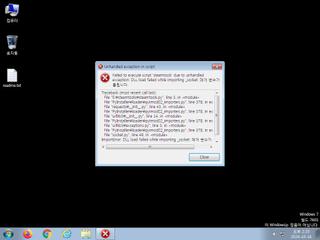
ScreenShot
| Created | 2024.10.16 14:30 | Machine | s1_win7_x6401 |
| Filename | 1174180.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 41 detected (AIDetectMalware, Malicious, score, GenericKD, Unsafe, Save, confidence, high confidence, GenCBL, DangerousSig, MalCert, CLASSIC, RKIT, ecpsx, moderate, BadCert, Detected, GrayWare, SafeGuard, Kuping, D0CNKZ, Noobyprotect, Eldorado, Krypt, R014H0CJF24) | ||
| md5 | 110a014684ddaaf25e6b81d798d7ae8f | ||
| sha256 | 5df0c8a02789c6833a07bfbbff5a02b161201c1e55e9b00af59e7f1684e193b9 | ||
| ssdeep | 196608:e/qaArDbenvmte2qUzCsXDjDyfndJolpPgToa10/UFOnJwDIU7/x:e/govmg2qaCEDAJ83a10MsEISZ | ||
| imphash | 12b2bc20d7737a83639913d36501fd39 | ||
| impfuzzy | 3:DyW5NdKeYXndLsSNKemyNAWcGC6eJTaZn23SHfW8MLnA1MJuE9zbW7uRAn:1dKRNLHzbCnTaZn2QR7ILVbGeA | ||
Network IP location
Signature (10cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 41 AntiVirus engines on VirusTotal as malicious |
| danger | Executed a process and injected code into it |
| watch | Communicates with host for which no DNS query was performed |
| notice | A process attempted to delay the analysis task. |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (19cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Gen_1_0904B0_Zero | Win32 Trojan Emotet | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | zip_file_format | ZIP file format | binaries (download) |
PE API
IAT(Import Address Table) Library
USER32.dll
0x1401b41b6 CreateWindowExW
COMCTL32.dll
0x1401b41ce None
KERNEL32.dll
0x1401b41e6 GetACP
ADVAPI32.dll
0x1401b41fe OpenProcessToken
GDI32.dll
0x1401b4216 SelectObject
IPHLPAPI.DLL
0x1401b422e GetInterfaceInfo
msvcrt.dll
0x1401b4246 _wcsnicmp
PSAPI.DLL
0x1401b425e GetMappedFileNameW
SHELL32.dll
0x1401b4276 SHGetFolderPathW
EAT(Export Address Table) is none
USER32.dll
0x1401b41b6 CreateWindowExW
COMCTL32.dll
0x1401b41ce None
KERNEL32.dll
0x1401b41e6 GetACP
ADVAPI32.dll
0x1401b41fe OpenProcessToken
GDI32.dll
0x1401b4216 SelectObject
IPHLPAPI.DLL
0x1401b422e GetInterfaceInfo
msvcrt.dll
0x1401b4246 _wcsnicmp
PSAPI.DLL
0x1401b425e GetMappedFileNameW
SHELL32.dll
0x1401b4276 SHGetFolderPathW
EAT(Export Address Table) is none