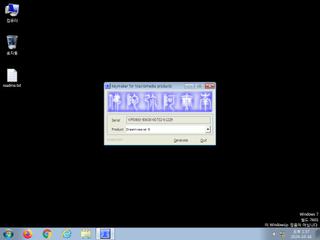
ScreenShot
| Created | 2024.10.16 13:40 | Machine | s1_win7_x6401 |
| Filename | keygen.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 33 detected (AIDetectMalware, Unsafe, Vopt, grayware, confidence, 100%, malicious, moderate confidence, IH potentially unsafe, Tool, Acronis, Viking, Detected, Presenoker, Malware@#30poc4x7fwuf9, HackTool, Eldorado, R23827, CrackTool, susgen, Shifu) | ||
| md5 | 3bd08acd4079d75290eb1fb0c34ff700 | ||
| sha256 | 4d3d060d8ec7089acfb4ba233d6f2a00a910503be648709a97714c84a80cccd8 | ||
| ssdeep | 768:PnnRvIebZmzgaCbKvyyEhI1lA8y2RsYAExUnzVBN5Rt4v94MtCZoSW:/nRAG6DvyyE+1lZy2RhAmUnty6MtTSW | ||
| imphash | 5ef21414f390ccd1ad383d2c569cd765 | ||
| impfuzzy | 6:dBJAEHGDvZ/GlzlrXWvIaJvrJ9N1G73T7d5eS2beuf:VA/DvZOzaJvrt1qj7PeSjuf | ||
Network IP location
Signature (6cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 33 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is compressed using UPX |
| info | Checks amount of memory in system |
| info | The executable uses a known packer |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.DLL
0x42a30c LoadLibraryA
0x42a310 GetProcAddress
0x42a314 ExitProcess
COMCTL32.dll
0x42a31c _TrackMouseEvent
GDI32.dll
0x42a324 BitBlt
MFC42.DLL
0x42a32c None
MSIMG32.dll
0x42a334 TransparentBlt
MSVCP60.dll
0x42a33c ?_Xran@std@@YAXXZ
MSVCRT.dll
0x42a344 rand
SHELL32.dll
0x42a34c ShellExecuteExA
USER32.dll
0x42a354 GetDC
WINMM.dll
0x42a35c PlaySoundA
EAT(Export Address Table) is none
KERNEL32.DLL
0x42a30c LoadLibraryA
0x42a310 GetProcAddress
0x42a314 ExitProcess
COMCTL32.dll
0x42a31c _TrackMouseEvent
GDI32.dll
0x42a324 BitBlt
MFC42.DLL
0x42a32c None
MSIMG32.dll
0x42a334 TransparentBlt
MSVCP60.dll
0x42a33c ?_Xran@std@@YAXXZ
MSVCRT.dll
0x42a344 rand
SHELL32.dll
0x42a34c ShellExecuteExA
USER32.dll
0x42a354 GetDC
WINMM.dll
0x42a35c PlaySoundA
EAT(Export Address Table) is none