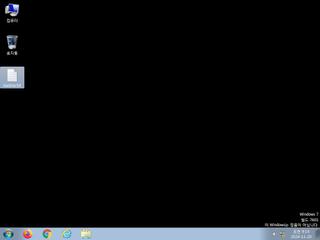
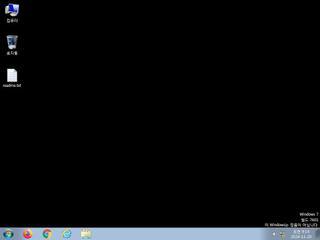
ScreenShot
| Created | 2024.11.20 09:19 | Machine | s1_win7_x6401 |
| Filename | exe010.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | e4f5c4520d567afd0eb58d190fff70a0 | ||
| sha256 | e3fccdf6f573f846653b71a54be347616d4b1b92b641a3757d4deb8422abede4 | ||
| ssdeep | 1536:hFdkWIXbevApQrS4az0ammrEWjXq+66DFUABABOVLefE/:XGWIkmowz0iEWj6+JB8M/ | ||
| imphash | 3ee11032a62fe9ae89669891ab01af7d | ||
| impfuzzy | 48:YqtQg1E//Cy5OCECLvRjv04Sey0Qu38twt4xXp95GTXnBKl/i/1sjFRnvVnmbZn6:Dtt1E/6y57WX4DAFdVcUAqZl | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| watch | Creates a slightly modified copy of itself |
| watch | Installs itself for autorun at Windows startup |
| notice | Creates executable files on the filesystem |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (11cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ole32.DLL
0x4322b0 CoCreateInstance
0x4322b4 CLSIDFromString
0x4322b8 CoInitialize
0x4322bc CoUninitialize
OLEAUT32.DLL
0x4322c4 SysAllocString
WININET.DLL
0x4322cc DeleteUrlCacheEntry
0x4322d0 FindFirstUrlCacheEntryA
0x4322d4 FindNextUrlCacheEntryA
KERNEL32.DLL
0x4322dc ExitProcess
0x4322e0 ExpandEnvironmentStringsA
0x4322e4 GetCommandLineA
0x4322e8 GetComputerNameA
0x4322ec GetCurrentProcessId
0x4322f0 GetCurrentThreadId
0x4322f4 GetExitCodeThread
0x4322f8 GetFileSize
0x4322fc GetModuleFileNameA
0x432300 GetModuleHandleA
0x432304 CloseHandle
0x432308 GetProcAddress
0x43230c GetSystemDirectoryA
0x432310 GetTempPathA
0x432314 GetTickCount
0x432318 GetVersion
0x43231c GetVersionExA
0x432320 GetWindowsDirectoryA
0x432324 GlobalMemoryStatus
0x432328 CopyFileA
0x43232c InterlockedIncrement
0x432330 IsBadReadPtr
0x432334 IsBadWritePtr
0x432338 LoadLibraryA
0x43233c LocalAlloc
0x432340 LocalFree
0x432344 OpenMutexA
0x432348 CreateFileA
0x43234c ReadFile
0x432350 RtlUnwind
0x432354 SetFilePointer
0x432358 CreateMutexA
0x43235c Sleep
0x432360 TerminateProcess
0x432364 VirtualQuery
0x432368 CreateProcessA
0x43236c WaitForSingleObject
0x432370 WideCharToMultiByte
0x432374 WinExec
0x432378 WriteFile
0x43237c lstrlenA
0x432380 lstrlenW
0x432384 CreateThread
0x432388 DeleteFileA
USER32.DLL
0x432390 GetWindowTextA
0x432394 GetWindowRect
0x432398 FindWindowA
0x43239c GetWindow
0x4323a0 GetClassNameA
0x4323a4 SetFocus
0x4323a8 GetForegroundWindow
0x4323ac LoadCursorA
0x4323b0 LoadIconA
0x4323b4 SetTimer
0x4323b8 RegisterClassA
0x4323bc MessageBoxA
0x4323c0 GetMessageA
0x4323c4 GetWindowLongA
0x4323c8 SetWindowLongA
0x4323cc CreateDesktopA
0x4323d0 SetThreadDesktop
0x4323d4 GetThreadDesktop
0x4323d8 TranslateMessage
0x4323dc DispatchMessageA
0x4323e0 SendMessageA
0x4323e4 PostQuitMessage
0x4323e8 ShowWindow
0x4323ec CreateWindowExA
0x4323f0 DestroyWindow
0x4323f4 MoveWindow
0x4323f8 DefWindowProcA
0x4323fc CallWindowProcA
GDI32.DLL
0x432404 GetStockObject
0x432408 SetBkColor
0x43240c SetTextColor
0x432410 CreateBrushIndirect
0x432414 CreateFontA
ADVAPI32.DLL
0x43241c GetUserNameA
0x432420 RegCreateKeyExA
0x432424 RegCloseKey
0x432428 RegOpenKeyExA
0x43242c RegQueryValueExA
0x432430 RegSetValueExA
0x432434 GetSecurityInfo
0x432438 SetSecurityInfo
0x43243c SetEntriesInAclA
CRTDLL.DLL
0x432444 __GetMainArgs
0x432448 _sleep
0x43244c _stricmp
0x432450 atoi
0x432454 exit
0x432458 memcpy
0x43245c memset
0x432460 printf
0x432464 raise
0x432468 rand
0x43246c signal
0x432470 sprintf
0x432474 srand
0x432478 sscanf
0x43247c strcat
0x432480 strchr
0x432484 strncmp
0x432488 vsprintf
MSVCRT.DLL
0x432490 _wgetcwd
opengl32.dll
0x400000 glShadeModel
0x400004 glEnable
0x400008 glHint
opengl32.dll
0x400000 glShadeModel
0x400004 glHint
0x400008 glEnable
authz.dll
0x400000 AuthzAddSidsToContext
0x400004 AuthzFreeResourceManager
kernel32.dll
0x400000 UnmapViewOfFile
0x400004 FlushInstructionCache
0x400008 SetErrorMode
0x40000c GetLogicalDriveStringsW
0x400010 LoadLibraryW
0x400014 GlobalMemoryStatus
0x400018 GetTimeFormatA
0x40001c CreateThread
0x400020 HeapAlloc
0x400024 GetVersionExA
0x400028 QueryDosDeviceA
0x40002c RaiseException
0x400030 GetTimeZoneInformation
0x400034 VirtualAllocEx
0x400038 DecodePointer
0x40003c GetDateFormatA
0x400040 ClearCommBreak
0x400044 TlsAlloc
0x400048 CompareStringA
0x40004c CloseHandle
0x400050 InitializeCriticalSection
0x400054 GetLastError
0x400058 GetPrivateProfileIntA
0x40005c VirtualQueryEx
EAT(Export Address Table) is none
ole32.DLL
0x4322b0 CoCreateInstance
0x4322b4 CLSIDFromString
0x4322b8 CoInitialize
0x4322bc CoUninitialize
OLEAUT32.DLL
0x4322c4 SysAllocString
WININET.DLL
0x4322cc DeleteUrlCacheEntry
0x4322d0 FindFirstUrlCacheEntryA
0x4322d4 FindNextUrlCacheEntryA
KERNEL32.DLL
0x4322dc ExitProcess
0x4322e0 ExpandEnvironmentStringsA
0x4322e4 GetCommandLineA
0x4322e8 GetComputerNameA
0x4322ec GetCurrentProcessId
0x4322f0 GetCurrentThreadId
0x4322f4 GetExitCodeThread
0x4322f8 GetFileSize
0x4322fc GetModuleFileNameA
0x432300 GetModuleHandleA
0x432304 CloseHandle
0x432308 GetProcAddress
0x43230c GetSystemDirectoryA
0x432310 GetTempPathA
0x432314 GetTickCount
0x432318 GetVersion
0x43231c GetVersionExA
0x432320 GetWindowsDirectoryA
0x432324 GlobalMemoryStatus
0x432328 CopyFileA
0x43232c InterlockedIncrement
0x432330 IsBadReadPtr
0x432334 IsBadWritePtr
0x432338 LoadLibraryA
0x43233c LocalAlloc
0x432340 LocalFree
0x432344 OpenMutexA
0x432348 CreateFileA
0x43234c ReadFile
0x432350 RtlUnwind
0x432354 SetFilePointer
0x432358 CreateMutexA
0x43235c Sleep
0x432360 TerminateProcess
0x432364 VirtualQuery
0x432368 CreateProcessA
0x43236c WaitForSingleObject
0x432370 WideCharToMultiByte
0x432374 WinExec
0x432378 WriteFile
0x43237c lstrlenA
0x432380 lstrlenW
0x432384 CreateThread
0x432388 DeleteFileA
USER32.DLL
0x432390 GetWindowTextA
0x432394 GetWindowRect
0x432398 FindWindowA
0x43239c GetWindow
0x4323a0 GetClassNameA
0x4323a4 SetFocus
0x4323a8 GetForegroundWindow
0x4323ac LoadCursorA
0x4323b0 LoadIconA
0x4323b4 SetTimer
0x4323b8 RegisterClassA
0x4323bc MessageBoxA
0x4323c0 GetMessageA
0x4323c4 GetWindowLongA
0x4323c8 SetWindowLongA
0x4323cc CreateDesktopA
0x4323d0 SetThreadDesktop
0x4323d4 GetThreadDesktop
0x4323d8 TranslateMessage
0x4323dc DispatchMessageA
0x4323e0 SendMessageA
0x4323e4 PostQuitMessage
0x4323e8 ShowWindow
0x4323ec CreateWindowExA
0x4323f0 DestroyWindow
0x4323f4 MoveWindow
0x4323f8 DefWindowProcA
0x4323fc CallWindowProcA
GDI32.DLL
0x432404 GetStockObject
0x432408 SetBkColor
0x43240c SetTextColor
0x432410 CreateBrushIndirect
0x432414 CreateFontA
ADVAPI32.DLL
0x43241c GetUserNameA
0x432420 RegCreateKeyExA
0x432424 RegCloseKey
0x432428 RegOpenKeyExA
0x43242c RegQueryValueExA
0x432430 RegSetValueExA
0x432434 GetSecurityInfo
0x432438 SetSecurityInfo
0x43243c SetEntriesInAclA
CRTDLL.DLL
0x432444 __GetMainArgs
0x432448 _sleep
0x43244c _stricmp
0x432450 atoi
0x432454 exit
0x432458 memcpy
0x43245c memset
0x432460 printf
0x432464 raise
0x432468 rand
0x43246c signal
0x432470 sprintf
0x432474 srand
0x432478 sscanf
0x43247c strcat
0x432480 strchr
0x432484 strncmp
0x432488 vsprintf
MSVCRT.DLL
0x432490 _wgetcwd
opengl32.dll
0x400000 glShadeModel
0x400004 glEnable
0x400008 glHint
opengl32.dll
0x400000 glShadeModel
0x400004 glHint
0x400008 glEnable
authz.dll
0x400000 AuthzAddSidsToContext
0x400004 AuthzFreeResourceManager
kernel32.dll
0x400000 UnmapViewOfFile
0x400004 FlushInstructionCache
0x400008 SetErrorMode
0x40000c GetLogicalDriveStringsW
0x400010 LoadLibraryW
0x400014 GlobalMemoryStatus
0x400018 GetTimeFormatA
0x40001c CreateThread
0x400020 HeapAlloc
0x400024 GetVersionExA
0x400028 QueryDosDeviceA
0x40002c RaiseException
0x400030 GetTimeZoneInformation
0x400034 VirtualAllocEx
0x400038 DecodePointer
0x40003c GetDateFormatA
0x400040 ClearCommBreak
0x400044 TlsAlloc
0x400048 CompareStringA
0x40004c CloseHandle
0x400050 InitializeCriticalSection
0x400054 GetLastError
0x400058 GetPrivateProfileIntA
0x40005c VirtualQueryEx
EAT(Export Address Table) is none