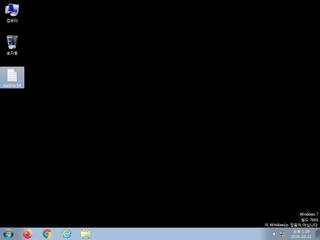
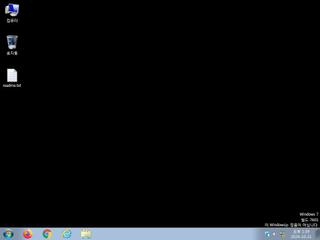
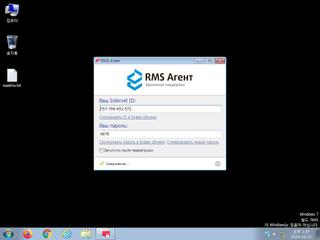
ScreenShot
| Created | 2024.10.21 13:46 | Machine | s1_win7_x6401 |
| Filename | a.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 42 detected (AIDetectMalware, RemoteUtilities, Malicious, score, Unsafe, Tool, Vooi, grayware, confidence, Attribute, HighConfidence, RemoteAdmin, W potentially unsafe, RemoteControl, jraccs, Hacktool, CLOUD, imskk, remote, access, Generic Reputation PUA, ABApplication, GMLQ, Artemis, RABased, RemoteManipulator, Gkjl, susgen, RynbpzAQBNHNGtN) | ||
| md5 | fec6019b90092723b543219410ce71b4 | ||
| sha256 | 6fb6cffbc9d37606dee6240083b2f3db1747a819ee84d2db3d1e2bc5937e93cc | ||
| ssdeep | 196608:np9T+NrpQJrG8M3+OvIKeFUOkpfG+n4qsYdz+FsCTk6x4acytLmfzB:n6rpQJK8M3+4teCOkpe3YhG7LmfzB | ||
| imphash | 19b321cb7a9ce31c90397152f38b67ea | ||
| impfuzzy | 6:omgtTJuVM4PaBJAEoZ/OEGDzyR2GgqxaZC3EQbJPyLGeQtMyyTc5KTXmJJcn:omgt34KABZG/DzigqxaZC3E6aLGbtITF | ||
Network IP location
Signature (21cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 42 AntiVirus engines on VirusTotal as malicious |
| danger | Connects to an IP address that is no longer responding to requests (legitimate services will remain up-and-running usually) |
| watch | Communicates with host for which no DNS query was performed |
| watch | Expresses interest in specific running processes |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Potentially malicious URLs were found in the process memory dump |
| notice | Searches running processes potentially to identify processes for sandbox evasion |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is compressed using UPX |
| notice | Yara rule detected in process memory |
| info | At least one process apparently crashed during execution |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Queries for the computername |
| info | The executable uses a known packer |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
Rules (40cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Emotet_2_Zero | Win32 Trojan Emotet | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | Network_DNS | Communications use DNS | memory |
| notice | Network_HTTP | Communications over HTTP | memory |
| notice | network_smtp_raw | Communications smtp | memory |
| notice | Network_SSL | Communications over SSL | memory |
| notice | Network_TCP_Socket | Communications over RAW Socket | memory |
| notice | Persistence | Install itself for autorun at Windows startup | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| notice | Str_Win32_Http_API | Match Windows Http API call | memory |
| notice | Str_Win32_Internet_API | Match Windows Inet API call | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | antisb_threatExpert | Anti-Sandbox checks for ThreatExpert | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (download) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
| info | WMI_VM_Detect | Detection of Virtual Appliances through the use of WMI for use of evasion. | memory |
PE API
IAT(Import Address Table) Library
advapi32.dll
0x1b98278 RegLoadKeyW
comctl32.dll
0x1b98280 ImageList_Add
gdi32.dll
0x1b98288 Pie
KERNEL32.DLL
0x1b98290 LoadLibraryA
0x1b98294 ExitProcess
0x1b98298 GetProcAddress
0x1b9829c VirtualProtect
msvcrt.dll
0x1b982a4 memcpy
netapi32.dll
0x1b982ac NetWkstaGetInfo
ole32.dll
0x1b982b4 IsEqualGUID
oleaut32.dll
0x1b982bc VariantInit
shell32.dll
0x1b982c4 ShellExecuteW
SHFolder.dll
0x1b982cc SHGetFolderPathW
user32.dll
0x1b982d4 GetDC
version.dll
0x1b982dc VerQueryValueW
winspool.drv
0x1b982e4 ClosePrinter
EAT(Export Address Table) is none
advapi32.dll
0x1b98278 RegLoadKeyW
comctl32.dll
0x1b98280 ImageList_Add
gdi32.dll
0x1b98288 Pie
KERNEL32.DLL
0x1b98290 LoadLibraryA
0x1b98294 ExitProcess
0x1b98298 GetProcAddress
0x1b9829c VirtualProtect
msvcrt.dll
0x1b982a4 memcpy
netapi32.dll
0x1b982ac NetWkstaGetInfo
ole32.dll
0x1b982b4 IsEqualGUID
oleaut32.dll
0x1b982bc VariantInit
shell32.dll
0x1b982c4 ShellExecuteW
SHFolder.dll
0x1b982cc SHGetFolderPathW
user32.dll
0x1b982d4 GetDC
version.dll
0x1b982dc VerQueryValueW
winspool.drv
0x1b982e4 ClosePrinter
EAT(Export Address Table) is none