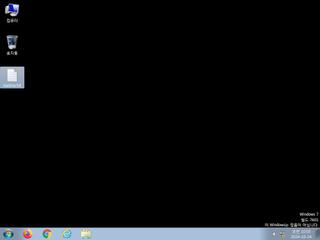
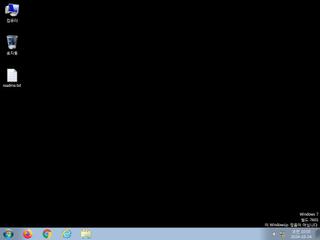
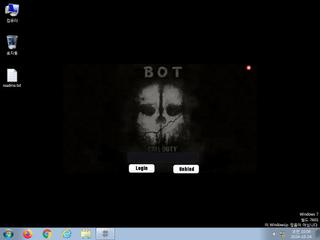
ScreenShot
| Created | 2024.10.24 10:06 | Machine | s1_win7_x6401 |
| Filename | LDvar.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 37 detected (AIDetectMalware, Malicious, score, Strictor, Unsafe, Save, confidence, Attribute, HighConfidence, high confidence, FlyStudio, RiskTool, Convagent, Real Protect, Generic ML PUA, Static AI, Malicious PE, Detected, ISVQ@5mbonp, Wacapew, Eldorado, Krypt, susgen, GenKryptik, DLII) | ||
| md5 | 2d7b09cd5f12fb6a3fc07e269a639051 | ||
| sha256 | ccc9f3d84c2251de94f54d03c62257b21ec7eeef29c16931fae4e06ef367c3fe | ||
| ssdeep | 196608:uRUxISBSxiw0pACjs/V7Uu8qGZRErzqCBa/8bJ225iStHg3:uuhBZyVP8PZREr7azIFt2 | ||
| imphash | 2cbb343f31943476e7ffd3952e3d673c | ||
| impfuzzy | 24:USWv3OhEz5qZfHEQ02ovQaQtXJHc9NDI5Q8:USWv3/zgWH2ovQnXpcM5Q8 | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| danger | Connects to an IP address that is no longer responding to requests (legitimate services will remain up-and-running usually) |
| danger | File has been identified by 37 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Foreign language identified in PE resource |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is likely packed with VMProtect |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| watch | VMProtect_Zero | VMProtect packed file | binaries (upload) |
| info | ftp_command | ftp command | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
iphlpapi.dll
0xfd4000 GetAdaptersInfo
WINMM.dll
0xfd4008 waveOutUnprepareHeader
WS2_32.dll
0xfd4010 inet_ntoa
MSVFW32.dll
0xfd4018 DrawDibDraw
AVIFIL32.dll
0xfd4020 AVIStreamInfoA
RASAPI32.dll
0xfd4028 RasGetConnectStatusA
KERNEL32.dll
0xfd4030 GetVersion
0xfd4034 GetVersionExA
USER32.dll
0xfd403c GetSysColorBrush
GDI32.dll
0xfd4044 GetPolyFillMode
WINSPOOL.DRV
0xfd404c ClosePrinter
comdlg32.dll
0xfd4054 GetFileTitleA
ADVAPI32.dll
0xfd405c RegCreateKeyExA
SHELL32.dll
0xfd4064 ShellExecuteA
ole32.dll
0xfd406c CLSIDFromProgID
OLEAUT32.dll
0xfd4074 VariantClear
COMCTL32.dll
0xfd407c ImageList_Destroy
WININET.dll
0xfd4084 HttpQueryInfoA
WTSAPI32.dll
0xfd408c WTSSendMessageW
KERNEL32.dll
0xfd4094 VirtualQuery
USER32.dll
0xfd409c GetUserObjectInformationW
KERNEL32.dll
0xfd40a4 LocalAlloc
0xfd40a8 LocalFree
0xfd40ac GetModuleFileNameW
0xfd40b0 GetProcessAffinityMask
0xfd40b4 SetProcessAffinityMask
0xfd40b8 SetThreadAffinityMask
0xfd40bc Sleep
0xfd40c0 ExitProcess
0xfd40c4 FreeLibrary
0xfd40c8 LoadLibraryA
0xfd40cc GetModuleHandleA
0xfd40d0 GetProcAddress
USER32.dll
0xfd40d8 GetProcessWindowStation
0xfd40dc GetUserObjectInformationW
EAT(Export Address Table) is none
iphlpapi.dll
0xfd4000 GetAdaptersInfo
WINMM.dll
0xfd4008 waveOutUnprepareHeader
WS2_32.dll
0xfd4010 inet_ntoa
MSVFW32.dll
0xfd4018 DrawDibDraw
AVIFIL32.dll
0xfd4020 AVIStreamInfoA
RASAPI32.dll
0xfd4028 RasGetConnectStatusA
KERNEL32.dll
0xfd4030 GetVersion
0xfd4034 GetVersionExA
USER32.dll
0xfd403c GetSysColorBrush
GDI32.dll
0xfd4044 GetPolyFillMode
WINSPOOL.DRV
0xfd404c ClosePrinter
comdlg32.dll
0xfd4054 GetFileTitleA
ADVAPI32.dll
0xfd405c RegCreateKeyExA
SHELL32.dll
0xfd4064 ShellExecuteA
ole32.dll
0xfd406c CLSIDFromProgID
OLEAUT32.dll
0xfd4074 VariantClear
COMCTL32.dll
0xfd407c ImageList_Destroy
WININET.dll
0xfd4084 HttpQueryInfoA
WTSAPI32.dll
0xfd408c WTSSendMessageW
KERNEL32.dll
0xfd4094 VirtualQuery
USER32.dll
0xfd409c GetUserObjectInformationW
KERNEL32.dll
0xfd40a4 LocalAlloc
0xfd40a8 LocalFree
0xfd40ac GetModuleFileNameW
0xfd40b0 GetProcessAffinityMask
0xfd40b4 SetProcessAffinityMask
0xfd40b8 SetThreadAffinityMask
0xfd40bc Sleep
0xfd40c0 ExitProcess
0xfd40c4 FreeLibrary
0xfd40c8 LoadLibraryA
0xfd40cc GetModuleHandleA
0xfd40d0 GetProcAddress
USER32.dll
0xfd40d8 GetProcessWindowStation
0xfd40dc GetUserObjectInformationW
EAT(Export Address Table) is none