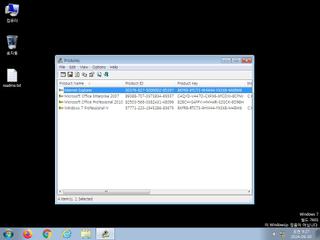
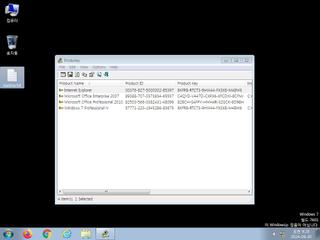
ScreenShot
| Created | 2024.09.30 09:56 | Machine | s1_win7_x6401 |
| Filename | ProduKey.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 15 detected (Unsafe, grayware, confidence, 100%, Nirsoft, PSWTool, ProductKey, A potentially unsafe, Presenoker, CLOUD, HackTool, PassView, ApplicUnwnt@#2nlap14tg2gay, 4WZIH9, MALICIOUS) | ||
| md5 | 8c1c2a6e66e0769380b878a0f3ab6208 | ||
| sha256 | 92392bd287c748f7da0c5ca8aa394f44d6980f0efdd276cf34d7adbd12ddfd6f | ||
| ssdeep | 3072:I5wYR6wga1nr9oH8OCpaCBXq5jK+hs6sTG9e+yO:nEgsFmCCurTYL | ||
| imphash | bb66491ce26787f56037d6cf12eeb987 | ||
| impfuzzy | 48:TRq4UFu/ZJCGHwXXHEHye0OYVoO/I9/R1g1CE0l3TECgS5/1xMG6U05zI7inB9y6:TRq4iC3CGS40OY+cIdRO1QOr/T99WG | ||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| watch | Detects Virtual Machines through their custom firmware |
| watch | File has been identified by 15 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | Checks amount of memory in system |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Queries for the computername |
| info | This executable has a PDB path |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
MPR.dll
0x140015288 WNetOpenEnumA
0x140015290 WNetCloseEnum
0x140015298 WNetEnumResourceA
msvcrt.dll
0x1400155c8 _exit
0x1400155d0 _cexit
0x1400155d8 exit
0x1400155e0 _acmdln
0x1400155e8 _purecall
0x1400155f0 qsort
0x1400155f8 _strlwr
0x140015600 _itoa
0x140015608 _c_exit
0x140015610 strtoul
0x140015618 strchr
0x140015620 _memicmp
0x140015628 strcmp
0x140015630 malloc
0x140015638 ??2@YAPEAX_K@Z
0x140015640 ??3@YAXPEAX@Z
0x140015648 _strnicmp
0x140015650 _XcptFilter
0x140015658 __C_specific_handler
0x140015660 __dllonexit
0x140015668 _onexit
0x140015670 free
0x140015678 _mbsicmp
0x140015680 strrchr
0x140015688 _strcmpi
0x140015690 _stricmp
0x140015698 memcpy
0x1400156a0 strlen
0x1400156a8 atof
0x1400156b0 memcmp
0x1400156b8 atoi
0x1400156c0 memset
0x1400156c8 strcpy
0x1400156d0 strncat
0x1400156d8 sprintf
0x1400156e0 strcat
0x1400156e8 __getmainargs
0x1400156f0 _initterm
0x1400156f8 __setusermatherr
0x140015700 _commode
0x140015708 _fmode
0x140015710 __set_app_type
COMCTL32.dll
0x140015058 ImageList_Create
0x140015060 CreateToolbarEx
0x140015068 None
0x140015070 ImageList_AddMasked
0x140015078 ImageList_SetImageCount
0x140015080 None
0x140015088 ImageList_ReplaceIcon
WS2_32.dll
0x140015550 gethostbyname
0x140015558 WSACleanup
0x140015560 WSAStartup
0x140015568 WSAAsyncSelect
0x140015570 gethostbyaddr
0x140015578 closesocket
0x140015580 WSASetLastError
0x140015588 htons
0x140015590 WSAGetLastError
0x140015598 connect
KERNEL32.dll
0x1400150e0 OpenProcess
0x1400150e8 ResumeThread
0x1400150f0 CreateThread
0x1400150f8 ExitProcess
0x140015100 GetCurrentProcessId
0x140015108 ReadProcessMemory
0x140015110 SetErrorMode
0x140015118 DeleteFileA
0x140015120 GetStdHandle
0x140015128 GetPrivateProfileIntA
0x140015130 GetStartupInfoA
0x140015138 GetModuleFileNameA
0x140015140 FindNextFileA
0x140015148 GetLastError
0x140015150 EnumResourceNamesA
0x140015158 WritePrivateProfileStringA
0x140015160 MultiByteToWideChar
0x140015168 WriteFile
0x140015170 GetDateFormatA
0x140015178 GetWindowsDirectoryA
0x140015180 FindClose
0x140015188 GetSystemDirectoryA
0x140015190 GetTempFileNameA
0x140015198 ReadFile
0x1400151a0 FormatMessageA
0x1400151a8 LoadLibraryExA
0x1400151b0 GetDriveTypeA
0x1400151b8 WideCharToMultiByte
0x1400151c0 GetPrivateProfileStringA
0x1400151c8 Sleep
0x1400151d0 GetCurrentProcess
0x1400151d8 CompareFileTime
0x1400151e0 GetLogicalDrives
0x1400151e8 GetComputerNameA
0x1400151f0 FileTimeToLocalFileTime
0x1400151f8 FileTimeToSystemTime
0x140015200 GetProcAddress
0x140015208 LoadLibraryA
0x140015210 FreeLibrary
0x140015218 GetModuleHandleA
0x140015220 GlobalAlloc
0x140015228 GetVersionExA
0x140015230 GlobalUnlock
0x140015238 GlobalLock
0x140015240 CloseHandle
0x140015248 CreateFileA
0x140015250 GetFileSize
0x140015258 GetTempPathA
0x140015260 GetTimeFormatA
0x140015268 FindFirstFileA
0x140015270 LocalFree
0x140015278 GetFileAttributesA
USER32.dll
0x1400152d8 RegisterWindowMessageA
0x1400152e0 GetMessageA
0x1400152e8 DispatchMessageA
0x1400152f0 GetWindowTextA
0x1400152f8 GetMenuItemInfoA
0x140015300 EndDeferWindowPos
0x140015308 DestroyWindow
0x140015310 CreateDialogParamA
0x140015318 DestroyMenu
0x140015320 GetDlgCtrlID
0x140015328 DialogBoxParamA
0x140015330 LoadStringA
0x140015338 GetFocus
0x140015340 KillTimer
0x140015348 TrackPopupMenu
0x140015350 BeginDeferWindowPos
0x140015358 PostQuitMessage
0x140015360 EnumChildWindows
0x140015368 SetTimer
0x140015370 IsDialogMessageA
0x140015378 DeferWindowPos
0x140015380 LoadCursorA
0x140015388 ShowWindow
0x140015390 SetCursor
0x140015398 ChildWindowFromPoint
0x1400153a0 ReleaseDC
0x1400153a8 GetDC
0x1400153b0 GetSysColorBrush
0x1400153b8 SetDlgItemTextA
0x1400153c0 GetDlgItemTextA
0x1400153c8 SetWindowTextA
0x1400153d0 SendDlgItemMessageA
0x1400153d8 GetDlgItemInt
0x1400153e0 EndDialog
0x1400153e8 GetDlgItem
0x1400153f0 CreateWindowExA
0x1400153f8 SetDlgItemInt
0x140015400 SendMessageA
0x140015408 RegisterClassA
0x140015410 UpdateWindow
0x140015418 GetSystemMetrics
0x140015420 GetWindowRect
0x140015428 PostMessageA
0x140015430 SetMenu
0x140015438 LoadAcceleratorsA
0x140015440 SetWindowPos
0x140015448 DefWindowProcA
0x140015450 TranslateAcceleratorA
0x140015458 MessageBoxA
0x140015460 GetWindowPlacement
0x140015468 LoadImageA
0x140015470 LoadIconA
0x140015478 GetWindowLongA
0x140015480 SetWindowLongA
0x140015488 InvalidateRect
0x140015490 SetFocus
0x140015498 EmptyClipboard
0x1400154a0 GetClassNameA
0x1400154a8 MoveWindow
0x1400154b0 EnableMenuItem
0x1400154b8 CloseClipboard
0x1400154c0 GetSubMenu
0x1400154c8 CheckMenuItem
0x1400154d0 GetMenuItemCount
0x1400154d8 GetClientRect
0x1400154e0 CheckMenuRadioItem
0x1400154e8 GetMenuStringA
0x1400154f0 GetCursorPos
0x1400154f8 SetClipboardData
0x140015500 ModifyMenuA
0x140015508 EnableWindow
0x140015510 GetSysColor
0x140015518 MapWindowPoints
0x140015520 GetMenu
0x140015528 GetParent
0x140015530 OpenClipboard
0x140015538 LoadMenuA
0x140015540 TranslateMessage
GDI32.dll
0x140015098 GetTextExtentPoint32A
0x1400150a0 SetBkColor
0x1400150a8 GetStockObject
0x1400150b0 SetBkMode
0x1400150b8 DeleteObject
0x1400150c0 SetTextColor
0x1400150c8 GetDeviceCaps
0x1400150d0 CreateFontIndirectA
comdlg32.dll
0x1400155a8 GetOpenFileNameA
0x1400155b0 FindTextA
0x1400155b8 GetSaveFileNameA
ADVAPI32.dll
0x140015000 RegQueryInfoKeyA
0x140015008 RegConnectRegistryA
0x140015010 RegLoadKeyA
0x140015018 RegUnLoadKeyA
0x140015020 RegQueryValueExA
0x140015028 RegEnumValueA
0x140015030 RegOpenKeyExA
0x140015038 RegEnumKeyExA
0x140015040 RegDeleteKeyA
0x140015048 RegCloseKey
SHELL32.dll
0x1400152a8 ShellExecuteA
0x1400152b0 SHGetMalloc
0x1400152b8 SHGetPathFromIDListA
0x1400152c0 SHBrowseForFolderA
0x1400152c8 ShellExecuteExA
ole32.dll
0x140015720 CoInitialize
0x140015728 CoUninitialize
EAT(Export Address Table) is none
MPR.dll
0x140015288 WNetOpenEnumA
0x140015290 WNetCloseEnum
0x140015298 WNetEnumResourceA
msvcrt.dll
0x1400155c8 _exit
0x1400155d0 _cexit
0x1400155d8 exit
0x1400155e0 _acmdln
0x1400155e8 _purecall
0x1400155f0 qsort
0x1400155f8 _strlwr
0x140015600 _itoa
0x140015608 _c_exit
0x140015610 strtoul
0x140015618 strchr
0x140015620 _memicmp
0x140015628 strcmp
0x140015630 malloc
0x140015638 ??2@YAPEAX_K@Z
0x140015640 ??3@YAXPEAX@Z
0x140015648 _strnicmp
0x140015650 _XcptFilter
0x140015658 __C_specific_handler
0x140015660 __dllonexit
0x140015668 _onexit
0x140015670 free
0x140015678 _mbsicmp
0x140015680 strrchr
0x140015688 _strcmpi
0x140015690 _stricmp
0x140015698 memcpy
0x1400156a0 strlen
0x1400156a8 atof
0x1400156b0 memcmp
0x1400156b8 atoi
0x1400156c0 memset
0x1400156c8 strcpy
0x1400156d0 strncat
0x1400156d8 sprintf
0x1400156e0 strcat
0x1400156e8 __getmainargs
0x1400156f0 _initterm
0x1400156f8 __setusermatherr
0x140015700 _commode
0x140015708 _fmode
0x140015710 __set_app_type
COMCTL32.dll
0x140015058 ImageList_Create
0x140015060 CreateToolbarEx
0x140015068 None
0x140015070 ImageList_AddMasked
0x140015078 ImageList_SetImageCount
0x140015080 None
0x140015088 ImageList_ReplaceIcon
WS2_32.dll
0x140015550 gethostbyname
0x140015558 WSACleanup
0x140015560 WSAStartup
0x140015568 WSAAsyncSelect
0x140015570 gethostbyaddr
0x140015578 closesocket
0x140015580 WSASetLastError
0x140015588 htons
0x140015590 WSAGetLastError
0x140015598 connect
KERNEL32.dll
0x1400150e0 OpenProcess
0x1400150e8 ResumeThread
0x1400150f0 CreateThread
0x1400150f8 ExitProcess
0x140015100 GetCurrentProcessId
0x140015108 ReadProcessMemory
0x140015110 SetErrorMode
0x140015118 DeleteFileA
0x140015120 GetStdHandle
0x140015128 GetPrivateProfileIntA
0x140015130 GetStartupInfoA
0x140015138 GetModuleFileNameA
0x140015140 FindNextFileA
0x140015148 GetLastError
0x140015150 EnumResourceNamesA
0x140015158 WritePrivateProfileStringA
0x140015160 MultiByteToWideChar
0x140015168 WriteFile
0x140015170 GetDateFormatA
0x140015178 GetWindowsDirectoryA
0x140015180 FindClose
0x140015188 GetSystemDirectoryA
0x140015190 GetTempFileNameA
0x140015198 ReadFile
0x1400151a0 FormatMessageA
0x1400151a8 LoadLibraryExA
0x1400151b0 GetDriveTypeA
0x1400151b8 WideCharToMultiByte
0x1400151c0 GetPrivateProfileStringA
0x1400151c8 Sleep
0x1400151d0 GetCurrentProcess
0x1400151d8 CompareFileTime
0x1400151e0 GetLogicalDrives
0x1400151e8 GetComputerNameA
0x1400151f0 FileTimeToLocalFileTime
0x1400151f8 FileTimeToSystemTime
0x140015200 GetProcAddress
0x140015208 LoadLibraryA
0x140015210 FreeLibrary
0x140015218 GetModuleHandleA
0x140015220 GlobalAlloc
0x140015228 GetVersionExA
0x140015230 GlobalUnlock
0x140015238 GlobalLock
0x140015240 CloseHandle
0x140015248 CreateFileA
0x140015250 GetFileSize
0x140015258 GetTempPathA
0x140015260 GetTimeFormatA
0x140015268 FindFirstFileA
0x140015270 LocalFree
0x140015278 GetFileAttributesA
USER32.dll
0x1400152d8 RegisterWindowMessageA
0x1400152e0 GetMessageA
0x1400152e8 DispatchMessageA
0x1400152f0 GetWindowTextA
0x1400152f8 GetMenuItemInfoA
0x140015300 EndDeferWindowPos
0x140015308 DestroyWindow
0x140015310 CreateDialogParamA
0x140015318 DestroyMenu
0x140015320 GetDlgCtrlID
0x140015328 DialogBoxParamA
0x140015330 LoadStringA
0x140015338 GetFocus
0x140015340 KillTimer
0x140015348 TrackPopupMenu
0x140015350 BeginDeferWindowPos
0x140015358 PostQuitMessage
0x140015360 EnumChildWindows
0x140015368 SetTimer
0x140015370 IsDialogMessageA
0x140015378 DeferWindowPos
0x140015380 LoadCursorA
0x140015388 ShowWindow
0x140015390 SetCursor
0x140015398 ChildWindowFromPoint
0x1400153a0 ReleaseDC
0x1400153a8 GetDC
0x1400153b0 GetSysColorBrush
0x1400153b8 SetDlgItemTextA
0x1400153c0 GetDlgItemTextA
0x1400153c8 SetWindowTextA
0x1400153d0 SendDlgItemMessageA
0x1400153d8 GetDlgItemInt
0x1400153e0 EndDialog
0x1400153e8 GetDlgItem
0x1400153f0 CreateWindowExA
0x1400153f8 SetDlgItemInt
0x140015400 SendMessageA
0x140015408 RegisterClassA
0x140015410 UpdateWindow
0x140015418 GetSystemMetrics
0x140015420 GetWindowRect
0x140015428 PostMessageA
0x140015430 SetMenu
0x140015438 LoadAcceleratorsA
0x140015440 SetWindowPos
0x140015448 DefWindowProcA
0x140015450 TranslateAcceleratorA
0x140015458 MessageBoxA
0x140015460 GetWindowPlacement
0x140015468 LoadImageA
0x140015470 LoadIconA
0x140015478 GetWindowLongA
0x140015480 SetWindowLongA
0x140015488 InvalidateRect
0x140015490 SetFocus
0x140015498 EmptyClipboard
0x1400154a0 GetClassNameA
0x1400154a8 MoveWindow
0x1400154b0 EnableMenuItem
0x1400154b8 CloseClipboard
0x1400154c0 GetSubMenu
0x1400154c8 CheckMenuItem
0x1400154d0 GetMenuItemCount
0x1400154d8 GetClientRect
0x1400154e0 CheckMenuRadioItem
0x1400154e8 GetMenuStringA
0x1400154f0 GetCursorPos
0x1400154f8 SetClipboardData
0x140015500 ModifyMenuA
0x140015508 EnableWindow
0x140015510 GetSysColor
0x140015518 MapWindowPoints
0x140015520 GetMenu
0x140015528 GetParent
0x140015530 OpenClipboard
0x140015538 LoadMenuA
0x140015540 TranslateMessage
GDI32.dll
0x140015098 GetTextExtentPoint32A
0x1400150a0 SetBkColor
0x1400150a8 GetStockObject
0x1400150b0 SetBkMode
0x1400150b8 DeleteObject
0x1400150c0 SetTextColor
0x1400150c8 GetDeviceCaps
0x1400150d0 CreateFontIndirectA
comdlg32.dll
0x1400155a8 GetOpenFileNameA
0x1400155b0 FindTextA
0x1400155b8 GetSaveFileNameA
ADVAPI32.dll
0x140015000 RegQueryInfoKeyA
0x140015008 RegConnectRegistryA
0x140015010 RegLoadKeyA
0x140015018 RegUnLoadKeyA
0x140015020 RegQueryValueExA
0x140015028 RegEnumValueA
0x140015030 RegOpenKeyExA
0x140015038 RegEnumKeyExA
0x140015040 RegDeleteKeyA
0x140015048 RegCloseKey
SHELL32.dll
0x1400152a8 ShellExecuteA
0x1400152b0 SHGetMalloc
0x1400152b8 SHGetPathFromIDListA
0x1400152c0 SHBrowseForFolderA
0x1400152c8 ShellExecuteExA
ole32.dll
0x140015720 CoInitialize
0x140015728 CoUninitialize
EAT(Export Address Table) is none