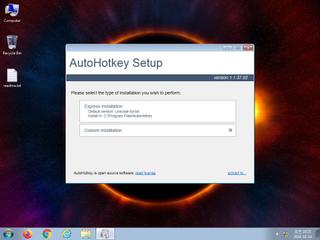
ScreenShot
| Created | 2024.10.14 10:42 | Machine | s1_win7_x6403 |
| Filename | AutoHotkey_1.1.37.02_setup.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | |||
| VT API (file) | 8 detected (Unsafe, Malicious, BuckBit, kpuuxe, Static AI, Suspicious SFX, Disco, susgen) | ||
| md5 | c2e8062052bb2b25d4951b78ba9a5e73 | ||
| sha256 | 49a48e879f7480238d2fe17520ac19afe83685aac0b886719f9e1eac818b75cc | ||
| ssdeep | 98304:m7EROaI2yEbVidvdahm6QAxuE4iLqmzLdtte96g:m4FyMVq4og4iLqmNqMg | ||
| imphash | fa4d5c869351014d1ce952f2833a7558 | ||
| impfuzzy | 12:SD5B+5QGu4Gv+GXRzGy5yJqhR9F38dPkO4qgOsZB4lJZVljR:SVB+5T0v+GdMqhR9F30kOxgO8B4X9jR | ||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Creates executable files on the filesystem |
| notice | Drops an executable to the user AppData folder |
| notice | File has been identified by 8 AntiVirus engines on VirusTotal as malicious |
| info | Checks amount of memory in system |
| info | The executable uses a known packer |
Rules (13cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | chm_file_format | chm file format | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
USER32.dll
0x4070d0 MessageBoxA
SHELL32.dll
0x4070c8 ShellExecuteExW
MSVCRT.dll
0x407064 _controlfp
0x407068 _except_handler3
0x40706c __set_app_type
0x407070 __p__fmode
0x407074 __p__commode
0x407078 _adjust_fdiv
0x40707c __setusermatherr
0x407080 _initterm
0x407084 __getmainargs
0x407088 _acmdln
0x40708c exit
0x407090 _XcptFilter
0x407094 _exit
0x407098 memcpy
0x40709c free
0x4070a0 malloc
0x4070a4 wcscmp
0x4070a8 memcmp
0x4070ac memmove
0x4070b0 strlen
0x4070b4 wcslen
0x4070b8 wcscpy
0x4070bc wcscat
0x4070c0 memset
KERNEL32.dll
0x407000 GetStartupInfoA
0x407004 GetModuleHandleA
0x407008 SetFilePointer
0x40700c WriteFile
0x407010 ReadFile
0x407014 CreateFileW
0x407018 DeleteFileW
0x40701c FindNextFileW
0x407020 RemoveDirectoryW
0x407024 FindFirstFileW
0x407028 FindClose
0x40702c GetModuleFileNameW
0x407030 GetCommandLineW
0x407034 GetTempPathW
0x407038 GetCurrentThreadId
0x40703c GetTickCount
0x407040 GetCurrentProcessId
0x407044 CreateDirectoryW
0x407048 GetLastError
0x40704c SetFileTime
0x407050 SetFileAttributesW
0x407054 CreateProcessW
0x407058 CloseHandle
0x40705c WaitForSingleObject
EAT(Export Address Table) is none
USER32.dll
0x4070d0 MessageBoxA
SHELL32.dll
0x4070c8 ShellExecuteExW
MSVCRT.dll
0x407064 _controlfp
0x407068 _except_handler3
0x40706c __set_app_type
0x407070 __p__fmode
0x407074 __p__commode
0x407078 _adjust_fdiv
0x40707c __setusermatherr
0x407080 _initterm
0x407084 __getmainargs
0x407088 _acmdln
0x40708c exit
0x407090 _XcptFilter
0x407094 _exit
0x407098 memcpy
0x40709c free
0x4070a0 malloc
0x4070a4 wcscmp
0x4070a8 memcmp
0x4070ac memmove
0x4070b0 strlen
0x4070b4 wcslen
0x4070b8 wcscpy
0x4070bc wcscat
0x4070c0 memset
KERNEL32.dll
0x407000 GetStartupInfoA
0x407004 GetModuleHandleA
0x407008 SetFilePointer
0x40700c WriteFile
0x407010 ReadFile
0x407014 CreateFileW
0x407018 DeleteFileW
0x40701c FindNextFileW
0x407020 RemoveDirectoryW
0x407024 FindFirstFileW
0x407028 FindClose
0x40702c GetModuleFileNameW
0x407030 GetCommandLineW
0x407034 GetTempPathW
0x407038 GetCurrentThreadId
0x40703c GetTickCount
0x407040 GetCurrentProcessId
0x407044 CreateDirectoryW
0x407048 GetLastError
0x40704c SetFileTime
0x407050 SetFileAttributesW
0x407054 CreateProcessW
0x407058 CloseHandle
0x40705c WaitForSingleObject
EAT(Export Address Table) is none