlloc
0x8bb700 GetTempPathW
0x8bb704 GetCommandLineW
0x8bb708 GetSystemInfo
0x8bb70c LeaveCriticalSection
0x8bb710 GetProcAddress
0x8bb714 ResumeThread
0x8bb718 SearchPathW
0x8bb71c GetLogicalDriveStringsW
0x8bb720 GetVersionExW
0x8bb724 GetModuleHandleA
0x8bb728 VerifyVersionInfoW
0x8bb72c HeapCreate
0x8bb730 LCMapStringW
0x8bb734 GetDiskFreeSpaceW
0x8bb738 VerSetConditionMask
0x8bb73c FindFirstFileW
0x8bb740 GetUserDefaultUILanguage
0x8bb744 LockFile
0x8bb748 GetConsoleOutputCP
0x8bb74c UnmapViewOfFile
0x8bb750 GetConsoleCP
0x8bb754 lstrlenW
0x8bb758 CompareStringA
0x8bb75c QueryPerformanceCounter
0x8bb760 SetEndOfFile
0x8bb764 HeapFree
0x8bb768 WideCharToMultiByte
0x8bb76c FindClose
0x8bb770 MultiByteToWideChar
0x8bb774 CreateMutexA
0x8bb778 LoadLibraryW
0x8bb77c SetEvent
0x8bb780 GetLocaleInfoW
0x8bb784 CreateFileW
0x8bb788 SystemTimeToFileTime
0x8bb78c DeleteFileW
0x8bb790 IsDBCSLeadByteEx
0x8bb794 GetEnvironmentVariableW
0x8bb798 GetLocalTime
0x8bb79c WaitForSingleObject
0x8bb7a0 WriteFile
0x8bb7a4 CreateFileMappingW
0x8bb7a8 ExitThread
0x8bb7ac DeleteCriticalSection
0x8bb7b0 GetDateFormatW
0x8bb7b4 TlsGetValue
0x8bb7b8 SetErrorMode
0x8bb7bc GetComputerNameW
0x8bb7c0 IsValidLocale
0x8bb7c4 TlsSetValue
0x8bb7c8 CreateDirectoryW
0x8bb7cc GetSystemDefaultUILanguage
0x8bb7d0 EnumCalendarInfoW
0x8bb7d4 LocalAlloc
0x8bb7d8 RemoveDirectoryW
0x8bb7dc CreateEventW
0x8bb7e0 GetPrivateProfileStringW
0x8bb7e4 WaitForMultipleObjectsEx
0x8bb7e8 GetThreadLocale
0x8bb7ec SetThreadLocale
shlwapi.dll
0x8bb7f4 PathRelativePathToW
shell32.dll
0x8bb7fc SHGetFolderPathW
ole32.dll
0x8bb804 CoInitializeEx
0x8bb808 CoInitialize
0x8bb80c CoCreateInstance
0x8bb810 CoUninitialize
0x8bb814 CoTaskMemFree
0x8bb818 CoTaskMemAlloc
0x8bb81c StringFromCLSID
version.dll
0x8bb824 GetFileVersionInfoSizeW
0x8bb828 VerQueryValueW
0x8bb82c GetFileVersionInfoW
user32.dll
0x8bb834 IsWindow
0x8bb838 FindWindowExW
0x8bb83c TranslateMessage
0x8bb840 CharLowerBuffA
0x8bb844 CharLowerBuffW
0x8bb848 CharUpperW
0x8bb84c PeekMessageA
0x8bb850 PeekMessageW
0x8bb854 GetSystemMetrics
0x8bb858 MessageBoxW
0x8bb85c PostThreadMessageW
0x8bb860 WaitMessage
0x8bb864 CharUpperBuffA
0x8bb868 CharUpperBuffW
0x8bb86c GetWindowThreadProcessId
0x8bb870 CharNextW
0x8bb874 MsgWaitForMultipleObjects
0x8bb878 LoadStringW
0x8bb87c IsWindowUnicode
0x8bb880 MsgWaitForMultipleObjectsEx
0x8bb884 DispatchMessageW
0x8bb888 DispatchMessageA
iphlpapi.dll
0x8bb890 GetAdaptersInfo
oleaut32.dll
0x8bb898 SafeArrayPutElement
0x8bb89c SetErrorInfo
0x8bb8a0 GetErrorInfo
0x8bb8a4 VariantInit
0x8bb8a8 VariantClear
0x8bb8ac SysFreeString
0x8bb8b0 SafeArrayAccessData
0x8bb8b4 SysReAllocStringLen
0x8bb8b8 SafeArrayCreate
0x8bb8bc CreateErrorInfo
0x8bb8c0 SafeArrayGetElement
0x8bb8c4 SysAllocStringLen
0x8bb8c8 SafeArrayUnaccessData
0x8bb8cc SafeArrayPtrOfIndex
0x8bb8d0 VariantCopy
0x8bb8d4 SafeArrayGetUBound
0x8bb8d8 SafeArrayGetLBound
0x8bb8dc VariantCopyInd
0x8bb8e0 VariantChangeType
msvcrt.dll
0x8bb8e8 isupper
0x8bb8ec isalpha
0x8bb8f0 isalnum
0x8bb8f4 toupper
0x8bb8f8 memchr
0x8bb8fc memcmp
0x8bb900 memcpy
0x8bb904 memset
0x8bb908 isprint
0x8bb90c isspace
0x8bb910 iscntrl
0x8bb914 isxdigit
0x8bb918 ispunct
0x8bb91c isgraph
0x8bb920 islower
0x8bb924 tolower
advapi32.dll
0x8bb92c RegSetValueExW
0x8bb930 RegConnectRegistryW
0x8bb934 GetUserNameW
0x8bb938 RegQueryInfoKeyW
0x8bb93c RegUnLoadKeyW
0x8bb940 RegSaveKeyW
0x8bb944 RegReplaceKeyW
0x8bb948 RegCreateKeyExW
0x8bb94c SetEntriesInAclW
0x8bb950 RegLoadKeyW
0x8bb954 RegEnumKeyExW
0x8bb958 RegDeleteKeyW
0x8bb95c RegOpenKeyExA
0x8bb960 RegOpenKeyExW
0x8bb964 FreeSid
0x8bb968 AllocateAndInitializeSid
0x8bb96c RegDeleteValueW
0x8bb970 RegFlushKey
0x8bb974 SetNamedSecurityInfoW
0x8bb978 RegQueryValueExA
0x8bb97c RegQueryValueExW
0x8bb980 RegEnumValueW
0x8bb984 RegCloseKey
0x8bb988 RegRestoreKeyW
winhttp.dll
0x8bb990 WinHttpGetIEProxyConfigForCurrentUser
0x8bb994 WinHttpSetTimeouts
0x8bb998 WinHttpSetStatusCallback
0x8bb99c WinHttpConnect
0x8bb9a0 WinHttpReceiveResponse
0x8bb9a4 WinHttpQueryAuthSchemes
0x8bb9a8 WinHttpGetProxyForUrl
0x8bb9ac WinHttpReadData
0x8bb9b0 WinHttpCloseHandle
0x8bb9b4 WinHttpQueryHeaders
0x8bb9b8 WinHttpOpenRequest
0x8bb9bc WinHttpAddRequestHeaders
0x8bb9c0 WinHttpOpen
0x8bb9c4 WinHttpWriteData
0x8bb9c8 WinHttpSetCredentials
0x8bb9cc WinHttpQueryDataAvailable
0x8bb9d0 WinHttpSetOption
0x8bb9d4 WinHttpSendRequest
0x8bb9d8 WinHttpQueryOption
EAT(Export Address Table) Library
0x515f8c Lock
0x515f94 MainThreadRequest
0x515f90 UnLock
0x41353c __dbk_fcall_wrapper
0x834648 dbkFCallWrapperAddr
kernel32.dll
0x8bb568 GetFileTime
0x8bb56c GetFileType
0x8bb570 SetFileTime
0x8bb574 QueryDosDeviceW
0x8bb578 GetACP
0x8bb57c GetExitCodeProcess
0x8bb580 GetStringTypeExW
0x8bb584 CloseHandle
0x8bb588 LocalFree
0x8bb58c GetCurrentProcessId
0x8bb590 SizeofResource
0x8bb594 VirtualProtect
0x8bb598 UnlockFile
0x8bb59c SetEnvironmentVariableW
0x8bb5a0 TerminateThread
0x8bb5a4 QueryPerformanceFrequency
0x8bb5a8 IsDebuggerPresent
0x8bb5ac FindNextFileW
0x8bb5b0 FlushInstructionCache
0x8bb5b4 GetFullPathNameW
0x8bb5b8 VirtualFree
0x8bb5bc GetProcessHeap
0x8bb5c0 ExitProcess
0x8bb5c4 HeapAlloc
0x8bb5c8 GetCPInfoExW
0x8bb5cc GetSystemTime
0x8bb5d0 GetLongPathNameW
0x8bb5d4 RtlUnwind
0x8bb5d8 GetCPInfo
0x8bb5dc EnumSystemLocalesW
0x8bb5e0 GetStdHandle
0x8bb5e4 GetTimeZoneInformation
0x8bb5e8 FileTimeToLocalFileTime
0x8bb5ec GetModuleHandleW
0x8bb5f0 FreeLibrary
0x8bb5f4 TryEnterCriticalSection
0x8bb5f8 HeapDestroy
0x8bb5fc FileTimeToDosDateTime
0x8bb600 ReadFile
0x8bb604 DosDateTimeToFileTime
0x8bb608 CreateProcessW
0x8bb60c GetLastError
0x8bb610 GetModuleFileNameW
0x8bb614 SetLastError
0x8bb618 FindResourceW
0x8bb61c lstrlenA
0x8bb620 OpenMutexW
0x8bb624 CreateThread
0x8bb628 CompareStringW
0x8bb62c CopyFileW
0x8bb630 MapViewOfFile
0x8bb634 CreateMutexW
0x8bb638 LoadLibraryA
0x8bb63c GetVolumeInformationW
0x8bb640 ResetEvent
0x8bb644 FreeResource
0x8bb648 GetComputerNameExW
0x8bb64c GetDriveTypeW
0x8bb650 GetVersion
0x8bb654 MoveFileW
0x8bb658 RaiseException
0x8bb65c FormatMessageW
0x8bb660 OpenProcess
0x8bb664 SwitchToThread
0x8bb668 GetExitCodeThread
0x8bb66c ReadDirectoryChangesW
0x8bb670 GetCurrentThread
0x8bb674 LocalFileTimeToFileTime
0x8bb678 GetFileAttributesExW
0x8bb67c IsBadReadPtr
0x8bb680 ExpandEnvironmentStringsW
0x8bb684 LockResource
0x8bb688 LoadLibraryExW
0x8bb68c FileTimeToSystemTime
0x8bb690 GetCurrentThreadId
0x8bb694 UnhandledExceptionFilter
0x8bb698 VirtualQuery
0x8bb69c GlobalFree
0x8bb6a0 VirtualQueryEx
0x8bb6a4 Sleep
0x8bb6a8 EnterCriticalSection
0x8bb6ac SetFilePointer
0x8bb6b0 ReleaseMutex
0x8bb6b4 FlushFileBuffers
0x8bb6b8 GetStringTypeExA
0x8bb6bc LoadResource
0x8bb6c0 SuspendThread
0x8bb6c4 GetTickCount
0x8bb6c8 WritePrivateProfileStringW
0x8bb6cc WaitForMultipleObjects
0x8bb6d0 GetTempFileNameW
0x8bb6d4 GetFileSize
0x8bb6d8 GetStartupInfoW
0x8bb6dc GetFileAttributesW
0x8bb6e0 SetCurrentDirectoryW
0x8bb6e4 GetCurrentDirectoryW
0x8bb6e8 InitializeCriticalSection
0x8bb6ec VerLanguageNameW
0x8bb6f0 GetThreadPriority
0x8bb6f4 GetCurrentProcess
0x8bb6f8 SetThreadPriority
0x8bb6fc VirtualAlloc
0x8bb700 GetTempPathW
0x8bb704 GetCommandLineW
0x8bb708 GetSystemInfo
0x8bb70c LeaveCriticalSection
0x8bb710 GetProcAddress
0x8bb714 ResumeThread
0x8bb718 SearchPathW
0x8bb71c GetLogicalDriveStringsW
0x8bb720 GetVersionExW
0x8bb724 GetModuleHandleA
0x8bb728 VerifyVersionInfoW
0x8bb72c HeapCreate
0x8bb730 LCMapStringW
0x8bb734 GetDiskFreeSpaceW
0x8bb738 VerSetConditionMask
0x8bb73c FindFirstFileW
0x8bb740 GetUserDefaultUILanguage
0x8bb744 LockFile
0x8bb748 GetConsoleOutputCP
0x8bb74c UnmapViewOfFile
0x8bb750 GetConsoleCP
0x8bb754 lstrlenW
0x8bb758 CompareStringA
0x8bb75c QueryPerformanceCounter
0x8bb760 SetEndOfFile
0x8bb764 HeapFree
0x8bb768 WideCharToMultiByte
0x8bb76c FindClose
0x8bb770 MultiByteToWideChar
0x8bb774 CreateMutexA
0x8bb778 LoadLibraryW
0x8bb77c SetEvent
0x8bb780 GetLocaleInfoW
0x8bb784 CreateFileW
0x8bb788 SystemTimeToFileTime
0x8bb78c DeleteFileW
0x8bb790 IsDBCSLeadByteEx
0x8bb794 GetEnvironmentVariableW
0x8bb798 GetLocalTime
0x8bb79c WaitForSingleObject
0x8bb7a0 WriteFile
0x8bb7a4 CreateFileMappingW
0x8bb7a8 ExitThread
0x8bb7ac DeleteCriticalSection
0x8bb7b0 GetDateFormatW
0x8bb7b4 TlsGetValue
0x8bb7b8 SetErrorMode
0x8bb7bc GetComputerNameW
0x8bb7c0 IsValidLocale
0x8bb7c4 TlsSetValue
0x8bb7c8 CreateDirectoryW
0x8bb7cc GetSystemDefaultUILanguage
0x8bb7d0 EnumCalendarInfoW
0x8bb7d4 LocalAlloc
0x8bb7d8 RemoveDirectoryW
0x8bb7dc CreateEventW
0x8bb7e0 GetPrivateProfileStringW
0x8bb7e4 WaitForMultipleObjectsEx
0x8bb7e8 GetThreadLocale
0x8bb7ec SetThreadLocale
shlwapi.dll
0x8bb7f4 PathRelativePathToW
shell32.dll
0x8bb7fc SHGetFolderPathW
ole32.dll
0x8bb804 CoInitializeEx
0x8bb808 CoInitialize
0x8bb80c CoCreateInstance
0x8bb810 CoUninitialize
0x8bb814 CoTaskMemFree
0x8bb818 CoTaskMemAlloc
0x8bb81c StringFromCLSID
version.dll
0x8bb824 GetFileVersionInfoSizeW
0x8bb828 VerQueryValueW
0x8bb82c GetFileVersionInfoW
user32.dll
0x8bb834 IsWindow
0x8bb838 FindWindowExW
0x8bb83c TranslateMessage
0x8bb840 CharLowerBuffA
0x8bb844 CharLowerBuffW
0x8bb848 CharUpperW
0x8bb84c PeekMessageA
0x8bb850 PeekMessageW
0x8bb854 GetSystemMetrics
0x8bb858 MessageBoxW
0x8bb85c PostThreadMessageW
0x8bb860 WaitMessage
0x8bb864 CharUpperBuffA
0x8bb868 CharUpperBuffW
0x8bb86c GetWindowThreadProcessId
0x8bb870 CharNextW
0x8bb874 MsgWaitForMultipleObjects
0x8bb878 LoadStringW
0x8bb87c IsWindowUnicode
0x8bb880 MsgWaitForMultipleObjectsEx
0x8bb884 DispatchMessageW
0x8bb888 DispatchMessageA
iphlpapi.dll
0x8bb890 GetAdaptersInfo
oleaut32.dll
0x8bb898 SafeArrayPutElement
0x8bb89c SetErrorInfo
0x8bb8a0 GetErrorInfo
0x8bb8a4 VariantInit
0x8bb8a8 VariantClear
0x8bb8ac SysFreeString
0x8bb8b0 SafeArrayAccessData
0x8bb8b4 SysReAllocStringLen
0x8bb8b8 SafeArrayCreate
0x8bb8bc CreateErrorInfo
0x8bb8c0 SafeArrayGetElement
0x8bb8c4 SysAllocStringLen
0x8bb8c8 SafeArrayUnaccessData
0x8bb8cc SafeArrayPtrOfIndex
0x8bb8d0 VariantCopy
0x8bb8d4 SafeArrayGetUBound
0x8bb8d8 SafeArrayGetLBound
0x8bb8dc VariantCopyInd
0x8bb8e0 VariantChangeType
msvcrt.dll
0x8bb8e8 isupper
0x8bb8ec isalpha
0x8bb8f0 isalnum
0x8bb8f4 toupper
0x8bb8f8 memchr
0x8bb8fc memcmp
0x8bb900 memcpy
0x8bb904 memset
0x8bb908 isprint
0x8bb90c isspace
0x8bb910 iscntrl
0x8bb914 isxdigit
0x8bb918 ispunct
0x8bb91c isgraph
0x8bb920 islower
0x8bb924 tolower
advapi32.dll
0x8bb92c RegSetValueExW
0x8bb930 RegConnectRegistryW
0x8bb934 GetUserNameW
0x8bb938 RegQueryInfoKeyW
0x8bb93c RegUnLoadKeyW
0x8bb940 RegSaveKeyW
0x8bb944 RegReplaceKeyW
0x8bb948 RegCreateKeyExW
0x8bb94c SetEntriesInAclW
0x8bb950 RegLoadKeyW
0x8bb954 RegEnumKeyExW
0x8bb958 RegDeleteKeyW
0x8bb95c RegOpenKeyExA
0x8bb960 RegOpenKeyExW
0x8bb964 FreeSid
0x8bb968 AllocateAndInitializeSid
0x8bb96c RegDeleteValueW
0x8bb970 RegFlushKey
0x8bb974 SetNamedSecurityInfoW
0x8bb978 RegQueryValueExA
0x8bb97c RegQueryValueExW
0x8bb980 RegEnumValueW
0x8bb984 RegCloseKey
0x8bb988 RegRestoreKeyW
winhttp.dll
0x8bb990 WinHttpGetIEProxyConfigForCurrentUser
0x8bb994 WinHttpSetTimeouts
0x8bb998 WinHttpSetStatusCallback
0x8bb99c WinHttpConnect
0x8bb9a0 WinHttpReceiveResponse
0x8bb9a4 WinHttpQueryAuthSchemes
0x8bb9a8 WinHttpGetProxyForUrl
0x8bb9ac WinHttpReadData
0x8bb9b0 WinHttpCloseHandle
0x8bb9b4 WinHttpQueryHeaders
0x8bb9b8 WinHttpOpenRequest
0x8bb9bc WinHttpAddRequestHeaders
0x8bb9c0 WinHttpOpen
0x8bb9c4 WinHttpWriteData
0x8bb9c8 WinHttpSetCredentials
0x8bb9cc WinHttpQueryDataAvailable
0x8bb9d0 WinHttpSetOption
0x8bb9d4 WinHttpSendRequest
0x8bb9d8 WinHttpQueryOption
EAT(Export Address Table) Library
0x515f8c Lock
0x515f94 MainThreadRequest
0x515f90 UnLock
0x41353c __dbk_fcall_wrapper
0x834648 dbkFCallWrapperAddr