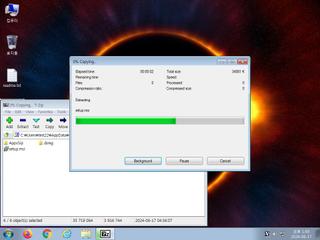
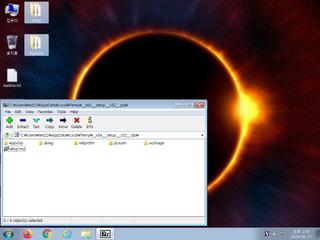
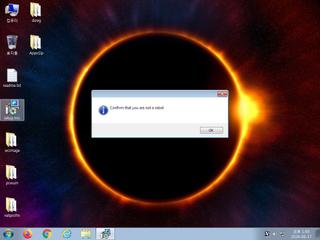
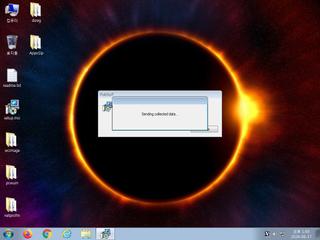
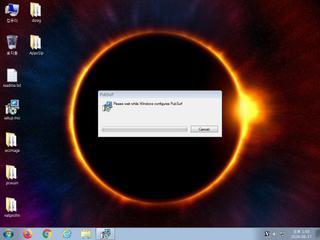
ScreenShot
| Created | 2024.06.17 13:43 | Machine | s1_win7_x6402 |
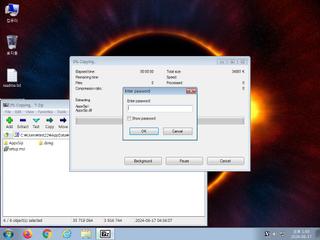
| Filename | __x64___setup___x32__.zip | ||
| Type | Zip archive data, at least v2.0 to extract | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | 7e05adc41fe0d6484c3cc75893991a2f | ||
| sha256 | d8fd991cb180b77de552c9f5b7adbb5748f5d5eeda44cf59be010dbbea9849ed | ||
| ssdeep | 393216:seo8E/4BL/07TM877zWIh9mfztg21vKZFf06OmC57MCoFy84CcVFonmkr:thIs87W29sztg2EtOmC57U884CQomK | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Sends data using the HTTP POST Method |
Rules (1cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | zip_file_format | ZIP file format | binaries (upload) |
Network (5cnts) ?
Suricata ids
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)