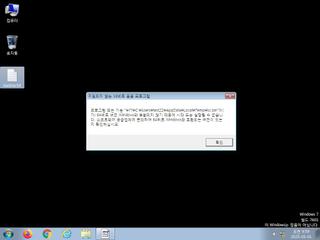
ScreenShot
| Created | 2025.05.01 10:02 | Machine | s1_win7_x6401 |
| Filename | sc.bin | ||
| Type | MS-DOS executable | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 21 detected (Cobaltstrike, Beacon, Marte, Swrort, Detected, XOREncoded, Sonbokli, BeaconLoader) | ||
| md5 | a060f805ad243ff1c98778d0bcee935e | ||
| sha256 | 0d257dafbf5ad79f01ad58372eb46ac6795f16ebdd2e9edc3b1bee393430f4a8 | ||
| ssdeep | 6144:8LcTIjJ1kCXMlviI9X6PLghTi2XDS/A/evqLjlvEE:8LWcdCviumghTi2zt2iLjl3 | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (1cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 21 AntiVirus engines on VirusTotal as malicious |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | HKTL_CobaltStrike_Beacon_Strings | Identifies strings used in Cobalt Strike Beacon DLL | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|