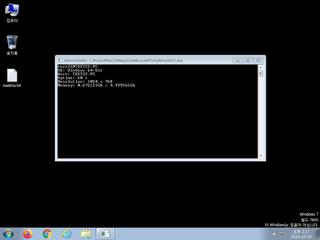
ScreenShot
| Created | 2024.10.15 14:20 | Machine | s1_win7_x6401 |
| Filename | neofetch.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 53 detected (AIDetectMalware, Malicious, score, Artemis, GenericKD, Unsafe, Vxws, confidence, Attribute, HighConfidence, high confidence, a variant of Generik, KRBHCYM, DropperX, xycxfp, CLOUD, Nekark, znxkz, MulDrop28, Detected, Multiverze, Chgt, R002H09J324, Gencirc, Dc3d6E3kNTY, susgen, PossibleThreat, PALLAS) | ||
| md5 | d6b10fe0f03dc8bdf3cd5ec9e4e3d305 | ||
| sha256 | d0786c4c6c967ba28706f92402a6151fc509b010e1d2a18f19118548bbe40393 | ||
| ssdeep | 49152:y62fe9dW85/6/+w0u9RQHNgB5ikccS6C8MXDTQom15:86W85/6/+sIga8MXDTQom15 | ||
| imphash | 52dee48e9c20d673929d8b1b29a57a87 | ||
| impfuzzy | 48:mbDlUM39ymYeF4+2R4I9bnXiX1PnvKlJJGZq5gQ61vm/Ghyq1J6urz/:UD2M3omX4HR4I9bnXiX1PviJJGsyQM7R | ||
Network IP location
Signature (19cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 53 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| watch | Creates a suspicious Powershell process |
| watch | Installs itself for autorun at Windows startup |
| watch | The process powershell.exe wrote an executable file to disk |
| watch | Uses Sysinternals tools in order to add additional command line functionality |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a shortcut to an executable file |
| notice | Creates a suspicious process |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
| notice | Uses Windows utilities for basic Windows functionality |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Queries for the computername |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | PowerShell | PowerShell script | scripts |
Suricata ids
ET INFO Executable Download from dotted-quad Host
ET HUNTING curl User-Agent to Dotted Quad
ET INFO Packed Executable Download
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET HUNTING curl User-Agent to Dotted Quad
ET INFO Packed Executable Download
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x1400ef500 GetTokenInformation
0x1400ef508 OpenProcessToken
KERNEL32.dll
0x1400ef518 AddVectoredExceptionHandler
0x1400ef520 CloseHandle
0x1400ef528 CreateEventA
0x1400ef530 CreateSemaphoreA
0x1400ef538 DeleteCriticalSection
0x1400ef540 DuplicateHandle
0x1400ef548 EnterCriticalSection
0x1400ef550 FormatMessageA
0x1400ef558 GetComputerNameA
0x1400ef560 GetCurrentProcess
0x1400ef568 GetCurrentProcessId
0x1400ef570 GetCurrentThread
0x1400ef578 GetCurrentThreadId
0x1400ef580 GetHandleInformation
0x1400ef588 GetLastError
0x1400ef590 GetModuleHandleW
0x1400ef598 GetProcAddress
0x1400ef5a0 GetProcessAffinityMask
0x1400ef5a8 GetSystemTimeAsFileTime
0x1400ef5b0 GetThreadContext
0x1400ef5b8 GetThreadPriority
0x1400ef5c0 GetTickCount64
0x1400ef5c8 GlobalMemoryStatusEx
0x1400ef5d0 InitializeCriticalSection
0x1400ef5d8 IsDBCSLeadByteEx
0x1400ef5e0 IsDebuggerPresent
0x1400ef5e8 LeaveCriticalSection
0x1400ef5f0 LoadLibraryW
0x1400ef5f8 LocalFree
0x1400ef600 MultiByteToWideChar
0x1400ef608 OpenProcess
0x1400ef610 OutputDebugStringA
0x1400ef618 RaiseException
0x1400ef620 ReleaseSemaphore
0x1400ef628 RemoveVectoredExceptionHandler
0x1400ef630 ResetEvent
0x1400ef638 ResumeThread
0x1400ef640 RtlCaptureContext
0x1400ef648 RtlLookupFunctionEntry
0x1400ef650 RtlUnwindEx
0x1400ef658 RtlVirtualUnwind
0x1400ef660 SetEvent
0x1400ef668 SetLastError
0x1400ef670 SetProcessAffinityMask
0x1400ef678 SetThreadContext
0x1400ef680 SetThreadPriority
0x1400ef688 SetUnhandledExceptionFilter
0x1400ef690 Sleep
0x1400ef698 SuspendThread
0x1400ef6a0 TlsAlloc
0x1400ef6a8 TlsGetValue
0x1400ef6b0 TlsSetValue
0x1400ef6b8 TryEnterCriticalSection
0x1400ef6c0 VirtualProtect
0x1400ef6c8 VirtualQuery
0x1400ef6d0 WaitForMultipleObjects
0x1400ef6d8 WaitForSingleObject
0x1400ef6e0 WideCharToMultiByte
0x1400ef6e8 __C_specific_handler
msvcrt.dll
0x1400ef6f8 ___lc_codepage_func
0x1400ef700 ___mb_cur_max_func
0x1400ef708 __getmainargs
0x1400ef710 __initenv
0x1400ef718 __iob_func
0x1400ef720 __set_app_type
0x1400ef728 __setusermatherr
0x1400ef730 _amsg_exit
0x1400ef738 _beginthreadex
0x1400ef740 _cexit
0x1400ef748 _commode
0x1400ef750 _errno
0x1400ef758 _endthreadex
0x1400ef760 _filelengthi64
0x1400ef768 _fileno
0x1400ef770 _fmode
0x1400ef778 _fstat64
0x1400ef780 _initterm
0x1400ef788 _lseeki64
0x1400ef790 fread
0x1400ef798 free
0x1400ef7a0 fsetpos
0x1400ef7a8 memchr
0x1400ef7b0 memcmp
0x1400ef7b8 memcpy
0x1400ef7c0 memmove
0x1400ef7c8 memset
0x1400ef7d0 printf
0x1400ef7d8 _onexit
0x1400ef7e0 _ultoa
0x1400ef7e8 _setjmp
0x1400ef7f0 _wfopen
0x1400ef7f8 abort
0x1400ef800 calloc
0x1400ef808 exit
0x1400ef810 fclose
0x1400ef818 fflush
0x1400ef820 fgetpos
0x1400ef828 fopen
0x1400ef830 fprintf
0x1400ef838 fputc
0x1400ef840 fputs
0x1400ef848 fwrite
0x1400ef850 getc
0x1400ef858 getenv
0x1400ef860 getwc
0x1400ef868 iswctype
0x1400ef870 localeconv
0x1400ef878 longjmp
0x1400ef880 malloc
0x1400ef888 putc
0x1400ef890 putwc
0x1400ef898 realloc
0x1400ef8a0 setlocale
0x1400ef8a8 setvbuf
0x1400ef8b0 signal
0x1400ef8b8 strchr
0x1400ef8c0 strcmp
0x1400ef8c8 strcoll
0x1400ef8d0 strerror
0x1400ef8d8 strftime
0x1400ef8e0 strlen
0x1400ef8e8 strncmp
0x1400ef8f0 strtoul
0x1400ef8f8 strxfrm
0x1400ef900 system
0x1400ef908 towlower
0x1400ef910 towupper
0x1400ef918 ungetc
0x1400ef920 ungetwc
0x1400ef928 vfprintf
0x1400ef930 wcscoll
0x1400ef938 wcsftime
0x1400ef940 wcslen
0x1400ef948 wcsxfrm
0x1400ef950 _write
0x1400ef958 _strdup
0x1400ef960 _read
0x1400ef968 _fileno
0x1400ef970 _fdopen
USER32.dll
0x1400ef980 GetDesktopWindow
0x1400ef988 GetWindowRect
EAT(Export Address Table) is none
ADVAPI32.dll
0x1400ef500 GetTokenInformation
0x1400ef508 OpenProcessToken
KERNEL32.dll
0x1400ef518 AddVectoredExceptionHandler
0x1400ef520 CloseHandle
0x1400ef528 CreateEventA
0x1400ef530 CreateSemaphoreA
0x1400ef538 DeleteCriticalSection
0x1400ef540 DuplicateHandle
0x1400ef548 EnterCriticalSection
0x1400ef550 FormatMessageA
0x1400ef558 GetComputerNameA
0x1400ef560 GetCurrentProcess
0x1400ef568 GetCurrentProcessId
0x1400ef570 GetCurrentThread
0x1400ef578 GetCurrentThreadId
0x1400ef580 GetHandleInformation
0x1400ef588 GetLastError
0x1400ef590 GetModuleHandleW
0x1400ef598 GetProcAddress
0x1400ef5a0 GetProcessAffinityMask
0x1400ef5a8 GetSystemTimeAsFileTime
0x1400ef5b0 GetThreadContext
0x1400ef5b8 GetThreadPriority
0x1400ef5c0 GetTickCount64
0x1400ef5c8 GlobalMemoryStatusEx
0x1400ef5d0 InitializeCriticalSection
0x1400ef5d8 IsDBCSLeadByteEx
0x1400ef5e0 IsDebuggerPresent
0x1400ef5e8 LeaveCriticalSection
0x1400ef5f0 LoadLibraryW
0x1400ef5f8 LocalFree
0x1400ef600 MultiByteToWideChar
0x1400ef608 OpenProcess
0x1400ef610 OutputDebugStringA
0x1400ef618 RaiseException
0x1400ef620 ReleaseSemaphore
0x1400ef628 RemoveVectoredExceptionHandler
0x1400ef630 ResetEvent
0x1400ef638 ResumeThread
0x1400ef640 RtlCaptureContext
0x1400ef648 RtlLookupFunctionEntry
0x1400ef650 RtlUnwindEx
0x1400ef658 RtlVirtualUnwind
0x1400ef660 SetEvent
0x1400ef668 SetLastError
0x1400ef670 SetProcessAffinityMask
0x1400ef678 SetThreadContext
0x1400ef680 SetThreadPriority
0x1400ef688 SetUnhandledExceptionFilter
0x1400ef690 Sleep
0x1400ef698 SuspendThread
0x1400ef6a0 TlsAlloc
0x1400ef6a8 TlsGetValue
0x1400ef6b0 TlsSetValue
0x1400ef6b8 TryEnterCriticalSection
0x1400ef6c0 VirtualProtect
0x1400ef6c8 VirtualQuery
0x1400ef6d0 WaitForMultipleObjects
0x1400ef6d8 WaitForSingleObject
0x1400ef6e0 WideCharToMultiByte
0x1400ef6e8 __C_specific_handler
msvcrt.dll
0x1400ef6f8 ___lc_codepage_func
0x1400ef700 ___mb_cur_max_func
0x1400ef708 __getmainargs
0x1400ef710 __initenv
0x1400ef718 __iob_func
0x1400ef720 __set_app_type
0x1400ef728 __setusermatherr
0x1400ef730 _amsg_exit
0x1400ef738 _beginthreadex
0x1400ef740 _cexit
0x1400ef748 _commode
0x1400ef750 _errno
0x1400ef758 _endthreadex
0x1400ef760 _filelengthi64
0x1400ef768 _fileno
0x1400ef770 _fmode
0x1400ef778 _fstat64
0x1400ef780 _initterm
0x1400ef788 _lseeki64
0x1400ef790 fread
0x1400ef798 free
0x1400ef7a0 fsetpos
0x1400ef7a8 memchr
0x1400ef7b0 memcmp
0x1400ef7b8 memcpy
0x1400ef7c0 memmove
0x1400ef7c8 memset
0x1400ef7d0 printf
0x1400ef7d8 _onexit
0x1400ef7e0 _ultoa
0x1400ef7e8 _setjmp
0x1400ef7f0 _wfopen
0x1400ef7f8 abort
0x1400ef800 calloc
0x1400ef808 exit
0x1400ef810 fclose
0x1400ef818 fflush
0x1400ef820 fgetpos
0x1400ef828 fopen
0x1400ef830 fprintf
0x1400ef838 fputc
0x1400ef840 fputs
0x1400ef848 fwrite
0x1400ef850 getc
0x1400ef858 getenv
0x1400ef860 getwc
0x1400ef868 iswctype
0x1400ef870 localeconv
0x1400ef878 longjmp
0x1400ef880 malloc
0x1400ef888 putc
0x1400ef890 putwc
0x1400ef898 realloc
0x1400ef8a0 setlocale
0x1400ef8a8 setvbuf
0x1400ef8b0 signal
0x1400ef8b8 strchr
0x1400ef8c0 strcmp
0x1400ef8c8 strcoll
0x1400ef8d0 strerror
0x1400ef8d8 strftime
0x1400ef8e0 strlen
0x1400ef8e8 strncmp
0x1400ef8f0 strtoul
0x1400ef8f8 strxfrm
0x1400ef900 system
0x1400ef908 towlower
0x1400ef910 towupper
0x1400ef918 ungetc
0x1400ef920 ungetwc
0x1400ef928 vfprintf
0x1400ef930 wcscoll
0x1400ef938 wcsftime
0x1400ef940 wcslen
0x1400ef948 wcsxfrm
0x1400ef950 _write
0x1400ef958 _strdup
0x1400ef960 _read
0x1400ef968 _fileno
0x1400ef970 _fdopen
USER32.dll
0x1400ef980 GetDesktopWindow
0x1400ef988 GetWindowRect
EAT(Export Address Table) is none