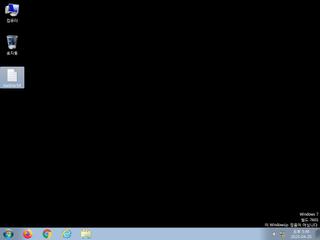
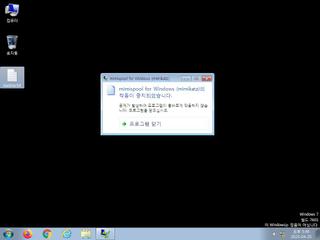
ScreenShot
| Created | 2023.04.25 17:49 | Machine | s1_win7_x6401 |
| Filename | mimispool.dll | ||
| Type | PE32+ executable (DLL) (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 50 detected (Mimikatz, Vfnv, TrojanPSW, malicious, confidence, 100%, Hacktool, high confidence, a variant of Generik, BAPJZZG, score, jsrsix, CVE-2021-1675, Tool, HKTL, MIMIKATZ64, Generic PWS, Detected, R445129, ai score=100, unsafe, Z7hKCBfrpcB, UfvKYTGIZOw, susgen, PossibleThreat) | ||
| md5 | c6cc0def7d584f431d69126c1cc33a20 | ||
| sha256 | 66928c3316a12091995198710e0c537430dacefac1dbe78f12a331e1520142bd | ||
| ssdeep | 192:DGMoIQaZcsBTSWoH6DlI0zPQ4Ib/me0C0uolZC7:VJxgWFlVC50C0uols | ||
| imphash | c38ebbf4627ca2303746c77210e5a12e | ||
| impfuzzy | 12:otNPKjDBIz0sLkJMyVt8Fsu8wQTZBzhPPXJ1XJHGJ030smMH/sJqXI:oK6z0sLkJMA65Q1Bz9L4Ja0TMAqY | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 50 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x180002000 CreateProcessAsUserW
0x180002008 SetTokenInformation
0x180002010 DuplicateTokenEx
0x180002018 OpenProcessToken
USERENV.dll
0x1800020a8 DestroyEnvironmentBlock
0x1800020b0 CreateEnvironmentBlock
WINSTA.dll
0x1800020c0 WinStationEnumerateW
0x1800020c8 WinStationFreeMemory
KERNEL32.dll
0x180002028 GetCurrentProcessId
0x180002030 GetCurrentThreadId
0x180002038 GetTickCount
0x180002040 QueryPerformanceCounter
0x180002048 SetUnhandledExceptionFilter
0x180002050 UnhandledExceptionFilter
0x180002058 Sleep
0x180002060 GetCurrentProcess
0x180002068 SetLastError
0x180002070 CloseHandle
0x180002078 TerminateProcess
0x180002080 RtlCaptureContext
0x180002088 RtlLookupFunctionEntry
0x180002090 RtlVirtualUnwind
0x180002098 GetSystemTimeAsFileTime
msvcrt.dll
0x1800020d8 memset
0x1800020e0 __C_specific_handler
0x1800020e8 _XcptFilter
0x1800020f0 malloc
0x1800020f8 free
0x180002100 _amsg_exit
0x180002108 _initterm
EAT(Export Address Table) Library
0x180001020 DrvDisableDriver
0x180001064 DrvEnableDriver
0x180001024 DrvQueryDriverInfo
0x180001020 DrvResetConfigCache
0x1800010a0 GenerateCopyFilePaths
0x1800010a4 SpoolerCopyFileEvent
ADVAPI32.dll
0x180002000 CreateProcessAsUserW
0x180002008 SetTokenInformation
0x180002010 DuplicateTokenEx
0x180002018 OpenProcessToken
USERENV.dll
0x1800020a8 DestroyEnvironmentBlock
0x1800020b0 CreateEnvironmentBlock
WINSTA.dll
0x1800020c0 WinStationEnumerateW
0x1800020c8 WinStationFreeMemory
KERNEL32.dll
0x180002028 GetCurrentProcessId
0x180002030 GetCurrentThreadId
0x180002038 GetTickCount
0x180002040 QueryPerformanceCounter
0x180002048 SetUnhandledExceptionFilter
0x180002050 UnhandledExceptionFilter
0x180002058 Sleep
0x180002060 GetCurrentProcess
0x180002068 SetLastError
0x180002070 CloseHandle
0x180002078 TerminateProcess
0x180002080 RtlCaptureContext
0x180002088 RtlLookupFunctionEntry
0x180002090 RtlVirtualUnwind
0x180002098 GetSystemTimeAsFileTime
msvcrt.dll
0x1800020d8 memset
0x1800020e0 __C_specific_handler
0x1800020e8 _XcptFilter
0x1800020f0 malloc
0x1800020f8 free
0x180002100 _amsg_exit
0x180002108 _initterm
EAT(Export Address Table) Library
0x180001020 DrvDisableDriver
0x180001064 DrvEnableDriver
0x180001024 DrvQueryDriverInfo
0x180001020 DrvResetConfigCache
0x1800010a0 GenerateCopyFilePaths
0x1800010a4 SpoolerCopyFileEvent