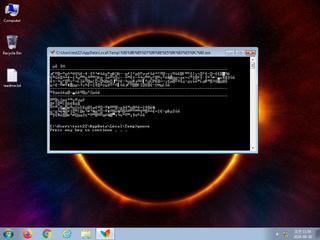
ScreenShot
| Created | 2024.09.30 12:02 | Machine | s1_win7_x6403 |
| Filename | %E6%B8%85%E7%90%86%E5%9E%83%E5%9C%BE.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 26 detected (cKW@t5uwqPpiB, unsafe, Attribute, HighConfidence, YzY0Onro+1sQRUHo, Proxy, malicious, high, score, ai score=80, Static AI, Malicious PE, susgen) | ||
| md5 | f004f01e7ad572da2ea0b7f7b377f203 | ||
| sha256 | 7c64671a310a721ac191f149b5c3b044482e3b2d2fa6266d7f7b41d268113d01 | ||
| ssdeep | 768:Wz+VZ1p/ija+1I2UqBg6Q4sNbEMLFAmC7+8G:vVZfqamsNbDF0i | ||
| imphash | 423f01e9d2b066cd1b31541d1211d4ba | ||
| impfuzzy | 24:F1w2w+4Q/wFFzXaOovsgO0MZrjmu1yfTu+POovYbOR:z8+4Q/WXdngO0MZim/bOR | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 26 AntiVirus engines on VirusTotal as malicious |
| notice | Creates a suspicious process |
| notice | Creates executable files on the filesystem |
| info | Command line console output was observed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Emotet_2_Zero | Win32 Trojan Emotet | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
advapi32.dll
0x40a168 RegQueryValueExA
0x40a16c RegOpenKeyExA
0x40a170 RegCloseKey
user32.dll
0x40a178 GetKeyboardType
0x40a17c DestroyWindow
0x40a180 MessageBoxA
kernel32.dll
0x40a188 GetACP
0x40a18c Sleep
0x40a190 VirtualFree
0x40a194 VirtualAlloc
0x40a198 GetTickCount
0x40a19c QueryPerformanceCounter
0x40a1a0 GetCurrentThreadId
0x40a1a4 VirtualQuery
0x40a1a8 GetStartupInfoA
0x40a1ac GetCommandLineA
0x40a1b0 FreeLibrary
0x40a1b4 ExitProcess
0x40a1b8 WriteFile
0x40a1bc UnhandledExceptionFilter
0x40a1c0 RtlUnwind
0x40a1c4 RaiseException
0x40a1c8 GetStdHandle
kernel32.dll
0x40a1d0 TlsSetValue
0x40a1d4 TlsGetValue
0x40a1d8 LocalAlloc
0x40a1dc GetModuleHandleA
user32.dll
0x40a1e4 CharPrevA
kernel32.dll
0x40a1ec WriteFile
0x40a1f0 WaitForSingleObject
0x40a1f4 SizeofResource
0x40a1f8 SetFileAttributesA
0x40a1fc SetEnvironmentVariableA
0x40a200 LockResource
0x40a204 LoadResource
0x40a208 GetWindowsDirectoryA
0x40a20c GetFullPathNameA
0x40a210 GetFileAttributesA
0x40a214 GetExitCodeProcess
0x40a218 GetEnvironmentVariableA
0x40a21c GetCurrentProcessId
0x40a220 GetCommandLineA
0x40a224 FreeResource
0x40a228 FreeLibrary
0x40a22c FindResourceA
0x40a230 DeleteFileA
0x40a234 CreateProcessA
0x40a238 CreateFileA
0x40a23c CloseHandle
EAT(Export Address Table) is none
advapi32.dll
0x40a168 RegQueryValueExA
0x40a16c RegOpenKeyExA
0x40a170 RegCloseKey
user32.dll
0x40a178 GetKeyboardType
0x40a17c DestroyWindow
0x40a180 MessageBoxA
kernel32.dll
0x40a188 GetACP
0x40a18c Sleep
0x40a190 VirtualFree
0x40a194 VirtualAlloc
0x40a198 GetTickCount
0x40a19c QueryPerformanceCounter
0x40a1a0 GetCurrentThreadId
0x40a1a4 VirtualQuery
0x40a1a8 GetStartupInfoA
0x40a1ac GetCommandLineA
0x40a1b0 FreeLibrary
0x40a1b4 ExitProcess
0x40a1b8 WriteFile
0x40a1bc UnhandledExceptionFilter
0x40a1c0 RtlUnwind
0x40a1c4 RaiseException
0x40a1c8 GetStdHandle
kernel32.dll
0x40a1d0 TlsSetValue
0x40a1d4 TlsGetValue
0x40a1d8 LocalAlloc
0x40a1dc GetModuleHandleA
user32.dll
0x40a1e4 CharPrevA
kernel32.dll
0x40a1ec WriteFile
0x40a1f0 WaitForSingleObject
0x40a1f4 SizeofResource
0x40a1f8 SetFileAttributesA
0x40a1fc SetEnvironmentVariableA
0x40a200 LockResource
0x40a204 LoadResource
0x40a208 GetWindowsDirectoryA
0x40a20c GetFullPathNameA
0x40a210 GetFileAttributesA
0x40a214 GetExitCodeProcess
0x40a218 GetEnvironmentVariableA
0x40a21c GetCurrentProcessId
0x40a220 GetCommandLineA
0x40a224 FreeResource
0x40a228 FreeLibrary
0x40a22c FindResourceA
0x40a230 DeleteFileA
0x40a234 CreateProcessA
0x40a238 CreateFileA
0x40a23c CloseHandle
EAT(Export Address Table) is none