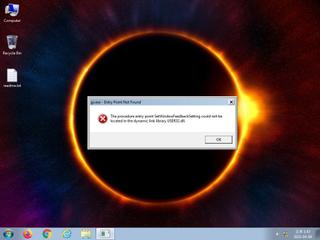
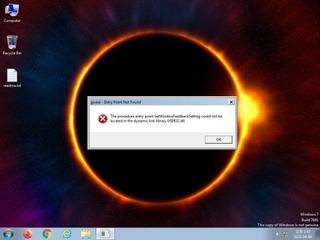
ScreenShot
| Created | 2025.04.09 13:46 | Machine | s1_win7_x6403 |
| Filename | gs.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 48 detected (AIDetectMalware, Malicious, score, Ghanarava, Lazy, Unsafe, Save, confidence, GenHeur, MalPbs, gen2, high confidence, GenKryptik, HHYM, DropperX, suWzIcHGsuD, Kryptik, guojb, LUMMASTEALER, YXFDIZ, moderate, Static AI, Malicious PE, GrayWare, Wacapew, LummaC, ABTrojan, QUWD, LummaC2, R699274, Artemis, Sgil, susgen, HHUD, GJ8PHU) | ||
| md5 | 899e8f69a4b5e13049ab33b475ca98fa | ||
| sha256 | 3fed869dca0c8d4262cbfb3dd8c0819eb771e3fda1cb0dd671da4379b14e8c52 | ||
| ssdeep | 24576:M7ha3luY0uMsAawT2yFsB4x95bJ73DYyXnPwHeXgTfKq:Mt8w3FsB4x91hsyXCehq | ||
| imphash | 4f1342a4b5f473a33cad1e0fbbb5c40c | ||
| impfuzzy | 12:oZG8uIX1N0C8FheQ+kkES/mlArvzBZzNXD9gc3:YVFOFFkQ+kkES/KArzBxNXD9g4 | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 48 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x470c18 ExitProcess
0x470c1c GetLogicalProcessorInformation
0x470c20 GetNativeSystemInfo
0x470c24 GetProcessHeap
0x470c28 GetSystemInfo
0x470c2c GetSystemTimes
0x470c30 GetThreadPriorityBoost
0x470c34 GetTickCount
0x470c38 GlobalMemoryStatusEx
0x470c3c HeapAlloc
0x470c40 HeapValidate
0x470c44 IsDebuggerPresent
0x470c48 QueryPerformanceCounter
0x470c4c Sleep
0x470c50 lstrcmpiW
USER32.dll
0x470c58 AnimateWindow
0x470c5c CreateWindowExW
0x470c60 DefWindowProcW
0x470c64 GetDesktopWindow
0x470c68 GetMessageTime
0x470c6c GetWindowRgnBox
0x470c70 LoadImageW
0x470c74 SetLayeredWindowAttributes
0x470c78 SetWindowFeedbackSetting
EAT(Export Address Table) Library
0x401000 ?DecoyAPICalls@@YAXXZ
KERNEL32.dll
0x470c18 ExitProcess
0x470c1c GetLogicalProcessorInformation
0x470c20 GetNativeSystemInfo
0x470c24 GetProcessHeap
0x470c28 GetSystemInfo
0x470c2c GetSystemTimes
0x470c30 GetThreadPriorityBoost
0x470c34 GetTickCount
0x470c38 GlobalMemoryStatusEx
0x470c3c HeapAlloc
0x470c40 HeapValidate
0x470c44 IsDebuggerPresent
0x470c48 QueryPerformanceCounter
0x470c4c Sleep
0x470c50 lstrcmpiW
USER32.dll
0x470c58 AnimateWindow
0x470c5c CreateWindowExW
0x470c60 DefWindowProcW
0x470c64 GetDesktopWindow
0x470c68 GetMessageTime
0x470c6c GetWindowRgnBox
0x470c70 LoadImageW
0x470c74 SetLayeredWindowAttributes
0x470c78 SetWindowFeedbackSetting
EAT(Export Address Table) Library
0x401000 ?DecoyAPICalls@@YAXXZ