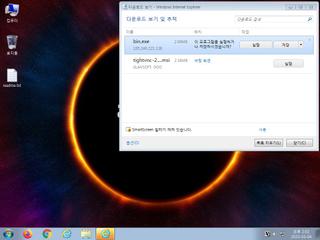
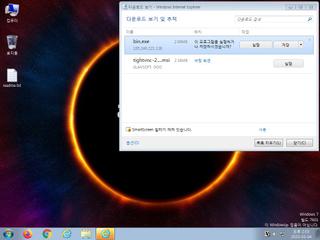
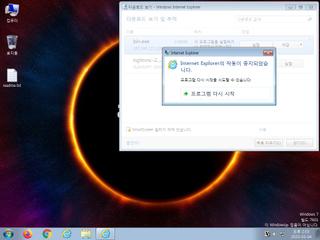
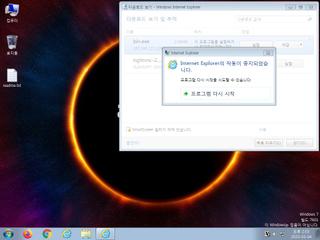
ScreenShot
| Created | 2023.03.05 05:11 | Machine | s1_win7_x6402 |
| Filename | bin.exe | ||
| Type | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | |||
| md5 | af4268c094f2a9c6e6a85f8626b9a5c7 | ||
| sha256 | 07b974442b53035b8d057a7b429c191fe71f149a698041b005ee85645a89c165 | ||
| ssdeep | 49152:y2sQ8R/u6S/gPV4PW/vlLr8EdiITRf+EGg7dH1zaSo5hTk6k1qFG:yfQM/fSoPFNLQg1WT5Q | ||
| imphash | 9cbefe68f395e67356e2a5d8d1b285c0 | ||
| impfuzzy | 24:UbVjhNwO+VuT2oLtXOr6kwmDruMztxdEr6tP:KwO+VAXOmGx0oP | ||
Network IP location
Signature (13cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | Found URLs in memory pointing to an IP address rather than a domain (potentially indicative of Command & Control traffic) |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | An application raised an exception which may be indicative of an exploit crash |
| notice | Creates executable files on the filesystem |
| notice | Drops an executable to the user AppData folder |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Potentially malicious URLs were found in the process memory dump |
| notice | Uses Windows utilities for basic Windows functionality |
| notice | Yara rule detected in process memory |
| info | One or more processes crashed |
Rules (40cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | Network_Downloader | File Downloader | memory |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| notice | Code_injection | Code injection with CreateRemoteThread in a remote process | memory |
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | Hijack_Network | Hijack network configuration | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | local_credential_Steal | Steal credential | memory |
| notice | Network_DGA | Communication using DGA | memory |
| notice | Network_DNS | Communications use DNS | memory |
| notice | Network_FTP | Communications over FTP | memory |
| notice | Network_HTTP | Communications over HTTP | memory |
| notice | Network_P2P_Win | Communications over P2P network | memory |
| notice | Network_TCP_Socket | Communications over RAW Socket | memory |
| notice | Persistence | Install itself for autorun at Windows startup | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| notice | Sniff_Audio | Record Audio | memory |
| notice | Str_Win32_Http_API | Match Windows Http API call | memory |
| notice | Str_Win32_Internet_API | Match Windows Inet API call | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | antisb_threatExpert | Anti-Sandbox checks for ThreatExpert | memory |
| info | Check_Dlls | (no description) | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerCheck__RemoteAPI | (no description) | memory |
| info | DebuggerException__ConsoleCtrl | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsPE32 | (no description) | binaries (download) |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
Suricata ids
ET INFO Executable Download from dotted-quad Host
ET MALWARE Possible MalDoc Payload Download Nov 11 2014
ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO TLS Handshake Failure
ET MALWARE Possible MalDoc Payload Download Nov 11 2014
ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO TLS Handshake Failure
PE API
IAT(Import Address Table) Library
kernel32.dll
0x6bc220 WriteFile
0x6bc224 WriteConsoleW
0x6bc228 WaitForMultipleObjects
0x6bc22c WaitForSingleObject
0x6bc230 VirtualQuery
0x6bc234 VirtualFree
0x6bc238 VirtualAlloc
0x6bc23c SwitchToThread
0x6bc240 SuspendThread
0x6bc244 SetWaitableTimer
0x6bc248 SetUnhandledExceptionFilter
0x6bc24c SetProcessPriorityBoost
0x6bc250 SetEvent
0x6bc254 SetErrorMode
0x6bc258 SetConsoleCtrlHandler
0x6bc25c ResumeThread
0x6bc260 PostQueuedCompletionStatus
0x6bc264 LoadLibraryA
0x6bc268 LoadLibraryW
0x6bc26c SetThreadContext
0x6bc270 GetThreadContext
0x6bc274 GetSystemInfo
0x6bc278 GetSystemDirectoryA
0x6bc27c GetStdHandle
0x6bc280 GetQueuedCompletionStatusEx
0x6bc284 GetProcessAffinityMask
0x6bc288 GetProcAddress
0x6bc28c GetEnvironmentStringsW
0x6bc290 GetConsoleMode
0x6bc294 FreeEnvironmentStringsW
0x6bc298 ExitProcess
0x6bc29c DuplicateHandle
0x6bc2a0 CreateWaitableTimerExW
0x6bc2a4 CreateThread
0x6bc2a8 CreateIoCompletionPort
0x6bc2ac CreateFileA
0x6bc2b0 CreateEventA
0x6bc2b4 CloseHandle
0x6bc2b8 AddVectoredExceptionHandler
EAT(Export Address Table) is none
kernel32.dll
0x6bc220 WriteFile
0x6bc224 WriteConsoleW
0x6bc228 WaitForMultipleObjects
0x6bc22c WaitForSingleObject
0x6bc230 VirtualQuery
0x6bc234 VirtualFree
0x6bc238 VirtualAlloc
0x6bc23c SwitchToThread
0x6bc240 SuspendThread
0x6bc244 SetWaitableTimer
0x6bc248 SetUnhandledExceptionFilter
0x6bc24c SetProcessPriorityBoost
0x6bc250 SetEvent
0x6bc254 SetErrorMode
0x6bc258 SetConsoleCtrlHandler
0x6bc25c ResumeThread
0x6bc260 PostQueuedCompletionStatus
0x6bc264 LoadLibraryA
0x6bc268 LoadLibraryW
0x6bc26c SetThreadContext
0x6bc270 GetThreadContext
0x6bc274 GetSystemInfo
0x6bc278 GetSystemDirectoryA
0x6bc27c GetStdHandle
0x6bc280 GetQueuedCompletionStatusEx
0x6bc284 GetProcessAffinityMask
0x6bc288 GetProcAddress
0x6bc28c GetEnvironmentStringsW
0x6bc290 GetConsoleMode
0x6bc294 FreeEnvironmentStringsW
0x6bc298 ExitProcess
0x6bc29c DuplicateHandle
0x6bc2a0 CreateWaitableTimerExW
0x6bc2a4 CreateThread
0x6bc2a8 CreateIoCompletionPort
0x6bc2ac CreateFileA
0x6bc2b0 CreateEventA
0x6bc2b4 CloseHandle
0x6bc2b8 AddVectoredExceptionHandler
EAT(Export Address Table) is none