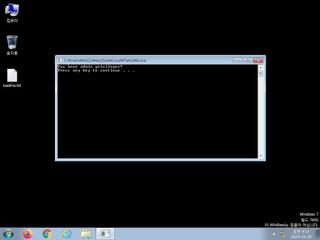
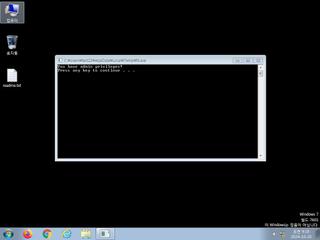
ScreenShot
| Created | 2024.10.20 09:41 | Machine | s1_win7_x6401 |
| Filename | lb.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 34 detected (AIDetectMalware, Malicious, score, GenericPMF, S18974517, GenericKD, Unsafe, Save, high confidence, Real Protect, high, Generic ML PUA, Static AI, Suspicious PE, Detected, Wacatac, SchoolBoy, Eldorado, CoinMiner, R243171, GenericRXWO, R002H09GF24, susgen, Nitol) | ||
| md5 | 069e089fa5687caab81cd32e6f931111 | ||
| sha256 | 82acdc79bf5adade712e838139343a3ba87459e831516293e37f4d3d33b78607 | ||
| ssdeep | 1536:3H7ftfkS5g9YOms+gZcQipICdXkNDqLLZX9lItVGL++eIOlnToIf6wJOl:3bFfHgTWmCRkGbKGLeNTBf6d | ||
| imphash | 2c5f2513605e48f2d8ea5440a870cb9e | ||
| impfuzzy | 48:YMuGno3GrCpb1HqJOI40EdXIqSZ/g/KA/kEUEk1WSY+09AEFXolvyAobFzGJ6tnm:Y7qo3qCpb1KJh400XIZW4wvIow | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 34 AntiVirus engines on VirusTotal as malicious |
| notice | Creates executable files on the filesystem |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Uses Windows utilities for basic Windows functionality |
| info | Checks amount of memory in system |
| info | Command line console output was observed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The executable uses a known packer |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
MSVCRT.dll
0x417470 memset
0x417474 wcsncmp
0x417478 memmove
0x41747c wcsncpy
0x417480 wcsstr
0x417484 _wcsnicmp
0x417488 _wcsdup
0x41748c free
0x417490 _wcsicmp
0x417494 wcslen
0x417498 wcscpy
0x41749c wcscmp
0x4174a0 wcscat
0x4174a4 memcpy
0x4174a8 tolower
0x4174ac malloc
KERNEL32.dll
0x4174b4 GetModuleHandleW
0x4174b8 HeapCreate
0x4174bc GetStdHandle
0x4174c0 SetConsoleCtrlHandler
0x4174c4 HeapDestroy
0x4174c8 ExitProcess
0x4174cc WriteFile
0x4174d0 GetTempFileNameW
0x4174d4 LoadLibraryExW
0x4174d8 EnumResourceTypesW
0x4174dc FreeLibrary
0x4174e0 RemoveDirectoryW
0x4174e4 EnumResourceNamesW
0x4174e8 GetCommandLineW
0x4174ec LoadResource
0x4174f0 SizeofResource
0x4174f4 FreeResource
0x4174f8 FindResourceW
0x4174fc GetNativeSystemInfo
0x417500 GetShortPathNameW
0x417504 GetWindowsDirectoryW
0x417508 GetSystemDirectoryW
0x41750c EnterCriticalSection
0x417510 CloseHandle
0x417514 LeaveCriticalSection
0x417518 InitializeCriticalSection
0x41751c WaitForSingleObject
0x417520 TerminateThread
0x417524 CreateThread
0x417528 GetProcAddress
0x41752c GetVersionExW
0x417530 Sleep
0x417534 WideCharToMultiByte
0x417538 HeapAlloc
0x41753c HeapFree
0x417540 LoadLibraryW
0x417544 GetCurrentProcessId
0x417548 GetCurrentThreadId
0x41754c GetModuleFileNameW
0x417550 PeekNamedPipe
0x417554 TerminateProcess
0x417558 GetEnvironmentVariableW
0x41755c SetEnvironmentVariableW
0x417560 GetCurrentProcess
0x417564 DuplicateHandle
0x417568 CreatePipe
0x41756c CreateProcessW
0x417570 GetExitCodeProcess
0x417574 SetUnhandledExceptionFilter
0x417578 HeapSize
0x41757c MultiByteToWideChar
0x417580 CreateDirectoryW
0x417584 SetFileAttributesW
0x417588 GetTempPathW
0x41758c DeleteFileW
0x417590 GetCurrentDirectoryW
0x417594 SetCurrentDirectoryW
0x417598 CreateFileW
0x41759c SetFilePointer
0x4175a0 TlsFree
0x4175a4 TlsGetValue
0x4175a8 TlsSetValue
0x4175ac TlsAlloc
0x4175b0 HeapReAlloc
0x4175b4 DeleteCriticalSection
0x4175b8 InterlockedCompareExchange
0x4175bc InterlockedExchange
0x4175c0 GetLastError
0x4175c4 SetLastError
0x4175c8 UnregisterWait
0x4175cc GetCurrentThread
0x4175d0 RegisterWaitForSingleObject
USER32.DLL
0x4175d8 CharUpperW
0x4175dc CharLowerW
0x4175e0 MessageBoxW
0x4175e4 DefWindowProcW
0x4175e8 DestroyWindow
0x4175ec GetWindowLongW
0x4175f0 GetWindowTextLengthW
0x4175f4 GetWindowTextW
0x4175f8 UnregisterClassW
0x4175fc LoadIconW
0x417600 LoadCursorW
0x417604 RegisterClassExW
0x417608 IsWindowEnabled
0x41760c EnableWindow
0x417610 GetSystemMetrics
0x417614 CreateWindowExW
0x417618 SetWindowLongW
0x41761c SendMessageW
0x417620 SetFocus
0x417624 CreateAcceleratorTableW
0x417628 SetForegroundWindow
0x41762c BringWindowToTop
0x417630 GetMessageW
0x417634 TranslateAcceleratorW
0x417638 TranslateMessage
0x41763c DispatchMessageW
0x417640 DestroyAcceleratorTable
0x417644 PostMessageW
0x417648 GetForegroundWindow
0x41764c GetWindowThreadProcessId
0x417650 IsWindowVisible
0x417654 EnumWindows
0x417658 SetWindowPos
GDI32.DLL
0x417660 GetStockObject
COMCTL32.DLL
0x417668 InitCommonControlsEx
SHELL32.DLL
0x417670 ShellExecuteExW
0x417674 SHGetFolderLocation
0x417678 SHGetPathFromIDListW
WINMM.DLL
0x417680 timeBeginPeriod
OLE32.DLL
0x417688 CoInitialize
0x41768c CoTaskMemFree
SHLWAPI.DLL
0x417694 PathAddBackslashW
0x417698 PathRenameExtensionW
0x41769c PathQuoteSpacesW
0x4176a0 PathRemoveArgsW
0x4176a4 PathRemoveBackslashW
EAT(Export Address Table) is none
MSVCRT.dll
0x417470 memset
0x417474 wcsncmp
0x417478 memmove
0x41747c wcsncpy
0x417480 wcsstr
0x417484 _wcsnicmp
0x417488 _wcsdup
0x41748c free
0x417490 _wcsicmp
0x417494 wcslen
0x417498 wcscpy
0x41749c wcscmp
0x4174a0 wcscat
0x4174a4 memcpy
0x4174a8 tolower
0x4174ac malloc
KERNEL32.dll
0x4174b4 GetModuleHandleW
0x4174b8 HeapCreate
0x4174bc GetStdHandle
0x4174c0 SetConsoleCtrlHandler
0x4174c4 HeapDestroy
0x4174c8 ExitProcess
0x4174cc WriteFile
0x4174d0 GetTempFileNameW
0x4174d4 LoadLibraryExW
0x4174d8 EnumResourceTypesW
0x4174dc FreeLibrary
0x4174e0 RemoveDirectoryW
0x4174e4 EnumResourceNamesW
0x4174e8 GetCommandLineW
0x4174ec LoadResource
0x4174f0 SizeofResource
0x4174f4 FreeResource
0x4174f8 FindResourceW
0x4174fc GetNativeSystemInfo
0x417500 GetShortPathNameW
0x417504 GetWindowsDirectoryW
0x417508 GetSystemDirectoryW
0x41750c EnterCriticalSection
0x417510 CloseHandle
0x417514 LeaveCriticalSection
0x417518 InitializeCriticalSection
0x41751c WaitForSingleObject
0x417520 TerminateThread
0x417524 CreateThread
0x417528 GetProcAddress
0x41752c GetVersionExW
0x417530 Sleep
0x417534 WideCharToMultiByte
0x417538 HeapAlloc
0x41753c HeapFree
0x417540 LoadLibraryW
0x417544 GetCurrentProcessId
0x417548 GetCurrentThreadId
0x41754c GetModuleFileNameW
0x417550 PeekNamedPipe
0x417554 TerminateProcess
0x417558 GetEnvironmentVariableW
0x41755c SetEnvironmentVariableW
0x417560 GetCurrentProcess
0x417564 DuplicateHandle
0x417568 CreatePipe
0x41756c CreateProcessW
0x417570 GetExitCodeProcess
0x417574 SetUnhandledExceptionFilter
0x417578 HeapSize
0x41757c MultiByteToWideChar
0x417580 CreateDirectoryW
0x417584 SetFileAttributesW
0x417588 GetTempPathW
0x41758c DeleteFileW
0x417590 GetCurrentDirectoryW
0x417594 SetCurrentDirectoryW
0x417598 CreateFileW
0x41759c SetFilePointer
0x4175a0 TlsFree
0x4175a4 TlsGetValue
0x4175a8 TlsSetValue
0x4175ac TlsAlloc
0x4175b0 HeapReAlloc
0x4175b4 DeleteCriticalSection
0x4175b8 InterlockedCompareExchange
0x4175bc InterlockedExchange
0x4175c0 GetLastError
0x4175c4 SetLastError
0x4175c8 UnregisterWait
0x4175cc GetCurrentThread
0x4175d0 RegisterWaitForSingleObject
USER32.DLL
0x4175d8 CharUpperW
0x4175dc CharLowerW
0x4175e0 MessageBoxW
0x4175e4 DefWindowProcW
0x4175e8 DestroyWindow
0x4175ec GetWindowLongW
0x4175f0 GetWindowTextLengthW
0x4175f4 GetWindowTextW
0x4175f8 UnregisterClassW
0x4175fc LoadIconW
0x417600 LoadCursorW
0x417604 RegisterClassExW
0x417608 IsWindowEnabled
0x41760c EnableWindow
0x417610 GetSystemMetrics
0x417614 CreateWindowExW
0x417618 SetWindowLongW
0x41761c SendMessageW
0x417620 SetFocus
0x417624 CreateAcceleratorTableW
0x417628 SetForegroundWindow
0x41762c BringWindowToTop
0x417630 GetMessageW
0x417634 TranslateAcceleratorW
0x417638 TranslateMessage
0x41763c DispatchMessageW
0x417640 DestroyAcceleratorTable
0x417644 PostMessageW
0x417648 GetForegroundWindow
0x41764c GetWindowThreadProcessId
0x417650 IsWindowVisible
0x417654 EnumWindows
0x417658 SetWindowPos
GDI32.DLL
0x417660 GetStockObject
COMCTL32.DLL
0x417668 InitCommonControlsEx
SHELL32.DLL
0x417670 ShellExecuteExW
0x417674 SHGetFolderLocation
0x417678 SHGetPathFromIDListW
WINMM.DLL
0x417680 timeBeginPeriod
OLE32.DLL
0x417688 CoInitialize
0x41768c CoTaskMemFree
SHLWAPI.DLL
0x417694 PathAddBackslashW
0x417698 PathRenameExtensionW
0x41769c PathQuoteSpacesW
0x4176a0 PathRemoveArgsW
0x4176a4 PathRemoveBackslashW
EAT(Export Address Table) is none