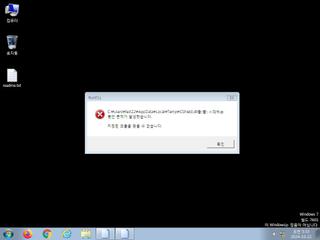
ScreenShot
| Created | 2024.10.22 05:33 | Machine | s1_win7_x6401 |
| Filename | CShield.dll | ||
| Type | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | |||
| md5 | db5198ea4d04bad9c91dc04ba2033579 | ||
| sha256 | 1998849026d2d7f4c307bef0a8f2de606d8d4c5966d8963a2592d107be4dc15e | ||
| ssdeep | 98304:m6h30YoT1QMYT17A8iwHbv33nnRNW3qn9wWZGPDxx+L9Vu:mkkx/Ubv3XnR069RcFxC9Vu | ||
| imphash | cae381e7af492d0839f28f8b1a4c21b2 | ||
| impfuzzy | 24:mDIq/uyWNYjwoOno1RQ58QtXJHc9NDI5Q8:DsCNyHwo1RQ5ZXpcM5Q8 | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1036c000 GetProcAddress
USER32.dll
0x1036c008 wsprintfA
MSVCP140.dll
0x1036c010 ?out@?$codecvt@DDU_Mbstatet@@@std@@QBEHAAU_Mbstatet@@PBD1AAPBDPAD3AAPAD@Z
VCRUNTIME140.dll
0x1036c018 __current_exception
api-ms-win-crt-time-l1-1-0.dll
0x1036c020 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x1036c028 _invalid_parameter_noinfo_noreturn
api-ms-win-crt-string-l1-1-0.dll
0x1036c030 strncmp
api-ms-win-crt-stdio-l1-1-0.dll
0x1036c038 _fseeki64
api-ms-win-crt-utility-l1-1-0.dll
0x1036c040 rand
api-ms-win-crt-heap-l1-1-0.dll
0x1036c048 _aligned_free
api-ms-win-crt-convert-l1-1-0.dll
0x1036c050 strtoull
api-ms-win-crt-locale-l1-1-0.dll
0x1036c058 localeconv
api-ms-win-crt-math-l1-1-0.dll
0x1036c060 _dclass
api-ms-win-crt-filesystem-l1-1-0.dll
0x1036c068 _lock_file
libcurl.dll
0x1036c070 curl_slist_append
WTSAPI32.dll
0x1036c078 WTSSendMessageW
KERNEL32.dll
0x1036c080 VirtualQuery
USER32.dll
0x1036c088 GetProcessWindowStation
KERNEL32.dll
0x1036c090 LocalAlloc
0x1036c094 LocalFree
0x1036c098 GetModuleFileNameW
0x1036c09c GetProcessAffinityMask
0x1036c0a0 SetProcessAffinityMask
0x1036c0a4 SetThreadAffinityMask
0x1036c0a8 Sleep
0x1036c0ac ExitProcess
0x1036c0b0 FreeLibrary
0x1036c0b4 LoadLibraryA
0x1036c0b8 GetModuleHandleA
0x1036c0bc GetProcAddress
USER32.dll
0x1036c0c4 GetProcessWindowStation
0x1036c0c8 GetUserObjectInformationW
EAT(Export Address Table) Library
0x10001eb0 ?CheckAttackspeed@@YA_NMM_N0@Z
0x10002050 ?CheckMovespeed@@YA_NM@Z
0x10006da0 ?GenKey@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@_NK@Z
0x10007e30 ?InitializeCShield@@YA?AU_CShieldData@@XZ
0x1004a02c ?charName@@3PADA
0x10049fc2 ?hackFound@@3_NA
KERNEL32.dll
0x1036c000 GetProcAddress
USER32.dll
0x1036c008 wsprintfA
MSVCP140.dll
0x1036c010 ?out@?$codecvt@DDU_Mbstatet@@@std@@QBEHAAU_Mbstatet@@PBD1AAPBDPAD3AAPAD@Z
VCRUNTIME140.dll
0x1036c018 __current_exception
api-ms-win-crt-time-l1-1-0.dll
0x1036c020 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x1036c028 _invalid_parameter_noinfo_noreturn
api-ms-win-crt-string-l1-1-0.dll
0x1036c030 strncmp
api-ms-win-crt-stdio-l1-1-0.dll
0x1036c038 _fseeki64
api-ms-win-crt-utility-l1-1-0.dll
0x1036c040 rand
api-ms-win-crt-heap-l1-1-0.dll
0x1036c048 _aligned_free
api-ms-win-crt-convert-l1-1-0.dll
0x1036c050 strtoull
api-ms-win-crt-locale-l1-1-0.dll
0x1036c058 localeconv
api-ms-win-crt-math-l1-1-0.dll
0x1036c060 _dclass
api-ms-win-crt-filesystem-l1-1-0.dll
0x1036c068 _lock_file
libcurl.dll
0x1036c070 curl_slist_append
WTSAPI32.dll
0x1036c078 WTSSendMessageW
KERNEL32.dll
0x1036c080 VirtualQuery
USER32.dll
0x1036c088 GetProcessWindowStation
KERNEL32.dll
0x1036c090 LocalAlloc
0x1036c094 LocalFree
0x1036c098 GetModuleFileNameW
0x1036c09c GetProcessAffinityMask
0x1036c0a0 SetProcessAffinityMask
0x1036c0a4 SetThreadAffinityMask
0x1036c0a8 Sleep
0x1036c0ac ExitProcess
0x1036c0b0 FreeLibrary
0x1036c0b4 LoadLibraryA
0x1036c0b8 GetModuleHandleA
0x1036c0bc GetProcAddress
USER32.dll
0x1036c0c4 GetProcessWindowStation
0x1036c0c8 GetUserObjectInformationW
EAT(Export Address Table) Library
0x10001eb0 ?CheckAttackspeed@@YA_NMM_N0@Z
0x10002050 ?CheckMovespeed@@YA_NM@Z
0x10006da0 ?GenKey@@YA?AV?$basic_string@DU?$char_traits@D@std@@V?$allocator@D@2@@std@@_NK@Z
0x10007e30 ?InitializeCShield@@YA?AU_CShieldData@@XZ
0x1004a02c ?charName@@3PADA
0x10049fc2 ?hackFound@@3_NA