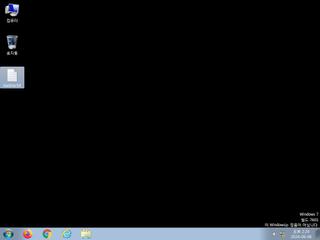
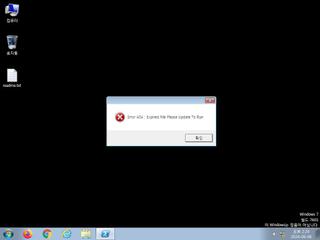
ScreenShot
| Created | 2024.06.06 14:27 | Machine | s1_win7_x6401 |
| Filename | SetupTools.exe | ||
| Type | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 56 detected (AIDetectMalware, Tasker, malicious, high confidence, score, TjnDroppr, Dapato, S28495190, FakeAlert, unsafe, Save, GenericRXTU, khrgag, DcRat, BNER4NzZWDL, ZPACK, Python, R06CC0DKD23, moderate, Tnega, Detected, ai score=88, 102OIFV, Lazy, Eldorado, R497632, BScope, Nitol, Gencirc, Static AI, Suspicious PE, Tiny) | ||
| md5 | 5ec12277c0679d4761d265dd821f674f | ||
| sha256 | 9006b7c9428d33596cbead41adbde739ce335f5abb10349305a65548fdb30d0f | ||
| ssdeep | 24576:0IiYWseNM1UIVK5mB83y3KNslIafpRxH0959:gbMEN3LIT5g/ | ||
| imphash | a9c887a4f18a3fede2cc29ceea138ed3 | ||
| impfuzzy | 6:HMJqX0umyRwXJxSBS0H5sD4sIWDLb4iPEcn:sJqpRSY58PLPXn | ||
Network IP location
Signature (26cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 56 AntiVirus engines on VirusTotal as malicious |
| watch | A process performed obfuscation on information about the computer or sent it to a remote location indicative of CnC Traffic/Preperations. |
| watch | Appends a known CryptoMix ransomware file extension to files that have been encrypted |
| watch | Attempts to access Bitcoin/ALTCoin wallets |
| watch | Deletes executed files from disk |
| watch | Installs itself for autorun at Windows startup |
| watch | The process powershell.exe wrote an executable file to disk |
| watch | Uses Sysinternals tools in order to add additional command line functionality |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a shortcut to an executable file |
| notice | Creates a suspicious process |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Uses Windows utilities for basic Windows functionality |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Command line console output was observed |
| info | Queries for the computername |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (10cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| info | Is_DotNET_EXE | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Suricata ids
ET HUNTING Telegram API Domain in DNS Lookup
ET INFO TLS Handshake Failure
ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI)
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO TLS Handshake Failure
ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI)
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
PE API
IAT(Import Address Table) Library
msvcrt.dll
0x4c7690 malloc
0x4c7694 memset
0x4c7698 strcmp
0x4c769c strcpy
0x4c76a0 getenv
0x4c76a4 sprintf
0x4c76a8 fopen
0x4c76ac fwrite
0x4c76b0 fclose
0x4c76b4 __argc
0x4c76b8 __argv
0x4c76bc _environ
0x4c76c0 _XcptFilter
0x4c76c4 __set_app_type
0x4c76c8 _controlfp
0x4c76cc __getmainargs
0x4c76d0 exit
shell32.dll
0x4c76d8 ShellExecuteA
kernel32.dll
0x4c76e0 SetUnhandledExceptionFilter
EAT(Export Address Table) is none
msvcrt.dll
0x4c7690 malloc
0x4c7694 memset
0x4c7698 strcmp
0x4c769c strcpy
0x4c76a0 getenv
0x4c76a4 sprintf
0x4c76a8 fopen
0x4c76ac fwrite
0x4c76b0 fclose
0x4c76b4 __argc
0x4c76b8 __argv
0x4c76bc _environ
0x4c76c0 _XcptFilter
0x4c76c4 __set_app_type
0x4c76c8 _controlfp
0x4c76cc __getmainargs
0x4c76d0 exit
shell32.dll
0x4c76d8 ShellExecuteA
kernel32.dll
0x4c76e0 SetUnhandledExceptionFilter
EAT(Export Address Table) is none